-
Notifications
You must be signed in to change notification settings - Fork 8.2k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Security Solution] FinalEdit: Add name and kql_query fields + shared components
#193828
Merged
Conversation
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
69 tasks
…nents' into 3wd-field-edit-base
3035808
to
ac4048e
Compare
|
Starting backport for target branches: 8.x https://github.com/elastic/kibana/actions/runs/11332069490 |
💚 Build Succeeded
Metrics [docs]Module Count
Async chunks
History
cc @nikitaindik |
kibanamachine
pushed a commit
to kibanamachine/kibana
that referenced
this pull request
Oct 14, 2024
…shared components (elastic#193828) **Partially addresses: elastic#171520 **Is a follow-up PR to: elastic#192342 ## Summary Changes: - Adds editable components for `name` and `kql_query` fields - Adds a `FieldFormWrapper` component that abstracts away form creation and data preparation for each field - Adds local context providers to pass data between the main context and field components - Adds some basic layout components to make the "edit" functionality work <img width="1392" alt="Schermafbeelding 2024-10-04 om 17 17 44" src="https://github.com/user-attachments/assets/6272ac84-8159-4b8a-a0d4-88b458f4bc5f"> --------- Co-authored-by: Maxim Palenov <maxim.palenov@elastic.co> (cherry picked from commit 424ffba)
💚 All backports created successfully
Note: Successful backport PRs will be merged automatically after passing CI. Questions ?Please refer to the Backport tool documentation |
kibanamachine
added a commit
that referenced
this pull request
Oct 14, 2024
… and `kql_query` fields + shared components (#193828) (#196191) # Backport This will backport the following commits from `main` to `8.x`: - [[Security Solution] `FinalEdit`: Add `name` and `kql_query` fields + shared components (#193828)](#193828) <!--- Backport version: 9.4.3 --> ### Questions ? Please refer to the [Backport tool documentation](https://github.com/sqren/backport) <!--BACKPORT [{"author":{"name":"Nikita Indik","email":"nikita.indik@elastic.co"},"sourceCommit":{"committedDate":"2024-10-14T17:09:59Z","message":"[Security Solution] `FinalEdit`: Add `name` and `kql_query` fields + shared components (#193828)\n\n**Partially addresses: https://github.com/elastic/kibana/issues/171520**\r\n**Is a follow-up PR to: https://github.com/elastic/kibana/pull/192342**\r\n\r\n## Summary\r\n\r\nChanges:\r\n - Adds editable components for `name` and `kql_query` fields\r\n- Adds a `FieldFormWrapper` component that abstracts away form creation\r\nand data preparation for each field\r\n- Adds local context providers to pass data between the main context and\r\nfield components\r\n- Adds some basic layout components to make the \"edit\" functionality\r\nwork\r\n\r\n<img width=\"1392\" alt=\"Schermafbeelding 2024-10-04 om 17 17 44\"\r\nsrc=\"https://github.com/user-attachments/assets/6272ac84-8159-4b8a-a0d4-88b458f4bc5f\">\r\n\r\n---------\r\n\r\nCo-authored-by: Maxim Palenov <maxim.palenov@elastic.co>","sha":"424ffbaffc6bdcec2634572d18cad5392ef0ace8","branchLabelMapping":{"^v9.0.0$":"main","^v8.16.0$":"8.x","^v(\\d+).(\\d+).\\d+$":"$1.$2"}},"sourcePullRequest":{"labels":["release_note:skip","v9.0.0","Team:Detections and Resp","Team: SecuritySolution","Team:Detection Rule Management","Feature:Prebuilt Detection Rules","backport:prev-minor"],"title":"[Security Solution] `FinalEdit`: Add `name` and `kql_query` fields + shared components","number":193828,"url":"https://github.com/elastic/kibana/pull/193828","mergeCommit":{"message":"[Security Solution] `FinalEdit`: Add `name` and `kql_query` fields + shared components (#193828)\n\n**Partially addresses: https://github.com/elastic/kibana/issues/171520**\r\n**Is a follow-up PR to: https://github.com/elastic/kibana/pull/192342**\r\n\r\n## Summary\r\n\r\nChanges:\r\n - Adds editable components for `name` and `kql_query` fields\r\n- Adds a `FieldFormWrapper` component that abstracts away form creation\r\nand data preparation for each field\r\n- Adds local context providers to pass data between the main context and\r\nfield components\r\n- Adds some basic layout components to make the \"edit\" functionality\r\nwork\r\n\r\n<img width=\"1392\" alt=\"Schermafbeelding 2024-10-04 om 17 17 44\"\r\nsrc=\"https://github.com/user-attachments/assets/6272ac84-8159-4b8a-a0d4-88b458f4bc5f\">\r\n\r\n---------\r\n\r\nCo-authored-by: Maxim Palenov <maxim.palenov@elastic.co>","sha":"424ffbaffc6bdcec2634572d18cad5392ef0ace8"}},"sourceBranch":"main","suggestedTargetBranches":[],"targetPullRequestStates":[{"branch":"main","label":"v9.0.0","branchLabelMappingKey":"^v9.0.0$","isSourceBranch":true,"state":"MERGED","url":"https://github.com/elastic/kibana/pull/193828","number":193828,"mergeCommit":{"message":"[Security Solution] `FinalEdit`: Add `name` and `kql_query` fields + shared components (#193828)\n\n**Partially addresses: https://github.com/elastic/kibana/issues/171520**\r\n**Is a follow-up PR to: https://github.com/elastic/kibana/pull/192342**\r\n\r\n## Summary\r\n\r\nChanges:\r\n - Adds editable components for `name` and `kql_query` fields\r\n- Adds a `FieldFormWrapper` component that abstracts away form creation\r\nand data preparation for each field\r\n- Adds local context providers to pass data between the main context and\r\nfield components\r\n- Adds some basic layout components to make the \"edit\" functionality\r\nwork\r\n\r\n<img width=\"1392\" alt=\"Schermafbeelding 2024-10-04 om 17 17 44\"\r\nsrc=\"https://github.com/user-attachments/assets/6272ac84-8159-4b8a-a0d4-88b458f4bc5f\">\r\n\r\n---------\r\n\r\nCo-authored-by: Maxim Palenov <maxim.palenov@elastic.co>","sha":"424ffbaffc6bdcec2634572d18cad5392ef0ace8"}}]}] BACKPORT--> Co-authored-by: Nikita Indik <nikita.indik@elastic.co>
maximpn
added a commit
that referenced
this pull request
Oct 25, 2024
**Partially addresses:** #171520 ## Summary This PR adds is built on top of #193828 and add a Data Source editable component for final edit side of Three Way Diff tab of the upgrade prebuilt rule workflow. ## Details #171520 required adding editable components for each field diffable rule field. It imposes some difficulties since it's quite problematic to reuse existing especially complex components like Data Source from Define Rule step component. This PR make little refactoring to the Define Rule step component to make it simpler and make it easier to reuse Data Source related code chunks scattered in Define Rule step component. You may notice some copy-paste chunks of Data Source editable component in the PR. At this stage it's the simplest way to proceed to avoid huge refactoring and potential new bugs. Taking into account deadlines for the task it looks like a good trade off. There is a plan to work on improvements for rules creation/editing forms later on.
kibanamachine
pushed a commit
to kibanamachine/kibana
that referenced
this pull request
Oct 25, 2024
**Partially addresses:** elastic#171520 ## Summary This PR adds is built on top of elastic#193828 and add a Data Source editable component for final edit side of Three Way Diff tab of the upgrade prebuilt rule workflow. ## Details elastic#171520 required adding editable components for each field diffable rule field. It imposes some difficulties since it's quite problematic to reuse existing especially complex components like Data Source from Define Rule step component. This PR make little refactoring to the Define Rule step component to make it simpler and make it easier to reuse Data Source related code chunks scattered in Define Rule step component. You may notice some copy-paste chunks of Data Source editable component in the PR. At this stage it's the simplest way to proceed to avoid huge refactoring and potential new bugs. Taking into account deadlines for the task it looks like a good trade off. There is a plan to work on improvements for rules creation/editing forms later on. (cherry picked from commit f34802b)
kibanamachine
added a commit
that referenced
this pull request
Oct 25, 2024
#197877) # Backport This will backport the following commits from `main` to `8.x`: - [[Security Solution] Add data source editable component (#196948)](#196948) <!--- Backport version: 9.4.3 --> ### Questions ? Please refer to the [Backport tool documentation](https://github.com/sqren/backport) <!--BACKPORT [{"author":{"name":"Maxim Palenov","email":"maxim.palenov@elastic.co"},"sourceCommit":{"committedDate":"2024-10-25T16:52:27Z","message":"[Security Solution] Add data source editable component (#196948)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and add a Data Source editable component for final edit side of Three Way Diff tab of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nhttps://github.com//issues/171520 required adding editable components for each field diffable rule field. It imposes some difficulties since it's quite problematic to reuse existing especially complex components like Data Source from Define Rule step component.\r\n\r\nThis PR make little refactoring to the Define Rule step component to make it simpler and make it easier to reuse Data Source related code chunks scattered in Define Rule step component. You may notice some copy-paste chunks of Data Source editable component in the PR. At this stage it's the simplest way to proceed to avoid huge refactoring and potential new bugs. Taking into account deadlines for the task it looks like a good trade off. There is a plan to work on improvements for rules creation/editing forms later on.","sha":"f34802bc6fae7a17e2b75e22ccde3fee380a4dee","branchLabelMapping":{"^v9.0.0$":"main","^v8.17.0$":"8.x","^v(\\d+).(\\d+).\\d+$":"$1.$2"}},"sourcePullRequest":{"labels":["release_note:skip","v9.0.0","Team:Detections and Resp","Team: SecuritySolution","Team:Detection Rule Management","Feature:Prebuilt Detection Rules","backport:prev-minor","v8.17.0"],"title":"[Security Solution] Add data source editable component","number":196948,"url":"https://github.com/elastic/kibana/pull/196948","mergeCommit":{"message":"[Security Solution] Add data source editable component (#196948)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and add a Data Source editable component for final edit side of Three Way Diff tab of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nhttps://github.com//issues/171520 required adding editable components for each field diffable rule field. It imposes some difficulties since it's quite problematic to reuse existing especially complex components like Data Source from Define Rule step component.\r\n\r\nThis PR make little refactoring to the Define Rule step component to make it simpler and make it easier to reuse Data Source related code chunks scattered in Define Rule step component. You may notice some copy-paste chunks of Data Source editable component in the PR. At this stage it's the simplest way to proceed to avoid huge refactoring and potential new bugs. Taking into account deadlines for the task it looks like a good trade off. There is a plan to work on improvements for rules creation/editing forms later on.","sha":"f34802bc6fae7a17e2b75e22ccde3fee380a4dee"}},"sourceBranch":"main","suggestedTargetBranches":["8.x"],"targetPullRequestStates":[{"branch":"main","label":"v9.0.0","branchLabelMappingKey":"^v9.0.0$","isSourceBranch":true,"state":"MERGED","url":"https://github.com/elastic/kibana/pull/196948","number":196948,"mergeCommit":{"message":"[Security Solution] Add data source editable component (#196948)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and add a Data Source editable component for final edit side of Three Way Diff tab of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nhttps://github.com//issues/171520 required adding editable components for each field diffable rule field. It imposes some difficulties since it's quite problematic to reuse existing especially complex components like Data Source from Define Rule step component.\r\n\r\nThis PR make little refactoring to the Define Rule step component to make it simpler and make it easier to reuse Data Source related code chunks scattered in Define Rule step component. You may notice some copy-paste chunks of Data Source editable component in the PR. At this stage it's the simplest way to proceed to avoid huge refactoring and potential new bugs. Taking into account deadlines for the task it looks like a good trade off. There is a plan to work on improvements for rules creation/editing forms later on.","sha":"f34802bc6fae7a17e2b75e22ccde3fee380a4dee"}},{"branch":"8.x","label":"v8.17.0","branchLabelMappingKey":"^v8.17.0$","isSourceBranch":false,"state":"NOT_CREATED"}]}] BACKPORT--> Co-authored-by: Maxim Palenov <maxim.palenov@elastic.co>
crespocarlos
added a commit
to crespocarlos/kibana
that referenced
this pull request
Nov 4, 2024
Create entity_client functions
Create entity_client functions
Fix entityLatest flatten object
Fix redirection to service overview
Fix redirection to service overview
Add tests
Add tests
Refactoring and tests
Clean up
[CI] Auto-commit changed files from 'node scripts/yarn_deduplicate'
fix after rebase
Fix build
[Dataset Quality]Fix elastic doc test (#197835)
Found a bug while backporting another PR.
The elastic docs in main always refer to master, but once a release is
cut, it check for specific version in the URL.
hence updated the test
P.S: This does not need backport to 8.x as this has already been fixed
in 8.x
[FTR][Ownership] Assign visualize, etc (#197664)
Assign test files to small number of reviewers
Assigned visualize due to the name
Assigned functional_execution_context due to
https://github.com/elastic/kibana/blob/main/x-pack/test/functional_execution_context/plugins/alerts/kibana.jsonc#L4
Assigned kubernetes_security per
https://github.com/elastic/kibana/blob/main/x-pack/plugins/kubernetes_security/kibana.jsonc#L4
Assigned licensing_plugin due to
https://github.com/elastic/kibana/blob/main/x-pack/plugins/licensing/kibana.jsonc#L4
Assigned rule_registry due to
https://github.com/elastic/kibana/blob/main/x-pack/plugins/rule_registry/kibana.jsonc#L4-L5
Assigned usage_collection due to
https://github.com/elastic/kibana/blob/main/api_docs/usage_collection.mdx#L18
- It says `Contact @elastic/kibana-core for questions regarding this
plugin.`
Assigned observability_onboarding_api_integration due to
https://github.com/elastic/kibana/blob/main/api_docs/observability_onboarding.mdx#L18
- It says `Contact @elastic/obs-ux-logs-team for questions regarding
this plugin.`
Contributes to: https://github.com/elastic/kibana/issues/194817
[React@18 failing tests] Dataset quality handles user privileges (#197830)
[Security Solution] Add data source editable component (#196948)
**Partially addresses:** https://github.com/elastic/kibana/issues/171520
This PR adds is built on top of https://github.com/elastic/kibana/pull/193828 and add a Data Source editable component for final edit side of Three Way Diff tab of the upgrade prebuilt rule workflow.
https://github.com/elastic/kibana/issues/171520 required adding editable components for each field diffable rule field. It imposes some difficulties since it's quite problematic to reuse existing especially complex components like Data Source from Define Rule step component.
This PR make little refactoring to the Define Rule step component to make it simpler and make it easier to reuse Data Source related code chunks scattered in Define Rule step component. You may notice some copy-paste chunks of Data Source editable component in the PR. At this stage it's the simplest way to proceed to avoid huge refactoring and potential new bugs. Taking into account deadlines for the task it looks like a good trade off. There is a plan to work on improvements for rules creation/editing forms later on.
search: move getting started to footer (#197849)
Moved the `Getting Started` link to the footer

[OpenAPI][DOCS] Add descriptions, examples, responses for role APIs (#195527)
Co-authored-by: Elena Shostak <165678770+elena-shostak@users.noreply.github.com>
[Security Solution] Unskips Timeline Cypress tests (#195721)
Fixes below Flaky tests issues :
- [x] https://github.com/elastic/kibana/issues/180688
- [x] https://github.com/elastic/kibana/issues/176945
- [x] https://github.com/elastic/kibana/issues/175180
- [x] https://github.com/elastic/kibana/issues/181466
- [x] https://github.com/elastic/kibana/issues/182021
- [x] https://github.com/elastic/kibana/issues/183085
- [x] https://github.com/elastic/kibana/issues/175180
---------
Co-authored-by: Michael Olorunnisola <michael.olorunnisola@elastic.co>
[ci] Use es snapshot cache on miscellaneous steps, adjust schedule (#197294)
The schedule adjustment is due to 7.17 verification taking longer than
other branches. Currently, we only rebuild once when main is updated.
This is a stopgap until a cache-only update can be introduced to avoid
continuous image rebuilds.
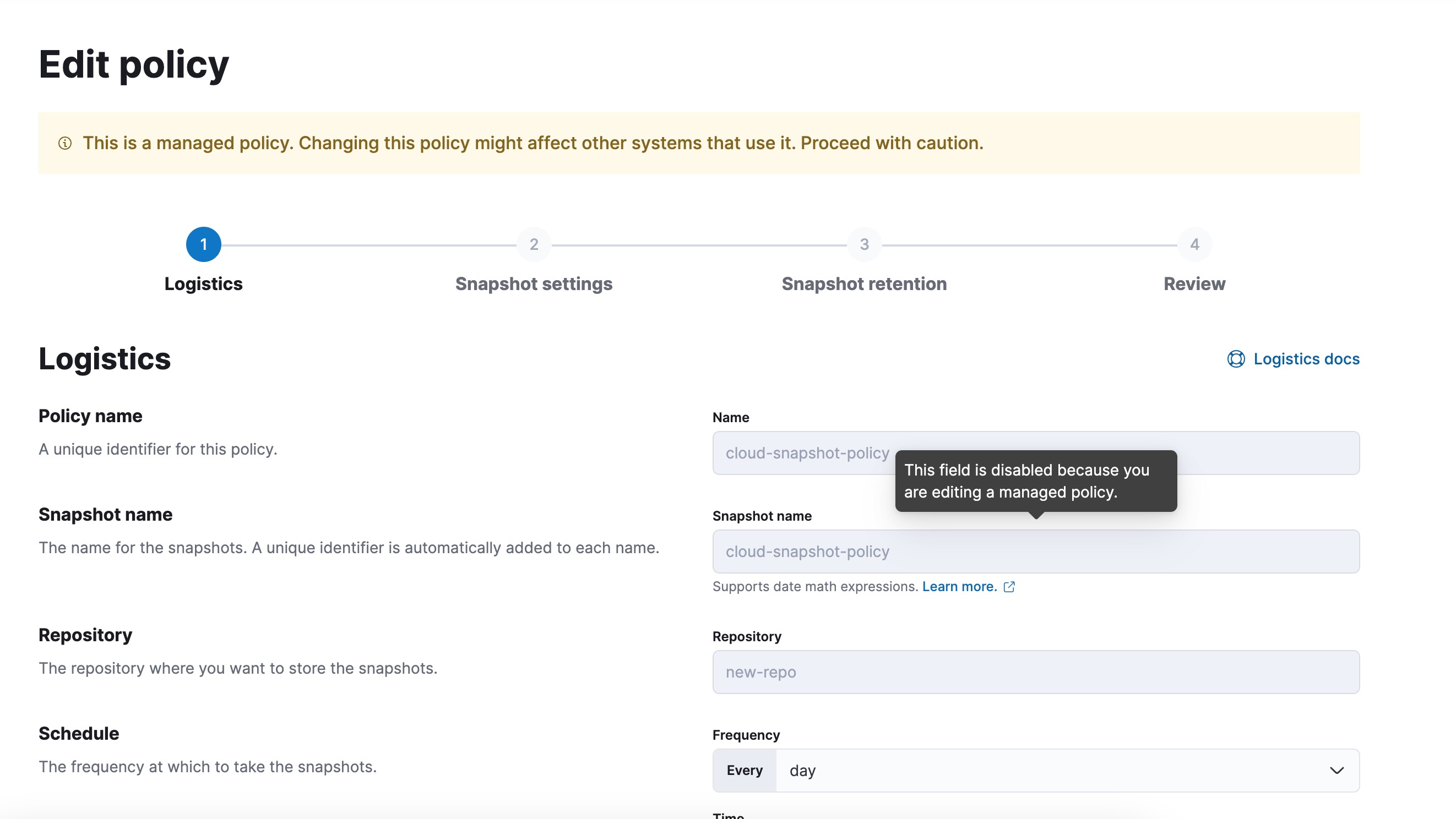
[SR] Add tooltips for disabled fields on managed SLM repository and policy (#196565)
Closes
https://github.com/elastic/kibana/issues/173124#issuecomment-2352968634
by adding tooltips details when hovering the disabled SLM repository or
policy fields.
**SLM managed repository**
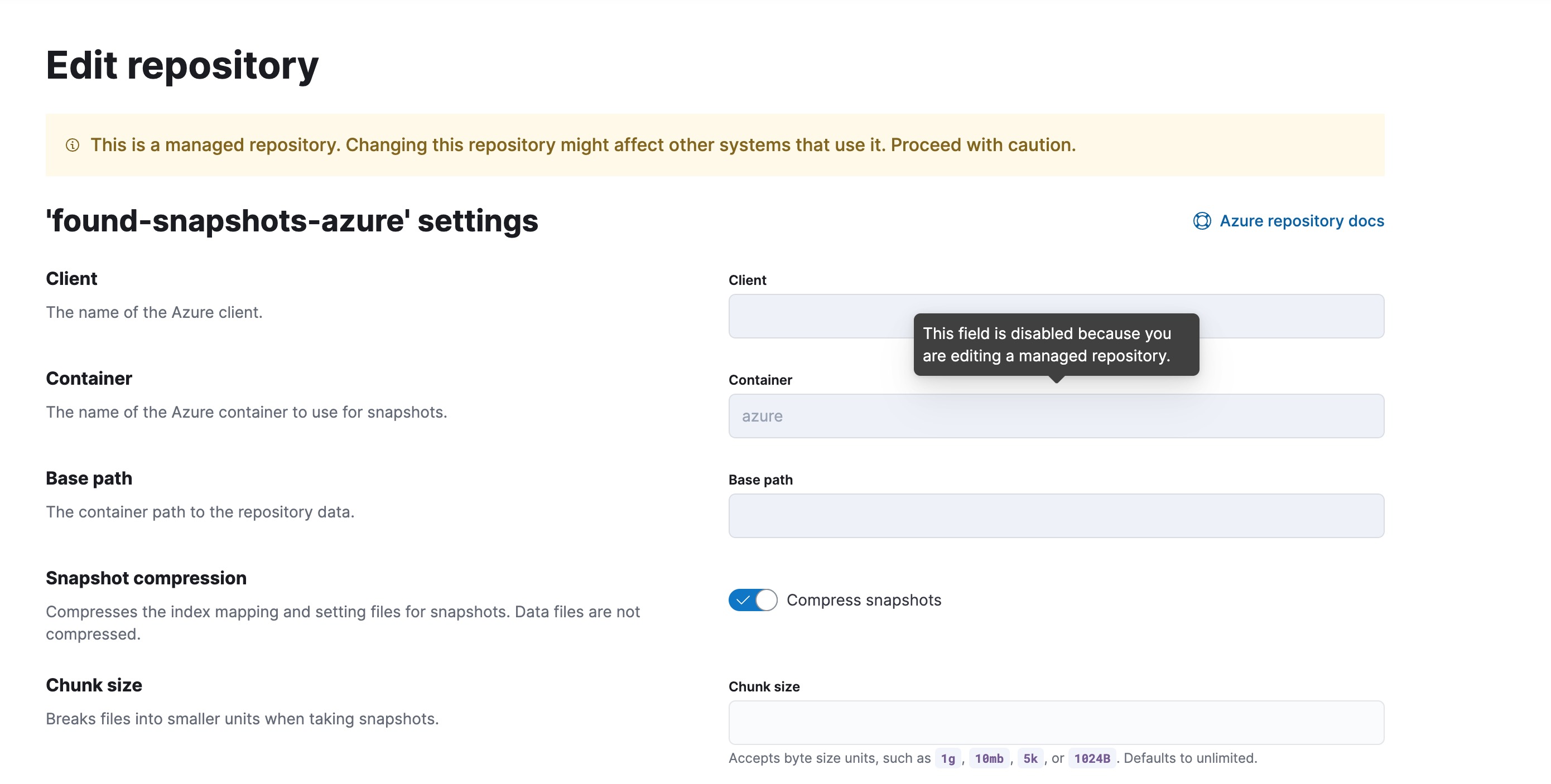
**SLM managed policy**
- [x] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [x] Any UI touched in this PR does not create any new axe failures
(run axe in browser:
[FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/),
[Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
- [x] This renders correctly on smaller devices using a responsive
layout. (You can test this [in your
browser](https://www.browserstack.com/guide/responsive-testing-on-local-server))
- [x] This was checked for [cross-browser
compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
- [x] This was checked for breaking API changes and was [labeled
appropriately](https://www.elastic.co/guide/en/kibana/master/contributing.html#_add_your_labels)
- [x] This will appear in the **Release Notes** and follow the
[guidelines](https://www.elastic.co/guide/en/kibana/master/contributing.html#kibana-release-notes-process)
---------
Co-authored-by: Elena Stoeva <59341489+ElenaStoeva@users.noreply.github.com>
[Security GenAI] When indices referenced in KB index entries are deleted from OUTSIDE the AI Assistant KB UI, there is not indication to the user (#197156) (#197722)
Bug https://github.com/elastic/kibana/issues/197156
This is a UI part of the bug that warns a user about missing indices
used in knowledge base entries.
1. Add an index entry that uses existing index
2. Remove that index
3. Go back to knowledge base entries page
4. You should see warning icon next to the name of the index entry which
uses removed index. Also, when you edit that entry you will see `Index
doesn't exist` error next to the `Index` field in the flyout
<img width="1458" alt="Screenshot 2024-10-24 at 19 54 36"
src="https://github.com/user-attachments/assets/7d4468f9-fada-4416-9480-99bfca3de220">
<img width="615" alt="Screenshot 2024-10-24 at 19 54 52"
src="https://github.com/user-attachments/assets/fd9bbe80-0a3c-40b8-909a-93f8082e69eb">
Delete any items that are not applicable to this PR.
- [x] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
[Security Solution][Endpoint] Ensure that DS indices for response actions are created prior to sending action to Endpoint (#196953)
PR adds changes to Security Solution so that DOT indices (restricted in
Serverless) are created in Kibana prior to Elastic Defend (Endpoint)
attempting to stream documents to these indices. The indices that are
now created in kibana are:
- `.logs-endpoint.diagnostic.collection-<namespace_from_policy>`
- `.logs-endpoint.action.responses-<namespace_from_policy>`
- `.logs-endpoint.heartbeat-<namespace_from_policy>` _(⚠️ created only
in serverless only)_
- Added support for the following two server-side extension points:
- `packagePolicyPostUpdate` : callbacks invoked after an integration
policy has been updated successfully
- `agentPolicyPostUpdate` : callbacks invoked after an agent policy has
been updated successfully
- Logic was added to the following Fleet server-side extension points
that checks if the necessary indices exist and if not, it creates them:
- After creating an Elastic Defend integration policy
- After updating an Elastic Defend integration policy
- After updating a Fleet Agent Policy that includes Elastic Defend
integration policy
Mark connector param validation failures as user errors (#197812)
Resolves https://github.com/elastic/response-ops-team/issues/255
In this PR, I'm changing the type of error thrown when connector
parameter validation fails so it indicates it's a user type of error.
This will allow us to exclude these errors from our serverless
monitoring given the users define the parameters the connectors receive
when they run. Mainly via alerting rule mustache templates, which are
easy to render empty strings and such.
[Security Solution][Notes] - fix createdBy filter for notes management page (#197706)
[Search][Fix] Index Details: poll mappings (#197885)
[Security GenAI] When a "global" Knowledge Base entry is updated to "private", a duplicate "private" entry gets created and the global entry remains unchanged (#197157) (#197516)
Original ticket describing the BUG:
https://github.com/elastic/kibana/issues/197157
These changes fix two issues:
1. Updating an entry from Global to Private duplicates it. After
discussing with the team we decided that this is an expected behaviour
and we would add a modal dialog which warns users about it. See more
details here
https://github.com/elastic/kibana/issues/197157#issuecomment-2432592394
2. Editing Private entry and switching the sharing option twice from
Private => Global => Private causes the issue where we would treat
selected entry as a new one and thus calling "create entry" instead of
"update".
* Edit private entry
* Update entry's name
* Switch sharing option to Global
* Switch sharing option back to Private
* Save the entry
**Current behaviour**: a new private entry is created
**Expected behaviour**: existing private entry is updated
https://github.com/user-attachments/assets/e11e14bd-c557-401e-a23f-e01ac7aedf30
Delete any items that are not applicable to this PR.
- [ ] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
Update docker.elastic.co/wolfi/chainguard-base:latest Docker digest to de4d5b0 (main) (#197917)
[Response Ops][Maintenance Window] Fix Maintenance Window Wildcard Scoped Queries (#194777)
Issue: https://github.com/elastic/sdh-kibana/issues/4923
Fixes maintenance window scoped query using wildcards by injecting the
`analyze_wildcard` property to the DSL used to determine which alerts
should be associated with the maintenance window.
Also fixes the update route to correctly take into account the user's
`allowLeadingWildcard` flag. It was implemented for the create route but
not the update route.
Fixes: https://github.com/elastic/kibana/issues/194763
1. Install sample data:

2. Create a maintenance window with the following scoped query:

3. Create a ES query rule and trigger actions:

4. Assert the `maintenance_window_id` on the 4 alerts are set

- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios)
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[api-docs] 2024-10-27 Daily api_docs build (#197930)
Generated by
https://buildkite.com/elastic/kibana-api-docs-daily/builds/873
[Cloud Security] Clicking on Contextual Flyout popout Icon now opens page in new tab (#196763)
Currently when user clicks on Popout icon on Misconfiguration or
Vulnerabilities Contextual flyout, user gets redirected to Findings page
but in the same tab. Popout Icon implies that it should navigate user to
other page on separate Tabs as such the current behaviour is not right.
This PR addresses that issue
---------
Co-authored-by: kibanamachine <42973632+kibanamachine@users.noreply.github.com>
[ES|QL] Update function metadata (#197940)
This PR updates the function definitions and inline docs based on the
latest metadata from Elasticsearch.
[Security Solution] Remove index pattern field from Sourcerer (#190113)
This PR removes index pattern field from the sourcerer model, replacing
it with direct access to data view spec.
The end goal for the sourcerer is to just utilize platform wide Data
View Types, instead of some custom abstractions / containers such as
indexPattern field which is effectively a DataViewSpec, just packed up
differently.
[Cloud Security] add posture type for CSPM dashboard accounts link (#197633)
- fixes https://github.com/elastic/security-team/issues/10914
[Observability Onboarding] Show search bar even when category is not selected (#197825)
Closes https://github.com/elastic/observability-dev/issues/4065 🔒
Fixes an issue when search bar is not visible unless a category is
selected.

Fix typo in the file name
CR fixes
[ResponseOps][Cases] Miscount of total numbers of alerts in telemetry (#196112)
Closes https://github.com/elastic/kibana/issues/177208
Problem:
- the metrics collected in telemetry for alerts don't count the total
number of alerts on a case correctly.
Solution:
- added new aggregation function: getUniqueAlertCommentsCountQuery,
which is now responsible for defining the cardinality aggregation for
counting unique alert comments by alertId.
- in the aggs section of the savedObjectsClient.find, the new
cardinality aggregation query was added
- the total number of alerts is updated to be the result extracted from
the new aggregation
Example:

- in the telemetry object, we have the following info:
<img width="331" alt="Screenshot 2024-10-22 at 15 21 40"
src="https://github.com/user-attachments/assets/6419e72d-84b4-4068-a741-6e32c6e966f7">
---------
Co-authored-by: Antonio <antoniodcoelho@gmail.com>
[ResponseOps][Cases]Add instructions of how to create a connector in the create case form (#197041)
Closes https://github.com/elastic/kibana/issues/189246
- A helper text was added in the create case form to tell the user that
needs to create a connector in the stack management > cases > settings
before attaching it to a case
- A new "add connector" button was placed in the stack management >
cases > settings page, in the connectors section
https://github.com/user-attachments/assets/7866b41a-11b5-4ca3-bd65-988412ab1e2f
---------
Co-authored-by: Antonio <antoniodcoelho@gmail.com>
[Discover][ES|QL] Rename Documents tab to Results (#197833)
This PR renames Documents label to Results for ES|QL mode.
<img width="1091" alt="Screenshot 2024-10-25 at 15 44 32"
src="https://github.com/user-attachments/assets/8678bb86-7e4b-4341-9bb3-50becced655b">
<img width="1676" alt="Screenshot 2024-10-25 at 15 52 55"
src="https://github.com/user-attachments/assets/c79d2ee0-62e1-4506-bcb5-29552287f140">
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
[EDR Workflows] Enable Blocklist CY in MKI (#197952)
Since adding this test file was tied to changes in Kibana, we initially
couldn’t enable it in the MKI. The MKI relies on a Kibana image built
from the main branch, and at that time, the necessary changes for these
tests to pass hadn’t yet been merged. Now that these updates are
included in the main branch, the Kibana image used in MKI has the
required changes, so we can proceed with enabling the tests.
Manual MKI run -
https://buildkite.com/elastic/kibana-serverless-security-solution-quality-gate-defend-workflows/builds/1545
[Security Solution][Detection Engine] removes legacy alerting endpoints from Security Solution dev scripts (#197424)
- addresses https://github.com/elastic/kibana/issues/95842
---------
Co-authored-by: Ryland Herrick <ryalnd@gmail.com>
[CodeQL] Local run script (#194272)
This PR introduces a script that allows developers to run CodeQL
analysis locally. It uses a Docker container with prebuilt CodeQL
queries to facilitate easy setup and execution.
The script has the following key steps:
- Creating a CodeQL database from the source code. The database is
essentially a representation of the codebase that CodeQL uses to analyze
for potential issues.
- Running the analysis on the created database,
`javascript-security-and-quality` suit is used.
```
bash scripts/codeql/quick_check.sh -s path/to/your-source-dir
```
For example
```
bash scripts/codeql/quick_check.sh -s ./x-pack/plugins/security_solution/public/common/components/ml/conditional_links
```
The `-s` option allows you to specify the path to the source code
directory that you wish to analyze.
Checked the ability to use MSFT image for local run
https://github.com/microsoft/codeql-container. Turned out it has several
problems:
1. The published one has an error with [execute
permissions](https://github.com/microsoft/codeql-container/issues/53).
2. Container has outdated nodejs version, so it didn't parse our syntax
(like `??`) and failed.
3. The technique used in the repository to download the CodeQL binaries
and precompile the queries is outdated in the sense that GitHub now
offers pre-compiled queries you can just download. Follow this
[comment](https://github.com/microsoft/codeql-container/issues/53#issuecomment-1875879512).
Taking this into consideration I have created a lightweight docker image
without extraneous dependencies for go/.net/java.
There are issues sometimes when analyze run returns no results,
particularly when analyzing a single folder.
It might be due to the missing context for the data flow graph CodeQL
generates or context for interdependencies. This is actually a trade off
of running it locally for a subset of source directories. We need to
explicitly state that in the documentation and advise to expand the
scope of source code directories involved for local scan.
Documentation for triaging issues will be updated separately.
__Closes: https://github.com/elastic/kibana/issues/195740__
chore(slo): remove tests migrated to agnostic framework (#197711)
Resolves https://github.com/elastic/kibana/issues/183397
This PR is a follow up of https://github.com/elastic/kibana/pull/195927,
that removes the old and migrated tests to the agnostic framework.
---------
Co-authored-by: kibanamachine <42973632+kibanamachine@users.noreply.github.com>
Co-authored-by: Dzmitry Lemechko <dzmitry.lemechko@elastic.co>
[Response Ops][Task Manager] change task claiming interface to stop using observables (#196196)
Resolves https://github.com/elastic/kibana/issues/184952
Changing task claimers to return promises instead of observables. This
is a code refactor and should not have any effect on task claiming
functionality.
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Fleet] Fix agents count in agent list table and add tooltip with correct info (#197834)
Fixes https://github.com/elastic/kibana/issues/195441
Selection agent count on agent list table gets incorrect when there are
multiple hosted agents, especially if they are on inactive state. In
fact to calculate the selected number of agents we were getting hosted
agents, but without taking into account the filtering applied on the
page, i.e. we were always getting all the hosted agent (inactive too).
This caused the final calculation to be off.
In this PR I'm fixing [the
query](https://github.com/elastic/kibana/pull/197834/files#diff-9707a4b93a96749876e4cf173a0b39cd5a620e311e2652c5ed4b8670ca7e6becR309-R320)
used to get those agents to take in account the filters and I'm also
adding a small tooltip that breaks up the number of agents (selected,
total, hosted)
- Make sure to have many agents, hosted and not in different states
(inactive, unenrolled)
- To make a hosted agent inactive follow the steps explained
[here](https://github.com/elastic/kibana/issues/195441)
- Verify that the selection numbers are correct: select agents on all
pages and hover on the new tooltip shown besides the "selected agents".
This number should match the number shown on the actions dropdown
<img width="2376" alt="Screenshot 2024-10-25 at 17 00 44"
src="https://github.com/user-attachments/assets/81d2836a-f997-4ccb-a23c-3d2cfbfa62d3">
<img width="2409" alt="Screenshot 2024-10-25 at 17 00 59"
src="https://github.com/user-attachments/assets/ba21933a-f1e6-457e-8059-e87b3e29a7d1">
https://github.com/user-attachments/assets/c153c491-29a1-481c-a3e3-25bab6412963
- [ ] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [ ]
[Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html)
was added for features that require explanation or tutorials
- [ ] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Cloud Security] exclude unknown findings from compliance score calculation (#197829)
Findings from 3rd party date can have `result.evaluation: unknown`. This
leads to incorrect posture/compliance score in our flows. This PR
removes these findings from the score calculation and graphical
representation. properly introducing `unknown` in the compliance score
UX flows will be solved separately
- fixes https://github.com/elastic/security-team/issues/10913
<img width="1473" alt="Screenshot 2024-10-25 at 14 19 03"
src="https://github.com/user-attachments/assets/c69e45b0-7da1-4eb8-b83a-f895e7b7c3a4">
Delete any items that are not applicable to this PR.
- [x] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [ ]
[Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html)
was added for features that require explanation or tutorials
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
- [x] [Flaky Test
Runner](https://ci-stats.kibana.dev/trigger_flaky_test_runner/1) was
used on any tests changed
- [ ] Any UI touched in this PR is usable by keyboard only (learn more
about [keyboard accessibility](https://webaim.org/techniques/keyboard/))
- [ ] Any UI touched in this PR does not create any new axe failures
(run axe in browser:
[FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/),
[Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
- [x] If a plugin configuration key changed, check if it needs to be
allowlisted in the cloud and added to the [docker
list](https://github.com/elastic/kibana/blob/main/src/dev/build/tasks/os_packages/docker_generator/resources/base/bin/kibana-docker)
- [ ] This renders correctly on smaller devices using a responsive
layout. (You can test this [in your
browser](https://www.browserstack.com/guide/responsive-testing-on-local-server))
- [ ] This was checked for [cross-browser
compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
[Authz] OAS Descriptions for Route Authz (#197001)
Closes https://github.com/elastic/kibana/issues/191714
Update process router to generate authz descriptions based on the new
Route Security objects.
Delete any items that are not applicable to this PR.
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
---------
Co-authored-by: kibanamachine <42973632+kibanamachine@users.noreply.github.com>
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
Add tags to connector run failures indicating if it's user or framework error (#197818)
Resolves https://github.com/elastic/kibana/issues/197315
In this PR, I'm adding the following tags to the connector failure logs
so it makes it easier to filter for systematic errors.
- `connector-run-failed` for logs specific to connector run failures
- `user-error` for errors caused by the user
- `framework-error` for systematic errors
You can either use the jest test to observe the returned flags or set
your logging to JSON and make connectors fail.
kibana.yml to set logging to JSON
```
logging:
appenders:
json-layout:
type: console
layout:
type: json
root:
appenders: [json-layout]
```
[EDR Workflows] Fix Cypress tests failing on Alerts step (#197384)
Delete data when clearing security entity store (#197938)
Fixed a bug where the "Clear all entities" button in the security entity
store didn't delete data due to a missing query parameter.
FTR SAML Auth - Adjust stateful internal request header (#197994)
This PR adds the `x-elastic-internal-origin` header to the stateful
internal request headers used by FTR.
This fixes an issue that we're seeing when running deployment agnostic
tests against ESS on 9.0.0-SNAPSHOT.
[SKIP ON MKI] reporting datastream (#197958)
See details: https://github.com/elastic/kibana/issues/197955
[SKIP ON MKI] discover reporting (#197959)
See details: https://github.com/elastic/kibana/issues/197957
fix: [Stateful:Connectors:New connector page]Configuration form missing instructions and field names from announcement (#197963)
Closes: #197586
Forms, requiring user input, should have clear instructions on how to
fill them. Specific fields can have their own help (guidance) text on
how to fill them with examples.
All fields which are present in the form can be programmatically
determined, especially for the users using assistive technology to
understand what fields are present, what input is expected.
1. `aria-label` values are explicitly set for
`ConnectorConfigurationField` child components. I suspect that due to
the dynamic nature of this component, the standard mechanism does not
work properly.
<img width="1163" alt="image"
src="https://github.com/user-attachments/assets/00e1bd87-30b3-4c8f-a3d7-0c7774028a66">
[ES|QL] detect the type of `COUNT(*)` (#197914)
We weren't properly detecting the type of the expression `COUNT(*)`. Now
we are!
Before:
<img width="950" alt="Screenshot 2024-10-25 at 4 38 08 PM"
src="https://github.com/user-attachments/assets/e9bd8d78-d0c8-4069-a818-5bf3486b925b">
After:
<img width="1093" alt="Screenshot 2024-10-25 at 4 35 44 PM"
src="https://github.com/user-attachments/assets/235c63dc-7d6c-49df-9adf-e225c4550a42">
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
Co-authored-by: Stratoula Kalafateli <efstratia.kalafateli@elastic.co>
[ES|QL] remove signatures from function suggestion labels (#197842)
Showing a single acceptable function signature in the suggestions list
is confusing since it may imply that other options are not accepted.
Instead, this PR follows the Typescript tooling and simply shows the
function name in the list.

The signatures are still available in the details flyout.
<img width="981" alt="Screenshot 2024-10-25 at 8 50 01 AM"
src="https://github.com/user-attachments/assets/17ca7b55-9c88-4a42-91e0-762cfc4809b5">
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
Co-authored-by: Stratoula Kalafateli <efstratia.kalafateli@elastic.co>
[Response Ops][Task Manager] Propagate `msearch` error status code so backpressure mechanism responds correctly (#197501)
Resolves https://github.com/elastic/response-ops-team/issues/240
Creating an `MsearchError` class that preserves the status code from any
msearch errors. These errors are already piped to the managed
configuration observable that watches for and responds to ES errors from
the update by query claim strategy so I updated that filter to filter
for msearch 429 and 503 errors as well.
1. Make sure you're using the mget claim strategy
(`xpack.task_manager.claim_strategy: 'mget'`) and start ES and Kibana.
2. Inject a 429 error into an msearch response.
```
--- a/x-pack/plugins/task_manager/server/task_store.ts
+++ b/x-pack/plugins/task_manager/server/task_store.ts
@@ -571,6 +571,8 @@ export class TaskStore {
});
const { responses } = result;
+ responses[0].status = 429;
+
const versionMap = this.createVersionMap([]);
```
3. See task manager log the msearch errors and eventually reduce polling
capacity
```
[2024-10-23T15:35:59.255-04:00][ERROR][plugins.taskManager] Failed to poll for work: Unexpected status code from taskStore::msearch: 429
[2024-10-23T15:35:59.756-04:00][ERROR][plugins.taskManager] Failed to poll for work: Unexpected status code from taskStore::msearch: 429
[2024-10-23T15:36:00.257-04:00][ERROR][plugins.taskManager] Failed to poll for work: Unexpected status code from taskStore::msearch: 429
[2024-10-23T15:36:00.757-04:00][ERROR][plugins.taskManager] Failed to poll for work: Unexpected status code from taskStore::msearch: 429
...
[2024-10-23T15:36:06.267-04:00][WARN ][plugins.taskManager] Poll interval configuration is temporarily increased after Elasticsearch returned 19 "too many request" and/or "execute [inline] script" error(s).
[2024-10-23T15:36:06.268-04:00][WARN ][plugins.taskManager] Capacity configuration is temporarily reduced after Elasticsearch returned 19 "too many request" and/or "execute [inline] script" error(s).
```
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Stateful sidenav] Fix dashboard listing breadcrumbs (#197986)
[Onboarding] Check for user privileges before creating an API key (#197964)
Resolves https://github.com/elastic/kibana/issues/192983
Check for user privileges before creating an API key
<img width="1413" alt="Screenshot 2024-10-28 at 10 28 58"
src="https://github.com/user-attachments/assets/aa54ce74-98ac-43f0-b422-ab3d895c97ab">
[Fleet] Couple agent and package policies spaces (#197487)
Consolidate Rule schemas (#195613)
Towards: #172513
This PR removes `RawRule` type from `alerting/server/type` and
`RuleAttributes` schema/types.
And uses the `RawRule` that is used for ModelVersions instead of them.
---------
Co-authored-by: kibanamachine <42973632+kibanamachine@users.noreply.github.com>
Improve header button spacing (#197896)
Closes #197873
- Fix spacing between 'Give feedback' and AI button.
- While in the neighborhood, I noticed the search button had some extra
padding, so I fixed that quick too.
- Lastly, I pushed the project switcher to the far right. This is only
used for local development of Serverless and was otherwise appearing
between production buttons.
<img width="420"
src="https://github.com/user-attachments/assets/f5abe1af-1762-4658-8040-d802b9752667"
/>
<img width="420"
src="https://github.com/user-attachments/assets/04288ff3-6012-4518-866f-0dea4ad62401"
/>
<img width="420"
src="https://github.com/user-attachments/assets/ef2e0eff-d4f4-4ceb-bbf8-c39d2e3e9949"
/>
To test, you'll need to run this in serverless mode where the 'Give
feedback' button appears.
You can force it on by setting the following line equal to `true`.
https://github.com/elastic/kibana/blob/ae9c0d385015f3068a04af46678e18e2f00b519a/src/plugins/guided_onboarding/public/plugin.tsx#L50
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Security Solution][Detection Engine] fixes preview logs issue when switching between rules (#197098)
- addresses https://github.com/elastic/kibana/issues/196616
[Lens] fix showing points on line by default (#197828)
Fix the missing style to show points in line charts. Line charts should
show data points whenever the distance between points is larger than
40px.
[Fleet] Fix flaky agentless test (#197951)
Fixes https://github.com/elastic/kibana/issues/189038
Attempt to fix [this flaky test
](https://buildkite.com/elastic/kibana-on-merge/builds/53472#0192c57d-51ca-4b9b-a934-dc13b0b9b7ca)
failing with
```
Timed out in waitForNextUpdate after 1000ms.
--
|
| at waitForNextUpdate (node_modules/@testing-library/react-hooks/lib/core/asyncUtils.js:96:13)
```
I'm adding a longer timeout hoping to resolve this issue. There is no
way to run jest tests with flaky test runner so I'm not sure how to
verify that the flakiness is really gone.
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
Serverless tests - enable dot-prefixed index validation (#197141)
This PR enables Elasticsearch dot-prefixed index validation for
serverless tests.
[ObsUx][Infra] Remove no longer used feature flags for GA features (#197684)
Closes #197612
This PR removes the feature flags
(`observability:enableInfrastructureHostsView` and
`enableInfrastructureContainerAssetView` ) for host and container views
Feature settings under `Infrastructure > Settings` (ignore the profiling
one)
| Before | After |
| ------ | ----- |
|
|

|
The feature flags should not appear in the settings
The Host menu item should be visible
The Container asset views should be always enabled and visible (without
an option to disable them)
The Host asset views should be always enabled and visible (without an
option to disable them)
https://github.com/user-attachments/assets/a4d574d0-2669-4f96-88a4-a40c2f5023c2
do not set full screen mode on ExitFullScreenButton re-render (#198012)
https://github.com/elastic/kibana/pull/194892 is refactoring
[DashboardRenderer](https://github.com/elastic/kibana/blob/3391344e8dc8377d359b918521b6c48838cde8ae/src/plugins/dashboard/public/dashboard_container/external_api/dashboard_renderer.tsx)
component to replace Dashboard Embeddable with a plain old javascript
object. Dashboard Embeddable rendered its contents in a new react tree.
The new implementation does not. Since the new implementation does not
render the dashboard in a new react tree, any re-render in
`DashboardViewport` parent components causes `ExitFullScreenButton` to
re-render. In its current form, re-rendering `ExitFullScreenButton`
calls `onExit`, which causing dashboard to exit full screen mode.
This PR makes use of `useCallback` to fix the issue where re-rending
`ExitFullScreenButton` calls `onExit`.
1) Open dashboard that ships with sample web logs data set
2) switch to view mode
3) click "Full screen" button
4) Maximize a panel. Verify dashboard stays in full screen mode.
[ci] Run linting before tests (#197310)
Linting is a frequent source of build failures. By increasing the cpu
count we can run this check before starting our highly-parallel tests
without impacting total build time.
Fix documentation for session lifespan default (#198065)
This pull request includes an update to the
`docs/settings/security-settings.asciidoc` file to clarify the default
session lifespan settings for different installation environments.
Documentation update:
*
[`docs/settings/security-settings.asciidoc`](diffhunk://#diff-97a4c4e3696b33b246f55ddd794608530b693f0a7a66ae1361a32b67c7461523L204-R204):
Clarified that the default session lifespan is 30 days for on-prem
installations and 24 hours for Elastic Cloud installations.
[FTR][Ownership] Assign aiops, custom branding, etc (#197468)
Assign test files to small number of reviewers
Assigned custom_branding due to
https://github.com/elastic/kibana/blob/main/x-pack/plugins/custom_branding/kibana.jsonc#L4
Assigned response_ops_docs due to the name
Assigned monitoring due to
https://github.com/elastic/kibana/blob/main/x-pack/plugins/monitoring/kibana.jsonc#L4
Assigned so managment due to
https://github.com/elastic/kibana/blob/main/src/plugins/saved_objects_management/kibana.jsonc#L4
Assigned aiops due to
https://github.com/elastic/kibana/blob/main/x-pack/plugins/aiops/kibana.jsonc#L4
Assigned banners_functional due to Pierre being all over the git blame.
:lol:
Assigned x-pack/test/screenshot_creation due to
https://github.com/elastic/kibana/pull/197468#discussion_r1817460031
Contributes to: https://github.com/elastic/kibana/issues/194817
[Security GenAI][BUG] KB index entry created via pdf upload does not give the right response (#198020)
These changes fix the issue with the wrong response of the AI Assistant
using knowledge base tool and index entry generated from a PDF file.
The issue happens because we are using the first chunk of uploaded PDF
document as a context that we pass to LLM instead of using inner hits
chunks which are actual parts of the document relevant to the questions.
Here is [the blog
post](https://www.elastic.co/search-labs/blog/semantic-text-with-amazon-bedrock)
that talks about the strategy of using inner hits to get the most
relevant documents. (see `Strategy 1: API Calls` section)
1. Navigate to Integrations page
2. Select "Upload a file"
3. Select and upload a PDF file
4. Press Import button
5. Switch to Advanced tab
6. Fill in "Index name"
7. Add additional field > Add semantic text field > Fill in form
* Field: `attachment.content`
* Copy to field: `content`
* Inference endpoint: `elser_model_2`
8. Press Add button
9. Press Import button
1. Navigate to AI Assistant's Knowledge Base page
2. New > Index
3. Fill in "New index entry" form (below are main fields)
* Name: `[add entry name]`
* Index: `[select index name created during uploading a PDF file]`
* Field: `content`
4. Press Save button
Enable knowledge base feature via
```
xpack.securitySolution.enableExperimental:
- 'assistantKnowledgeBaseByDefault'
```
**PDF document**:
[Elastic Global Threat Report
2024](https://github.com/user-attachments/files/17544720/elastic-global-threat-report-2024.pdf)
**KB Index entry**:
Data Description: "Use this tool to answer questions about the Elastic
Global Threat Report (GTR) 2024"
Query Instruction: "Key terms to return data relevant to the Elastic
Global Threat Report (GTR) 2024"
**Questions**:
1. Who are the authors of the GTR 2024?
2. What is the forecast for the coming year in GTR 2024?
3. What are top 10 Process Injection by rules in Windows endpoints in
GTR 2024?
4. What is the most widely adopted cloud service provider this year
according to GTR 2024?
6. Give a brief conclusion of the GTR 2024
**Current behaviour**:
<img width="656" alt="Screenshot 2024-10-28 at 16 43 48"
src="https://github.com/user-attachments/assets/90615356-8807-4786-b58d-ca28c83aaec9">
**Fixed behaviour**:
<img width="655" alt="Screenshot 2024-10-28 at 16 44 47"
src="https://github.com/user-attachments/assets/9ebefbcc-20c2-4c79-98f3-11fa6acf3da6">
Improves pattern matching for data telemetry (#197876)
Addresses concerns with Regex matching.
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Synthetics] Refactor delete route !! (#195387)
Fixes https://github.com/elastic/kibana/issues/193790 !!
Refactor delete route !!
Make sure to send delete response in bulk to synthetics service !!
[Fleet] Prevent hosted policies space change (#198043)
Revert "[Canvas] Update kbn/flot to remove table.replace() issue" (#198067)
Fixes #197998
Reverts elastic/kibana#195643
skip failing test suite (#181466)
[Global Search] Instantly set `isLoading=true` when search value changes (#197750)
Close https://github.com/elastic/kibana/issues/77059
This PR solves the bug by setting the `isLoading` flag outside of the
block of debounced code whenever the search term changes.
This also makes a few slight cleanups to `search_bar.tsx`, which is
quite large. I avoided doing any serious cleanups that would make the
diff hard to read or detract from the fix.
skip flaky suite (#178404)
skip flaky suite (#197335)
skip flaky suite (#189038)
skip flaky suite (#192126)
skip flaky suite (#197765)
skip flaky suite (#189739)
skip flaky suite (#196766)
skip flaky suite (#174661)
Added redirect option after Entity CSV upload (#197937)
Added a redirect button to view Entities after a successful Asset
Criticality CSV file upload process
Additionally, made some small changes to the copy for the Entity Store
management workflows
<img width="1490" alt="Screenshot 2024-10-27 at 9 49 17 PM"
src="https://github.com/user-attachments/assets/77b587b7-8300-40ae-adc2-5119aa5f39ab">
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
Update dependency msw to ^2.4.12 (main) (#198060)
This PR contains the following updates:
| Package | Type | Update | Change | Pending |
|---|---|---|---|---|
| [msw](https://mswjs.io) ([source](https://togithub.com/mswjs/msw)) |
devDependencies | patch | [`^2.4.11` ->
`^2.4.12`](https://renovatebot.com/diffs/npm/msw/2.4.11/2.4.12) |
`2.5.2` (+3) |
---
<details>
<summary>mswjs/msw (msw)</summary>
[Compare
Source](https://togithub.com/mswjs/msw/compare/v2.4.11...v2.4.12)
- **node:** preserve headers instanceof when recording raw headers
([#​2321](https://togithub.com/mswjs/msw/issues/2321))
([`a58a300`](https://togithub.com/mswjs/msw/commit/a58a300687a48e13c0268403a71183cf7825f748))
[@​paoloricciuti](https://togithub.com/paoloricciuti)
</details>
---
📅 **Schedule**: Branch creation - At any time (no schedule defined),
Automerge - At any time (no schedule defined).
🚦 **Automerge**: Disabled by config. Please merge this manually once you
are satisfied.
♻ **Rebasing**: Whenever PR becomes conflicted, or you tick the
rebase/retry checkbox.
🔕 **Ignore**: Close this PR and you won't be reminded about this update
again.
---
- [ ] <!-- rebase-check -->If you want to rebase/retry this PR, check
this box
---
This PR has been generated by [Renovate
Bot](https://togithub.com/renovatebot/renovate).
<!--renovate-debug:eyJjcmVhdGVkSW5WZXIiOiIzNy40MjUuMSIsInVwZGF0ZWRJblZlciI6IjM3LjQyNS4xIiwidGFyZ2V0QnJhbmNoIjoibWFpbiIsImxhYmVscyI6WyJUZWFtOkNsb3VkIFNlY3VyaXR5IiwiYmFja3BvcnQ6c2tpcCIsInJlbGVhc2Vfbm90ZTpza2lwIl19-->
Co-authored-by: elastic-renovate-prod[bot] <174716857+elastic-renovate-prod[bot]@users.noreply.github.com>
[CI] Disable UpdateCLI workflow on forks (#196624)
The UpdateCLI workflow is running against forks when it shouldn't be:
https://github.com/Ikuni17/kibana/actions/runs/11359905941
Fix Dev Container KBN_DIR (#195810)
In #193488, `KBN_DIR` was changed to be a dynamic variable. It wasn't
being properly propagated through the build process in the Dockerfile
and the full path to `env.sh` wasn't being set. This passes the
directory as a build `ARG` as well to fix the path.
[api-docs] 2024-10-29 Daily api_docs build (#198103)
Generated by
https://buildkite.com/elastic/kibana-api-docs-daily/builds/875
[Security Solution][Hotfix] Avoid blocking prebuilt rule upgrade upon conflicts with disabled feature flag (#198106)
It turned out some of the update rule buttons are disabled. This is a side effect of the functionality not fully hidden under a feature flag. This PR hides prebuilt rule customisation functionality disabling update rule buttons under `prebuiltRulesCustomizationEnabled` feature flag.

<img width="1719" alt="image" src="https://github.com/user-attachments/assets/349223dc-dda5-46fb-832f-d7097a81580e">
<img width="1721" alt="image" src="https://github.com/user-attachments/assets/a28512f6-e605-460e-884d-571ab408a7d9">
[Infra] Fix anomalies flyout navigation failing test (#197999)
Closes #192882
The issue was that the url was checked too early which resulted in
checking the locator url instead of the page url after navigating so I
added a check for loading before the URL check and this solved the
issue.
https://buildkite.com/elastic/kibana-flaky-test-suite-runner/builds/7284
[ObsUx][Infra] Unskip and try to fix hosts view test (#197861)
Closes #191806
The parts of the unskipped test were fixed here - the only case I
couldn't find the reason for failing after unskipping it is `should have
an option to open the chart in lens` - for some reason, the whole menu
is gone when checking the CI and I couldn't reproduce that so this will
be the only skipped part so we can at least have all the other `Hosts
view` tests
[Cloud Security] Fix flaky metering tests
[Observability Onboarding] Set tech preview badges correctly (#197831)
As discussed, adjust the first onboarding page:
* Remove tech preview labels from EA flows
* Change wording
<img width="857" alt="Screenshot 2024-10-25 at 15 23 47"
src="https://github.com/user-attachments/assets/ceffbe90-019d-4fa8-ab6f-16cbf0aaf3d4">
<img width="814" alt="Screenshot 2024-10-25 at 15 23 59"
src="https://github.com/user-attachments/assets/4f5cf657-6fd2-479f-aa92-9460bc2ecfef">
[EDR Workflows] Skip Osquery test in MKI (#198117)
[EDR Workflows] Improve on unavailable shard exception flakiness in cypress (#197864)
The cypress task `cy.task('indexEndpointHosts')` sometimes throws
`no_shard_available_action_exception`, when transforms are stopped. This
looks like a temporary issue, and in other tests it is simply retried.
This PR adds the retry logic for this type of error, and unskips some
tests.
closes #194135
closes #191914
Delete any items that are not applicable to this PR.
- [x] [Flaky Test
Runner](https://ci-stats.kibana.dev/trigger_flaky_test_runner/1) was
used on any tests changed
[Cloud Security] add vulnerabilties data set to filter for links from CNVM dashboard (#197648)
- fixes https://github.com/elastic/security-team/issues/10915
[Entity Analytics] [Entity Store] Telemetry (#196880)
This PR adds telemetry for the Entity Store.
Client side tracks UI enablement actions, whilst Kibana side tracks
execution time of the store initialisation process and execution time of
the enrich policy task.
Finally we also track number of entities in the store
Update docker.elastic.co/wolfi/chainguard-base:latest Docker digest to 1815394 (main) (#198099)
This PR contains the following updates:
| Package | Update | Change |
|---|---|---|
| docker.elastic.co/wolfi/chainguard-base | digest | `de4d5b0` ->
`1815394` |
---
📅 **Schedule**: Branch creation - At any time (no schedule defined),
Automerge - At any time (no schedule defined).
🚦 **Automerge**: Disabled by config. Please merge this manually once you
are satisfied.
♻ **Rebasing**: Whenever PR becomes conflicted, or you tick the
rebase/retry checkbox.
🔕 **Ignore**: Close this PR and you won't be reminded about this update
again.
---
- [ ] <!-- rebase-check -->If you want to rebase/retry this PR, check
this box
---
This PR has been generated by [Renovate
Bot](https://togithub.com/renovatebot/renovate).
<!--renovate-debug:eyJjcmVhdGVkSW5WZXIiOiIzNy40MjUuMSIsInVwZGF0ZWRJblZlciI6IjM3LjQyNS4xIiwidGFyZ2V0QnJhbmNoIjoibWFpbiIsImxhYmVscyI6WyJUZWFtOk9wZXJhdGlvbnMiLCJyZWxlYXNlX25vdGU6c2tpcCJdfQ==-->
Co-authored-by: elastic-renovate-prod[bot] <174716857+elastic-renovate-prod[bot]@users.noreply.github.com>
Update dependency @launchdarkly/node-server-sdk to ^9.6.1 (main) (#196897)
[ML] Data Frame Analytics: removing scss overrides for exploration pages (#197724)
Related meta issue: https://github.com/elastic/kibana/issues/140695
Regression model evaluation before:
<img width="1455" alt="image"
src="https://github.com/user-attachments/assets/cfdb794d-4576-4c10-96c1-0b3856857cdd">
After:
<img width="1455" alt="image"
src="https://github.com/user-attachments/assets/4c2bbdf3-85ef-489e-bc3a-1281d3531328">
Classification evaluation before:
<img width="1474" alt="image"
src="https://github.com/user-attachments/assets/e565cac3-8c1d-4e4f-8cac-7ea8abf4358d">
After switching fully to flex layout as we no longer support IE11 and
all the workarounds were no longer needed (Note it's all left aligned
now):
<img width="1467" alt="image"
src="https://github.com/user-attachments/assets/280ea446-17fc-4622-a925-57ef6c01cd89">
Delete any items that are not applicable to this PR.
- [ ] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [ ]
[Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html)
was added for features that require explanation or tutorials
- [ ] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
- [ ] [Flaky Test
Runner](https://ci-stats.kibana.dev/trigger_flaky_test_runner/1) was
used on any tests changed
- [ ] Any UI touched in this PR is usable by keyboard only (learn more
about [keyboard accessibility](https://webaim.org/techniques/keyboard/))
- [ ] Any UI touched in this PR does not create any new axe failures
(run axe in browser:
[FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/),
[Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
- [ ] If a plugin configuration key changed, check if it needs to be
allowlisted in the cloud and added to the [docker
list](https://github.com/elastic/kibana/blob/main/src/dev/build/tasks/os_packages/docker_generator/resources/base/bin/kibana-docker)
- [ ] This renders correctly on smaller devices using a responsive
layout. (You can test this [in your
browser](https://www.browserstack.com/guide/responsive-testing-on-local-server))
- [ ] This was checked for [cross-browser
compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[ES|QL] separate `KEEP`, `DROP`, and `SORT` autocomplete routines (#197744)
This PR begins the refactor described in
https://github.com/elastic/kibana/issues/195418.
The autocomplete engine now delegates to command-specific routines
attached to the command definitions for `KEEP`, `DROP`, and `SORT`.
The naming of `getFieldsFor` has been broadened to `getColumnsFor`
because the response from Elasticsearch can contain variables as well as
fields, depending on the query that is used to fetch the columns.
No user-facing behavior should have changed.
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[CI] Fix project build & deploy job (#196562)
In #195581 we've added the option to deploy through the clickable
triggers. But in it's current state, it's broken in several aspects.
(1) It's not starting on click. Triggers was resulting in a 422 on
Buildkite's side, and after digging more into it, this was the error:
<img width="1019" alt="Screenshot 2024-10-16 at 16 53 13"
src="https://github.com/user-attachments/assets/f602dde9-2cc4-474f-b432-a3d4f9d5ae91">
Apparently, building PRs needs to be enabled on jobs that want to be
triggered through the PR bot.
(2) It is set up to run regardless of the labels
(3) There's no feedback on runs
This PR:
- enables buildability in the pipeline's config
- exits early if deploy labels are missing
- adds a comment on the PR if a deploy job is started or finished
- removes the kibana build step, it's not needed, as we have a step to
build the docker image
TODO:
- [x] Add feedback about a started job (either through a non-required
check, or a github comment)
- [x] Early exit if a label is missing
There are several other builds started right now, because the logic that
would trigger a build on changing a draft to ready. To be fixed in
https://github.com/elastic/buildkite-pr-bot/issues/78
Tested after manually by enabling the option on the UI, and triggering
through the checkbox:
https://buildkite.com/elastic/kibana-deploy-project-from-pr/builds/23
Expand README (#197880)
Adds a bit more general background, intro to concepts, and guidelines
about what to use FF for and what not to
Delete any items that are not applicable to this PR.
- [ ] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [ ]
[Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html)
was added for features that require explanation or tutorials
- [ ] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
- [ ] [Flaky Test
Runner](https://ci-stats.kibana.dev/trigger_flaky_test_runner/1) was
used on any tests changed
- [ ] Any UI touched in this PR is usable by keyboard only (learn more
about [keyboard accessibility](https://webaim.org/techniques/keyboard/))
- [ ] Any UI touched in this PR does not create any new axe failures
(run axe in browser:
[FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/),
[Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
- [ ] If a plugin configuration key changed, check if it needs to be
allowlisted in the cloud and added to the [docker
list](https://github.com/elastic/kibana/blob/main/src/dev/build/tasks/os_packages/docker_generator/resources/base/bin/kibana-docker)
- [ ] This renders correctly on smaller devices using a responsive
layout. (You can test this [in your
browser](https://www.browserstack.com/guide/responsive-testing-on-local-server))
- [ ] This was checked for [cross-browser
compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
Delete this section if it is not applicable to this PR.
Before closing this PR, invite QA, stakeholders, and other developers to
identify risks that should be tested prior to the change/feature
release.
When forming the risk matrix, consider some of the following examples
and how they may potentially impact the change:
| Risk | Probability | Severity | Mitigation/Notes |
|---------------------------|-------------|----------|-------------------------|
| Multiple Spaces—unexpected behavior in non-default Kibana Space.
| Low | High | Integration tests will verify that all features are still
supported in non-default Kibana Space and when user switches between
spaces. |
| Multiple nodes—Elasticsearch polling might have race conditions
when multiple Kibana nodes are polling for the same tasks. | High | Low
| Tasks are idempotent, so executing them multiple times will not result
in logical error, but will degrade performance. To test for this case we
add plenty of unit tests around this logic and document manual testing
procedure. |
| Code should gracefully handle cases when feature X or plugin Y are
disabled. | Medium | High | Unit tests will verify that any feature flag
or plugin combination still results in our service operational. |
| [See more potential risk
examples](https://github.com/elastic/kibana/blob/main/RISK_MATRIX.mdx) |
- [ ] This was checked for breaking API changes and was [labeled
appropriately](https://www.elastic.co/guide/en/kibana/master/contributing.html#_add_your_labels)
- [ ] This will appear in the **Release Notes** and follow the
[guidelines](https://www.elastic.co/guide/en/kibana/master/contributing.html#kibana-release-notes-process)
---------
Co-authored-by: Alejandro Fernández Haro <alejandro.haro@elastic.co>
Fix Typo: Change 'dashaboard' to 'dashboard' on APM-service Dashboards page #195773 (#196969)
**Title:** Fix Typo: Change 'dashaboard' to 'dashboard' on APM-service
Dashboards page
**Description:**
This PR fixes a typo on the "Dashboards" page for APM-service. The typo
"dashaboard" has been corrected to "dashboard" to ensure proper
functionality and readability.
closes #195773
**Changes Made:**
- Corrected the typo in the text "To get started, add your dashaboard"
to "To get started, add your dashboard."
**Testing:**
- Verified the change on the Dashboards page for APM-service.
- Ensured no other instances of the typo exist in the codebase.
**Release note:**
Fixes a typo on the "Dashboards" page for APM-service, changing
'dashaboard' to 'dashboard'.
**Additional Notes:**
No additional notes.
Summarize your PR. If it involves visual changes include a screenshot or
gif.
Delete any items that are not applicable to this PR.
- [x] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [ ]
[Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html)
was added for features that require explanation or tutorials
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
- [ ] [Flaky Test
Runner](https://ci-stats.kibana.dev/trigger_flaky_test_runner/1) was
used on any tests changed
- [x] Any UI touched in this PR is usable by keyboard only (learn more
about [keyboard accessibility](https://webaim.org/techniques/keyboard/))
- [x] Any UI touched in this PR does not create any new axe failures
(run axe in browser:
[FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/),
[Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
- [ ] If a plugin configuration key changed, check if it needs to be
allowlisted in the cloud and added to the [docker
list](https://github.com/elastic/kibana/blob/main/src/dev/build/tasks/os_packages/docker_generator/resources/base/bin/kibana-docker)
- [x] This renders correctly on smaller devices using a responsive
layout. (You can test this [in your
browser](https://www.browserstack.com/guide/responsive-testing-on-local-server))
- [x] This was checked for [cross-browser
compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
Delete this section if it is not applicable to this PR.
Before closing this PR, invite QA, stakeholders, and other developers to
identify risks that should be tested prior to the change/feature
release.
When forming the risk matrix, consider some of the following examples
and how they may potentially impact the change:
| Risk | Probability | Severity | Mitigation/Notes |
|---------------------------|-------------|----------|-------------------------|
| Multiple Spaces—unexpected behavior in non-default Kibana Space.
| Low | High | Integration tests will verify that all features are still
supported in non-default Kibana Space and when user switches between
spaces. |
| Multiple nodes—Elasticsearch polling might have race conditions
when multiple Kibana nodes are polling for the same tasks. | High | Low
| Tasks are idempotent, so executing them multiple times will not result
in logical error, but will degrade performance. To test for this case we
add plenty of unit tests around this logic and document manual testing
procedure. |
| Code should gracefully handle cases when feature X or plugin Y are
disabled. | Medium | High | Unit tests will verify that any feature flag
or plugin combination still results in our service operational. |
| [See more potential risk
examples](https://github.com/elastic/kibana/blob/main/RISK_MATRIX.mdx) |
- [ ] This was checked for breaking API changes and was [labeled
appropriately](https://www.elastic.co/guide/en/kibana/master/contributing.html#_add_your_labels)
- [ ] This will appear in the **Release Notes** and follow the
[guidelines](https://www.elastic.co/guide/en/kibana/master/contributing.html#kibana-release-notes-process)
---------
Co-authored-by: Cauê Marcondes <55978943+cauemarcondes@users.noreply.github.com>
Co-authored-by: Nathan L Smith <nathan.smith@elastic.co>
Co-authored-by: jennypavlova <dzheni.pavlova@elastic.co>
[Response Ops][Actions] Remove deprecated HTTP APIs (#197510)
Resolves https://github.com/elastic/kibana/issues/90382
Removes legacy action APIs for 9.0 and updates all tests that still used
the legacy APIs to use the current APIs. Also did some renaming of
action -> connector in the files I had to touch.
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Fleet] Prevent duplication of managed policy !! (#197575)
Fixes https://github.com/elastic/kibana/issues/194149
Prevent duplication of managed policy !!
<img width="1594" alt="image"
src="https://github.com/user-attachments/assets/f386a287-4f9e-4307-ba84-98f3ea807ef9">
[Security Solution][Notes] - switch the securitySolutionNotesEnables feature flag to securitySolutionNotesDisabled (#196778)
This PR switches the `securitySolutionNotesEnabled` to
`securitySolutionNotesDisabled` (with a `false` value by default) to
enable the new Notes functionality in `8.16`.
Customers can set the new `securitySolutionNotesDisabled` feature flag
to true in their environment if they want to go back to the old notes
system.
The PR also fixes a tiny bug with the badge showing the number of notes
in the Timeline Notes tab. The new system was not taking into account a
timeline description, so if the timeline had a description the number of
notes was always 1 lower than the actual number of notes displayed
below. This issue was highlighted by a Cypress test!
The goal is to remove the old system entirely within a few releases
(maybe `8.18` or `9.0`).
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
https://github.com/elastic/kibana/issues/189879
[ci] Fix cloud deployments (#198086)
Our build scripts are relying on a step that was removed in
https://github.com/elastic/elasticsearch/pull/115357. The image that was
produced by this script is eventually consumed by cloud deployments from
pull requests.
This updates our scripts to use the cloud-ess variant instead. There
should not be any functional difference.
We'll need the image to go through our promotion pipeline to be tested
via label.
https://buildkite.com/elastic/kibana-elasticsearch-snapshot-build/builds/4673
[ci] Use es snapshot cache on miscellaneous steps 2 (#198078)
Adds the remaining steps missing snapshot loading from cache that I
missed on the first loop.
[Observability] Update breadcrumbs for observability project based navigation (#196785)
~⚠️ I'm still putting out some fires with tests, but this is ready to
start being reviewed.~
A continuation of https://github.com/elastic/kibana/pull/196169 for
Observability (please read that PR description first).
Related: https://github.com/elastic/kibana/issues/192050
There are essentially three types of breadcrumbs - serverless (which is
project style), stateful project style (set through spaces settings),
and classic style (the old breadcrumbs we've seen for years). Whilst
serverless and stateful project style both use the project based style
the navigation trees are slightly different, so the breadcrumbs results
are not identical [when they derive the "nav
crumbs"](https://github.com/elastic/kibana/blob/9577aa980dd1565fba05e34292fb5c0bba692889/packages/core/chrome/core-chrome-browser-internal/src/project_navigation/breadcrumbs.tsx#L55).
Here "project style" will refer to serverless and stateful project
style.
In these changes I've, for the most part, tried to refactor things so
Observability solutions route their breadcrumbs through the
observability-shared `useBreadcrumbs` hook, this way the logic around
project style, adding an Observability crumb in classic etc is
consolidated in one place.
[For several solutions `absolute` breadcrumbs are being
used](https://github.com/elastic/kibana/blob/9577aa980dd1565fba05e34292fb5c0bba692889/packages/core/chrome/core-chrome-browser-internal/src/project_navigation/breadcrumbs.tsx#L46),
and this means we'll roughly have the same breadcrumbs across the 3
experience…
crespocarlos
added a commit
to crespocarlos/kibana
that referenced
this pull request
Nov 4, 2024
Create entity_client functions
Create entity_client functions
Fix entityLatest flatten object
Fix redirection to service overview
Fix redirection to service overview
Add tests
Add tests
Refactoring and tests
Clean up
[CI] Auto-commit changed files from 'node scripts/yarn_deduplicate'
fix after rebase
Fix build
[Dataset Quality]Fix elastic doc test (#197835)
Found a bug while backporting another PR.
The elastic docs in main always refer to master, but once a release is
cut, it check for specific version in the URL.
hence updated the test
P.S: This does not need backport to 8.x as this has already been fixed
in 8.x
[FTR][Ownership] Assign visualize, etc (#197664)
Assign test files to small number of reviewers
Assigned visualize due to the name
Assigned functional_execution_context due to
https://github.com/elastic/kibana/blob/main/x-pack/test/functional_execution_context/plugins/alerts/kibana.jsonc#L4
Assigned kubernetes_security per
https://github.com/elastic/kibana/blob/main/x-pack/plugins/kubernetes_security/kibana.jsonc#L4
Assigned licensing_plugin due to
https://github.com/elastic/kibana/blob/main/x-pack/plugins/licensing/kibana.jsonc#L4
Assigned rule_registry due to
https://github.com/elastic/kibana/blob/main/x-pack/plugins/rule_registry/kibana.jsonc#L4-L5
Assigned usage_collection due to
https://github.com/elastic/kibana/blob/main/api_docs/usage_collection.mdx#L18
- It says `Contact @elastic/kibana-core for questions regarding this
plugin.`
Assigned observability_onboarding_api_integration due to
https://github.com/elastic/kibana/blob/main/api_docs/observability_onboarding.mdx#L18
- It says `Contact @elastic/obs-ux-logs-team for questions regarding
this plugin.`
Contributes to: https://github.com/elastic/kibana/issues/194817
[React@18 failing tests] Dataset quality handles user privileges (#197830)
[Security Solution] Add data source editable component (#196948)
**Partially addresses:** https://github.com/elastic/kibana/issues/171520
This PR adds is built on top of https://github.com/elastic/kibana/pull/193828 and add a Data Source editable component for final edit side of Three Way Diff tab of the upgrade prebuilt rule workflow.
https://github.com/elastic/kibana/issues/171520 required adding editable components for each field diffable rule field. It imposes some difficulties since it's quite problematic to reuse existing especially complex components like Data Source from Define Rule step component.
This PR make little refactoring to the Define Rule step component to make it simpler and make it easier to reuse Data Source related code chunks scattered in Define Rule step component. You may notice some copy-paste chunks of Data Source editable component in the PR. At this stage it's the simplest way to proceed to avoid huge refactoring and potential new bugs. Taking into account deadlines for the task it looks like a good trade off. There is a plan to work on improvements for rules creation/editing forms later on.
search: move getting started to footer (#197849)
Moved the `Getting Started` link to the footer

[OpenAPI][DOCS] Add descriptions, examples, responses for role APIs (#195527)
Co-authored-by: Elena Shostak <165678770+elena-shostak@users.noreply.github.com>
[Security Solution] Unskips Timeline Cypress tests (#195721)
Fixes below Flaky tests issues :
- [x] https://github.com/elastic/kibana/issues/180688
- [x] https://github.com/elastic/kibana/issues/176945
- [x] https://github.com/elastic/kibana/issues/175180
- [x] https://github.com/elastic/kibana/issues/181466
- [x] https://github.com/elastic/kibana/issues/182021
- [x] https://github.com/elastic/kibana/issues/183085
- [x] https://github.com/elastic/kibana/issues/175180
---------
Co-authored-by: Michael Olorunnisola <michael.olorunnisola@elastic.co>
[ci] Use es snapshot cache on miscellaneous steps, adjust schedule (#197294)
The schedule adjustment is due to 7.17 verification taking longer than
other branches. Currently, we only rebuild once when main is updated.
This is a stopgap until a cache-only update can be introduced to avoid
continuous image rebuilds.
[SR] Add tooltips for disabled fields on managed SLM repository and policy (#196565)
Closes
https://github.com/elastic/kibana/issues/173124#issuecomment-2352968634
by adding tooltips details when hovering the disabled SLM repository or
policy fields.
**SLM managed repository**

**SLM managed policy**

- [x] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [x] Any UI touched in this PR does not create any new axe failures
(run axe in browser:
[FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/),
[Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
- [x] This renders correctly on smaller devices using a responsive
layout. (You can test this [in your
browser](https://www.browserstack.com/guide/responsive-testing-on-local-server))
- [x] This was checked for [cross-browser
compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
- [x] This was checked for breaking API changes and was [labeled
appropriately](https://www.elastic.co/guide/en/kibana/master/contributing.html#_add_your_labels)
- [x] This will appear in the **Release Notes** and follow the
[guidelines](https://www.elastic.co/guide/en/kibana/master/contributing.html#kibana-release-notes-process)
---------
Co-authored-by: Elena Stoeva <59341489+ElenaStoeva@users.noreply.github.com>
[Security GenAI] When indices referenced in KB index entries are deleted from OUTSIDE the AI Assistant KB UI, there is not indication to the user (#197156) (#197722)
Bug https://github.com/elastic/kibana/issues/197156
This is a UI part of the bug that warns a user about missing indices
used in knowledge base entries.
1. Add an index entry that uses existing index
2. Remove that index
3. Go back to knowledge base entries page
4. You should see warning icon next to the name of the index entry which
uses removed index. Also, when you edit that entry you will see `Index
doesn't exist` error next to the `Index` field in the flyout
<img width="1458" alt="Screenshot 2024-10-24 at 19 54 36"
src="https://github.com/user-attachments/assets/7d4468f9-fada-4416-9480-99bfca3de220">
<img width="615" alt="Screenshot 2024-10-24 at 19 54 52"
src="https://github.com/user-attachments/assets/fd9bbe80-0a3c-40b8-909a-93f8082e69eb">
Delete any items that are not applicable to this PR.
- [x] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
[Security Solution][Endpoint] Ensure that DS indices for response actions are created prior to sending action to Endpoint (#196953)
PR adds changes to Security Solution so that DOT indices (restricted in
Serverless) are created in Kibana prior to Elastic Defend (Endpoint)
attempting to stream documents to these indices. The indices that are
now created in kibana are:
- `.logs-endpoint.diagnostic.collection-<namespace_from_policy>`
- `.logs-endpoint.action.responses-<namespace_from_policy>`
- `.logs-endpoint.heartbeat-<namespace_from_policy>` _(⚠️ created only
in serverless only)_
- Added support for the following two server-side extension points:
- `packagePolicyPostUpdate` : callbacks invoked after an integration
policy has been updated successfully
- `agentPolicyPostUpdate` : callbacks invoked after an agent policy has
been updated successfully
- Logic was added to the following Fleet server-side extension points
that checks if the necessary indices exist and if not, it creates them:
- After creating an Elastic Defend integration policy
- After updating an Elastic Defend integration policy
- After updating a Fleet Agent Policy that includes Elastic Defend
integration policy
Mark connector param validation failures as user errors (#197812)
Resolves https://github.com/elastic/response-ops-team/issues/255
In this PR, I'm changing the type of error thrown when connector
parameter validation fails so it indicates it's a user type of error.
This will allow us to exclude these errors from our serverless
monitoring given the users define the parameters the connectors receive
when they run. Mainly via alerting rule mustache templates, which are
easy to render empty strings and such.
[Security Solution][Notes] - fix createdBy filter for notes management page (#197706)
[Search][Fix] Index Details: poll mappings (#197885)
[Security GenAI] When a "global" Knowledge Base entry is updated to "private", a duplicate "private" entry gets created and the global entry remains unchanged (#197157) (#197516)
Original ticket describing the BUG:
https://github.com/elastic/kibana/issues/197157
These changes fix two issues:
1. Updating an entry from Global to Private duplicates it. After
discussing with the team we decided that this is an expected behaviour
and we would add a modal dialog which warns users about it. See more
details here
https://github.com/elastic/kibana/issues/197157#issuecomment-2432592394
2. Editing Private entry and switching the sharing option twice from
Private => Global => Private causes the issue where we would treat
selected entry as a new one and thus calling "create entry" instead of
"update".
* Edit private entry
* Update entry's name
* Switch sharing option to Global
* Switch sharing option back to Private
* Save the entry
**Current behaviour**: a new private entry is created
**Expected behaviour**: existing private entry is updated
https://github.com/user-attachments/assets/e11e14bd-c557-401e-a23f-e01ac7aedf30
Delete any items that are not applicable to this PR.
- [ ] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
Update docker.elastic.co/wolfi/chainguard-base:latest Docker digest to de4d5b0 (main) (#197917)
[Response Ops][Maintenance Window] Fix Maintenance Window Wildcard Scoped Queries (#194777)
Issue: https://github.com/elastic/sdh-kibana/issues/4923
Fixes maintenance window scoped query using wildcards by injecting the
`analyze_wildcard` property to the DSL used to determine which alerts
should be associated with the maintenance window.
Also fixes the update route to correctly take into account the user's
`allowLeadingWildcard` flag. It was implemented for the create route but
not the update route.
Fixes: https://github.com/elastic/kibana/issues/194763
1. Install sample data:

2. Create a maintenance window with the following scoped query:

3. Create a ES query rule and trigger actions:

4. Assert the `maintenance_window_id` on the 4 alerts are set

- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios)
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[api-docs] 2024-10-27 Daily api_docs build (#197930)
Generated by
https://buildkite.com/elastic/kibana-api-docs-daily/builds/873
[Cloud Security] Clicking on Contextual Flyout popout Icon now opens page in new tab (#196763)
Currently when user clicks on Popout icon on Misconfiguration or
Vulnerabilities Contextual flyout, user gets redirected to Findings page
but in the same tab. Popout Icon implies that it should navigate user to
other page on separate Tabs as such the current behaviour is not right.
This PR addresses that issue
---------
Co-authored-by: kibanamachine <42973632+kibanamachine@users.noreply.github.com>
[ES|QL] Update function metadata (#197940)
This PR updates the function definitions and inline docs based on the
latest metadata from Elasticsearch.
[Security Solution] Remove index pattern field from Sourcerer (#190113)
This PR removes index pattern field from the sourcerer model, replacing
it with direct access to data view spec.
The end goal for the sourcerer is to just utilize platform wide Data
View Types, instead of some custom abstractions / containers such as
indexPattern field which is effectively a DataViewSpec, just packed up
differently.
[Cloud Security] add posture type for CSPM dashboard accounts link (#197633)
- fixes https://github.com/elastic/security-team/issues/10914
[Observability Onboarding] Show search bar even when category is not selected (#197825)
Closes https://github.com/elastic/observability-dev/issues/4065 🔒
Fixes an issue when search bar is not visible unless a category is
selected.

Fix typo in the file name
CR fixes
[ResponseOps][Cases] Miscount of total numbers of alerts in telemetry (#196112)
Closes https://github.com/elastic/kibana/issues/177208
Problem:
- the metrics collected in telemetry for alerts don't count the total
number of alerts on a case correctly.
Solution:
- added new aggregation function: getUniqueAlertCommentsCountQuery,
which is now responsible for defining the cardinality aggregation for
counting unique alert comments by alertId.
- in the aggs section of the savedObjectsClient.find, the new
cardinality aggregation query was added
- the total number of alerts is updated to be the result extracted from
the new aggregation
Example:

- in the telemetry object, we have the following info:
<img width="331" alt="Screenshot 2024-10-22 at 15 21 40"
src="https://github.com/user-attachments/assets/6419e72d-84b4-4068-a741-6e32c6e966f7">
---------
Co-authored-by: Antonio <antoniodcoelho@gmail.com>
[ResponseOps][Cases]Add instructions of how to create a connector in the create case form (#197041)
Closes https://github.com/elastic/kibana/issues/189246
- A helper text was added in the create case form to tell the user that
needs to create a connector in the stack management > cases > settings
before attaching it to a case
- A new "add connector" button was placed in the stack management >
cases > settings page, in the connectors section
https://github.com/user-attachments/assets/7866b41a-11b5-4ca3-bd65-988412ab1e2f
---------
Co-authored-by: Antonio <antoniodcoelho@gmail.com>
[Discover][ES|QL] Rename Documents tab to Results (#197833)
This PR renames Documents label to Results for ES|QL mode.
<img width="1091" alt="Screenshot 2024-10-25 at 15 44 32"
src="https://github.com/user-attachments/assets/8678bb86-7e4b-4341-9bb3-50becced655b">
<img width="1676" alt="Screenshot 2024-10-25 at 15 52 55"
src="https://github.com/user-attachments/assets/c79d2ee0-62e1-4506-bcb5-29552287f140">
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
[EDR Workflows] Enable Blocklist CY in MKI (#197952)
Since adding this test file was tied to changes in Kibana, we initially
couldn’t enable it in the MKI. The MKI relies on a Kibana image built
from the main branch, and at that time, the necessary changes for these
tests to pass hadn’t yet been merged. Now that these updates are
included in the main branch, the Kibana image used in MKI has the
required changes, so we can proceed with enabling the tests.
Manual MKI run -
https://buildkite.com/elastic/kibana-serverless-security-solution-quality-gate-defend-workflows/builds/1545
[Security Solution][Detection Engine] removes legacy alerting endpoints from Security Solution dev scripts (#197424)
- addresses https://github.com/elastic/kibana/issues/95842
---------
Co-authored-by: Ryland Herrick <ryalnd@gmail.com>
[CodeQL] Local run script (#194272)
This PR introduces a script that allows developers to run CodeQL
analysis locally. It uses a Docker container with prebuilt CodeQL
queries to facilitate easy setup and execution.
The script has the following key steps:
- Creating a CodeQL database from the source code. The database is
essentially a representation of the codebase that CodeQL uses to analyze
for potential issues.
- Running the analysis on the created database,
`javascript-security-and-quality` suit is used.
```
bash scripts/codeql/quick_check.sh -s path/to/your-source-dir
```
For example
```
bash scripts/codeql/quick_check.sh -s ./x-pack/plugins/security_solution/public/common/components/ml/conditional_links
```
The `-s` option allows you to specify the path to the source code
directory that you wish to analyze.
Checked the ability to use MSFT image for local run
https://github.com/microsoft/codeql-container. Turned out it has several
problems:
1. The published one has an error with [execute
permissions](https://github.com/microsoft/codeql-container/issues/53).
2. Container has outdated nodejs version, so it didn't parse our syntax
(like `??`) and failed.
3. The technique used in the repository to download the CodeQL binaries
and precompile the queries is outdated in the sense that GitHub now
offers pre-compiled queries you can just download. Follow this
[comment](https://github.com/microsoft/codeql-container/issues/53#issuecomment-1875879512).
Taking this into consideration I have created a lightweight docker image
without extraneous dependencies for go/.net/java.
There are issues sometimes when analyze run returns no results,
particularly when analyzing a single folder.
It might be due to the missing context for the data flow graph CodeQL
generates or context for interdependencies. This is actually a trade off
of running it locally for a subset of source directories. We need to
explicitly state that in the documentation and advise to expand the
scope of source code directories involved for local scan.
Documentation for triaging issues will be updated separately.
__Closes: https://github.com/elastic/kibana/issues/195740__
chore(slo): remove tests migrated to agnostic framework (#197711)
Resolves https://github.com/elastic/kibana/issues/183397
This PR is a follow up of https://github.com/elastic/kibana/pull/195927,
that removes the old and migrated tests to the agnostic framework.
---------
Co-authored-by: kibanamachine <42973632+kibanamachine@users.noreply.github.com>
Co-authored-by: Dzmitry Lemechko <dzmitry.lemechko@elastic.co>
[Response Ops][Task Manager] change task claiming interface to stop using observables (#196196)
Resolves https://github.com/elastic/kibana/issues/184952
Changing task claimers to return promises instead of observables. This
is a code refactor and should not have any effect on task claiming
functionality.
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Fleet] Fix agents count in agent list table and add tooltip with correct info (#197834)
Fixes https://github.com/elastic/kibana/issues/195441
Selection agent count on agent list table gets incorrect when there are
multiple hosted agents, especially if they are on inactive state. In
fact to calculate the selected number of agents we were getting hosted
agents, but without taking into account the filtering applied on the
page, i.e. we were always getting all the hosted agent (inactive too).
This caused the final calculation to be off.
In this PR I'm fixing [the
query](https://github.com/elastic/kibana/pull/197834/files#diff-9707a4b93a96749876e4cf173a0b39cd5a620e311e2652c5ed4b8670ca7e6becR309-R320)
used to get those agents to take in account the filters and I'm also
adding a small tooltip that breaks up the number of agents (selected,
total, hosted)
- Make sure to have many agents, hosted and not in different states
(inactive, unenrolled)
- To make a hosted agent inactive follow the steps explained
[here](https://github.com/elastic/kibana/issues/195441)
- Verify that the selection numbers are correct: select agents on all
pages and hover on the new tooltip shown besides the "selected agents".
This number should match the number shown on the actions dropdown
<img width="2376" alt="Screenshot 2024-10-25 at 17 00 44"
src="https://github.com/user-attachments/assets/81d2836a-f997-4ccb-a23c-3d2cfbfa62d3">
<img width="2409" alt="Screenshot 2024-10-25 at 17 00 59"
src="https://github.com/user-attachments/assets/ba21933a-f1e6-457e-8059-e87b3e29a7d1">
https://github.com/user-attachments/assets/c153c491-29a1-481c-a3e3-25bab6412963
- [ ] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [ ]
[Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html)
was added for features that require explanation or tutorials
- [ ] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Cloud Security] exclude unknown findings from compliance score calculation (#197829)
Findings from 3rd party date can have `result.evaluation: unknown`. This
leads to incorrect posture/compliance score in our flows. This PR
removes these findings from the score calculation and graphical
representation. properly introducing `unknown` in the compliance score
UX flows will be solved separately
- fixes https://github.com/elastic/security-team/issues/10913
<img width="1473" alt="Screenshot 2024-10-25 at 14 19 03"
src="https://github.com/user-attachments/assets/c69e45b0-7da1-4eb8-b83a-f895e7b7c3a4">
Delete any items that are not applicable to this PR.
- [x] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [ ]
[Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html)
was added for features that require explanation or tutorials
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
- [x] [Flaky Test
Runner](https://ci-stats.kibana.dev/trigger_flaky_test_runner/1) was
used on any tests changed
- [ ] Any UI touched in this PR is usable by keyboard only (learn more
about [keyboard accessibility](https://webaim.org/techniques/keyboard/))
- [ ] Any UI touched in this PR does not create any new axe failures
(run axe in browser:
[FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/),
[Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
- [x] If a plugin configuration key changed, check if it needs to be
allowlisted in the cloud and added to the [docker
list](https://github.com/elastic/kibana/blob/main/src/dev/build/tasks/os_packages/docker_generator/resources/base/bin/kibana-docker)
- [ ] This renders correctly on smaller devices using a responsive
layout. (You can test this [in your
browser](https://www.browserstack.com/guide/responsive-testing-on-local-server))
- [ ] This was checked for [cross-browser
compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
[Authz] OAS Descriptions for Route Authz (#197001)
Closes https://github.com/elastic/kibana/issues/191714
Update process router to generate authz descriptions based on the new
Route Security objects.
Delete any items that are not applicable to this PR.
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
---------
Co-authored-by: kibanamachine <42973632+kibanamachine@users.noreply.github.com>
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
Add tags to connector run failures indicating if it's user or framework error (#197818)
Resolves https://github.com/elastic/kibana/issues/197315
In this PR, I'm adding the following tags to the connector failure logs
so it makes it easier to filter for systematic errors.
- `connector-run-failed` for logs specific to connector run failures
- `user-error` for errors caused by the user
- `framework-error` for systematic errors
You can either use the jest test to observe the returned flags or set
your logging to JSON and make connectors fail.
kibana.yml to set logging to JSON
```
logging:
appenders:
json-layout:
type: console
layout:
type: json
root:
appenders: [json-layout]
```
[EDR Workflows] Fix Cypress tests failing on Alerts step (#197384)
Delete data when clearing security entity store (#197938)
Fixed a bug where the "Clear all entities" button in the security entity
store didn't delete data due to a missing query parameter.
FTR SAML Auth - Adjust stateful internal request header (#197994)
This PR adds the `x-elastic-internal-origin` header to the stateful
internal request headers used by FTR.
This fixes an issue that we're seeing when running deployment agnostic
tests against ESS on 9.0.0-SNAPSHOT.
[SKIP ON MKI] reporting datastream (#197958)
See details: https://github.com/elastic/kibana/issues/197955
[SKIP ON MKI] discover reporting (#197959)
See details: https://github.com/elastic/kibana/issues/197957
fix: [Stateful:Connectors:New connector page]Configuration form missing instructions and field names from announcement (#197963)
Closes: #197586
Forms, requiring user input, should have clear instructions on how to
fill them. Specific fields can have their own help (guidance) text on
how to fill them with examples.
All fields which are present in the form can be programmatically
determined, especially for the users using assistive technology to
understand what fields are present, what input is expected.
1. `aria-label` values are explicitly set for
`ConnectorConfigurationField` child components. I suspect that due to
the dynamic nature of this component, the standard mechanism does not
work properly.
<img width="1163" alt="image"
src="https://github.com/user-attachments/assets/00e1bd87-30b3-4c8f-a3d7-0c7774028a66">
[ES|QL] detect the type of `COUNT(*)` (#197914)
We weren't properly detecting the type of the expression `COUNT(*)`. Now
we are!
Before:
<img width="950" alt="Screenshot 2024-10-25 at 4 38 08 PM"
src="https://github.com/user-attachments/assets/e9bd8d78-d0c8-4069-a818-5bf3486b925b">
After:
<img width="1093" alt="Screenshot 2024-10-25 at 4 35 44 PM"
src="https://github.com/user-attachments/assets/235c63dc-7d6c-49df-9adf-e225c4550a42">
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
Co-authored-by: Stratoula Kalafateli <efstratia.kalafateli@elastic.co>
[ES|QL] remove signatures from function suggestion labels (#197842)
Showing a single acceptable function signature in the suggestions list
is confusing since it may imply that other options are not accepted.
Instead, this PR follows the Typescript tooling and simply shows the
function name in the list.

The signatures are still available in the details flyout.
<img width="981" alt="Screenshot 2024-10-25 at 8 50 01 AM"
src="https://github.com/user-attachments/assets/17ca7b55-9c88-4a42-91e0-762cfc4809b5">
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
Co-authored-by: Stratoula Kalafateli <efstratia.kalafateli@elastic.co>
[Response Ops][Task Manager] Propagate `msearch` error status code so backpressure mechanism responds correctly (#197501)
Resolves https://github.com/elastic/response-ops-team/issues/240
Creating an `MsearchError` class that preserves the status code from any
msearch errors. These errors are already piped to the managed
configuration observable that watches for and responds to ES errors from
the update by query claim strategy so I updated that filter to filter
for msearch 429 and 503 errors as well.
1. Make sure you're using the mget claim strategy
(`xpack.task_manager.claim_strategy: 'mget'`) and start ES and Kibana.
2. Inject a 429 error into an msearch response.
```
--- a/x-pack/plugins/task_manager/server/task_store.ts
+++ b/x-pack/plugins/task_manager/server/task_store.ts
@@ -571,6 +571,8 @@ export class TaskStore {
});
const { responses } = result;
+ responses[0].status = 429;
+
const versionMap = this.createVersionMap([]);
```
3. See task manager log the msearch errors and eventually reduce polling
capacity
```
[2024-10-23T15:35:59.255-04:00][ERROR][plugins.taskManager] Failed to poll for work: Unexpected status code from taskStore::msearch: 429
[2024-10-23T15:35:59.756-04:00][ERROR][plugins.taskManager] Failed to poll for work: Unexpected status code from taskStore::msearch: 429
[2024-10-23T15:36:00.257-04:00][ERROR][plugins.taskManager] Failed to poll for work: Unexpected status code from taskStore::msearch: 429
[2024-10-23T15:36:00.757-04:00][ERROR][plugins.taskManager] Failed to poll for work: Unexpected status code from taskStore::msearch: 429
...
[2024-10-23T15:36:06.267-04:00][WARN ][plugins.taskManager] Poll interval configuration is temporarily increased after Elasticsearch returned 19 "too many request" and/or "execute [inline] script" error(s).
[2024-10-23T15:36:06.268-04:00][WARN ][plugins.taskManager] Capacity configuration is temporarily reduced after Elasticsearch returned 19 "too many request" and/or "execute [inline] script" error(s).
```
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Stateful sidenav] Fix dashboard listing breadcrumbs (#197986)
[Onboarding] Check for user privileges before creating an API key (#197964)
Resolves https://github.com/elastic/kibana/issues/192983
Check for user privileges before creating an API key
<img width="1413" alt="Screenshot 2024-10-28 at 10 28 58"
src="https://github.com/user-attachments/assets/aa54ce74-98ac-43f0-b422-ab3d895c97ab">
[Fleet] Couple agent and package policies spaces (#197487)
Consolidate Rule schemas (#195613)
Towards: #172513
This PR removes `RawRule` type from `alerting/server/type` and
`RuleAttributes` schema/types.
And uses the `RawRule` that is used for ModelVersions instead of them.
---------
Co-authored-by: kibanamachine <42973632+kibanamachine@users.noreply.github.com>
Improve header button spacing (#197896)
Closes #197873
- Fix spacing between 'Give feedback' and AI button.
- While in the neighborhood, I noticed the search button had some extra
padding, so I fixed that quick too.
- Lastly, I pushed the project switcher to the far right. This is only
used for local development of Serverless and was otherwise appearing
between production buttons.
<img width="420"
src="https://github.com/user-attachments/assets/f5abe1af-1762-4658-8040-d802b9752667"
/>
<img width="420"
src="https://github.com/user-attachments/assets/04288ff3-6012-4518-866f-0dea4ad62401"
/>
<img width="420"
src="https://github.com/user-attachments/assets/ef2e0eff-d4f4-4ceb-bbf8-c39d2e3e9949"
/>
To test, you'll need to run this in serverless mode where the 'Give
feedback' button appears.
You can force it on by setting the following line equal to `true`.
https://github.com/elastic/kibana/blob/ae9c0d385015f3068a04af46678e18e2f00b519a/src/plugins/guided_onboarding/public/plugin.tsx#L50
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Security Solution][Detection Engine] fixes preview logs issue when switching between rules (#197098)
- addresses https://github.com/elastic/kibana/issues/196616
[Lens] fix showing points on line by default (#197828)
Fix the missing style to show points in line charts. Line charts should
show data points whenever the distance between points is larger than
40px.
[Fleet] Fix flaky agentless test (#197951)
Fixes https://github.com/elastic/kibana/issues/189038
Attempt to fix [this flaky test
](https://buildkite.com/elastic/kibana-on-merge/builds/53472#0192c57d-51ca-4b9b-a934-dc13b0b9b7ca)
failing with
```
Timed out in waitForNextUpdate after 1000ms.
--
|
| at waitForNextUpdate (node_modules/@testing-library/react-hooks/lib/core/asyncUtils.js:96:13)
```
I'm adding a longer timeout hoping to resolve this issue. There is no
way to run jest tests with flaky test runner so I'm not sure how to
verify that the flakiness is really gone.
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
Serverless tests - enable dot-prefixed index validation (#197141)
This PR enables Elasticsearch dot-prefixed index validation for
serverless tests.
[ObsUx][Infra] Remove no longer used feature flags for GA features (#197684)
Closes #197612
This PR removes the feature flags
(`observability:enableInfrastructureHostsView` and
`enableInfrastructureContainerAssetView` ) for host and container views
Feature settings under `Infrastructure > Settings` (ignore the profiling
one)
| Before | After |
| ------ | ----- |
|
|

|
The feature flags should not appear in the settings
The Host menu item should be visible
The Container asset views should be always enabled and visible (without
an option to disable them)
The Host asset views should be always enabled and visible (without an
option to disable them)
https://github.com/user-attachments/assets/a4d574d0-2669-4f96-88a4-a40c2f5023c2
do not set full screen mode on ExitFullScreenButton re-render (#198012)
https://github.com/elastic/kibana/pull/194892 is refactoring
[DashboardRenderer](https://github.com/elastic/kibana/blob/3391344e8dc8377d359b918521b6c48838cde8ae/src/plugins/dashboard/public/dashboard_container/external_api/dashboard_renderer.tsx)
component to replace Dashboard Embeddable with a plain old javascript
object. Dashboard Embeddable rendered its contents in a new react tree.
The new implementation does not. Since the new implementation does not
render the dashboard in a new react tree, any re-render in
`DashboardViewport` parent components causes `ExitFullScreenButton` to
re-render. In its current form, re-rendering `ExitFullScreenButton`
calls `onExit`, which causing dashboard to exit full screen mode.
This PR makes use of `useCallback` to fix the issue where re-rending
`ExitFullScreenButton` calls `onExit`.
1) Open dashboard that ships with sample web logs data set
2) switch to view mode
3) click "Full screen" button
4) Maximize a panel. Verify dashboard stays in full screen mode.
[ci] Run linting before tests (#197310)
Linting is a frequent source of build failures. By increasing the cpu
count we can run this check before starting our highly-parallel tests
without impacting total build time.
Fix documentation for session lifespan default (#198065)
This pull request includes an update to the
`docs/settings/security-settings.asciidoc` file to clarify the default
session lifespan settings for different installation environments.
Documentation update:
*
[`docs/settings/security-settings.asciidoc`](diffhunk://#diff-97a4c4e3696b33b246f55ddd794608530b693f0a7a66ae1361a32b67c7461523L204-R204):
Clarified that the default session lifespan is 30 days for on-prem
installations and 24 hours for Elastic Cloud installations.
[FTR][Ownership] Assign aiops, custom branding, etc (#197468)
Assign test files to small number of reviewers
Assigned custom_branding due to
https://github.com/elastic/kibana/blob/main/x-pack/plugins/custom_branding/kibana.jsonc#L4
Assigned response_ops_docs due to the name
Assigned monitoring due to
https://github.com/elastic/kibana/blob/main/x-pack/plugins/monitoring/kibana.jsonc#L4
Assigned so managment due to
https://github.com/elastic/kibana/blob/main/src/plugins/saved_objects_management/kibana.jsonc#L4
Assigned aiops due to
https://github.com/elastic/kibana/blob/main/x-pack/plugins/aiops/kibana.jsonc#L4
Assigned banners_functional due to Pierre being all over the git blame.
:lol:
Assigned x-pack/test/screenshot_creation due to
https://github.com/elastic/kibana/pull/197468#discussion_r1817460031
Contributes to: https://github.com/elastic/kibana/issues/194817
[Security GenAI][BUG] KB index entry created via pdf upload does not give the right response (#198020)
These changes fix the issue with the wrong response of the AI Assistant
using knowledge base tool and index entry generated from a PDF file.
The issue happens because we are using the first chunk of uploaded PDF
document as a context that we pass to LLM instead of using inner hits
chunks which are actual parts of the document relevant to the questions.
Here is [the blog
post](https://www.elastic.co/search-labs/blog/semantic-text-with-amazon-bedrock)
that talks about the strategy of using inner hits to get the most
relevant documents. (see `Strategy 1: API Calls` section)
1. Navigate to Integrations page
2. Select "Upload a file"
3. Select and upload a PDF file
4. Press Import button
5. Switch to Advanced tab
6. Fill in "Index name"
7. Add additional field > Add semantic text field > Fill in form
* Field: `attachment.content`
* Copy to field: `content`
* Inference endpoint: `elser_model_2`
8. Press Add button
9. Press Import button
1. Navigate to AI Assistant's Knowledge Base page
2. New > Index
3. Fill in "New index entry" form (below are main fields)
* Name: `[add entry name]`
* Index: `[select index name created during uploading a PDF file]`
* Field: `content`
4. Press Save button
Enable knowledge base feature via
```
xpack.securitySolution.enableExperimental:
- 'assistantKnowledgeBaseByDefault'
```
**PDF document**:
[Elastic Global Threat Report
2024](https://github.com/user-attachments/files/17544720/elastic-global-threat-report-2024.pdf)
**KB Index entry**:
Data Description: "Use this tool to answer questions about the Elastic
Global Threat Report (GTR) 2024"
Query Instruction: "Key terms to return data relevant to the Elastic
Global Threat Report (GTR) 2024"
**Questions**:
1. Who are the authors of the GTR 2024?
2. What is the forecast for the coming year in GTR 2024?
3. What are top 10 Process Injection by rules in Windows endpoints in
GTR 2024?
4. What is the most widely adopted cloud service provider this year
according to GTR 2024?
6. Give a brief conclusion of the GTR 2024
**Current behaviour**:
<img width="656" alt="Screenshot 2024-10-28 at 16 43 48"
src="https://github.com/user-attachments/assets/90615356-8807-4786-b58d-ca28c83aaec9">
**Fixed behaviour**:
<img width="655" alt="Screenshot 2024-10-28 at 16 44 47"
src="https://github.com/user-attachments/assets/9ebefbcc-20c2-4c79-98f3-11fa6acf3da6">
Improves pattern matching for data telemetry (#197876)
Addresses concerns with Regex matching.
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Synthetics] Refactor delete route !! (#195387)
Fixes https://github.com/elastic/kibana/issues/193790 !!
Refactor delete route !!
Make sure to send delete response in bulk to synthetics service !!
[Fleet] Prevent hosted policies space change (#198043)
Revert "[Canvas] Update kbn/flot to remove table.replace() issue" (#198067)
Fixes #197998
Reverts elastic/kibana#195643
skip failing test suite (#181466)
[Global Search] Instantly set `isLoading=true` when search value changes (#197750)
Close https://github.com/elastic/kibana/issues/77059
This PR solves the bug by setting the `isLoading` flag outside of the
block of debounced code whenever the search term changes.
This also makes a few slight cleanups to `search_bar.tsx`, which is
quite large. I avoided doing any serious cleanups that would make the
diff hard to read or detract from the fix.
skip flaky suite (#178404)
skip flaky suite (#197335)
skip flaky suite (#189038)
skip flaky suite (#192126)
skip flaky suite (#197765)
skip flaky suite (#189739)
skip flaky suite (#196766)
skip flaky suite (#174661)
Added redirect option after Entity CSV upload (#197937)
Added a redirect button to view Entities after a successful Asset
Criticality CSV file upload process
Additionally, made some small changes to the copy for the Entity Store
management workflows
<img width="1490" alt="Screenshot 2024-10-27 at 9 49 17 PM"
src="https://github.com/user-attachments/assets/77b587b7-8300-40ae-adc2-5119aa5f39ab">
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
Update dependency msw to ^2.4.12 (main) (#198060)
This PR contains the following updates:
| Package | Type | Update | Change | Pending |
|---|---|---|---|---|
| [msw](https://mswjs.io) ([source](https://togithub.com/mswjs/msw)) |
devDependencies | patch | [`^2.4.11` ->
`^2.4.12`](https://renovatebot.com/diffs/npm/msw/2.4.11/2.4.12) |
`2.5.2` (+3) |
---
<details>
<summary>mswjs/msw (msw)</summary>
[Compare
Source](https://togithub.com/mswjs/msw/compare/v2.4.11...v2.4.12)
- **node:** preserve headers instanceof when recording raw headers
([#​2321](https://togithub.com/mswjs/msw/issues/2321))
([`a58a300`](https://togithub.com/mswjs/msw/commit/a58a300687a48e13c0268403a71183cf7825f748))
[@​paoloricciuti](https://togithub.com/paoloricciuti)
</details>
---
📅 **Schedule**: Branch creation - At any time (no schedule defined),
Automerge - At any time (no schedule defined).
🚦 **Automerge**: Disabled by config. Please merge this manually once you
are satisfied.
♻ **Rebasing**: Whenever PR becomes conflicted, or you tick the
rebase/retry checkbox.
🔕 **Ignore**: Close this PR and you won't be reminded about this update
again.
---
- [ ] <!-- rebase-check -->If you want to rebase/retry this PR, check
this box
---
This PR has been generated by [Renovate
Bot](https://togithub.com/renovatebot/renovate).
<!--renovate-debug:eyJjcmVhdGVkSW5WZXIiOiIzNy40MjUuMSIsInVwZGF0ZWRJblZlciI6IjM3LjQyNS4xIiwidGFyZ2V0QnJhbmNoIjoibWFpbiIsImxhYmVscyI6WyJUZWFtOkNsb3VkIFNlY3VyaXR5IiwiYmFja3BvcnQ6c2tpcCIsInJlbGVhc2Vfbm90ZTpza2lwIl19-->
Co-authored-by: elastic-renovate-prod[bot] <174716857+elastic-renovate-prod[bot]@users.noreply.github.com>
[CI] Disable UpdateCLI workflow on forks (#196624)
The UpdateCLI workflow is running against forks when it shouldn't be:
https://github.com/Ikuni17/kibana/actions/runs/11359905941
Fix Dev Container KBN_DIR (#195810)
In #193488, `KBN_DIR` was changed to be a dynamic variable. It wasn't
being properly propagated through the build process in the Dockerfile
and the full path to `env.sh` wasn't being set. This passes the
directory as a build `ARG` as well to fix the path.
[api-docs] 2024-10-29 Daily api_docs build (#198103)
Generated by
https://buildkite.com/elastic/kibana-api-docs-daily/builds/875
[Security Solution][Hotfix] Avoid blocking prebuilt rule upgrade upon conflicts with disabled feature flag (#198106)
It turned out some of the update rule buttons are disabled. This is a side effect of the functionality not fully hidden under a feature flag. This PR hides prebuilt rule customisation functionality disabling update rule buttons under `prebuiltRulesCustomizationEnabled` feature flag.

<img width="1719" alt="image" src="https://github.com/user-attachments/assets/349223dc-dda5-46fb-832f-d7097a81580e">
<img width="1721" alt="image" src="https://github.com/user-attachments/assets/a28512f6-e605-460e-884d-571ab408a7d9">
[Infra] Fix anomalies flyout navigation failing test (#197999)
Closes #192882
The issue was that the url was checked too early which resulted in
checking the locator url instead of the page url after navigating so I
added a check for loading before the URL check and this solved the
issue.
https://buildkite.com/elastic/kibana-flaky-test-suite-runner/builds/7284
[ObsUx][Infra] Unskip and try to fix hosts view test (#197861)
Closes #191806
The parts of the unskipped test were fixed here - the only case I
couldn't find the reason for failing after unskipping it is `should have
an option to open the chart in lens` - for some reason, the whole menu
is gone when checking the CI and I couldn't reproduce that so this will
be the only skipped part so we can at least have all the other `Hosts
view` tests
[Cloud Security] Fix flaky metering tests
[Observability Onboarding] Set tech preview badges correctly (#197831)
As discussed, adjust the first onboarding page:
* Remove tech preview labels from EA flows
* Change wording
<img width="857" alt="Screenshot 2024-10-25 at 15 23 47"
src="https://github.com/user-attachments/assets/ceffbe90-019d-4fa8-ab6f-16cbf0aaf3d4">
<img width="814" alt="Screenshot 2024-10-25 at 15 23 59"
src="https://github.com/user-attachments/assets/4f5cf657-6fd2-479f-aa92-9460bc2ecfef">
[EDR Workflows] Skip Osquery test in MKI (#198117)
[EDR Workflows] Improve on unavailable shard exception flakiness in cypress (#197864)
The cypress task `cy.task('indexEndpointHosts')` sometimes throws
`no_shard_available_action_exception`, when transforms are stopped. This
looks like a temporary issue, and in other tests it is simply retried.
This PR adds the retry logic for this type of error, and unskips some
tests.
closes #194135
closes #191914
Delete any items that are not applicable to this PR.
- [x] [Flaky Test
Runner](https://ci-stats.kibana.dev/trigger_flaky_test_runner/1) was
used on any tests changed
[Cloud Security] add vulnerabilties data set to filter for links from CNVM dashboard (#197648)
- fixes https://github.com/elastic/security-team/issues/10915
[Entity Analytics] [Entity Store] Telemetry (#196880)
This PR adds telemetry for the Entity Store.
Client side tracks UI enablement actions, whilst Kibana side tracks
execution time of the store initialisation process and execution time of
the enrich policy task.
Finally we also track number of entities in the store
Update docker.elastic.co/wolfi/chainguard-base:latest Docker digest to 1815394 (main) (#198099)
This PR contains the following updates:
| Package | Update | Change |
|---|---|---|
| docker.elastic.co/wolfi/chainguard-base | digest | `de4d5b0` ->
`1815394` |
---
📅 **Schedule**: Branch creation - At any time (no schedule defined),
Automerge - At any time (no schedule defined).
🚦 **Automerge**: Disabled by config. Please merge this manually once you
are satisfied.
♻ **Rebasing**: Whenever PR becomes conflicted, or you tick the
rebase/retry checkbox.
🔕 **Ignore**: Close this PR and you won't be reminded about this update
again.
---
- [ ] <!-- rebase-check -->If you want to rebase/retry this PR, check
this box
---
This PR has been generated by [Renovate
Bot](https://togithub.com/renovatebot/renovate).
<!--renovate-debug:eyJjcmVhdGVkSW5WZXIiOiIzNy40MjUuMSIsInVwZGF0ZWRJblZlciI6IjM3LjQyNS4xIiwidGFyZ2V0QnJhbmNoIjoibWFpbiIsImxhYmVscyI6WyJUZWFtOk9wZXJhdGlvbnMiLCJyZWxlYXNlX25vdGU6c2tpcCJdfQ==-->
Co-authored-by: elastic-renovate-prod[bot] <174716857+elastic-renovate-prod[bot]@users.noreply.github.com>
Update dependency @launchdarkly/node-server-sdk to ^9.6.1 (main) (#196897)
[ML] Data Frame Analytics: removing scss overrides for exploration pages (#197724)
Related meta issue: https://github.com/elastic/kibana/issues/140695
Regression model evaluation before:
<img width="1455" alt="image"
src="https://github.com/user-attachments/assets/cfdb794d-4576-4c10-96c1-0b3856857cdd">
After:
<img width="1455" alt="image"
src="https://github.com/user-attachments/assets/4c2bbdf3-85ef-489e-bc3a-1281d3531328">
Classification evaluation before:
<img width="1474" alt="image"
src="https://github.com/user-attachments/assets/e565cac3-8c1d-4e4f-8cac-7ea8abf4358d">
After switching fully to flex layout as we no longer support IE11 and
all the workarounds were no longer needed (Note it's all left aligned
now):
<img width="1467" alt="image"
src="https://github.com/user-attachments/assets/280ea446-17fc-4622-a925-57ef6c01cd89">
Delete any items that are not applicable to this PR.
- [ ] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [ ]
[Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html)
was added for features that require explanation or tutorials
- [ ] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
- [ ] [Flaky Test
Runner](https://ci-stats.kibana.dev/trigger_flaky_test_runner/1) was
used on any tests changed
- [ ] Any UI touched in this PR is usable by keyboard only (learn more
about [keyboard accessibility](https://webaim.org/techniques/keyboard/))
- [ ] Any UI touched in this PR does not create any new axe failures
(run axe in browser:
[FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/),
[Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
- [ ] If a plugin configuration key changed, check if it needs to be
allowlisted in the cloud and added to the [docker
list](https://github.com/elastic/kibana/blob/main/src/dev/build/tasks/os_packages/docker_generator/resources/base/bin/kibana-docker)
- [ ] This renders correctly on smaller devices using a responsive
layout. (You can test this [in your
browser](https://www.browserstack.com/guide/responsive-testing-on-local-server))
- [ ] This was checked for [cross-browser
compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[ES|QL] separate `KEEP`, `DROP`, and `SORT` autocomplete routines (#197744)
This PR begins the refactor described in
https://github.com/elastic/kibana/issues/195418.
The autocomplete engine now delegates to command-specific routines
attached to the command definitions for `KEEP`, `DROP`, and `SORT`.
The naming of `getFieldsFor` has been broadened to `getColumnsFor`
because the response from Elasticsearch can contain variables as well as
fields, depending on the query that is used to fetch the columns.
No user-facing behavior should have changed.
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
---------
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[CI] Fix project build & deploy job (#196562)
In #195581 we've added the option to deploy through the clickable
triggers. But in it's current state, it's broken in several aspects.
(1) It's not starting on click. Triggers was resulting in a 422 on
Buildkite's side, and after digging more into it, this was the error:
<img width="1019" alt="Screenshot 2024-10-16 at 16 53 13"
src="https://github.com/user-attachments/assets/f602dde9-2cc4-474f-b432-a3d4f9d5ae91">
Apparently, building PRs needs to be enabled on jobs that want to be
triggered through the PR bot.
(2) It is set up to run regardless of the labels
(3) There's no feedback on runs
This PR:
- enables buildability in the pipeline's config
- exits early if deploy labels are missing
- adds a comment on the PR if a deploy job is started or finished
- removes the kibana build step, it's not needed, as we have a step to
build the docker image
TODO:
- [x] Add feedback about a started job (either through a non-required
check, or a github comment)
- [x] Early exit if a label is missing
There are several other builds started right now, because the logic that
would trigger a build on changing a draft to ready. To be fixed in
https://github.com/elastic/buildkite-pr-bot/issues/78
Tested after manually by enabling the option on the UI, and triggering
through the checkbox:
https://buildkite.com/elastic/kibana-deploy-project-from-pr/builds/23
Expand README (#197880)
Adds a bit more general background, intro to concepts, and guidelines
about what to use FF for and what not to
Delete any items that are not applicable to this PR.
- [ ] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [ ]
[Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html)
was added for features that require explanation or tutorials
- [ ] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
- [ ] [Flaky Test
Runner](https://ci-stats.kibana.dev/trigger_flaky_test_runner/1) was
used on any tests changed
- [ ] Any UI touched in this PR is usable by keyboard only (learn more
about [keyboard accessibility](https://webaim.org/techniques/keyboard/))
- [ ] Any UI touched in this PR does not create any new axe failures
(run axe in browser:
[FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/),
[Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
- [ ] If a plugin configuration key changed, check if it needs to be
allowlisted in the cloud and added to the [docker
list](https://github.com/elastic/kibana/blob/main/src/dev/build/tasks/os_packages/docker_generator/resources/base/bin/kibana-docker)
- [ ] This renders correctly on smaller devices using a responsive
layout. (You can test this [in your
browser](https://www.browserstack.com/guide/responsive-testing-on-local-server))
- [ ] This was checked for [cross-browser
compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
Delete this section if it is not applicable to this PR.
Before closing this PR, invite QA, stakeholders, and other developers to
identify risks that should be tested prior to the change/feature
release.
When forming the risk matrix, consider some of the following examples
and how they may potentially impact the change:
| Risk | Probability | Severity | Mitigation/Notes |
|---------------------------|-------------|----------|-------------------------|
| Multiple Spaces—unexpected behavior in non-default Kibana Space.
| Low | High | Integration tests will verify that all features are still
supported in non-default Kibana Space and when user switches between
spaces. |
| Multiple nodes—Elasticsearch polling might have race conditions
when multiple Kibana nodes are polling for the same tasks. | High | Low
| Tasks are idempotent, so executing them multiple times will not result
in logical error, but will degrade performance. To test for this case we
add plenty of unit tests around this logic and document manual testing
procedure. |
| Code should gracefully handle cases when feature X or plugin Y are
disabled. | Medium | High | Unit tests will verify that any feature flag
or plugin combination still results in our service operational. |
| [See more potential risk
examples](https://github.com/elastic/kibana/blob/main/RISK_MATRIX.mdx) |
- [ ] This was checked for breaking API changes and was [labeled
appropriately](https://www.elastic.co/guide/en/kibana/master/contributing.html#_add_your_labels)
- [ ] This will appear in the **Release Notes** and follow the
[guidelines](https://www.elastic.co/guide/en/kibana/master/contributing.html#kibana-release-notes-process)
---------
Co-authored-by: Alejandro Fernández Haro <alejandro.haro@elastic.co>
Fix Typo: Change 'dashaboard' to 'dashboard' on APM-service Dashboards page #195773 (#196969)
**Title:** Fix Typo: Change 'dashaboard' to 'dashboard' on APM-service
Dashboards page
**Description:**
This PR fixes a typo on the "Dashboards" page for APM-service. The typo
"dashaboard" has been corrected to "dashboard" to ensure proper
functionality and readability.
closes #195773
**Changes Made:**
- Corrected the typo in the text "To get started, add your dashaboard"
to "To get started, add your dashboard."
**Testing:**
- Verified the change on the Dashboards page for APM-service.
- Ensured no other instances of the typo exist in the codebase.
**Release note:**
Fixes a typo on the "Dashboards" page for APM-service, changing
'dashaboard' to 'dashboard'.
**Additional Notes:**
No additional notes.
Summarize your PR. If it involves visual changes include a screenshot or
gif.
Delete any items that are not applicable to this PR.
- [x] Any text added follows [EUI's writing
guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses
sentence case text and includes [i18n
support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md)
- [ ]
[Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html)
was added for features that require explanation or tutorials
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
- [ ] [Flaky Test
Runner](https://ci-stats.kibana.dev/trigger_flaky_test_runner/1) was
used on any tests changed
- [x] Any UI touched in this PR is usable by keyboard only (learn more
about [keyboard accessibility](https://webaim.org/techniques/keyboard/))
- [x] Any UI touched in this PR does not create any new axe failures
(run axe in browser:
[FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/),
[Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
- [ ] If a plugin configuration key changed, check if it needs to be
allowlisted in the cloud and added to the [docker
list](https://github.com/elastic/kibana/blob/main/src/dev/build/tasks/os_packages/docker_generator/resources/base/bin/kibana-docker)
- [x] This renders correctly on smaller devices using a responsive
layout. (You can test this [in your
browser](https://www.browserstack.com/guide/responsive-testing-on-local-server))
- [x] This was checked for [cross-browser
compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
Delete this section if it is not applicable to this PR.
Before closing this PR, invite QA, stakeholders, and other developers to
identify risks that should be tested prior to the change/feature
release.
When forming the risk matrix, consider some of the following examples
and how they may potentially impact the change:
| Risk | Probability | Severity | Mitigation/Notes |
|---------------------------|-------------|----------|-------------------------|
| Multiple Spaces—unexpected behavior in non-default Kibana Space.
| Low | High | Integration tests will verify that all features are still
supported in non-default Kibana Space and when user switches between
spaces. |
| Multiple nodes—Elasticsearch polling might have race conditions
when multiple Kibana nodes are polling for the same tasks. | High | Low
| Tasks are idempotent, so executing them multiple times will not result
in logical error, but will degrade performance. To test for this case we
add plenty of unit tests around this logic and document manual testing
procedure. |
| Code should gracefully handle cases when feature X or plugin Y are
disabled. | Medium | High | Unit tests will verify that any feature flag
or plugin combination still results in our service operational. |
| [See more potential risk
examples](https://github.com/elastic/kibana/blob/main/RISK_MATRIX.mdx) |
- [ ] This was checked for breaking API changes and was [labeled
appropriately](https://www.elastic.co/guide/en/kibana/master/contributing.html#_add_your_labels)
- [ ] This will appear in the **Release Notes** and follow the
[guidelines](https://www.elastic.co/guide/en/kibana/master/contributing.html#kibana-release-notes-process)
---------
Co-authored-by: Cauê Marcondes <55978943+cauemarcondes@users.noreply.github.com>
Co-authored-by: Nathan L Smith <nathan.smith@elastic.co>
Co-authored-by: jennypavlova <dzheni.pavlova@elastic.co>
[Response Ops][Actions] Remove deprecated HTTP APIs (#197510)
Resolves https://github.com/elastic/kibana/issues/90382
Removes legacy action APIs for 9.0 and updates all tests that still used
the legacy APIs to use the current APIs. Also did some renaming of
action -> connector in the files I had to touch.
Co-authored-by: Elastic Machine <elasticmachine@users.noreply.github.com>
[Fleet] Prevent duplication of managed policy !! (#197575)
Fixes https://github.com/elastic/kibana/issues/194149
Prevent duplication of managed policy !!
<img width="1594" alt="image"
src="https://github.com/user-attachments/assets/f386a287-4f9e-4307-ba84-98f3ea807ef9">
[Security Solution][Notes] - switch the securitySolutionNotesEnables feature flag to securitySolutionNotesDisabled (#196778)
This PR switches the `securitySolutionNotesEnabled` to
`securitySolutionNotesDisabled` (with a `false` value by default) to
enable the new Notes functionality in `8.16`.
Customers can set the new `securitySolutionNotesDisabled` feature flag
to true in their environment if they want to go back to the old notes
system.
The PR also fixes a tiny bug with the badge showing the number of notes
in the Timeline Notes tab. The new system was not taking into account a
timeline description, so if the timeline had a description the number of
notes was always 1 lower than the actual number of notes displayed
below. This issue was highlighted by a Cypress test!
The goal is to remove the old system entirely within a few releases
(maybe `8.18` or `9.0`).
- [x] [Unit or functional
tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)
were updated or added to match the most common scenarios
https://github.com/elastic/kibana/issues/189879
[ci] Fix cloud deployments (#198086)
Our build scripts are relying on a step that was removed in
https://github.com/elastic/elasticsearch/pull/115357. The image that was
produced by this script is eventually consumed by cloud deployments from
pull requests.
This updates our scripts to use the cloud-ess variant instead. There
should not be any functional difference.
We'll need the image to go through our promotion pipeline to be tested
via label.
https://buildkite.com/elastic/kibana-elasticsearch-snapshot-build/builds/4673
[ci] Use es snapshot cache on miscellaneous steps 2 (#198078)
Adds the remaining steps missing snapshot loading from cache that I
missed on the first loop.
[Observability] Update breadcrumbs for observability project based navigation (#196785)
~⚠️ I'm still putting out some fires with tests, but this is ready to
start being reviewed.~
A continuation of https://github.com/elastic/kibana/pull/196169 for
Observability (please read that PR description first).
Related: https://github.com/elastic/kibana/issues/192050
There are essentially three types of breadcrumbs - serverless (which is
project style), stateful project style (set through spaces settings),
and classic style (the old breadcrumbs we've seen for years). Whilst
serverless and stateful project style both use the project based style
the navigation trees are slightly different, so the breadcrumbs results
are not identical [when they derive the "nav
crumbs"](https://github.com/elastic/kibana/blob/9577aa980dd1565fba05e34292fb5c0bba692889/packages/core/chrome/core-chrome-browser-internal/src/project_navigation/breadcrumbs.tsx#L55).
Here "project style" will refer to serverless and stateful project
style.
In these changes I've, for the most part, tried to refactor things so
Observability solutions route their breadcrumbs through the
observability-shared `useBreadcrumbs` hook, this way the logic around
project style, adding an Observability crumb in classic etc is
consolidated in one place.
[For several solutions `absolute` breadcrumbs are being
used](https://github.com/elastic/kibana/blob/9577aa980dd1565fba05e34292fb5c0bba692889/packages/core/chrome/core-chrome-browser-internal/src/project_navigation/breadcrumbs.tsx#L46),
and this means we'll roughly have the same breadcrumbs across the 3
experience…
maximpn
added a commit
that referenced
this pull request
Nov 12, 2024
**Partially addresses:** #171520 ## Summary This PR adds is built on top of #193828 and #196948 and adds an Alert Suppression editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow. ## Details #171520 required adding editable components for each field diffable rule field. Alert Suppression edit component was extracted from Define Rule Step Component into a separate reusable component. To simplify the logic it was split into common Alert Suppression and Threshold Alert Suppression since the latter is a specific use case. ## Caveats Upgrade prebuilt rules workflow is quite different from rule creation and editing. In create and edit rule forms users are capable to change any field at their will. Upgrade prebuilt rules workflow allow to modify only specific fields having diff in the current rule upgrade. There are fields which depend on each other. In particular Alert Suppression isn't supported for EQL sequence though it's addressed in #189725. - Alert Suppression editable component in Three Way Diff workflow isn't disabled EQL sequence rule queries. Alert suppression support for rules with EQL sequence queries is implemented in #189725. - Machine learning rule type require running selected machine learning jobs otherwise input could be disabled in case of there are no fields to pick from otherwise a warning message below the combobox is shown. ## How to test The simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below - Enable Prebuilt rule customization feature by adding a `prebuiltRulesCustomizationEnabled` feature flag - Run Kibana locally - Install a prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e` - Patch the installed rule by running a query below ```bash curl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H "elastic-api-version: 2023-10-31" -d '{"rule_id":"2a692072-d78d-42f3-a48a-775677d79c4e","version":1,"alert_suppression":{"group_by":["host.name"]}}' http://localhost:5601/kbn/api/detection_engine/rules ``` - Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button ## Screenshots Custom query prebuilt rule (UI looks similar for EQL, Indicator Match, New Terms and ES|QL rule types)  Machine learning prebuilt rule with a diff in alert suppression  Threshold prebuilt rule 
maximpn
added a commit
that referenced
this pull request
Nov 12, 2024
…198673) (#199809) # Backport This will backport the following commits from `main` to `8.x`: - [[Security Solution] Add Alert Suppression editable component (#198673)](#198673) <!--- Backport version: 8.9.8 --> ### Questions ? Please refer to the [Backport tool documentation](https://github.com/sqren/backport) <!--BACKPORT [{"author":{"name":"Maxim Palenov","email":"maxim.palenov@elastic.co"},"sourceCommit":{"committedDate":"2024-11-12T14:46:39Z","message":"[Security Solution] Add Alert Suppression editable component (#198673)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and #196948 and adds an Alert Suppression editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nhttps://github.com//issues/171520 required adding editable components for each field diffable rule field. Alert Suppression edit component was extracted from Define Rule Step Component into a separate reusable component. To simplify the logic it was split into common Alert Suppression and Threshold Alert Suppression since the latter is a specific use case.\r\n\r\n## Caveats\r\n\r\nUpgrade prebuilt rules workflow is quite different from rule creation and editing. In create and edit rule forms users are capable to change any field at their will. Upgrade prebuilt rules workflow allow to modify only specific fields having diff in the current rule upgrade.\r\n\r\nThere are fields which depend on each other. In particular Alert Suppression isn't supported for EQL sequence though it's addressed in #189725. \r\n\r\n- Alert Suppression editable component in Three Way Diff workflow isn't disabled EQL sequence rule queries. Alert suppression support for rules with EQL sequence queries is implemented in #189725. \r\n\r\n- Machine learning rule type require running selected machine learning jobs otherwise input could be disabled in case of there are no fields to pick from otherwise a warning message below the combobox is shown.\r\n\r\n## How to test\r\n\r\nThe simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below\r\n\r\n- Enable Prebuilt rule customization feature by adding a `prebuiltRulesCustomizationEnabled` feature flag\r\n- Run Kibana locally\r\n- Install a prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e`\r\n- Patch the installed rule by running a query below\r\n\r\n```bash\r\ncurl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H \"elastic-api-version: 2023-10-31\" -d '{\"rule_id\":\"2a692072-d78d-42f3-a48a-775677d79c4e\",\"version\":1,\"alert_suppression\":{\"group_by\":[\"host.name\"]}}' http://localhost:5601/kbn/api/detection_engine/rules\r\n```\r\n\r\n- Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button\r\n\r\n## Screenshots\r\n\r\nCustom query prebuilt rule (UI looks similar for EQL, Indicator Match, New Terms and ES|QL rule types)\r\n\r\n\r\n\r\nMachine learning prebuilt rule with a diff in alert suppression\r\n\r\n\r\n\r\nThreshold prebuilt rule\r\n\r\n","sha":"06986e4a86a0fa3c3951fcb6b2ba34ebe2769820","branchLabelMapping":{"^v9.0.0$":"main","^v8.17.0$":"8.x","^v(\\d+).(\\d+).\\d+$":"$1.$2"}},"sourcePullRequest":{"labels":["release_note:skip","v9.0.0","Team:Detections and Resp","Team: SecuritySolution","Team:Detection Rule Management","Feature:Prebuilt Detection Rules","backport:prev-minor","v8.17.0"],"number":198673,"url":"https://github.com/elastic/kibana/pull/198673","mergeCommit":{"message":"[Security Solution] Add Alert Suppression editable component (#198673)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and #196948 and adds an Alert Suppression editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nhttps://github.com//issues/171520 required adding editable components for each field diffable rule field. Alert Suppression edit component was extracted from Define Rule Step Component into a separate reusable component. To simplify the logic it was split into common Alert Suppression and Threshold Alert Suppression since the latter is a specific use case.\r\n\r\n## Caveats\r\n\r\nUpgrade prebuilt rules workflow is quite different from rule creation and editing. In create and edit rule forms users are capable to change any field at their will. Upgrade prebuilt rules workflow allow to modify only specific fields having diff in the current rule upgrade.\r\n\r\nThere are fields which depend on each other. In particular Alert Suppression isn't supported for EQL sequence though it's addressed in #189725. \r\n\r\n- Alert Suppression editable component in Three Way Diff workflow isn't disabled EQL sequence rule queries. Alert suppression support for rules with EQL sequence queries is implemented in #189725. \r\n\r\n- Machine learning rule type require running selected machine learning jobs otherwise input could be disabled in case of there are no fields to pick from otherwise a warning message below the combobox is shown.\r\n\r\n## How to test\r\n\r\nThe simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below\r\n\r\n- Enable Prebuilt rule customization feature by adding a `prebuiltRulesCustomizationEnabled` feature flag\r\n- Run Kibana locally\r\n- Install a prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e`\r\n- Patch the installed rule by running a query below\r\n\r\n```bash\r\ncurl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H \"elastic-api-version: 2023-10-31\" -d '{\"rule_id\":\"2a692072-d78d-42f3-a48a-775677d79c4e\",\"version\":1,\"alert_suppression\":{\"group_by\":[\"host.name\"]}}' http://localhost:5601/kbn/api/detection_engine/rules\r\n```\r\n\r\n- Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button\r\n\r\n## Screenshots\r\n\r\nCustom query prebuilt rule (UI looks similar for EQL, Indicator Match, New Terms and ES|QL rule types)\r\n\r\n\r\n\r\nMachine learning prebuilt rule with a diff in alert suppression\r\n\r\n\r\n\r\nThreshold prebuilt rule\r\n\r\n","sha":"06986e4a86a0fa3c3951fcb6b2ba34ebe2769820"}},"sourceBranch":"main","suggestedTargetBranches":["8.x"],"targetPullRequestStates":[{"branch":"main","label":"v9.0.0","labelRegex":"^v9.0.0$","isSourceBranch":true,"state":"MERGED","url":"https://github.com/elastic/kibana/pull/198673","number":198673,"mergeCommit":{"message":"[Security Solution] Add Alert Suppression editable component (#198673)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and #196948 and adds an Alert Suppression editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nhttps://github.com//issues/171520 required adding editable components for each field diffable rule field. Alert Suppression edit component was extracted from Define Rule Step Component into a separate reusable component. To simplify the logic it was split into common Alert Suppression and Threshold Alert Suppression since the latter is a specific use case.\r\n\r\n## Caveats\r\n\r\nUpgrade prebuilt rules workflow is quite different from rule creation and editing. In create and edit rule forms users are capable to change any field at their will. Upgrade prebuilt rules workflow allow to modify only specific fields having diff in the current rule upgrade.\r\n\r\nThere are fields which depend on each other. In particular Alert Suppression isn't supported for EQL sequence though it's addressed in #189725. \r\n\r\n- Alert Suppression editable component in Three Way Diff workflow isn't disabled EQL sequence rule queries. Alert suppression support for rules with EQL sequence queries is implemented in #189725. \r\n\r\n- Machine learning rule type require running selected machine learning jobs otherwise input could be disabled in case of there are no fields to pick from otherwise a warning message below the combobox is shown.\r\n\r\n## How to test\r\n\r\nThe simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below\r\n\r\n- Enable Prebuilt rule customization feature by adding a `prebuiltRulesCustomizationEnabled` feature flag\r\n- Run Kibana locally\r\n- Install a prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e`\r\n- Patch the installed rule by running a query below\r\n\r\n```bash\r\ncurl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H \"elastic-api-version: 2023-10-31\" -d '{\"rule_id\":\"2a692072-d78d-42f3-a48a-775677d79c4e\",\"version\":1,\"alert_suppression\":{\"group_by\":[\"host.name\"]}}' http://localhost:5601/kbn/api/detection_engine/rules\r\n```\r\n\r\n- Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button\r\n\r\n## Screenshots\r\n\r\nCustom query prebuilt rule (UI looks similar for EQL, Indicator Match, New Terms and ES|QL rule types)\r\n\r\n\r\n\r\nMachine learning prebuilt rule with a diff in alert suppression\r\n\r\n\r\n\r\nThreshold prebuilt rule\r\n\r\n","sha":"06986e4a86a0fa3c3951fcb6b2ba34ebe2769820"}},{"branch":"8.x","label":"v8.17.0","labelRegex":"^v8.17.0$","isSourceBranch":false,"state":"NOT_CREATED"}]}] BACKPORT-->
tkajtoch
pushed a commit
to tkajtoch/kibana
that referenced
this pull request
Nov 12, 2024
…#198673) **Partially addresses:** elastic#171520 ## Summary This PR adds is built on top of elastic#193828 and elastic#196948 and adds an Alert Suppression editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow. ## Details elastic#171520 required adding editable components for each field diffable rule field. Alert Suppression edit component was extracted from Define Rule Step Component into a separate reusable component. To simplify the logic it was split into common Alert Suppression and Threshold Alert Suppression since the latter is a specific use case. ## Caveats Upgrade prebuilt rules workflow is quite different from rule creation and editing. In create and edit rule forms users are capable to change any field at their will. Upgrade prebuilt rules workflow allow to modify only specific fields having diff in the current rule upgrade. There are fields which depend on each other. In particular Alert Suppression isn't supported for EQL sequence though it's addressed in elastic#189725. - Alert Suppression editable component in Three Way Diff workflow isn't disabled EQL sequence rule queries. Alert suppression support for rules with EQL sequence queries is implemented in elastic#189725. - Machine learning rule type require running selected machine learning jobs otherwise input could be disabled in case of there are no fields to pick from otherwise a warning message below the combobox is shown. ## How to test The simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below - Enable Prebuilt rule customization feature by adding a `prebuiltRulesCustomizationEnabled` feature flag - Run Kibana locally - Install a prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e` - Patch the installed rule by running a query below ```bash curl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H "elastic-api-version: 2023-10-31" -d '{"rule_id":"2a692072-d78d-42f3-a48a-775677d79c4e","version":1,"alert_suppression":{"group_by":["host.name"]}}' http://localhost:5601/kbn/api/detection_engine/rules ``` - Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button ## Screenshots Custom query prebuilt rule (UI looks similar for EQL, Indicator Match, New Terms and ES|QL rule types)  Machine learning prebuilt rule with a diff in alert suppression  Threshold prebuilt rule 
This was referenced Nov 14, 2024
CAWilson94
pushed a commit
to CAWilson94/kibana
that referenced
this pull request
Nov 18, 2024
…#198673) **Partially addresses:** elastic#171520 ## Summary This PR adds is built on top of elastic#193828 and elastic#196948 and adds an Alert Suppression editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow. ## Details elastic#171520 required adding editable components for each field diffable rule field. Alert Suppression edit component was extracted from Define Rule Step Component into a separate reusable component. To simplify the logic it was split into common Alert Suppression and Threshold Alert Suppression since the latter is a specific use case. ## Caveats Upgrade prebuilt rules workflow is quite different from rule creation and editing. In create and edit rule forms users are capable to change any field at their will. Upgrade prebuilt rules workflow allow to modify only specific fields having diff in the current rule upgrade. There are fields which depend on each other. In particular Alert Suppression isn't supported for EQL sequence though it's addressed in elastic#189725. - Alert Suppression editable component in Three Way Diff workflow isn't disabled EQL sequence rule queries. Alert suppression support for rules with EQL sequence queries is implemented in elastic#189725. - Machine learning rule type require running selected machine learning jobs otherwise input could be disabled in case of there are no fields to pick from otherwise a warning message below the combobox is shown. ## How to test The simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below - Enable Prebuilt rule customization feature by adding a `prebuiltRulesCustomizationEnabled` feature flag - Run Kibana locally - Install a prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e` - Patch the installed rule by running a query below ```bash curl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H "elastic-api-version: 2023-10-31" -d '{"rule_id":"2a692072-d78d-42f3-a48a-775677d79c4e","version":1,"alert_suppression":{"group_by":["host.name"]}}' http://localhost:5601/kbn/api/detection_engine/rules ``` - Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button ## Screenshots Custom query prebuilt rule (UI looks similar for EQL, Indicator Match, New Terms and ES|QL rule types)  Machine learning prebuilt rule with a diff in alert suppression  Threshold prebuilt rule 
maximpn
added a commit
that referenced
this pull request
Nov 22, 2024
… fields (#199115) **Partially addresses:** #171520 ## Summary This PR adds is built on top of #193828 and #196948 and adds an EQL Query editable component with EQL Options fields (`event_category_override`, `timestamp_field` and `tiebreaker_field`) for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow. ## Details This PR make a set of changes to make existing EQL Query bar component easily reusable and type safe when used in forms. In particular the following was done - EQL query bar was wrapped in `EqlQueryEdit` component with `UseField` inside. It helps to make it type safe avoiding issues like passing invalid types to `EqlQueryBar`. `UseField` types component properties as `Record<string, any>` so potentially any refactoring can break some functionality. For example code in Timeline passes `DataViewSpec` where `DataViewBase` is expected while these two types aren't fully compatible. - Validation was added directly to `EqlQueryEdit`. Passing field configuration to `UseField` rewrites field configuration defined in from schema. It leads to cases when validation is defined in both form schema and as a field configuration for `UseFields`. Additionally we can reduce reusing complexity by incapsulating absolutely required validation in `EqlQueryEdit` component. - Empty string `tiebreakerField` was removed in Timelines. `tiebreakerField` is part of EQL options used for EQL validation. EQL validation endpoint `/internal/search/eql` returns an error when an empty string provided for `tiebreakerField`. This problem didn't surface earlier since It looks like EQL options weren't provided correctly before this PR. Timeline EQL validation requests were sent without EQL options. ## How to test The simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below - Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled - Run Kibana locally - Install an EQL prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e` - Patch the installed rule by running a query below ```bash curl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H "elastic-api-version: 2023-10-31" -d '{"rule_id":"2a692072-d78d-42f3-a48a-775677d79c4e","version":1,"query":"process where process.name == \"cmd.exe\"","language":"eql","event_category_override": "test","timestamp_field": "@timestamp","tiebreaker_field": "tiebreaker"}' http://localhost:5601/kbn/api/detection_engine/rules ``` - Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button ## Screenshots - EQL Query in Prebuilt Rules Update workflow <img width="2560" alt="image" src="https://github.com/user-attachments/assets/59d157b2-6aca-4b21-95d0-f71a2e174df2"> - event_category_override + tiebreaker_field + timestamp_field (aka EQL options) in Prebuilt Rules Update workflow <img width="2552" alt="image" src="https://github.com/user-attachments/assets/1886d3b4-98f9-40a7-954c-2a6d4b8e925a"> - Examples of invalid EQL <img width="2560" alt="image" src="https://github.com/user-attachments/assets/d584deca-7903-45c5-9499-718552df441c"> <img width="2548" alt="image" src="https://github.com/user-attachments/assets/b734e22c-ab62-4624-85d0-e4e6dbb9d523">
maximpn
added a commit
to maximpn/kibana
that referenced
this pull request
Nov 22, 2024
… fields (elastic#199115) **Partially addresses:** elastic#171520 ## Summary This PR adds is built on top of elastic#193828 and elastic#196948 and adds an EQL Query editable component with EQL Options fields (`event_category_override`, `timestamp_field` and `tiebreaker_field`) for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow. ## Details This PR make a set of changes to make existing EQL Query bar component easily reusable and type safe when used in forms. In particular the following was done - EQL query bar was wrapped in `EqlQueryEdit` component with `UseField` inside. It helps to make it type safe avoiding issues like passing invalid types to `EqlQueryBar`. `UseField` types component properties as `Record<string, any>` so potentially any refactoring can break some functionality. For example code in Timeline passes `DataViewSpec` where `DataViewBase` is expected while these two types aren't fully compatible. - Validation was added directly to `EqlQueryEdit`. Passing field configuration to `UseField` rewrites field configuration defined in from schema. It leads to cases when validation is defined in both form schema and as a field configuration for `UseFields`. Additionally we can reduce reusing complexity by incapsulating absolutely required validation in `EqlQueryEdit` component. - Empty string `tiebreakerField` was removed in Timelines. `tiebreakerField` is part of EQL options used for EQL validation. EQL validation endpoint `/internal/search/eql` returns an error when an empty string provided for `tiebreakerField`. This problem didn't surface earlier since It looks like EQL options weren't provided correctly before this PR. Timeline EQL validation requests were sent without EQL options. ## How to test The simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below - Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled - Run Kibana locally - Install an EQL prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e` - Patch the installed rule by running a query below ```bash curl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H "elastic-api-version: 2023-10-31" -d '{"rule_id":"2a692072-d78d-42f3-a48a-775677d79c4e","version":1,"query":"process where process.name == \"cmd.exe\"","language":"eql","event_category_override": "test","timestamp_field": "@timestamp","tiebreaker_field": "tiebreaker"}' http://localhost:5601/kbn/api/detection_engine/rules ``` - Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button ## Screenshots - EQL Query in Prebuilt Rules Update workflow <img width="2560" alt="image" src="https://github.com/user-attachments/assets/59d157b2-6aca-4b21-95d0-f71a2e174df2"> - event_category_override + tiebreaker_field + timestamp_field (aka EQL options) in Prebuilt Rules Update workflow <img width="2552" alt="image" src="https://github.com/user-attachments/assets/1886d3b4-98f9-40a7-954c-2a6d4b8e925a"> - Examples of invalid EQL <img width="2560" alt="image" src="https://github.com/user-attachments/assets/d584deca-7903-45c5-9499-718552df441c"> <img width="2548" alt="image" src="https://github.com/user-attachments/assets/b734e22c-ab62-4624-85d0-e4e6dbb9d523"> (cherry picked from commit c0c803c) # Conflicts: # x-pack/plugins/security_solution/public/timelines/components/timeline/query_bar/eql/index.tsx
maximpn
added a commit
that referenced
this pull request
Nov 22, 2024
…ptions fields (#199115) (#201314) # Backport This will backport the following commits from `main` to `8.x`: - [[Security Solution] Add EQL query editable component with EQL options fields (#199115)](#199115) <!--- Backport version: 8.9.8 --> ### Questions ? Please refer to the [Backport tool documentation](https://github.com/sqren/backport) <!--BACKPORT [{"author":{"name":"Maxim Palenov","email":"maxim.palenov@elastic.co"},"sourceCommit":{"committedDate":"2024-11-22T07:27:40Z","message":"[Security Solution] Add EQL query editable component with EQL options fields (#199115)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and #196948 and adds an EQL Query editable component with EQL Options fields (`event_category_override`, `timestamp_field` and `tiebreaker_field`) for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nThis PR make a set of changes to make existing EQL Query bar component easily reusable and type safe when used in forms. In particular the following was done\r\n\r\n- EQL query bar was wrapped in `EqlQueryEdit` component with `UseField` inside. It helps to make it type safe avoiding issues like passing invalid types to `EqlQueryBar`. `UseField` types component properties as `Record<string, any>` so potentially any refactoring can break some functionality. For example code in Timeline passes `DataViewSpec` where `DataViewBase` is expected while these two types aren't fully compatible.\r\n- Validation was added directly to `EqlQueryEdit`. Passing field configuration to `UseField` rewrites field configuration defined in from schema. It leads to cases when validation is defined in both form schema and as a field configuration for `UseFields`. Additionally we can reduce reusing complexity by incapsulating absolutely required validation in `EqlQueryEdit` component.\r\n- Empty string `tiebreakerField` was removed in Timelines. `tiebreakerField` is part of EQL options used for EQL validation. EQL validation endpoint `/internal/search/eql` returns an error when an empty string provided for `tiebreakerField`. This problem didn't surface earlier since It looks like EQL options weren't provided correctly before this PR. Timeline EQL validation requests were sent without EQL options.\r\n\r\n## How to test\r\n\r\nThe simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below\r\n\r\n- Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled\r\n- Run Kibana locally\r\n- Install an EQL prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e`\r\n- Patch the installed rule by running a query below\r\n\r\n```bash\r\ncurl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H \"elastic-api-version: 2023-10-31\" -d '{\"rule_id\":\"2a692072-d78d-42f3-a48a-775677d79c4e\",\"version\":1,\"query\":\"process where process.name == \\\"cmd.exe\\\"\",\"language\":\"eql\",\"event_category_override\": \"test\",\"timestamp_field\": \"@timestamp\",\"tiebreaker_field\": \"tiebreaker\"}' http://localhost:5601/kbn/api/detection_engine/rules\r\n```\r\n\r\n- Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button\r\n\r\n## Screenshots\r\n\r\n- EQL Query in Prebuilt Rules Update workflow\r\n<img width=\"2560\" alt=\"image\" src=\"https://github.com/user-attachments/assets/59d157b2-6aca-4b21-95d0-f71a2e174df2\">\r\n\r\n- event_category_override + tiebreaker_field + timestamp_field (aka EQL options) in Prebuilt Rules Update workflow\r\n<img width=\"2552\" alt=\"image\" src=\"https://github.com/user-attachments/assets/1886d3b4-98f9-40a7-954c-2a6d4b8e925a\">\r\n\r\n- Examples of invalid EQL\r\n<img width=\"2560\" alt=\"image\" src=\"https://github.com/user-attachments/assets/d584deca-7903-45c5-9499-718552df441c\">\r\n\r\n<img width=\"2548\" alt=\"image\" src=\"https://github.com/user-attachments/assets/b734e22c-ab62-4624-85d0-e4e6dbb9d523\">","sha":"c0c803c8830c10f1df1b204a7d7b859f1f584991","branchLabelMapping":{"^v9.0.0$":"main","^v8.18.0$":"8.x","^v(\\d+).(\\d+).\\d+$":"$1.$2"}},"sourcePullRequest":{"labels":["release_note:skip","v9.0.0","Team:Detections and Resp","Team: SecuritySolution","Team:Detection Rule Management","Feature:Prebuilt Detection Rules","backport:version","v8.18.0"],"number":199115,"url":"https://github.com/elastic/kibana/pull/199115","mergeCommit":{"message":"[Security Solution] Add EQL query editable component with EQL options fields (#199115)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and #196948 and adds an EQL Query editable component with EQL Options fields (`event_category_override`, `timestamp_field` and `tiebreaker_field`) for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nThis PR make a set of changes to make existing EQL Query bar component easily reusable and type safe when used in forms. In particular the following was done\r\n\r\n- EQL query bar was wrapped in `EqlQueryEdit` component with `UseField` inside. It helps to make it type safe avoiding issues like passing invalid types to `EqlQueryBar`. `UseField` types component properties as `Record<string, any>` so potentially any refactoring can break some functionality. For example code in Timeline passes `DataViewSpec` where `DataViewBase` is expected while these two types aren't fully compatible.\r\n- Validation was added directly to `EqlQueryEdit`. Passing field configuration to `UseField` rewrites field configuration defined in from schema. It leads to cases when validation is defined in both form schema and as a field configuration for `UseFields`. Additionally we can reduce reusing complexity by incapsulating absolutely required validation in `EqlQueryEdit` component.\r\n- Empty string `tiebreakerField` was removed in Timelines. `tiebreakerField` is part of EQL options used for EQL validation. EQL validation endpoint `/internal/search/eql` returns an error when an empty string provided for `tiebreakerField`. This problem didn't surface earlier since It looks like EQL options weren't provided correctly before this PR. Timeline EQL validation requests were sent without EQL options.\r\n\r\n## How to test\r\n\r\nThe simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below\r\n\r\n- Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled\r\n- Run Kibana locally\r\n- Install an EQL prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e`\r\n- Patch the installed rule by running a query below\r\n\r\n```bash\r\ncurl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H \"elastic-api-version: 2023-10-31\" -d '{\"rule_id\":\"2a692072-d78d-42f3-a48a-775677d79c4e\",\"version\":1,\"query\":\"process where process.name == \\\"cmd.exe\\\"\",\"language\":\"eql\",\"event_category_override\": \"test\",\"timestamp_field\": \"@timestamp\",\"tiebreaker_field\": \"tiebreaker\"}' http://localhost:5601/kbn/api/detection_engine/rules\r\n```\r\n\r\n- Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button\r\n\r\n## Screenshots\r\n\r\n- EQL Query in Prebuilt Rules Update workflow\r\n<img width=\"2560\" alt=\"image\" src=\"https://github.com/user-attachments/assets/59d157b2-6aca-4b21-95d0-f71a2e174df2\">\r\n\r\n- event_category_override + tiebreaker_field + timestamp_field (aka EQL options) in Prebuilt Rules Update workflow\r\n<img width=\"2552\" alt=\"image\" src=\"https://github.com/user-attachments/assets/1886d3b4-98f9-40a7-954c-2a6d4b8e925a\">\r\n\r\n- Examples of invalid EQL\r\n<img width=\"2560\" alt=\"image\" src=\"https://github.com/user-attachments/assets/d584deca-7903-45c5-9499-718552df441c\">\r\n\r\n<img width=\"2548\" alt=\"image\" src=\"https://github.com/user-attachments/assets/b734e22c-ab62-4624-85d0-e4e6dbb9d523\">","sha":"c0c803c8830c10f1df1b204a7d7b859f1f584991"}},"sourceBranch":"main","suggestedTargetBranches":["8.x"],"targetPullRequestStates":[{"branch":"main","label":"v9.0.0","labelRegex":"^v9.0.0$","isSourceBranch":true,"state":"MERGED","url":"https://github.com/elastic/kibana/pull/199115","number":199115,"mergeCommit":{"message":"[Security Solution] Add EQL query editable component with EQL options fields (#199115)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and #196948 and adds an EQL Query editable component with EQL Options fields (`event_category_override`, `timestamp_field` and `tiebreaker_field`) for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nThis PR make a set of changes to make existing EQL Query bar component easily reusable and type safe when used in forms. In particular the following was done\r\n\r\n- EQL query bar was wrapped in `EqlQueryEdit` component with `UseField` inside. It helps to make it type safe avoiding issues like passing invalid types to `EqlQueryBar`. `UseField` types component properties as `Record<string, any>` so potentially any refactoring can break some functionality. For example code in Timeline passes `DataViewSpec` where `DataViewBase` is expected while these two types aren't fully compatible.\r\n- Validation was added directly to `EqlQueryEdit`. Passing field configuration to `UseField` rewrites field configuration defined in from schema. It leads to cases when validation is defined in both form schema and as a field configuration for `UseFields`. Additionally we can reduce reusing complexity by incapsulating absolutely required validation in `EqlQueryEdit` component.\r\n- Empty string `tiebreakerField` was removed in Timelines. `tiebreakerField` is part of EQL options used for EQL validation. EQL validation endpoint `/internal/search/eql` returns an error when an empty string provided for `tiebreakerField`. This problem didn't surface earlier since It looks like EQL options weren't provided correctly before this PR. Timeline EQL validation requests were sent without EQL options.\r\n\r\n## How to test\r\n\r\nThe simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below\r\n\r\n- Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled\r\n- Run Kibana locally\r\n- Install an EQL prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e`\r\n- Patch the installed rule by running a query below\r\n\r\n```bash\r\ncurl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H \"elastic-api-version: 2023-10-31\" -d '{\"rule_id\":\"2a692072-d78d-42f3-a48a-775677d79c4e\",\"version\":1,\"query\":\"process where process.name == \\\"cmd.exe\\\"\",\"language\":\"eql\",\"event_category_override\": \"test\",\"timestamp_field\": \"@timestamp\",\"tiebreaker_field\": \"tiebreaker\"}' http://localhost:5601/kbn/api/detection_engine/rules\r\n```\r\n\r\n- Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button\r\n\r\n## Screenshots\r\n\r\n- EQL Query in Prebuilt Rules Update workflow\r\n<img width=\"2560\" alt=\"image\" src=\"https://github.com/user-attachments/assets/59d157b2-6aca-4b21-95d0-f71a2e174df2\">\r\n\r\n- event_category_override + tiebreaker_field + timestamp_field (aka EQL options) in Prebuilt Rules Update workflow\r\n<img width=\"2552\" alt=\"image\" src=\"https://github.com/user-attachments/assets/1886d3b4-98f9-40a7-954c-2a6d4b8e925a\">\r\n\r\n- Examples of invalid EQL\r\n<img width=\"2560\" alt=\"image\" src=\"https://github.com/user-attachments/assets/d584deca-7903-45c5-9499-718552df441c\">\r\n\r\n<img width=\"2548\" alt=\"image\" src=\"https://github.com/user-attachments/assets/b734e22c-ab62-4624-85d0-e4e6dbb9d523\">","sha":"c0c803c8830c10f1df1b204a7d7b859f1f584991"}},{"branch":"8.x","label":"v8.18.0","labelRegex":"^v8.18.0$","isSourceBranch":false,"state":"NOT_CREATED"}]}] BACKPORT-->
paulinashakirova
pushed a commit
to paulinashakirova/kibana
that referenced
this pull request
Nov 26, 2024
… fields (elastic#199115) **Partially addresses:** elastic#171520 ## Summary This PR adds is built on top of elastic#193828 and elastic#196948 and adds an EQL Query editable component with EQL Options fields (`event_category_override`, `timestamp_field` and `tiebreaker_field`) for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow. ## Details This PR make a set of changes to make existing EQL Query bar component easily reusable and type safe when used in forms. In particular the following was done - EQL query bar was wrapped in `EqlQueryEdit` component with `UseField` inside. It helps to make it type safe avoiding issues like passing invalid types to `EqlQueryBar`. `UseField` types component properties as `Record<string, any>` so potentially any refactoring can break some functionality. For example code in Timeline passes `DataViewSpec` where `DataViewBase` is expected while these two types aren't fully compatible. - Validation was added directly to `EqlQueryEdit`. Passing field configuration to `UseField` rewrites field configuration defined in from schema. It leads to cases when validation is defined in both form schema and as a field configuration for `UseFields`. Additionally we can reduce reusing complexity by incapsulating absolutely required validation in `EqlQueryEdit` component. - Empty string `tiebreakerField` was removed in Timelines. `tiebreakerField` is part of EQL options used for EQL validation. EQL validation endpoint `/internal/search/eql` returns an error when an empty string provided for `tiebreakerField`. This problem didn't surface earlier since It looks like EQL options weren't provided correctly before this PR. Timeline EQL validation requests were sent without EQL options. ## How to test The simplest way to test is via patching installed prebuilt rules via Rule Patch API. Please follow steps below - Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled - Run Kibana locally - Install an EQL prebuilt rule, e.g. `Potential Code Execution via Postgresql` with rule_id `2a692072-d78d-42f3-a48a-775677d79c4e` - Patch the installed rule by running a query below ```bash curl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H "elastic-api-version: 2023-10-31" -d '{"rule_id":"2a692072-d78d-42f3-a48a-775677d79c4e","version":1,"query":"process where process.name == \"cmd.exe\"","language":"eql","event_category_override": "test","timestamp_field": "@timestamp","tiebreaker_field": "tiebreaker"}' http://localhost:5601/kbn/api/detection_engine/rules ``` - Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `Potential Code Execution via Postgresql` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button ## Screenshots - EQL Query in Prebuilt Rules Update workflow <img width="2560" alt="image" src="https://github.com/user-attachments/assets/59d157b2-6aca-4b21-95d0-f71a2e174df2"> - event_category_override + tiebreaker_field + timestamp_field (aka EQL options) in Prebuilt Rules Update workflow <img width="2552" alt="image" src="https://github.com/user-attachments/assets/1886d3b4-98f9-40a7-954c-2a6d4b8e925a"> - Examples of invalid EQL <img width="2560" alt="image" src="https://github.com/user-attachments/assets/d584deca-7903-45c5-9499-718552df441c"> <img width="2548" alt="image" src="https://github.com/user-attachments/assets/b734e22c-ab62-4624-85d0-e4e6dbb9d523">
maximpn
added a commit
that referenced
this pull request
Nov 28, 2024
**Partially addresses:** #171520 ## Summary This PR adds is built on top of #193828 and #196948 and adds an ES|QL Query editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow. ## Details This PR extracts ES|QL Query edit component from Define rule form step and makes it reusable. The following changes were made - ES|QL validator was refactored and covered by unit tests - Query persistence was addressed and covered by tests (previous functionality didn't work out of the box and didn't have tests) ## How to test The simplest way to test is via patching installed prebuilt rules (a.k.a. downgrading a prebuilt rule) via Rule Patch API. Please follow steps below - Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled - Run Kibana locally - Install an ES|QL prebuilt rule, e.g. `AWS Bedrock Guardrails Detected Multiple Violations by a Single User Over a Session` with rule_id `0cd2f3e6-41da-40e6-b28b-466f688f00a6` - Patch the installed rule by running a query below ```bash curl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H "elastic-api-version: 2023-10-31" -d '{"rule_id":"0cd2f3e6-41da-40e6-b28b-466f688f00a6","version":1,"query":"from logs-*","language":"esql"}' http://localhost:5601/kbn/api/detection_engine/rules ``` - Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `AWS Bedrock Guardrails Detected Multiple Violations by a Single User Over a Session` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button ## Screenshots <img width="2550" alt="image" src="https://github.com/user-attachments/assets/f65d04d5-9fd9-4d3f-8741-eba04a3be8a6"> <img width="2552" alt="image" src="https://github.com/user-attachments/assets/dd0a2613-5262-44b2-bbeb-d0ed34d57d9c">
maximpn
added a commit
to maximpn/kibana
that referenced
this pull request
Nov 28, 2024
**Partially addresses:** elastic#171520 ## Summary This PR adds is built on top of elastic#193828 and elastic#196948 and adds an ES|QL Query editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow. ## Details This PR extracts ES|QL Query edit component from Define rule form step and makes it reusable. The following changes were made - ES|QL validator was refactored and covered by unit tests - Query persistence was addressed and covered by tests (previous functionality didn't work out of the box and didn't have tests) ## How to test The simplest way to test is via patching installed prebuilt rules (a.k.a. downgrading a prebuilt rule) via Rule Patch API. Please follow steps below - Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled - Run Kibana locally - Install an ES|QL prebuilt rule, e.g. `AWS Bedrock Guardrails Detected Multiple Violations by a Single User Over a Session` with rule_id `0cd2f3e6-41da-40e6-b28b-466f688f00a6` - Patch the installed rule by running a query below ```bash curl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H "elastic-api-version: 2023-10-31" -d '{"rule_id":"0cd2f3e6-41da-40e6-b28b-466f688f00a6","version":1,"query":"from logs-*","language":"esql"}' http://localhost:5601/kbn/api/detection_engine/rules ``` - Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `AWS Bedrock Guardrails Detected Multiple Violations by a Single User Over a Session` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button ## Screenshots <img width="2550" alt="image" src="https://github.com/user-attachments/assets/f65d04d5-9fd9-4d3f-8741-eba04a3be8a6"> <img width="2552" alt="image" src="https://github.com/user-attachments/assets/dd0a2613-5262-44b2-bbeb-d0ed34d57d9c"> (cherry picked from commit e55232f) # Conflicts: # x-pack/plugins/security_solution/public/detection_engine/rule_creation/logic/esql_validator.test.ts # x-pack/plugins/security_solution/public/detection_engine/rule_creation/logic/esql_validator.ts # x-pack/plugins/translations/translations/zh-CN.json
maximpn
added a commit
that referenced
this pull request
Nov 29, 2024
#202224) # Backport This will backport the following commits from `main` to `8.x`: - [[Security Solution] Add ES|QL Query editable component (#199887)](#199887) <!--- Backport version: 8.9.8 --> ### Questions ? Please refer to the [Backport tool documentation](https://github.com/sqren/backport) <!--BACKPORT [{"author":{"name":"Maxim Palenov","email":"maxim.palenov@elastic.co"},"sourceCommit":{"committedDate":"2024-11-28T14:48:48Z","message":"[Security Solution] Add ES|QL Query editable component (#199887)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and #196948 and adds an ES|QL Query editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nThis PR extracts ES|QL Query edit component from Define rule form step and makes it reusable. The following changes were made\r\n\r\n- ES|QL validator was refactored and covered by unit tests\r\n- Query persistence was addressed and covered by tests (previous functionality didn't work out of the box and didn't have tests)\r\n\r\n## How to test\r\n\r\nThe simplest way to test is via patching installed prebuilt rules (a.k.a. downgrading a prebuilt rule) via Rule Patch API. Please follow steps below\r\n\r\n- Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled\r\n- Run Kibana locally\r\n- Install an ES|QL prebuilt rule, e.g. `AWS Bedrock Guardrails Detected Multiple Violations by a Single User Over a Session` with rule_id `0cd2f3e6-41da-40e6-b28b-466f688f00a6`\r\n- Patch the installed rule by running a query below\r\n\r\n```bash\r\ncurl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H \"elastic-api-version: 2023-10-31\" -d '{\"rule_id\":\"0cd2f3e6-41da-40e6-b28b-466f688f00a6\",\"version\":1,\"query\":\"from logs-*\",\"language\":\"esql\"}' http://localhost:5601/kbn/api/detection_engine/rules\r\n```\r\n\r\n- Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `AWS Bedrock Guardrails Detected Multiple Violations by a Single User Over a Session` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button\r\n\r\n## Screenshots\r\n\r\n<img width=\"2550\" alt=\"image\" src=\"https://github.com/user-attachments/assets/f65d04d5-9fd9-4d3f-8741-eba04a3be8a6\">\r\n\r\n<img width=\"2552\" alt=\"image\" src=\"https://github.com/user-attachments/assets/dd0a2613-5262-44b2-bbeb-d0ed34d57d9c\">","sha":"e55232f87732594eb9502993766203a219be44db","branchLabelMapping":{"^v9.0.0$":"main","^v8.18.0$":"8.x","^v(\\d+).(\\d+).\\d+$":"$1.$2"}},"sourcePullRequest":{"labels":["release_note:skip","v9.0.0","Team:Detections and Resp","Team: SecuritySolution","Team:Detection Rule Management","Feature:Prebuilt Detection Rules","backport:version","v8.18.0"],"number":199887,"url":"https://github.com/elastic/kibana/pull/199887","mergeCommit":{"message":"[Security Solution] Add ES|QL Query editable component (#199887)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and #196948 and adds an ES|QL Query editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nThis PR extracts ES|QL Query edit component from Define rule form step and makes it reusable. The following changes were made\r\n\r\n- ES|QL validator was refactored and covered by unit tests\r\n- Query persistence was addressed and covered by tests (previous functionality didn't work out of the box and didn't have tests)\r\n\r\n## How to test\r\n\r\nThe simplest way to test is via patching installed prebuilt rules (a.k.a. downgrading a prebuilt rule) via Rule Patch API. Please follow steps below\r\n\r\n- Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled\r\n- Run Kibana locally\r\n- Install an ES|QL prebuilt rule, e.g. `AWS Bedrock Guardrails Detected Multiple Violations by a Single User Over a Session` with rule_id `0cd2f3e6-41da-40e6-b28b-466f688f00a6`\r\n- Patch the installed rule by running a query below\r\n\r\n```bash\r\ncurl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H \"elastic-api-version: 2023-10-31\" -d '{\"rule_id\":\"0cd2f3e6-41da-40e6-b28b-466f688f00a6\",\"version\":1,\"query\":\"from logs-*\",\"language\":\"esql\"}' http://localhost:5601/kbn/api/detection_engine/rules\r\n```\r\n\r\n- Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `AWS Bedrock Guardrails Detected Multiple Violations by a Single User Over a Session` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button\r\n\r\n## Screenshots\r\n\r\n<img width=\"2550\" alt=\"image\" src=\"https://github.com/user-attachments/assets/f65d04d5-9fd9-4d3f-8741-eba04a3be8a6\">\r\n\r\n<img width=\"2552\" alt=\"image\" src=\"https://github.com/user-attachments/assets/dd0a2613-5262-44b2-bbeb-d0ed34d57d9c\">","sha":"e55232f87732594eb9502993766203a219be44db"}},"sourceBranch":"main","suggestedTargetBranches":["8.x"],"targetPullRequestStates":[{"branch":"main","label":"v9.0.0","labelRegex":"^v9.0.0$","isSourceBranch":true,"state":"MERGED","url":"https://github.com/elastic/kibana/pull/199887","number":199887,"mergeCommit":{"message":"[Security Solution] Add ES|QL Query editable component (#199887)\n\n**Partially addresses:** https://github.com/elastic/kibana/issues/171520\r\n\r\n## Summary\r\n\r\nThis PR adds is built on top of #193828 and #196948 and adds an ES|QL Query editable component for Three Way Diff tab's final edit side of the upgrade prebuilt rule workflow.\r\n\r\n## Details\r\n\r\nThis PR extracts ES|QL Query edit component from Define rule form step and makes it reusable. The following changes were made\r\n\r\n- ES|QL validator was refactored and covered by unit tests\r\n- Query persistence was addressed and covered by tests (previous functionality didn't work out of the box and didn't have tests)\r\n\r\n## How to test\r\n\r\nThe simplest way to test is via patching installed prebuilt rules (a.k.a. downgrading a prebuilt rule) via Rule Patch API. Please follow steps below\r\n\r\n- Ensure the `prebuiltRulesCustomizationEnabled` feature flag is enabled\r\n- Run Kibana locally\r\n- Install an ES|QL prebuilt rule, e.g. `AWS Bedrock Guardrails Detected Multiple Violations by a Single User Over a Session` with rule_id `0cd2f3e6-41da-40e6-b28b-466f688f00a6`\r\n- Patch the installed rule by running a query below\r\n\r\n```bash\r\ncurl -X PATCH --user elastic:changeme -H 'Content-Type: application/json' -H 'kbn-xsrf: 123' -H \"elastic-api-version: 2023-10-31\" -d '{\"rule_id\":\"0cd2f3e6-41da-40e6-b28b-466f688f00a6\",\"version\":1,\"query\":\"from logs-*\",\"language\":\"esql\"}' http://localhost:5601/kbn/api/detection_engine/rules\r\n```\r\n\r\n- Open `Detection Rules (SIEM)` Page -> `Rule Updates` -> click on `AWS Bedrock Guardrails Detected Multiple Violations by a Single User Over a Session` rule -> expand `EQL Query` to see EQL Query -> press `Edit` button\r\n\r\n## Screenshots\r\n\r\n<img width=\"2550\" alt=\"image\" src=\"https://github.com/user-attachments/assets/f65d04d5-9fd9-4d3f-8741-eba04a3be8a6\">\r\n\r\n<img width=\"2552\" alt=\"image\" src=\"https://github.com/user-attachments/assets/dd0a2613-5262-44b2-bbeb-d0ed34d57d9c\">","sha":"e55232f87732594eb9502993766203a219be44db"}},{"branch":"8.x","label":"v8.18.0","labelRegex":"^v8.18.0$","isSourceBranch":false,"state":"NOT_CREATED"}]}] BACKPORT-->
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Labels
backport:prev-minor
Backport to (8.x) the previous minor version (i.e. one version back from main)
Feature:Prebuilt Detection Rules
Security Solution Prebuilt Detection Rules area
release_note:skip
Skip the PR/issue when compiling release notes
Team:Detection Rule Management
Security Detection Rule Management Team
Team:Detections and Resp
Security Detection Response Team
Team: SecuritySolution
Security Solutions Team working on SIEM, Endpoint, Timeline, Resolver, etc.
v8.16.0
v9.0.0
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.

Partially addresses: #171520
Is a follow-up PR to: #192342
Summary
Changes:
nameandkql_queryfieldsFieldFormWrappercomponent that abstracts away form creation and data preparation for each field