diff --git a/README.md b/README.md
index 237bb9ab..41faca10 100644
--- a/README.md
+++ b/README.md
@@ -1,17 +1,17 @@
-# BruteForceSettings
-
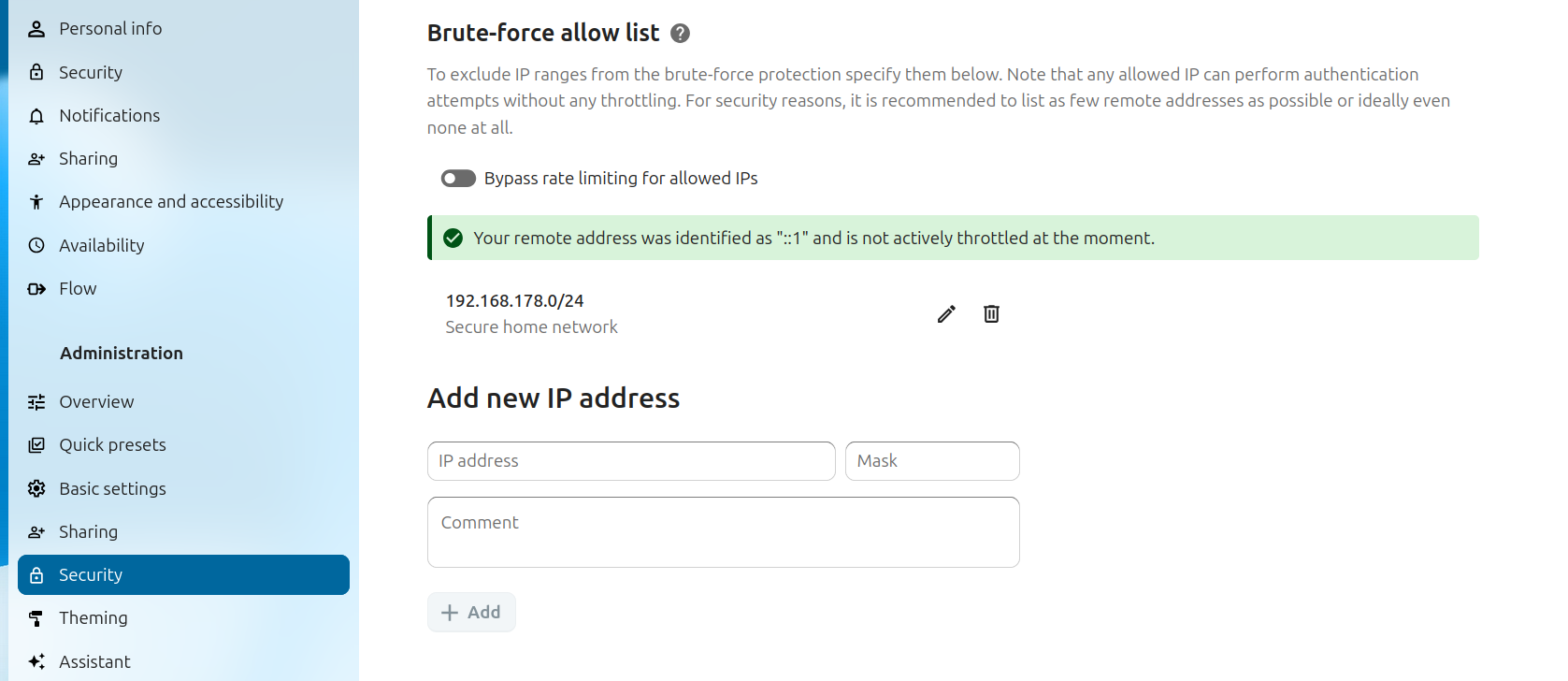
-This app provides the possibility to manage some settings of the brute force protection in Nextcloud.
-
-- [See app in NC AppStore](https://apps.nextcloud.com/apps/bruteforcesettings)
-
-## Screenshot
-
-
-
-## Description
-
-Brute Force Protection is meant to protect Nextcloud servers from attempts to guess user passwords in various ways. Besides the obvious "*let's try a big list of commonly used passwords*" attack, it also makes it harder to use slightly more sophisticated attacks via the reset password form or trying to find app password tokens.
-
-If triggered, brute force protection makes requests coming from an IP on a bruteforce protected controller with the same API slower for a 24 hour period.
-
-With this app, the admin can exempt an IP address or range from this protection which can be useful for testing purposes or when there are false positives due to a lot of users on one IP address.
+# BruteForceSettings
+
+This app provides the possibility to manage some settings of the brute force protection in Nextcloud.
+
+- [See app in NC AppStore](https://apps.nextcloud.com/apps/bruteforcesettings)
+
+## Screenshot
+
+
+
+## Description
+
+Brute Force Protection is meant to protect Nextcloud servers from attempts to guess passwords and tokens in various ways. Besides the obvious "*let's try a big list of commonly used passwords*" attack, it also makes it harder to use slightly more sophisticated attacks via the reset password form or trying to find app password tokens.
+
+If triggered, brute force protection makes requests coming from an IP on a bruteforce protected controller with the same API slower for a 24 hour period.
+
+With this app, the admin can exempt an IP address or range from this protection which can be useful for testing purposes or when there are false positives due to a lot of people on a single IP address.
diff --git a/appinfo/info.xml b/appinfo/info.xml
index e10465f2..b76589f2 100644
--- a/appinfo/info.xml
+++ b/appinfo/info.xml
@@ -4,7 +4,7 @@
Brute-force settings
Whitelist IPs
+positives due to a lot of accounts on one IP address.]]>
2.5.0
agpl
Roeland Jago Douma