-
Notifications
You must be signed in to change notification settings - Fork 313
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Agent: add new secrets capability to implement secret storage
#5348
Merged
olafurpg
merged 1 commit into
main
from
olafurpg-cody-3509-use-webview-for-authentication-2
Aug 27, 2024
Merged
Agent: add new secrets capability to implement secret storage
#5348
olafurpg
merged 1 commit into
main
from
olafurpg-cody-3509-use-webview-for-authentication-2
Aug 27, 2024
Conversation
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
Previously, the agent only supported stateless secret storage, where the agent server stored secrets in a temporary hashmap that was lost whenever the agent started. Now, clients can optionally declare that they're able to store secrets using the `secrets: 'client-managed'` capability. With this new capability, client can store/retrieve/delete/change secrets using the new JSON-RPC methods: * `secrets/get` * `secrets/store` * `secrets/delete` * `secrets/didChange`
077aaf0 to
59f3458
Compare
abeatrix
approved these changes
Aug 27, 2024
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Lgtm this would be super helpful with the authentication capabilities!
jamesmcnamara
approved these changes
Aug 27, 2024
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Nice! Agent code is finally starting to look straightforward to me.
3 tasks
abeatrix
added a commit
that referenced
this pull request
Sep 4, 2024
…ctions (#5325) Allows agent to set up HTTP server to listen for authentication redirections when agent capabilities for authentication are enabled. TODO: - [x] authentication url handler - [x] agent capability configuration - [x] work with secret storage (added by #5348) Follow-ups: - we should close the opened browser to refocus the webview if possible. ## Test plan <!-- Required. See https://docs-legacy.sourcegraph.com/dev/background-information/testing_principles. --> Example of this feature working in Visual Studio: https://github.com/user-attachments/assets/d21c8c2f-2667-426a-9c4d-991b7645d2e5 Updated onboarding view for non VS Code editors to support login with browser for enterprise: 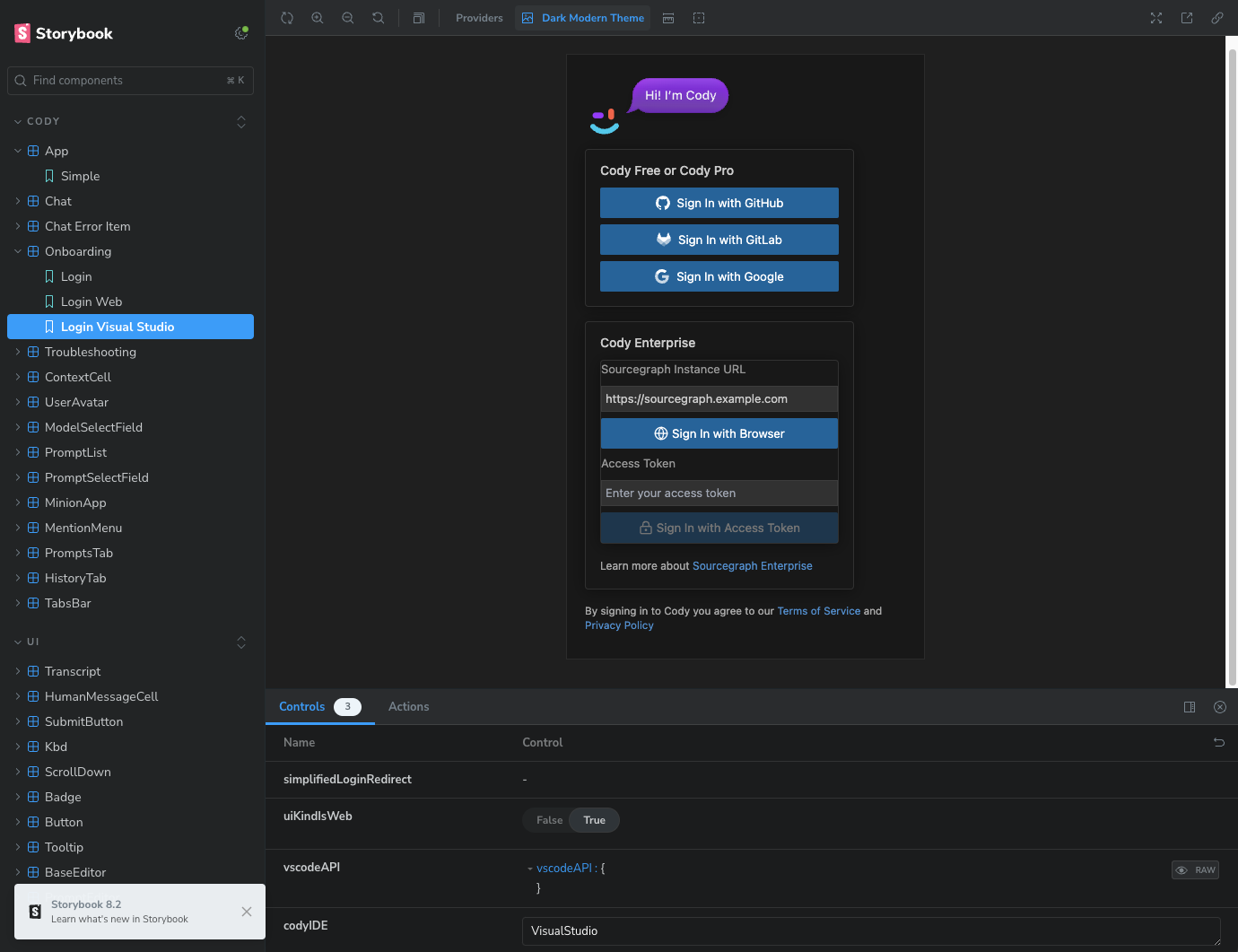 ## Changelog <!-- OPTIONAL; info at https://www.notion.so/sourcegraph/Writing-a-changelog-entry-dd997f411d524caabf0d8d38a24a878c -->
abeatrix
added a commit
to sourcegraph/cody-vs
that referenced
this pull request
Sep 6, 2024
CLOSE #72 https://linear.app/sourcegraph/issue/CODY-3619/implement-ivscredentialstorageservice-interface-for-storing-secrets https://linear.app/sourcegraph/issue/CODY-3618/agent-api-for-secret-storage-capability https://linear.app/sourcegraph/issue/CODY-3617/implement-agent-requests-for-secret-storage-capability Try logout and then log back into Cody to confirm you can now use token redirect and secret storage via Agent:  This PR enables client capability for authentication (added in sourcegraph/cody#5325) and secrets (added in sourcegraph/cody#5348) that allows users to use the native webview for authentication in Cody for Visual Studio. The protocols for secret storage operations have also been implemented and the secrets will be stored in [IVsCredentialStorageService](https://learn.microsoft.com/en-us/dotnet/api/microsoft.visualstudio.shell.connected.credentialstorage?view=visualstudiosdk-2017). Demo: https://github.com/user-attachments/assets/d21c8c2f-2667-426a-9c4d-991b7645d2e5 --------- Co-authored-by: Piotr Karczmarz <piotr@karczmarz.com>
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
Previously, the agent only supported stateless secret storage, where the agent server stored secrets in a temporary hashmap that was lost whenever the agent started. Now, clients can optionally declare that they're able to store secrets using the
secrets: 'client-managed'capability. With this new capability, client canstore/retrieve/delete/change secrets using the new JSON-RPC methods:
secrets/getsecrets/storesecrets/deletesecrets/didChangeHere's the PR moving to client-managed secrets for the Eclipse plugin, which allowed us to delete 600 lines of native UI code 😮 sourcegraph/eclipse#54
Test plan
This PR changes
TestClientto use client-managed secrets, so we're stressing this new code path in all the integration tests by default.Changelog