,
@@ -30,30 +41,77 @@ where
represents a co
## Security parameters
-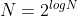: the ring dimension, which defines the degree of the cyclotomic polynomial, and the number of coefficients of the plaintext/ciphertext polynomials; it should always be a power of two. This parameter has an impact on both security and performance (security increases with N and performance decreases with N). It should be chosen carefully to suit the intended use of the scheme.
-
-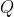: the ciphertext modulus. In Lattigo, it is chosen to be the product of a chain of small coprime moduli 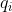 that verify 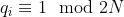 in order to enable both the RNS and NTT representation. The used moduli 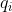 are chosen to be of size 30 to 60 bits for the best performance. This parameter has an impact on both security and performance (for a fixed 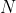, a larger 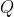 implies both lower security and lower performance). It is closely related to 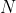 and should be carefully chosen to suit the intended use of the scheme.
-
-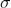: the variance used for the error polynomials. This parameter is closely tied to the security of the scheme (a larger 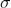 implies higher security).
+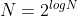: the ring dimension,
+which defines the degree of the cyclotomic polynomial, and the number of coefficients of the
+plaintext/ciphertext polynomials; it should always be a power of two. This parameter has an impact
+on both security and performance (security increases with N and performance decreases with N). It
+should be chosen carefully to suit the intended use of the scheme.
+
+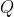: the ciphertext modulus. In Lattigo, it is
+chosen to be the product of a chain of small coprime moduli
+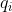 that verify
+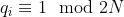 in order to
+enable both the RNS and NTT representation. The used moduli
+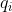 are chosen to be of size 30 to 60 bits for the
+best performance. This parameter has an impact on both security and performance (for a fixed
+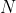, a larger
+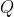 implies both lower security and lower
+performance). It is closely related to 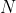 and
+should be carefully chosen to suit the intended use of the scheme.
+
+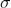: the variance used for the error
+polynomials. This parameter is closely tied to the security of the scheme (a larger
+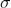 implies higher security).
## Other parameters
-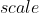: the plaintext scale. Since complex numbers are encoded on polynomials with integer coefficients, the original values must be scaled during the encoding, before being rounded to the nearest integer. The 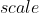 parameter is the power of two by which the values are multiplied during the encoding. It has an impact on the precision of the output and on the amount of operations a fresh encryption can undergo before overflowing.
+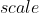: the plaintext scale. Since complex numbers
+are encoded on polynomials with integer coefficients, the original values must be scaled during the
+encoding, before being rounded to the nearest integer. The
+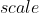 parameter is the power of two by which the
+values are multiplied during the encoding. It has an impact on the precision of the output and on
+the amount of operations a fresh encryption can undergo before overflowing.
## Choosing the right parameters for a given application
There are 3 application-dependent parameters:
-- **LogN**: it determines (a) how many values can be encoded (batched) at once (maximum N/2) in one plaintext, and (b) the maximum total modulus bit size (the product of all the moduli) for a given security parameter.
-- **Modulichain**: it determines how many consecutive scalar and non-scalar multiplications (the depth of the arithmetic circuit) can be evaluated before requiring decryption. Since Lattigo features an RNS implementation, this parameter requires careful fine-tuning depending on the application; i.e., the rescaling procedure can only rescale by one of the RNS modulus at a time, whose size has to be chosen when creating the CKKS context. Additionally, the individual size of each of the moduli also has an effect on the error introduced during the rescaling, since they cannot be powers of 2, so they should be chosen as NTT primes as close as possible to a power of 2 instead.
-- **Logscale**: it determines the scale of the plaintext, affecting both the precision and the maximum allowed depth for a given security parameter.
-
-Configuring parameters for CKKS is very application dependent, requiring a prior analysis of the circuit to be executed under encryption. The following example illustrates how this parametrization can be done, showing that it is possible to come up with different parameter sets for a given circuit, each set having pros and cons.
-
-Let us define the evaluation of an arbitrary smooth function f(x) on an array of ~4000 complex elements contained in a square of side 2 centered at the complex origin (with values ranging between -1-1i and 1+1i). We first need to find a good polynomial approximation for the given range. Lattigo provides an automatic Chebyshev approximation for any given polynomial degree, which can be used for this purpose (it is also possible to define a different polynomial approximation of lower degree with an acceptable error).
-
-Let us assume that we find an approximation of degree 5, i.e., *a + bx + cx^3 + dx^5*. This function can be evaluated with 3 scalar multiplications, 3 additions and 3 non-scalar multiplications, consuming a total of 4 levels (one for the scalar multiplications and 3 for the non-scalar multiplications).
-
-We then need to chose a scale for the plaintext, that will influence both the bit consumption for the rescaling, and the precision of the computation. If we choose a scale of 2^40, we need to consume at least 160 bits (4 levels) during the evaluation, and we still need some bits left to store the final result with an acceptable precision. Let us assume that the output of the approximation lies always in the square between -20-20i and 20+20i; then, the final modulus must be at least 5 bits larger than the final scale (to preserve the integer precision).
+- **LogN**: it determines (a) how many values can be encoded (batched) at once (maximum N/2) in one
+ plaintext, and (b) the maximum total modulus bit size (the product of all the moduli) for a given
+ security parameter.
+- **Modulichain**: it determines how many consecutive scalar and non-scalar multiplications (the
+ depth of the arithmetic circuit) can be evaluated before requiring decryption. Since Lattigo
+ features an RNS implementation, this parameter requires careful fine-tuning depending on the
+ application; i.e., the rescaling procedure can only rescale by one of the RNS modulus at a time,
+ whose size has to be chosen when creating the CKKS context. Additionally, the individual size of
+ each of the moduli also has an effect on the error introduced during the rescaling, since they
+ cannot be powers of 2, so they should be chosen as NTT primes as close as possible to a power of 2
+ instead.
+- **Logscale**: it determines the scale of the plaintext, affecting both the precision and the
+ maximum allowed depth for a given security parameter.
+
+Configuring parameters for CKKS is very application dependent, requiring a prior analysis of the
+circuit to be executed under encryption. The following example illustrates how this parametrization
+can be done, showing that it is possible to come up with different parameter sets for a given
+circuit, each set having pros and cons.
+
+Let us define the evaluation of an arbitrary smooth function f(x) on an array of ~4000 complex
+elements contained in a square of side 2 centered at the complex origin (with values ranging between
+-1-1i and 1+1i). We first need to find a good polynomial approximation for the given range. Lattigo
+provides an automatic Chebyshev approximation for any given polynomial degree, which can be used for
+this purpose (it is also possible to define a different polynomial approximation of lower degree
+with an acceptable error).
+
+Let us assume that we find an approximation of degree 5, i.e., *a + bx + cx^3 + dx^5*. This function
+can be evaluated with 3 scalar multiplications, 3 additions and 3 non-scalar multiplications,
+consuming a total of 4 levels (one for the scalar multiplications and 3 for the non-scalar
+multiplications).
+
+We then need to chose a scale for the plaintext, that will influence both the bit consumption for
+the rescaling, and the precision of the computation. If we choose a scale of 2^40, we need to
+consume at least 160 bits (4 levels) during the evaluation, and we still need some bits left to
+store the final result with an acceptable precision. Let us assume that the output of the
+approximation lies always in the square between -20-20i and 20+20i; then, the final modulus must be
+at least 5 bits larger than the final scale (to preserve the integer precision).
The following parameters will work for the posed example:
@@ -61,7 +119,11 @@ The following parameters will work for the posed example:
- **Modulichain** = [45, 40, 40, 40, 40], for a logQ <= 205
- **LogScale** = 40
-But it is also possible to use less levels to have ciphertexts of smaller size and, therefore, a faster evaluation, at the expense of less precision. This can be achieved by using a scale of 30 bits and squeezing two multiplications in a single level, while pre-computing the last scalar multiplication already in the plaintext. Instead of evaluating *a + bx + cx^3 + dx^5*, we pre-multiply the plaintext by d^(1/5) and evaluate *a + b/(d^(1/5))x + c/(d^(3/5)) + x^5*.
+But it is also possible to use less levels to have ciphertexts of smaller size and, therefore, a
+faster evaluation, at the expense of less precision. This can be achieved by using a scale of 30
+bits and squeezing two multiplications in a single level, while pre-computing the last scalar
+multiplication already in the plaintext. Instead of evaluating *a + bx + cx^3 + dx^5*, we
+pre-multiply the plaintext by d^(1/5) and evaluate *a + b/(d^(1/5))x + c/(d^(3/5)) + x^5*.
The following parameters are enough to evaluate this modified function:
@@ -69,19 +131,39 @@ The following parameters are enough to evaluate this modified function:
- **Modulichain** = [35, 60, 60], for a logQ <= 155
- **LogScale** = 30
-To summarize, several parameter sets can be used to evaluate a given function, achieving different trade-offs for space and time versus precision.
+To summarize, several parameter sets can be used to evaluate a given function, achieving different
+trade-offs for space and time versus precision.
## Choosing secure parameters
-The CKKS scheme supports the standard recommended parameters chosen to offer a security of 128 bits for a secret key with uniform ternary distribution 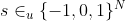, according to the Homomorphic Encryption Standards group (https://homomorphicencryption.org/standard/).
+The CKKS scheme supports the standard recommended parameters chosen to offer a security of 128 bits
+for a secret key with uniform ternary distribution
+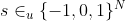,
+according to the Homomorphic Encryption Standards group
+(https://homomorphicencryption.org/standard/).
-Each set of security parameters is defined by the tuple 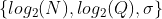 :
+Each set of security parameters is defined by the tuple
+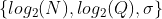
+:
- **{12, 109, 3.2}**
- **{13, 218, 3.2}**
- **{14, 438, 3.2}**
- **{15, 881, 3.2}**
-As mentioned, setting parameters for CKKS involves not only choosing this tuple, but also defining the actual moduli chain depending on the application at hand, which is why the provided default parameter sets have to be fine-tuned, preserving the values of the aforementioned tuples, in order to maintain the required security level of 128 bits. That is, Lattigo provides a set of default parameters for CKKS, including example moduli chains, ensuring 128 bit security. The user might want to choose different values in the moduli chain optimized for a specific application. As long as the total modulus is equal or below the above values for a given logN, the scheme will still provide a security of at least 128 bits against the current best known attacks.
-
-Finally, it is worth noting that these security parameters are computed for fully entropic ternary keys (with probability distribution {1/3,1/3,1/3} for values {-1,0,1}). Lattigo uses this fully-entropic key configuration by default. It is possible, though, to generate keys with lower entropy, by modifying their distribution to {(1-p)/2, p, (1-p)/2}, for any p between 0 and 1, which for p>>1/3 can result in low Hamming weight keys (*sparse* keys). *We recall that it has been shown that the security of sparse keys can be considerably lower than that of fully entropic keys, and the CKKS security parameters should be re-evaluated if sparse keys are used*.
+As mentioned, setting parameters for CKKS involves not only choosing this tuple, but also defining
+the actual moduli chain depending on the application at hand, which is why the provided default
+parameter sets have to be fine-tuned, preserving the values of the aforementioned tuples, in order
+to maintain the required security level of 128 bits. That is, Lattigo provides a set of default
+parameters for CKKS, including example moduli chains, ensuring 128 bit security. The user might want
+to choose different values in the moduli chain optimized for a specific application. As long as the
+total modulus is equal or below the above values for a given logN, the scheme will still provide a
+security of at least 128 bits against the current best known attacks.
+
+Finally, it is worth noting that these security parameters are computed for fully entropic ternary
+keys (with probability distribution {1/3,1/3,1/3} for values {-1,0,1}). Lattigo uses this
+fully-entropic key configuration by default. It is possible, though, to generate keys with lower
+entropy, by modifying their distribution to {(1-p)/2, p, (1-p)/2}, for any p between 0 and 1, which
+for p>>1/3 can result in low Hamming weight keys (*sparse* keys). *We recall that it has been shown
+that the security of sparse keys can be considerably lower than that of fully entropic keys, and the
+CKKS security parameters should be re-evaluated if sparse keys are used*.
diff --git a/ckks/advanced/evaluator.go b/ckks/advanced/evaluator.go
index a06f78cbc..2598b53a7 100644
--- a/ckks/advanced/evaluator.go
+++ b/ckks/advanced/evaluator.go
@@ -3,9 +3,9 @@ package advanced
import (
"math"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
// Evaluator is an interface embeding the ckks.Evaluator interface with
diff --git a/ckks/advanced/homomorphic_encoding.go b/ckks/advanced/homomorphic_encoding.go
index ccb97efb8..85f04371a 100644
--- a/ckks/advanced/homomorphic_encoding.go
+++ b/ckks/advanced/homomorphic_encoding.go
@@ -3,8 +3,8 @@ package advanced
import (
"math"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// LinearTransformType is a type used to distinguish different linear transformations.
diff --git a/ckks/advanced/homomorphic_encoding_test.go b/ckks/advanced/homomorphic_encoding_test.go
index c999cad5b..c725b2f8b 100644
--- a/ckks/advanced/homomorphic_encoding_test.go
+++ b/ckks/advanced/homomorphic_encoding_test.go
@@ -5,11 +5,11 @@ import (
"runtime"
"testing"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
"github.com/stretchr/testify/assert"
"github.com/stretchr/testify/require"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
var printPrecisionStats = flag.Bool("print-precision", false, "print precision stats")
diff --git a/ckks/advanced/homomorphic_mod.go b/ckks/advanced/homomorphic_mod.go
index 01086de23..a5a61c952 100644
--- a/ckks/advanced/homomorphic_mod.go
+++ b/ckks/advanced/homomorphic_mod.go
@@ -4,8 +4,8 @@ import (
"math"
"math/cmplx"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// SineType is the type of function used during the bootstrapping
diff --git a/ckks/advanced/homomorphic_mod_test.go b/ckks/advanced/homomorphic_mod_test.go
index 0d4974e5c..14af1d0d0 100644
--- a/ckks/advanced/homomorphic_mod_test.go
+++ b/ckks/advanced/homomorphic_mod_test.go
@@ -5,10 +5,10 @@ import (
"runtime"
"testing"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
"github.com/stretchr/testify/assert"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
func TestHomomorphicMod(t *testing.T) {
diff --git a/ckks/bootstrapping/bootstrap.go b/ckks/bootstrapping/bootstrap.go
index 354b68a18..761cc16b6 100644
--- a/ckks/bootstrapping/bootstrap.go
+++ b/ckks/bootstrapping/bootstrap.go
@@ -3,8 +3,8 @@ package bootstrapping
import (
"math"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/ring"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/ring"
)
// Bootstrapp re-encrypt a ciphertext at lvl Q0 to a ciphertext at MaxLevel-k where k is the depth of the bootstrapping circuit.
diff --git a/ckks/bootstrapping/bootstrap_bench_test.go b/ckks/bootstrapping/bootstrap_bench_test.go
index 4f5dd3b28..b8322db5d 100644
--- a/ckks/bootstrapping/bootstrap_bench_test.go
+++ b/ckks/bootstrapping/bootstrap_bench_test.go
@@ -5,8 +5,8 @@ import (
"testing"
"time"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
func BenchmarkBootstrapp(b *testing.B) {
diff --git a/ckks/bootstrapping/bootstrap_params.go b/ckks/bootstrapping/bootstrap_params.go
index 6f34a7d42..616243734 100644
--- a/ckks/bootstrapping/bootstrap_params.go
+++ b/ckks/bootstrapping/bootstrap_params.go
@@ -1,10 +1,10 @@
package bootstrapping
import (
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/ckks/advanced"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/ckks/advanced"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Parameters is a struct for the default bootstrapping parameters
diff --git a/ckks/bootstrapping/bootstrap_test.go b/ckks/bootstrapping/bootstrap_test.go
index 6f9da0091..25f7a7654 100644
--- a/ckks/bootstrapping/bootstrap_test.go
+++ b/ckks/bootstrapping/bootstrap_test.go
@@ -7,10 +7,10 @@ import (
"sync"
"testing"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
"github.com/stretchr/testify/assert"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
var flagLongTest = flag.Bool("long", false, "run the long test suite (all parameters + secure bootstrapping). Overrides -short and requires -timeout=0.")
diff --git a/ckks/bootstrapping/bootstrapper.go b/ckks/bootstrapping/bootstrapper.go
index db32ab72f..d26752064 100644
--- a/ckks/bootstrapping/bootstrapper.go
+++ b/ckks/bootstrapping/bootstrapper.go
@@ -4,9 +4,9 @@ import (
"fmt"
"math"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/ckks/advanced"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/ckks/advanced"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
// Bootstrapper is a struct to stores a memory pool the plaintext matrices
diff --git a/ckks/bridge.go b/ckks/bridge.go
index 0597cec9e..d71877852 100644
--- a/ckks/bridge.go
+++ b/ckks/bridge.go
@@ -3,9 +3,9 @@ package ckks
import (
"fmt"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// DomainSwitcher is a type for switching between the standard CKKS domain (which encrypts vectors of complex numbers)
diff --git a/ckks/ciphertext.go b/ckks/ciphertext.go
index eccad35f0..1ed6c08a5 100644
--- a/ckks/ciphertext.go
+++ b/ckks/ciphertext.go
@@ -5,9 +5,9 @@ import (
"errors"
"math"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Ciphertext is *ring.Poly array representing a polynomial of degree > 0 with coefficients in R_Q.
diff --git a/ckks/ckks_benchmarks_test.go b/ckks/ckks_benchmarks_test.go
index 00552f13b..7575d7230 100644
--- a/ckks/ckks_benchmarks_test.go
+++ b/ckks/ckks_benchmarks_test.go
@@ -4,8 +4,8 @@ import (
"encoding/json"
"testing"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
func BenchmarkCKKSScheme(b *testing.B) {
diff --git a/ckks/ckks_test.go b/ckks/ckks_test.go
index 03b481771..62bd9a4eb 100644
--- a/ckks/ckks_test.go
+++ b/ckks/ckks_test.go
@@ -9,11 +9,11 @@ import (
"runtime"
"testing"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
"github.com/stretchr/testify/assert"
"github.com/stretchr/testify/require"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
var flagLongTest = flag.Bool("long", false, "run the long test suite (all parameters + secure bootstrapping). Overrides -short and requires -timeout=0.")
diff --git a/ckks/decryptor.go b/ckks/decryptor.go
index a6059240d..caf76a2ca 100644
--- a/ckks/decryptor.go
+++ b/ckks/decryptor.go
@@ -1,7 +1,7 @@
package ckks
import (
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
// Decryptor is an interface wrapping a rlwe.Decryptor.
diff --git a/ckks/encoder.go b/ckks/encoder.go
index 1885c012a..6da225192 100644
--- a/ckks/encoder.go
+++ b/ckks/encoder.go
@@ -7,9 +7,9 @@ import (
"math/big"
"math/bits"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// GaloisGen is an integer of order N/2 modulo M and that spans Z_M with the integer -1.
diff --git a/ckks/encryptor.go b/ckks/encryptor.go
index e22534e63..73216f8e2 100644
--- a/ckks/encryptor.go
+++ b/ckks/encryptor.go
@@ -1,8 +1,8 @@
package ckks
import (
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
// Encryptor an encryption interface for the CKKS scheme.
diff --git a/ckks/evaluator.go b/ckks/evaluator.go
index da93fc9a1..4981b7869 100644
--- a/ckks/evaluator.go
+++ b/ckks/evaluator.go
@@ -5,9 +5,9 @@ import (
"fmt"
"math"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Operand is a common interface for Ciphertext and Plaintext types.
diff --git a/ckks/keys.go b/ckks/keys.go
index 4907de648..bdb7c8841 100644
--- a/ckks/keys.go
+++ b/ckks/keys.go
@@ -1,6 +1,6 @@
package ckks
-import "github.com/ldsec/lattigo/v2/rlwe"
+import "github.com/tuneinsight/lattigo/v3/rlwe"
// KeyGenerator is an interface for the generation of CKKS keys.
type KeyGenerator interface {
diff --git a/ckks/linear_transform.go b/ckks/linear_transform.go
index b7bb8b60d..b21d2998d 100644
--- a/ckks/linear_transform.go
+++ b/ckks/linear_transform.go
@@ -3,9 +3,9 @@ package ckks
import (
"runtime"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Trace maps X -> sum((-1)^i * X^{i*n+1}) for 0 <= i < N
diff --git a/ckks/params.go b/ckks/params.go
index 1a5352f5e..1cfc8b936 100644
--- a/ckks/params.go
+++ b/ckks/params.go
@@ -7,9 +7,9 @@ import (
"math"
"math/big"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Name of the different default parameter sets
diff --git a/ckks/plaintext.go b/ckks/plaintext.go
index 4c8cf58b9..45e0bb818 100644
--- a/ckks/plaintext.go
+++ b/ckks/plaintext.go
@@ -1,8 +1,8 @@
package ckks
import (
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
// Plaintext is is a Element with only one Poly.
diff --git a/ckks/polynomial_evaluation.go b/ckks/polynomial_evaluation.go
index f3c5f2187..d23c7bb93 100644
--- a/ckks/polynomial_evaluation.go
+++ b/ckks/polynomial_evaluation.go
@@ -7,8 +7,8 @@ import (
"math/bits"
"runtime"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Polynomial is a struct storing the coefficients of a polynomial
diff --git a/ckks/utils.go b/ckks/utils.go
index 470e594c1..f4729638c 100644
--- a/ckks/utils.go
+++ b/ckks/utils.go
@@ -4,7 +4,7 @@ import (
"math"
"math/big"
- "github.com/ldsec/lattigo/v2/ring"
+ "github.com/tuneinsight/lattigo/v3/ring"
)
// StandardDeviation computes the scaled standard deviation of the input vector.
diff --git a/dbfv/dbfv_benchmark_test.go b/dbfv/dbfv_benchmark_test.go
index aefeade3f..030690f2c 100644
--- a/dbfv/dbfv_benchmark_test.go
+++ b/dbfv/dbfv_benchmark_test.go
@@ -4,9 +4,9 @@ import (
"encoding/json"
"testing"
- "github.com/ldsec/lattigo/v2/bfv"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/bfv"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
func Benchmark_DBFV(b *testing.B) {
diff --git a/dbfv/dbfv_test.go b/dbfv/dbfv_test.go
index 89fc7bf30..4c585b843 100644
--- a/dbfv/dbfv_test.go
+++ b/dbfv/dbfv_test.go
@@ -8,13 +8,13 @@ import (
"runtime"
"testing"
- "github.com/ldsec/lattigo/v2/bfv"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
"github.com/stretchr/testify/assert"
"github.com/stretchr/testify/require"
+ "github.com/tuneinsight/lattigo/v3/bfv"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
var flagLongTest = flag.Bool("long", false, "run the long test suite (all parameters). Overrides -short and requires -timeout=0.")
diff --git a/dbfv/keygen.go b/dbfv/keygen.go
index fc11bdd7c..024145bfa 100644
--- a/dbfv/keygen.go
+++ b/dbfv/keygen.go
@@ -2,8 +2,8 @@
package dbfv
import (
- "github.com/ldsec/lattigo/v2/bfv"
- "github.com/ldsec/lattigo/v2/drlwe"
+ "github.com/tuneinsight/lattigo/v3/bfv"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
)
// CKGProtocol is the structure storing the parameters and state for a party in the collective key generation protocol.
diff --git a/dbfv/keyswitch.go b/dbfv/keyswitch.go
index 682f77090..696c79758 100644
--- a/dbfv/keyswitch.go
+++ b/dbfv/keyswitch.go
@@ -1,8 +1,8 @@
package dbfv
import (
- "github.com/ldsec/lattigo/v2/bfv"
- "github.com/ldsec/lattigo/v2/drlwe"
+ "github.com/tuneinsight/lattigo/v3/bfv"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
)
// CKSProtocol is a structure storing the parameters for the collective key-switching protocol.
diff --git a/dbfv/refresh.go b/dbfv/refresh.go
index 91b10251f..266249c80 100644
--- a/dbfv/refresh.go
+++ b/dbfv/refresh.go
@@ -1,10 +1,10 @@
package dbfv
import (
- "github.com/ldsec/lattigo/v2/bfv"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/bfv"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
// RefreshProtocol is a struct storing the relevant parameters for the Refresh protocol.
diff --git a/dbfv/sharing.go b/dbfv/sharing.go
index 248821d13..4ae8d7782 100644
--- a/dbfv/sharing.go
+++ b/dbfv/sharing.go
@@ -1,11 +1,11 @@
package dbfv
import (
- "github.com/ldsec/lattigo/v2/bfv"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/bfv"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// E2SProtocol is the structure storing the parameters and temporary buffers
diff --git a/dbfv/transform.go b/dbfv/transform.go
index 95ee7db56..25b121a19 100644
--- a/dbfv/transform.go
+++ b/dbfv/transform.go
@@ -1,11 +1,11 @@
package dbfv
import (
- "github.com/ldsec/lattigo/v2/bfv"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/bfv"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// MaskedTransformProtocol is a struct storing the parameters for the MaskedTransformProtocol protocol.
diff --git a/dckks/dckks_benchmark_test.go b/dckks/dckks_benchmark_test.go
index b42a8e039..475c5f330 100644
--- a/dckks/dckks_benchmark_test.go
+++ b/dckks/dckks_benchmark_test.go
@@ -4,10 +4,10 @@ import (
"encoding/json"
"testing"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
func BenchmarkDCKKS(b *testing.B) {
diff --git a/dckks/dckks_test.go b/dckks/dckks_test.go
index c8c06838d..14f047757 100644
--- a/dckks/dckks_test.go
+++ b/dckks/dckks_test.go
@@ -9,11 +9,11 @@ import (
"github.com/stretchr/testify/require"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
var flagLongTest = flag.Bool("long", false, "run the long test suite (all parameters + secure bootstrapping). Overrides -short and requires -timeout=0.")
diff --git a/dckks/keygen.go b/dckks/keygen.go
index 588897fcd..66edf3cc5 100644
--- a/dckks/keygen.go
+++ b/dckks/keygen.go
@@ -2,8 +2,8 @@
package dckks
import (
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
)
// CKGProtocol is the structure storing the parameters and state for a party in the collective key generation protocol.
diff --git a/dckks/keyswitch.go b/dckks/keyswitch.go
index 8cfd40380..ef49056b7 100644
--- a/dckks/keyswitch.go
+++ b/dckks/keyswitch.go
@@ -1,8 +1,8 @@
package dckks
import (
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
)
// CKSProtocol is a structure storing the parameters for the collective key-switching protocol.
diff --git a/dckks/refresh.go b/dckks/refresh.go
index 02fae260e..75391d55a 100644
--- a/dckks/refresh.go
+++ b/dckks/refresh.go
@@ -1,10 +1,10 @@
package dckks
import (
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
// RefreshProtocol is a struct storing the relevant parameters for the Refresh protocol.
diff --git a/dckks/sharing.go b/dckks/sharing.go
index 92203a58c..8ef542cf1 100644
--- a/dckks/sharing.go
+++ b/dckks/sharing.go
@@ -3,11 +3,11 @@ package dckks
import (
"math/big"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// E2SProtocol is the structure storing the parameters and temporary buffers
diff --git a/dckks/transform.go b/dckks/transform.go
index 99d5539df..9f69f1280 100644
--- a/dckks/transform.go
+++ b/dckks/transform.go
@@ -5,11 +5,11 @@ import (
"encoding/binary"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// MaskedTransformProtocol is a struct storing the parameters for the MaskedTransformProtocol protocol.
diff --git a/dckks/utils.go b/dckks/utils.go
index ae1757f80..629b5be69 100644
--- a/dckks/utils.go
+++ b/dckks/utils.go
@@ -4,9 +4,9 @@ import (
"math"
"math/bits"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
// GetMinimumLevelForBootstrapping takes the security parameter lambda, the ciphertext scale, the number of parties and the moduli chain
diff --git a/drlwe/crs.go b/drlwe/crs.go
index c3e800802..acbc58fc4 100644
--- a/drlwe/crs.go
+++ b/drlwe/crs.go
@@ -1,7 +1,7 @@
package drlwe
import (
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// CRS is an interface for Common Reference Strings.
diff --git a/drlwe/drlwe_test.go b/drlwe/drlwe_test.go
index 049ae4fcc..7be32dff2 100644
--- a/drlwe/drlwe_test.go
+++ b/drlwe/drlwe_test.go
@@ -10,10 +10,10 @@ import (
"runtime"
"testing"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
"github.com/stretchr/testify/require"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
var nbParties = int(3)
diff --git a/drlwe/keygen_cpk.go b/drlwe/keygen_cpk.go
index 98ac47541..54e423d7d 100644
--- a/drlwe/keygen_cpk.go
+++ b/drlwe/keygen_cpk.go
@@ -2,9 +2,9 @@
package drlwe
import (
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// CollectivePublicKeyGenerator is an interface describing the local steps of a generic RLWE CKG protocol.
diff --git a/drlwe/keygen_relin.go b/drlwe/keygen_relin.go
index 4ea1e3e04..f655ef426 100644
--- a/drlwe/keygen_relin.go
+++ b/drlwe/keygen_relin.go
@@ -4,9 +4,9 @@ import (
"errors"
"math/big"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// RelinearizationKeyGenerator is an interface describing the local steps of a generic RLWE RKG protocol.
diff --git a/drlwe/keygen_rot.go b/drlwe/keygen_rot.go
index f6e329790..730179990 100644
--- a/drlwe/keygen_rot.go
+++ b/drlwe/keygen_rot.go
@@ -3,9 +3,9 @@ package drlwe
import (
"errors"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// RotationKeyGenerator is an interface for the local operation in the generation of rotation keys.
diff --git a/drlwe/keyswitch_pk.go b/drlwe/keyswitch_pk.go
index aafa20096..884ef4098 100644
--- a/drlwe/keyswitch_pk.go
+++ b/drlwe/keyswitch_pk.go
@@ -1,9 +1,9 @@
package drlwe
import (
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// PublicKeySwitchingProtocol is an interface describing the local steps of a generic RLWE PCKS protocol.
diff --git a/drlwe/keyswitch_sk.go b/drlwe/keyswitch_sk.go
index c61ba3b02..ec3923672 100644
--- a/drlwe/keyswitch_sk.go
+++ b/drlwe/keyswitch_sk.go
@@ -1,9 +1,9 @@
package drlwe
import (
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// KeySwitchingProtocol is an interface describing the local steps of a generic RLWE CKS protocol
diff --git a/examples/bfv/main.go b/examples/bfv/main.go
index 0a3803f95..9dd7a821f 100644
--- a/examples/bfv/main.go
+++ b/examples/bfv/main.go
@@ -5,11 +5,11 @@ import (
"math"
"math/bits"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
- "github.com/ldsec/lattigo/v2/bfv"
- "github.com/ldsec/lattigo/v2/ring"
+ "github.com/tuneinsight/lattigo/v3/bfv"
+ "github.com/tuneinsight/lattigo/v3/ring"
)
func obliviousRiding() {
diff --git a/examples/ckks/advanced/rlwe_lwe_bridge_LHHMQ20/main.go b/examples/ckks/advanced/rlwe_lwe_bridge_LHHMQ20/main.go
index 530de6538..2a02b97b6 100644
--- a/examples/ckks/advanced/rlwe_lwe_bridge_LHHMQ20/main.go
+++ b/examples/ckks/advanced/rlwe_lwe_bridge_LHHMQ20/main.go
@@ -5,11 +5,11 @@ import (
"math"
"time"
- "github.com/ldsec/lattigo/v2/ckks"
- ckksAdvanced "github.com/ldsec/lattigo/v2/ckks/advanced"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ ckksAdvanced "github.com/tuneinsight/lattigo/v3/ckks/advanced"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// This example is an implementation of the RLWE -> LWE extraction followed by an LWE -> RLWE repacking
diff --git a/examples/ckks/bootstrapping/main.go b/examples/ckks/bootstrapping/main.go
index fcff0709e..33fd2f25a 100644
--- a/examples/ckks/bootstrapping/main.go
+++ b/examples/ckks/bootstrapping/main.go
@@ -4,10 +4,10 @@ import (
"fmt"
"math"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/ckks/bootstrapping"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/ckks/bootstrapping"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
func main() {
@@ -25,7 +25,7 @@ func main() {
// Bootstrapping parameters
// Four sets of parameters (index 0 to 3) ensuring 128 bit of security
- // are available in github.com/ldsec/lattigo/v2/ckks/bootstrap_params
+ // are available in github.com/tuneinsight/lattigo/v3/ckks/bootstrap_params
// LogSlots is hardcoded to 15 in the parameters, but can be changed from 1 to 15.
// When changing logSlots make sure that the number of levels allocated to CtS and StC is
// smaller or equal to logSlots.
diff --git a/examples/ckks/euler/main.go b/examples/ckks/euler/main.go
index 2f84d8f13..c700cac59 100644
--- a/examples/ckks/euler/main.go
+++ b/examples/ckks/euler/main.go
@@ -6,8 +6,8 @@ import (
"math/cmplx"
"time"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/rlwe"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
)
func example() {
diff --git a/examples/ckks/polyeval/main.go b/examples/ckks/polyeval/main.go
index 7a2f66d83..ff5f29459 100644
--- a/examples/ckks/polyeval/main.go
+++ b/examples/ckks/polyeval/main.go
@@ -4,9 +4,9 @@ import (
"fmt"
"math"
- "github.com/ldsec/lattigo/v2/ckks"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ckks"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
func chebyshevinterpolation() {
diff --git a/examples/dbfv/pir/main.go b/examples/dbfv/pir/main.go
index d62425570..44bc6388f 100644
--- a/examples/dbfv/pir/main.go
+++ b/examples/dbfv/pir/main.go
@@ -7,11 +7,11 @@ import (
"sync"
"time"
- "github.com/ldsec/lattigo/v2/bfv"
- "github.com/ldsec/lattigo/v2/dbfv"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/bfv"
+ "github.com/tuneinsight/lattigo/v3/dbfv"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
func check(err error) {
diff --git a/examples/dbfv/psi/main.go b/examples/dbfv/psi/main.go
index 3aa154830..fa9726360 100644
--- a/examples/dbfv/psi/main.go
+++ b/examples/dbfv/psi/main.go
@@ -7,11 +7,11 @@ import (
"sync"
"time"
- "github.com/ldsec/lattigo/v2/bfv"
- "github.com/ldsec/lattigo/v2/dbfv"
- "github.com/ldsec/lattigo/v2/drlwe"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/bfv"
+ "github.com/tuneinsight/lattigo/v3/dbfv"
+ "github.com/tuneinsight/lattigo/v3/drlwe"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
func check(err error) {
diff --git a/examples/ring/vOLE/main.go b/examples/ring/vOLE/main.go
index cc365a872..d1298893c 100644
--- a/examples/ring/vOLE/main.go
+++ b/examples/ring/vOLE/main.go
@@ -6,8 +6,8 @@ import (
"math/big"
"time"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Vectorized oblivious evaluation is a two-party protocol for the function f(x) = ax + b where a sender
diff --git a/examples/rlwe/lwe_bridge/main.go b/examples/rlwe/lwe_bridge/main.go
index 51a143f99..5799d4fb5 100644
--- a/examples/rlwe/lwe_bridge/main.go
+++ b/examples/rlwe/lwe_bridge/main.go
@@ -7,9 +7,9 @@ import (
"math/rand"
"time"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/rlwe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/rlwe"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// This example implements an oblivious shuffling of the plaintext slots of an RLWE encryption.
diff --git a/go.mod b/go.mod
index ebb18656b..9df79f545 100644
--- a/go.mod
+++ b/go.mod
@@ -1,4 +1,4 @@
-module github.com/ldsec/lattigo/v2
+module github.com/tuneinsight/lattigo/v3
go 1.13
diff --git a/ring/conjugate_invariant.go b/ring/conjugate_invariant.go
index c60e8eb5f..7fc9a60f3 100644
--- a/ring/conjugate_invariant.go
+++ b/ring/conjugate_invariant.go
@@ -1,7 +1,7 @@
package ring
import (
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// UnfoldConjugateInvariantToStandard maps the compressed representation (N/2 coefficients)
diff --git a/ring/ring.go b/ring/ring.go
index 83cdc9cbf..53a3cae54 100644
--- a/ring/ring.go
+++ b/ring/ring.go
@@ -11,7 +11,7 @@ import (
"math/big"
"math/bits"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Type is the type of ring used by the cryptographic scheme
diff --git a/ring/ring_automorphism.go b/ring/ring_automorphism.go
index 6da70f2e4..56f730238 100644
--- a/ring/ring_automorphism.go
+++ b/ring/ring_automorphism.go
@@ -4,7 +4,7 @@ import (
"math/bits"
"unsafe"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// GenGaloisParams generates the generators for the Galois endomorphisms.
diff --git a/ring/ring_operations.go b/ring/ring_operations.go
index 984328117..9d249d60f 100644
--- a/ring/ring_operations.go
+++ b/ring/ring_operations.go
@@ -4,7 +4,7 @@ import (
"math/big"
"math/bits"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
func (r *Ring) minLevelTernary(p1, p2, p3 *Poly) int {
diff --git a/ring/ring_poly.go b/ring/ring_poly.go
index 3c0f3644d..2605acc1c 100644
--- a/ring/ring_poly.go
+++ b/ring/ring_poly.go
@@ -3,8 +3,9 @@ package ring
import (
"encoding/binary"
"errors"
- "github.com/ldsec/lattigo/v2/utils"
"math/bits"
+
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Poly is the structure that contains the coefficients of a polynomial.
diff --git a/ring/ring_sampler.go b/ring/ring_sampler.go
index 391a8f796..df7040dd0 100644
--- a/ring/ring_sampler.go
+++ b/ring/ring_sampler.go
@@ -1,7 +1,7 @@
package ring
import (
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
const precision = uint64(56)
diff --git a/ring/ring_sampler_gaussian.go b/ring/ring_sampler_gaussian.go
index 9e8a14224..9149d4d01 100644
--- a/ring/ring_sampler_gaussian.go
+++ b/ring/ring_sampler_gaussian.go
@@ -4,7 +4,7 @@ import (
"encoding/binary"
"math"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// GaussianSampler keeps the state of a truncated Gaussian polynomial sampler.
diff --git a/ring/ring_sampler_ternary.go b/ring/ring_sampler_ternary.go
index f7d3bec34..9583e50d2 100644
--- a/ring/ring_sampler_ternary.go
+++ b/ring/ring_sampler_ternary.go
@@ -4,7 +4,7 @@ import (
"math"
"math/bits"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// TernarySampler keeps the state of a polynomial sampler in the ternary distribution.
diff --git a/ring/ring_sampler_uniform.go b/ring/ring_sampler_uniform.go
index 4e33005a9..fc19f6cb6 100644
--- a/ring/ring_sampler_uniform.go
+++ b/ring/ring_sampler_uniform.go
@@ -3,7 +3,7 @@ package ring
import (
"encoding/binary"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// UniformSampler wraps a util.PRNG and represents the state of a sampler of uniform polynomials.
diff --git a/ring/ring_test.go b/ring/ring_test.go
index b04e57dd8..c1533f02d 100644
--- a/ring/ring_test.go
+++ b/ring/ring_test.go
@@ -6,7 +6,7 @@ import (
"math/big"
"testing"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/utils"
"github.com/stretchr/testify/require"
)
diff --git a/rlwe/decryptor.go b/rlwe/decryptor.go
index c017be2de..fded3a4b2 100644
--- a/rlwe/decryptor.go
+++ b/rlwe/decryptor.go
@@ -1,8 +1,8 @@
package rlwe
import (
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Decryptor is an interface generic RLWE encryption.
diff --git a/rlwe/elements.go b/rlwe/elements.go
index c3ba83109..a0702fd51 100644
--- a/rlwe/elements.go
+++ b/rlwe/elements.go
@@ -3,8 +3,8 @@ package rlwe
import (
"math/big"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Plaintext is a common base type for RLWE plaintexts.
diff --git a/rlwe/encryptor.go b/rlwe/encryptor.go
index bac8b9ab9..394cb6f97 100644
--- a/rlwe/encryptor.go
+++ b/rlwe/encryptor.go
@@ -1,8 +1,8 @@
package rlwe
import (
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// Encryptor a generic RLWE encryption interface.
diff --git a/rlwe/keygen.go b/rlwe/keygen.go
index f6a949269..b14b6cb44 100644
--- a/rlwe/keygen.go
+++ b/rlwe/keygen.go
@@ -4,8 +4,8 @@ import (
"math"
"math/big"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// KeyGenerator is an interface implementing the methods of the KeyGenerator.
diff --git a/rlwe/keyswitch.go b/rlwe/keyswitch.go
index 53e16bdb6..e226e22b1 100644
--- a/rlwe/keyswitch.go
+++ b/rlwe/keyswitch.go
@@ -3,7 +3,7 @@ package rlwe
import (
"math"
- "github.com/ldsec/lattigo/v2/ring"
+ "github.com/tuneinsight/lattigo/v3/ring"
)
// KeySwitcher is a struct for RLWE key-switching.
diff --git a/rlwe/marshaler.go b/rlwe/marshaler.go
index 526b0e2d0..8621d52a7 100644
--- a/rlwe/marshaler.go
+++ b/rlwe/marshaler.go
@@ -3,7 +3,8 @@ package rlwe
import (
"encoding/binary"
"errors"
- "github.com/ldsec/lattigo/v2/ring"
+
+ "github.com/tuneinsight/lattigo/v3/ring"
)
// GetDataLen returns the length in bytes of the target Ciphertext.
diff --git a/rlwe/params.go b/rlwe/params.go
index cd92300ea..90bb3dc0f 100644
--- a/rlwe/params.go
+++ b/rlwe/params.go
@@ -7,8 +7,8 @@ import (
"math/big"
"math/bits"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// MaxLogN is the log2 of the largest supported polynomial modulus degree.
diff --git a/rlwe/ring_qp.go b/rlwe/ring_qp.go
index ee0748bb2..2294f02b7 100644
--- a/rlwe/ring_qp.go
+++ b/rlwe/ring_qp.go
@@ -1,8 +1,8 @@
package rlwe
import (
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
// PolyQP represents a polynomial in the ring of polynomial modulo Q*P.
diff --git a/rlwe/rlwe_test.go b/rlwe/rlwe_test.go
index d0eef461c..fd22dbfc6 100644
--- a/rlwe/rlwe_test.go
+++ b/rlwe/rlwe_test.go
@@ -13,8 +13,8 @@ import (
"github.com/stretchr/testify/assert"
"github.com/stretchr/testify/require"
- "github.com/ldsec/lattigo/v2/ring"
- "github.com/ldsec/lattigo/v2/utils"
+ "github.com/tuneinsight/lattigo/v3/ring"
+ "github.com/tuneinsight/lattigo/v3/utils"
)
var flagParamString = flag.String("params", "", "specify the test cryptographic parameters as a JSON string. Overrides -short and -long.")
 -
+
-Lattigo is a Go module that implements Ring-Learning-With-Errors-based homomorphic-encryption primitives and Multiparty-Homomorphic-Encryption-based secure protocols.
-The library features:
+Lattigo is a Go module that implements Ring-Learning-With-Errors-based homomorphic-encryption
+primitives and Multiparty-Homomorphic-Encryption-based secure protocols. The library features:
- An implementation of the full-RNS BFV and CKKS schemes and their respective multiparty versions.
- Comparable performance to state-of-the-art C++ libraries.
- Dense-key and sparse-key efficient and high-precision bootstrapping procedures for full-RNS CKKS.
-- A pure Go implementation that enables cross-platform builds, including WASM compilation for browser clients.
+- A pure Go implementation that enables cross-platform builds, including WASM compilation for
+ browser clients.
-Lattigo is meant to support HE in distributed systems and microservices architectures, for which Go is a common choice thanks to its natural concurrency model and portability.
+Lattigo is meant to support HE in distributed systems and microservices architectures, for which Go
+is a common choice thanks to its natural concurrency model and portability.
## Library overview
The library exposes the following packages:
-- `lattigo/ring`: Modular arithmetic operations for polynomials in the RNS basis, including: RNS basis extension; RNS rescaling; number theoretic transform (NTT); uniform, Gaussian and ternary sampling.
+- `lattigo/ring`: Modular arithmetic operations for polynomials in the RNS basis, including: RNS
+ basis extension; RNS rescaling; number theoretic transform (NTT); uniform, Gaussian and ternary
+ sampling.
-- `lattigo/bfv`: The Full-RNS variant of the Brakerski-Fan-Vercauteren scale-invariant homomorphic encryption scheme. It provides modular arithmetic over the integers.
+- `lattigo/bfv`: The Full-RNS variant of the Brakerski-Fan-Vercauteren scale-invariant homomorphic
+ encryption scheme. It provides modular arithmetic over the integers.
-- `lattigo/ckks`: The Full-RNS Homomorphic Encryption for Arithmetic for Approximate Numbers (HEAAN, a.k.a. CKKS) scheme. It provides approximate arithmetic over the complex numbers (in its classic variant) and over the real numbers (in its conjugate-invariant variant).
+- `lattigo/ckks`: The Full-RNS Homomorphic Encryption for Arithmetic for Approximate Numbers (HEAAN,
+ a.k.a. CKKS) scheme. It provides approximate arithmetic over the complex numbers (in its classic
+ variant) and over the real numbers (in its conjugate-invariant variant).
-- `lattigo/dbfv` and `lattigo/dckks`: Multiparty (a.k.a. distributed or threshold) versions of the BFV and CKKS schemes that enable secure multiparty computation solutions with secret-shared secret keys.
+- `lattigo/dbfv` and `lattigo/dckks`: Multiparty (a.k.a. distributed or threshold) versions of the
+ BFV and CKKS schemes that enable secure multiparty computation solutions with secret-shared secret
+ keys.
-- `lattigo/rlwe` and `lattigo/drlwe`: common base for generic RLWE-based multiparty homomorphic encryption. It is imported by the `lattigo/bfv` and `lattigo/ckks` packages.
+- `lattigo/rlwe` and `lattigo/drlwe`: common base for generic RLWE-based multiparty homomorphic
+ encryption. It is imported by the `lattigo/bfv` and `lattigo/ckks` packages.
-- `lattigo/examples`: Executable Go programs that demonstrate the use of the Lattigo library.
- Each subpackage includes test files that further demonstrate the use of Lattigo primitives.
+- `lattigo/examples`: Executable Go programs that demonstrate the use of the Lattigo library. Each
+ subpackage includes test files that further demonstrate the use of Lattigo
+ primitives.
- `lattigo/utils`: Supporting structures and functions.
## Versions and Roadmap
-This version of Lattigo, (v2.x.x) is meant to be a working prototype.
-Hence, there will be backward-incompatible changes within this version.
+The Lattigo library was originally exclusively developed by the EPFL Laboratory for Data Security
+until its version 2.4.0.
-See CHANGELOG.md for the current and past versions.
+Starting with the release of version 3.0.0, Lattigo is maintained and supported by [Tune Insight
+SA](https://tuneinsight.com).
+
+Also starting with from version 3.0.0, the module name has changed to
+github.com/tuneinsight/lattigo/v3, and the official repository has been moved to
+https://github.com/tuneinsight/lattigo. This has the following implications for modules that depend
+on Lattigo:
+- Modules that require `github.com/ldsec/lattigo/v2` will still build correctly.
+- To upgrade to a version >= 3.0.0, depending modules must require `github.com/tuneinsight/lattigo/v3/`,
+ for example by changing the imports to `github.com/tuneinsight/lattigo/v3/[package]` and by
+ running `go mod tidy`.
-## Disclaimer
-This library is still at an experimental stage and should be used for research purposes only.
+The current version of Lattigo, (v3.x.x) is fast-evolving and in constant development. Consequently,
+there will still be backward-incompatible changes within this major version, in addition to many bug
+fixes and new features. Hence, we encourage all Lattigo users to update to the latest Lattigo
+version.
+
+
+See CHANGELOG.md for the current and past versions.
## License
@@ -51,35 +77,43 @@ Lattigo is licensed under the Apache 2.0 License. See LICENSE.
## Contact
-If you want to contribute to Lattigo or you have any suggestion, do not hesitate to contact us at [lattigo@listes.epfl.ch](mailto:lattigo@listes.epfl.ch).
+If you want to contribute to Lattigo or you have any suggestion, do not hesitate to contact us at
+[lattigo@tuneinsight.com](mailto:lattigo@tuneinsight.com).
## Citing
Please use the following BibTex entry for citing Lattigo:
@misc{lattigo,
- title = {Lattigo v2.4.0},
- howpublished = {Online: \url{https://github.com/ldsec/lattigo}},
- month = Jan,
+ title = {Lattigo v3.0.0},
+ howpublished = {Online: \url{https://github.com/tuneinsight/lattigo}},
+ month = Feb,
year = 2022,
- note = {EPFL-LDS}
+ note = {EPFL-LDS, Tune Insight SA}
}
## References
-1. Efficient Bootstrapping for ApproximateHomomorphic Encryption with Non-Sparse Keys (
-
+
-Lattigo is a Go module that implements Ring-Learning-With-Errors-based homomorphic-encryption primitives and Multiparty-Homomorphic-Encryption-based secure protocols.
-The library features:
+Lattigo is a Go module that implements Ring-Learning-With-Errors-based homomorphic-encryption
+primitives and Multiparty-Homomorphic-Encryption-based secure protocols. The library features:
- An implementation of the full-RNS BFV and CKKS schemes and their respective multiparty versions.
- Comparable performance to state-of-the-art C++ libraries.
- Dense-key and sparse-key efficient and high-precision bootstrapping procedures for full-RNS CKKS.
-- A pure Go implementation that enables cross-platform builds, including WASM compilation for browser clients.
+- A pure Go implementation that enables cross-platform builds, including WASM compilation for
+ browser clients.
-Lattigo is meant to support HE in distributed systems and microservices architectures, for which Go is a common choice thanks to its natural concurrency model and portability.
+Lattigo is meant to support HE in distributed systems and microservices architectures, for which Go
+is a common choice thanks to its natural concurrency model and portability.
## Library overview
The library exposes the following packages:
-- `lattigo/ring`: Modular arithmetic operations for polynomials in the RNS basis, including: RNS basis extension; RNS rescaling; number theoretic transform (NTT); uniform, Gaussian and ternary sampling.
+- `lattigo/ring`: Modular arithmetic operations for polynomials in the RNS basis, including: RNS
+ basis extension; RNS rescaling; number theoretic transform (NTT); uniform, Gaussian and ternary
+ sampling.
-- `lattigo/bfv`: The Full-RNS variant of the Brakerski-Fan-Vercauteren scale-invariant homomorphic encryption scheme. It provides modular arithmetic over the integers.
+- `lattigo/bfv`: The Full-RNS variant of the Brakerski-Fan-Vercauteren scale-invariant homomorphic
+ encryption scheme. It provides modular arithmetic over the integers.
-- `lattigo/ckks`: The Full-RNS Homomorphic Encryption for Arithmetic for Approximate Numbers (HEAAN, a.k.a. CKKS) scheme. It provides approximate arithmetic over the complex numbers (in its classic variant) and over the real numbers (in its conjugate-invariant variant).
+- `lattigo/ckks`: The Full-RNS Homomorphic Encryption for Arithmetic for Approximate Numbers (HEAAN,
+ a.k.a. CKKS) scheme. It provides approximate arithmetic over the complex numbers (in its classic
+ variant) and over the real numbers (in its conjugate-invariant variant).
-- `lattigo/dbfv` and `lattigo/dckks`: Multiparty (a.k.a. distributed or threshold) versions of the BFV and CKKS schemes that enable secure multiparty computation solutions with secret-shared secret keys.
+- `lattigo/dbfv` and `lattigo/dckks`: Multiparty (a.k.a. distributed or threshold) versions of the
+ BFV and CKKS schemes that enable secure multiparty computation solutions with secret-shared secret
+ keys.
-- `lattigo/rlwe` and `lattigo/drlwe`: common base for generic RLWE-based multiparty homomorphic encryption. It is imported by the `lattigo/bfv` and `lattigo/ckks` packages.
+- `lattigo/rlwe` and `lattigo/drlwe`: common base for generic RLWE-based multiparty homomorphic
+ encryption. It is imported by the `lattigo/bfv` and `lattigo/ckks` packages.
-- `lattigo/examples`: Executable Go programs that demonstrate the use of the Lattigo library.
- Each subpackage includes test files that further demonstrate the use of Lattigo primitives.
+- `lattigo/examples`: Executable Go programs that demonstrate the use of the Lattigo library. Each
+ subpackage includes test files that further demonstrate the use of Lattigo
+ primitives.
- `lattigo/utils`: Supporting structures and functions.
## Versions and Roadmap
-This version of Lattigo, (v2.x.x) is meant to be a working prototype.
-Hence, there will be backward-incompatible changes within this version.
+The Lattigo library was originally exclusively developed by the EPFL Laboratory for Data Security
+until its version 2.4.0.
-See CHANGELOG.md for the current and past versions.
+Starting with the release of version 3.0.0, Lattigo is maintained and supported by [Tune Insight
+SA](https://tuneinsight.com).
+
+Also starting with from version 3.0.0, the module name has changed to
+github.com/tuneinsight/lattigo/v3, and the official repository has been moved to
+https://github.com/tuneinsight/lattigo. This has the following implications for modules that depend
+on Lattigo:
+- Modules that require `github.com/ldsec/lattigo/v2` will still build correctly.
+- To upgrade to a version >= 3.0.0, depending modules must require `github.com/tuneinsight/lattigo/v3/`,
+ for example by changing the imports to `github.com/tuneinsight/lattigo/v3/[package]` and by
+ running `go mod tidy`.
-## Disclaimer
-This library is still at an experimental stage and should be used for research purposes only.
+The current version of Lattigo, (v3.x.x) is fast-evolving and in constant development. Consequently,
+there will still be backward-incompatible changes within this major version, in addition to many bug
+fixes and new features. Hence, we encourage all Lattigo users to update to the latest Lattigo
+version.
+
+
+See CHANGELOG.md for the current and past versions.
## License
@@ -51,35 +77,43 @@ Lattigo is licensed under the Apache 2.0 License. See LICENSE.
## Contact
-If you want to contribute to Lattigo or you have any suggestion, do not hesitate to contact us at [lattigo@listes.epfl.ch](mailto:lattigo@listes.epfl.ch).
+If you want to contribute to Lattigo or you have any suggestion, do not hesitate to contact us at
+[lattigo@tuneinsight.com](mailto:lattigo@tuneinsight.com).
## Citing
Please use the following BibTex entry for citing Lattigo:
@misc{lattigo,
- title = {Lattigo v2.4.0},
- howpublished = {Online: \url{https://github.com/ldsec/lattigo}},
- month = Jan,
+ title = {Lattigo v3.0.0},
+ howpublished = {Online: \url{https://github.com/tuneinsight/lattigo}},
+ month = Feb,
year = 2022,
- note = {EPFL-LDS}
+ note = {EPFL-LDS, Tune Insight SA}
}
## References
-1. Efficient Bootstrapping for ApproximateHomomorphic Encryption with Non-Sparse Keys (