-
-
Notifications
You must be signed in to change notification settings - Fork 1.5k
Closed
Labels
security issue 🔑Issue concerns Boostnote's security. Usually high priority.Issue concerns Boostnote's security. Usually high priority.
Description
Current behavior
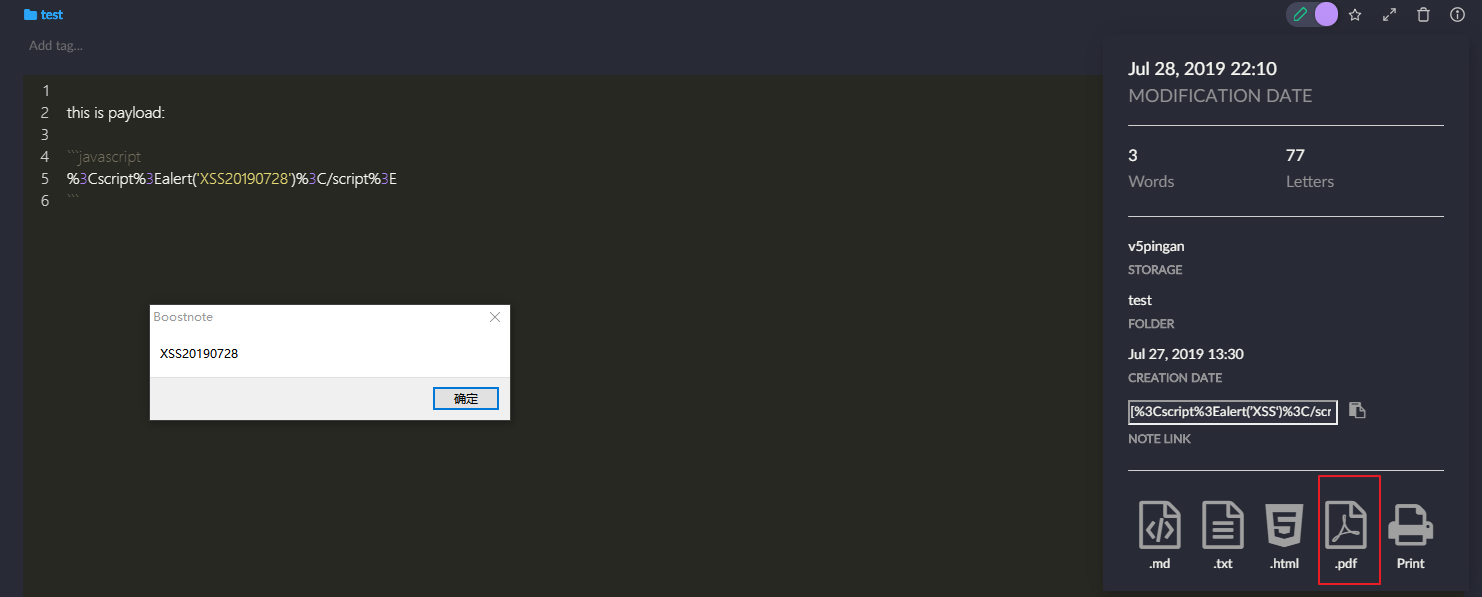
Notes Exported to PDF Format Is Existing XSS Attacks.
Expected behavior
Notes Exported to PDF Format Is Existing XSS Attacks.
When there is a code in the note:
``` JavaScript
% 3Cscript%3Ealert('XSS')%3C/script%3E
```
XSS attacks are triggered when the export PDF function is reused.
Steps to reproduce
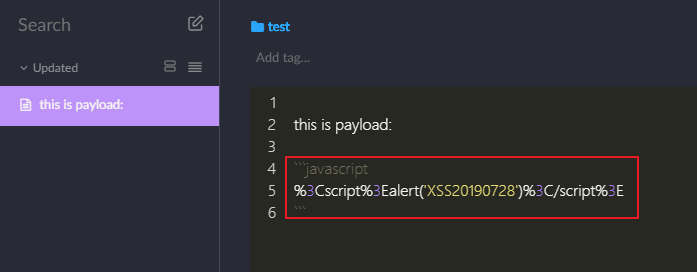
1. Put the payload below into your notes.
- Payload:
``` JavaScript
% 3Cscript%3Ealert('XSS')%3C/script%3E
```
2. Click on the "Info" button in the upper right corner of the note to export the file in PDF format. This will trigger payload to generate a bullet window, that is, there is an XSS attack.
Environment
- Version : 0.12.1
- OS Version and name : Microsoft Windows 10 Home Chinese Version
Metadata
Metadata
Assignees
Labels
security issue 🔑Issue concerns Boostnote's security. Usually high priority.Issue concerns Boostnote's security. Usually high priority.