-
-
Notifications
You must be signed in to change notification settings - Fork 1.1k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
the trait bound *const str: diesel::deserialize::FromSql<diesel::sql_types::Timestamp, diesel::pg::Pg> is not satisfied
#2011
Comments
|
The field order of your The following definition of #[derive(Eq, PartialEq, Debug, Serialize, Deserialize, Queryable)]
pub struct AccessToken {
pub id: String,
pub client_id: String,
pub grant_type: String,
pub issued_at: NaiveDateTime,
pub scope: String,
pub expires_at: NaiveDateTime,
pub user_id: String,
}Note that this behaviour is explicitly documented for our (Closed because that's nothing that is actionable by the diesel core team) |
|
@weiznich Thank you so much for saving my day! Sorry for my mistake, I didn't notice that. |
|
Apparent the fields order are the same, but still has this error. |
|
@videni Our issue tracker is the wrong place to ask for support. It's for tracking bugs and coordinating work between contributors. Please use the forum or the gitter channel to ask this kind of questions. You also may want to include more context, because otherwise it's not possible to give you an helpful answer. |
|
@weiznich ok, thanks |
|
the problem is with the order. table! { |
Setup
Versions
Feature Flags
Problem Description
This error message shows when compile.
What is the expected output?
No error output
What is the actual output?
Error message
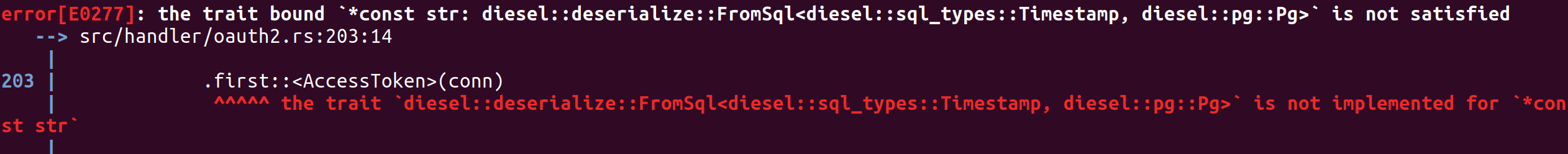
Are you seeing any additional errors?
##Other useful code
src/schema.rssrc/models/oauth2.rssrc/handler/oauth2.rsChecklist
closed if this is not the case)
The text was updated successfully, but these errors were encountered: