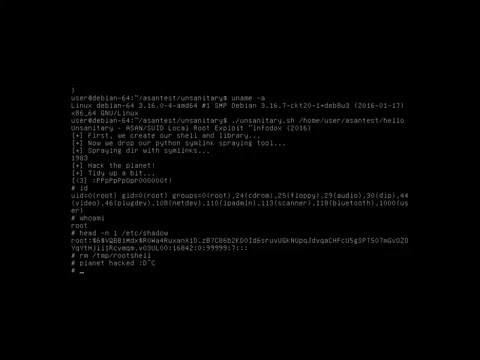
Exploits unsanitized env var passing in ASAN which leads to file clobbering as root when executing setuid root binaries compiled with ASAN.
Uses an overwrite of /etc/ld.so.preload to get root on a vulnerable system. Supply your own target binary to use for exploitation.
Implements the bug found here: http://seclists.org/oss-sec/2016/q1/363