-
Notifications
You must be signed in to change notification settings - Fork 10.3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Support access logging with Common Log Format/Extended Log Format #5894
Comments
|
From @Tratcher on February 3, 2017 18:13 Would this be better as middleware? Is there any information middleware wouldn't have access to? |
|
From @CesarBS on February 3, 2017 18:14 With Kestrel at least, middleware wouldn't log bad requests rejected before the app runs. |
|
@shirhatti @DamianEdwards thoughts? |
|
From @DamianEdwards on February 3, 2017 21:16 This is interesting. I wasn't aware the log file format was a standard. Do we think we'd just do this internally in Kestrel or would we try to use |
|
@DamianEdwards Yeah, this is a simple format and there are a bunch of analysis tools since forever that can parse this format and provide information. We discussed different options for implementing this (just doing it internally and writing a file, providing a stream that user can do whatever they want with, using the existing logging abstractions) -- each has pros and cons. |
|
From @DamianEdwards on February 3, 2017 21:31 Would be good to capture the different approaches and their pros and cons. |
|
From @CesarBS on February 3, 2017 21:35 @DamianEdwards The advantage of using existing log infrastructure is the flexibility and if people use Serilog they get log file rotation and such. The downside is that setting it up is more involved than just offering an option in |
|
From @DamianEdwards on February 3, 2017 21:50 How would it work using |
|
From @CesarBS on February 17, 2017 0:10 Yeah, Kestrel would have to do the formatting. If a logger were to intercept the messages and decorate it in any way, that would make the message useless since it couldn't be parsed by tools that look into these logs. |
|
From @halter73 on February 17, 2017 0:31 Decorated messages wouldn't exactly be useless, but they wouldn't fit the common log format. Presumably if you're using a logger that decorates messages, you aren't to interested in the common log format to begin with. There's also nothing stopping developers from configuring multiple logger providers: one that decorates and another that doesn't for common logs. I think that common logs should have a unique source so providers can be configured to filter out everything else. Being able to use existing providers to get features like rolling log files, logging to some other persistence layer, etc. certainly would be nice. |
|
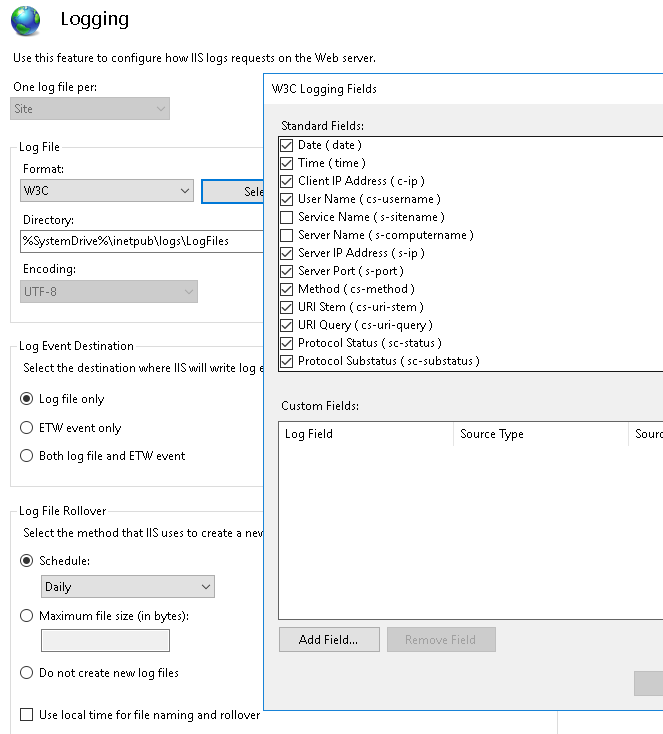
From @benaadams on February 17, 2017 0:42 Is it an external component though? The while the layout is standard the output is configurable For example IIS's options for W3C logging The fields would have to be identifiable so they can be switched on and off |
|
From @CesarBS on February 17, 2017 1:16 @benaadams Yeah, that's the extended format. The first W3C log format had fixed fields, but modern servers also support Extended Log Format which allows you to specify which fields you want logged per access. We'd have to add a |
|
@shirhatti Needs design (though lower pri for 2.0.0) |
|
How about doing this with a DiagnosticListener and one of the existing DiagnosticSource events ( |
|
@cwe1ss That's the idea. The one thing we need to figure out is rejected requests that don't make it into hosting. |
|
@muratg at this point I assume this isn't happening for 2.0? |
|
@glennc Could you please add this as a feature to track with the 2.1.0 project so that it gets prioritized with the rest of the features. |
|
This is a very basic feature that should have been in alpha. I understand that originally Kestrel was supposed to run behind proxy but now that it is supported as a standalone. This is especially important for us since we need to run on Service Fabric when no IIS is allowed near it. |
|
@glennc this needs design. |
|
Should this be mentioned in the 2.2 Roadmap? I don't see a mention of it in Announcements. |
|
It's not in scope for 2.2 |
|
Thanks, @DamianEdwards. When can we expect it? |
|
Sorry, we have no details on that right now. It hasn't made it's way high enough on the priority list yet. |
|
Okay. It is a high priority for us. I would venture to say a minimal implementation (i.e. common log format without extended logging) would be a great step forward. |
|
As a workaround, I use NLog.config to filter 'Microsoft.AspNetCore.Hosting.Internal.WebHost' related entries: Sample output: |
|
Hi @DamianEdwards, You wrote Kestrel (post/request) logging is not high on the priority list for ASP.net Core team. Let me try to convince you otherwise. a) For some time now you can use Kestrel as a 'stand alone' web server, without the need of a proxy server. It's fast and light weight. That's my setup and I'm loving it. b) Post and Request logging (according to industry standards) is utterly important nowadays. You really need to have some easy way to check your log to see what's happening with your web server. Check IP addresses and check abuse. I'm not talking about debugging, you have a couple of other solutions for what already, I'm talking about the safety and performance of my server. Could you and your team please consider moving this issue higher up your priority list? Many thanks for all of your hard work, your live videos etc. ASP.NET Core is what I've waited for all of my life. Since 1987 FidoNet :) |
|
@JeepNL extremely baffles me why they just don't get it. |
I stared your GitHub repo, it's good. |
|
If you use Serilog, then you can try this Middleware: |
|
Any new developments on this? Kestrel support for W3C extended log format out of the box? For .NET 5 maybe? See also Microsoft Docs: W3C Logging |
|
Thanks for contacting us. |
|
This should be implemented in Kestrel directly as a structured log in a specific category. |
|
@davidfowl Yes, please :) (Just FYI): I've mentioned the log analyzer AWStats already in this thread, GoAccess is another fast and light weight log analyzer which is used by many NGINX/Apache systems. I think this (generating W3C logfiles) is an important feature which Kestrel, like any other stand alone production webserver, should support. |
|
We removed nginx in front of our system recently and expose Kestrel directly, but didn't except something standard as access logs to be missing. Looking forward to seeing this added too |
|
FYI @CumpsD The ASP.NET team started with this in ASP.NET Core 6 Preview 4
And about W3C logging, Justin Kotalik tweeted they're working on that for ASP.NET Core 6 Preview 5, see: #31843 |
|
See #33251 |
|
Thanks! |
|
This is done as of #33251, will be included as part of dotnet 6.0-preview7 |

From @CesarBS on February 3, 2017 18:6
Every web server does this:
http://httpd.apache.org/docs/current/logs.html#accesslog
http://redmine.lighttpd.net/projects/1/wiki/Docs_ModAccessLog
http://nginx.org/en/docs/http/ngx_http_log_module.html#access_log
https://www.iis.net/configreference/system.applicationhost/log/centralw3clogfile
There are tools that analyze logs using those formats.
For reference:
https://en.wikipedia.org/wiki/Common_Log_Format
https://www.w3.org/TR/WD-logfile.html
Copied from original issue: aspnet/KestrelHttpServer#1339
The text was updated successfully, but these errors were encountered: