You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
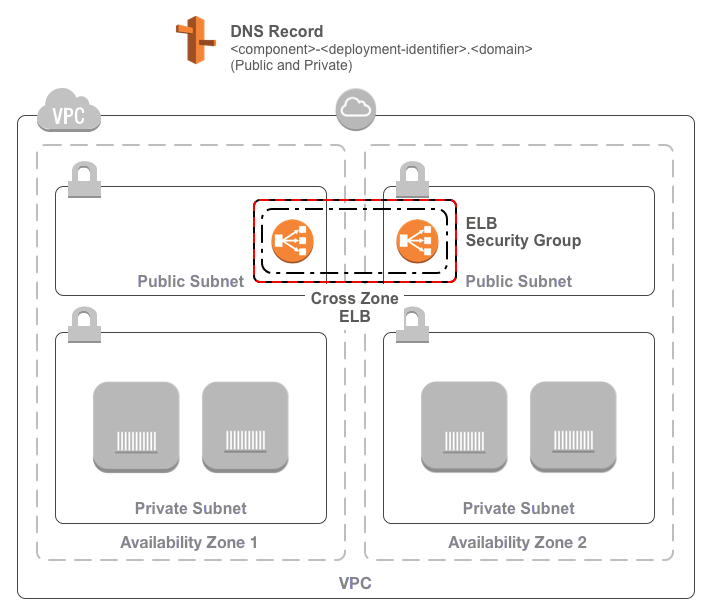
A Terraform module for building a network load balancer in AWS.
7
7
8
8
The load balancer requires:
9
+
9
10
* An existing VPC
10
11
* Some existing subnets
11
12
* A domain name and public and private hosted zones
12
-
13
+
13
14
The ECS load balancer consists of:
15
+
14
16
* An NLB
15
-
* Deployed across the provided subnet IDs
16
-
* Either internal or internet-facing as specified
17
-
* With a health check using the specified target
18
-
* With connection draining as specified
19
-
* A security group allowing access to/from the load balancer according to the
17
+
* Deployed across the provided subnet IDs
18
+
* Either internal or internet-facing as specified
19
+
* With a health check using the specified target
20
+
* With connection draining as specified
21
+
* A security group allowing access to/from the load balancer according to the
20
22
specified access control and egress CIDRs configuration
21
23
* A security group for use by instances allowing access from the load balancer
22
24
according to the specified access control configuration
23
25
* A DNS entry
24
-
* In the public hosted zone if specified
25
-
* In the private hosted zone if specified
26
+
* In the public hosted zone if specified
27
+
* In the private hosted zone if specified
26
28
27
29
| region | The region into which to deploy the load balancer | - | yes |
120
+
| vpc_id | The ID of the VPC into which to deploy the load balancer | - | yes |
121
+
| subnet_ids | The IDs of the subnets for the NLB | - | yes |
122
+
| component | The component for which the load balancer is being created | - | yes |
123
+
| deployment_identifier | An identifier for this instantiation | - | yes |
124
+
| domain_name | The domain name of the supplied Route 53 zones | - | yes |
125
+
| public_zone_id | The ID of the public Route 53 zone | - | yes |
126
+
| private_zone_id | The ID of the private Route 53 zone | - | yes |
127
+
| enable_cross_zone_load_balancing | Whether or not to enable cross zone load balancing (\"yes\" or \"no\"). | no | no |
128
+
| enable_deletion_protection | Whether or not to enable deletion protection for the load balancer. | false | no |
129
+
| enable_access_logs | Whether or not to enable access logs on the load balancer. | false | no |
130
+
| access_logs_bucket_name | The name of the S3 bucket in which to store access logs when `enable_access_logs` is `true`. | false | no |
131
+
| access_logs_bucket_prefix | The prefix to use for objects in the access logs S3 bucket when `enable_access_logs` is `true`. Logs are stored in the root if `null`. | false | no |
132
+
| idle_timeout | The time after which idle connections are closed. | 60 | no |
133
+
| include_public_dns_record | Whether or not to create a public DNS entry (\"yes\" or \"no\"). | no | no |
134
+
| include_private_dns_record | Whether or not to create a private DNS entry (\"yes\" or \"no\"). | yes | no |
135
+
| expose_to_public_internet | Whether or not to the NLB should be internet facing (\"yes\" or \"no\"). | no | no |
136
+
| use_https | whether or not to use HTTPS | no | no |
137
+
| target_group_port | The port that the application is listening on | - | yes |
138
+
| target_group_type | The type of target that you must specify when registering targets with this target group. | instance | no |
139
+
| target_group_protocol | The protocol to use for routing traffic to the targets. Should be either TCP or TLS | TCP | no |
140
+
| health_check_port | The port to use to connect with the target. Either ports 1-65536, or traffic-port | traffic-port | no |
141
+
| health_check_protocol | The protocol to use for health checks | TLS | no |
142
+
| health_check_interval | The time between health check attempts in seconds | 30 | no |
143
+
| health_check_unhealthy_threshold | The number of failed health checks before an instance is taken out of service | 2 | no |
144
+
| health_check_healthy_threshold | The number of successful health checks before an instance is put into service | 10 | no |
145
+
| listener_port | Port that NLB listens on | 443 | no |
146
+
| listener_protocol | Protocol that the NLB listens on | TLS | no |
147
+
| listener_certificate_arn | certificate ARN to be used by the certificate | - | yes |
0 commit comments