You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Hi!
I am a 360 security guard staff member. We found multiple vulnerabilities in Opengrok in our open source code detection project. The details are as follows:
1.XML deserialization vulnerability
The set method in ConfigurationController.java receives the request body in the put request
Finally, the parameter is passed to the decodeObject method and xml is deserialized.
But the attacker will execute the command when passing the following request body.
The same problem still exists at line 230 of FileHistoryCache.java
2.Reflective xss
Received two parameters r1 and r2 in the request at line 233 of PageConfig.java.
Finally, after a series of patchwork (but no filtering), output in diff.jsp
E.g:
3.zip_slip
Decompress the zip file in the extractArchive method of FileUtilities.java
Since the zip entry name is not verified, when the zip file maliciously constructed by the attacker is decompressed (the entry name has "../" for path backtracking), the file can be decompressed to any directory, or even overwritten. System Files
The text was updated successfully, but these errors were encountered:
Ideally, this should have been entered as 3 separate issues, we might deal with them as such.
In general, it would be beneficial to have a discussion on what attack vectors are important to us. For example, the XML decoding problem can only happen when it is possible to submit new configuration (this is normally constrained to localhost thanks to LocalhostFilter) which would be a problem on its own so the problem described is not really serious. That said, it pokes another hole in our serialization scheme.
vladak
changed the title
Opengrok Vulnerability
multiple vulnerabilities in input data handling
Apr 12, 2019
Uh oh!
There was an error while loading. Please reload this page.
Hi!


I am a 360 security guard staff member. We found multiple vulnerabilities in Opengrok in our open source code detection project. The details are as follows:
1.XML deserialization vulnerability
The set method in ConfigurationController.java receives the request body in the put request
Finally, the parameter is passed to the decodeObject method and xml is deserialized.
But the attacker will execute the command when passing the following request body.
The same problem still exists at line 230 of FileHistoryCache.java
2.Reflective xss
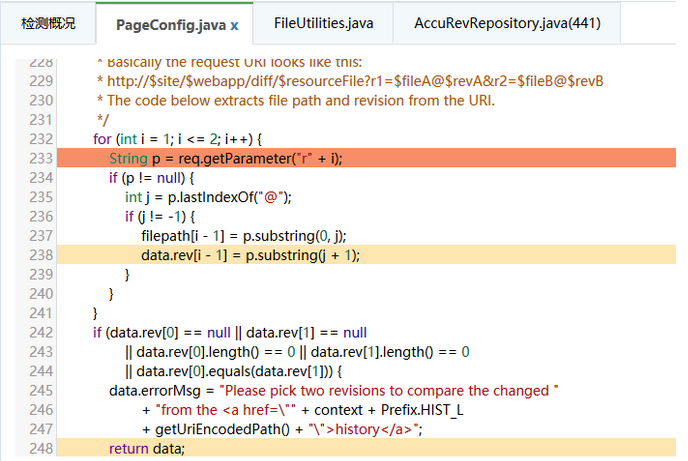

Received two parameters r1 and r2 in the request at line 233 of PageConfig.java.
Finally, after a series of patchwork (but no filtering), output in diff.jsp
E.g:
3.zip_slip

Decompress the zip file in the extractArchive method of FileUtilities.java
Since the zip entry name is not verified, when the zip file maliciously constructed by the attacker is decompressed (the entry name has "../" for path backtracking), the file can be decompressed to any directory, or even overwritten. System Files
The text was updated successfully, but these errors were encountered: