Minimal login scenario with Keycloak (OIDC Provider) and Python (Flask).
- Check REPORT.md for more details.
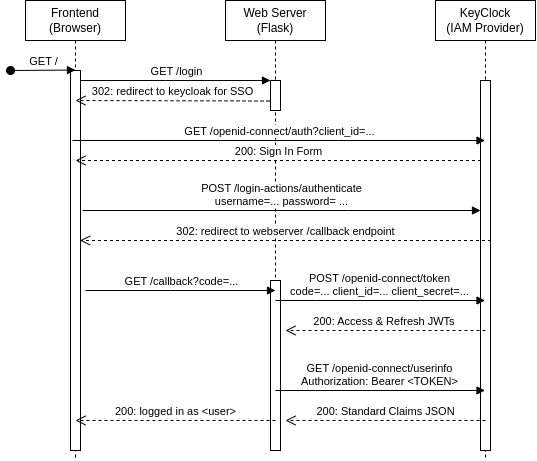
The sequence diagram illustrates the typical interactions between system components to implement a simple login scenario.
-
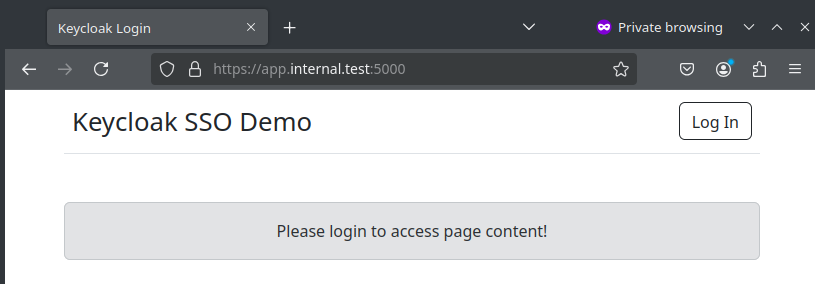
Application webpage before logging in. Configured locally with self-signed certs for HTTPS.
-
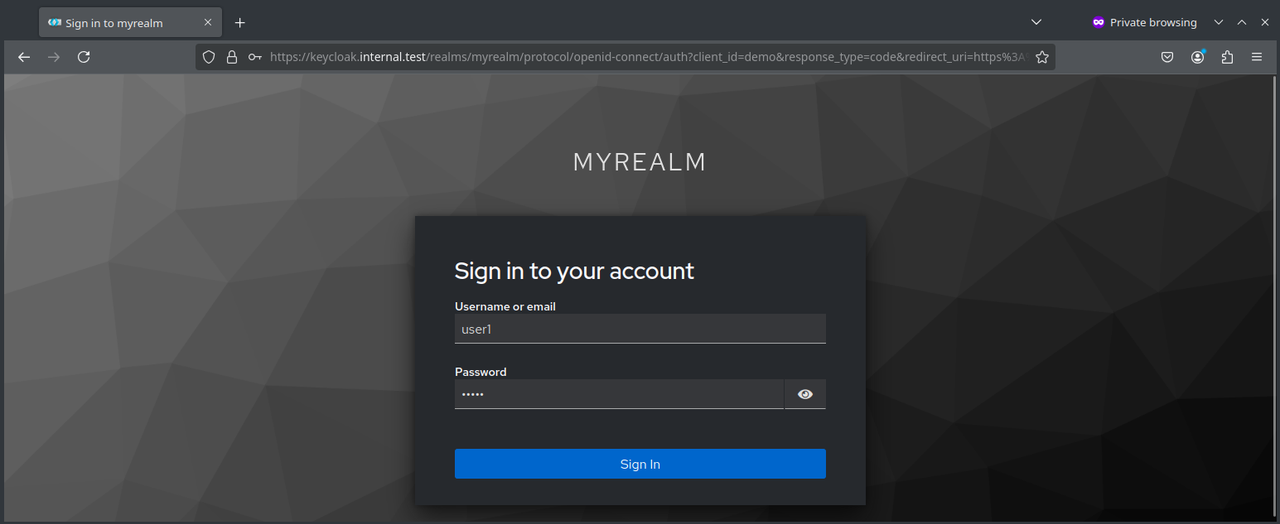
Clicking "Log In" redirects to Keyclock login form.
- Need to pre-configure connection to the client and sample users/roles in "myrealm".
-
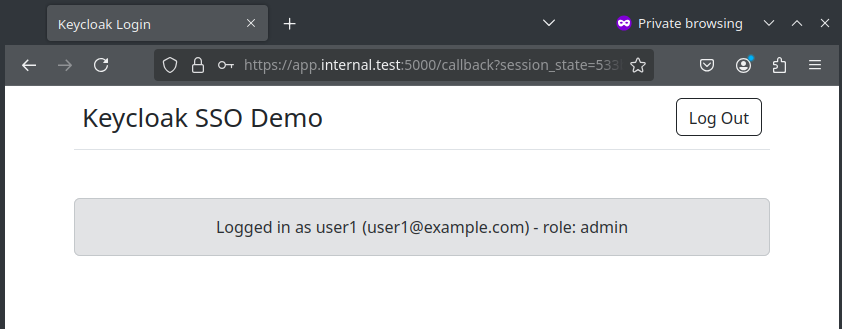
Successful login and redirection.
-
The client session can be inspected at the server
-
Clone repository
git clone https://github.com/sh3b0/keycloak-sso cd keycloak-sso -
Configure certificates in
certsdirectory. Refer to REPORT.md for more details- Expected content:
tls.crt,tls.key, andca.crt(issuer CA).
- Expected content:
-
Create
.envwith environment variables. Sample config:CA_PATH=/app/certs/ca.crt KEYCLOAK_SERVER_URL=https://keycloak.internal.test KEYCLOAK_REALM=myrealm KEYCLOAK_CLIENT_ID=demo KEYCLOAK_CLIENT_SECRET=<KEYCLOAK_CLIENT_SECRET> KEYCLOAK_REDIRECT_URI=https://app.internal.test:5000/callback
-
Configure domain names for
appandkeycloakaccordingly. -
Run
keycloakandappcontainers in the same network.docker compose up -d
-
Login to Keycloak UI with
admin:admin, then change credentials. -
Create a realm, a client, and sample users for testing.
-
Access the test client at port 5000.