-
Notifications
You must be signed in to change notification settings - Fork 254
Mango
When starting mango you have the option to start a new session or continue an existing one. A session is nothing more than a SQLite db file which is used by Mango to save a batch of parsed APKs. Imagine for example that you are working on a malware family or a vulnerability pattern, then you can import APKs in to a db (we will see how) and perform useful queries among the analysed entries. That being said when you run mango, you have one of the following options:

If you already have been working on a session you can resume it by giving it as an argument to the mango script:

Mango will present you the already analysed APKs and ask you to choose one:
Enter the index of application to load:
Doing so, mango will present the following screen:

After this, mango will prompt you to connect to an existing mobile device in order to continue your session.
There are two ways to import an APK in to the Mango's database. This is either by typing:
mango> import /full/path/to/foo.apk
Or you can pull one from the connected device and then import it:
mango> pull package_name
mango> import base.apk
After doing so, mango will parse the APK and add db entries for its activities, services, receivers, providers, deeplinks, intent filters, permissions and resource strings. Out of mango, you can open the session file using a SQLite editor:
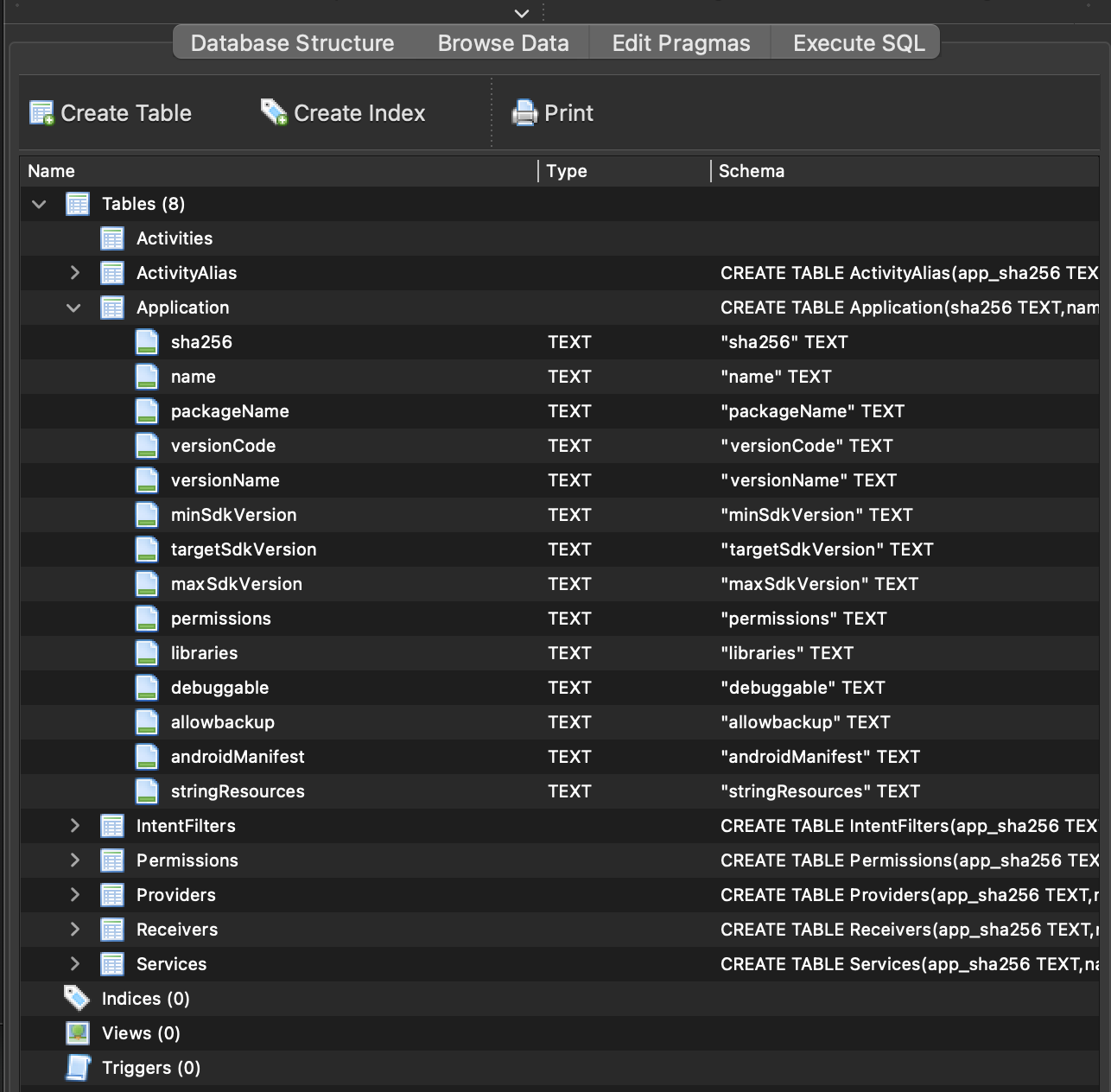
Finally, you can load an APK which has already been analysed using the load command followed by the package name:
mango> load package_name
Important: you can always use the tab key after typing a command to see the available options
After loading an application mango will parse the AndroidManifest and create entries in your session db for the application's components. You can start exploring these components using the show command followed by one of the following options:
- activities, e.g.
mango> show activities
Prints the application's activities in the following form:
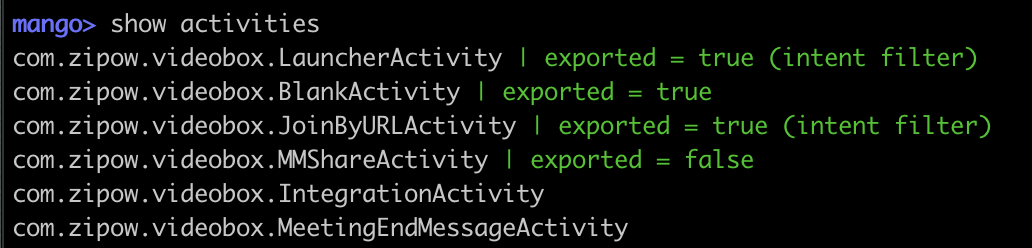
You can filter for exported only activities by using the -e additional option. The activityAlias, services, receivers, providers, permissions, deeplinks and intentFilters work in exactly similar way.
- exposure, e.g.
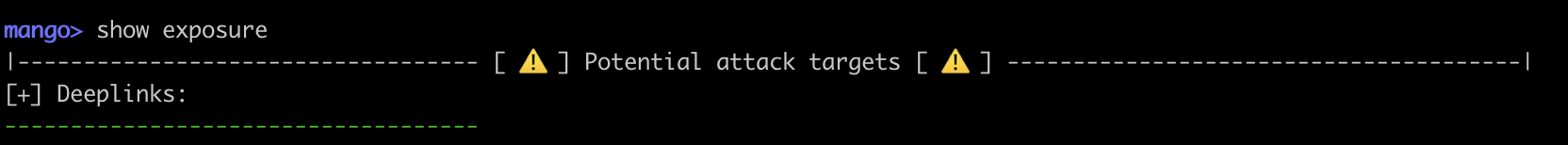
mango> show exposure
Prints the application's "attack surface", including deeplinks, exported activities, activity aliases, services, receivers and providers:
- info, e.g.
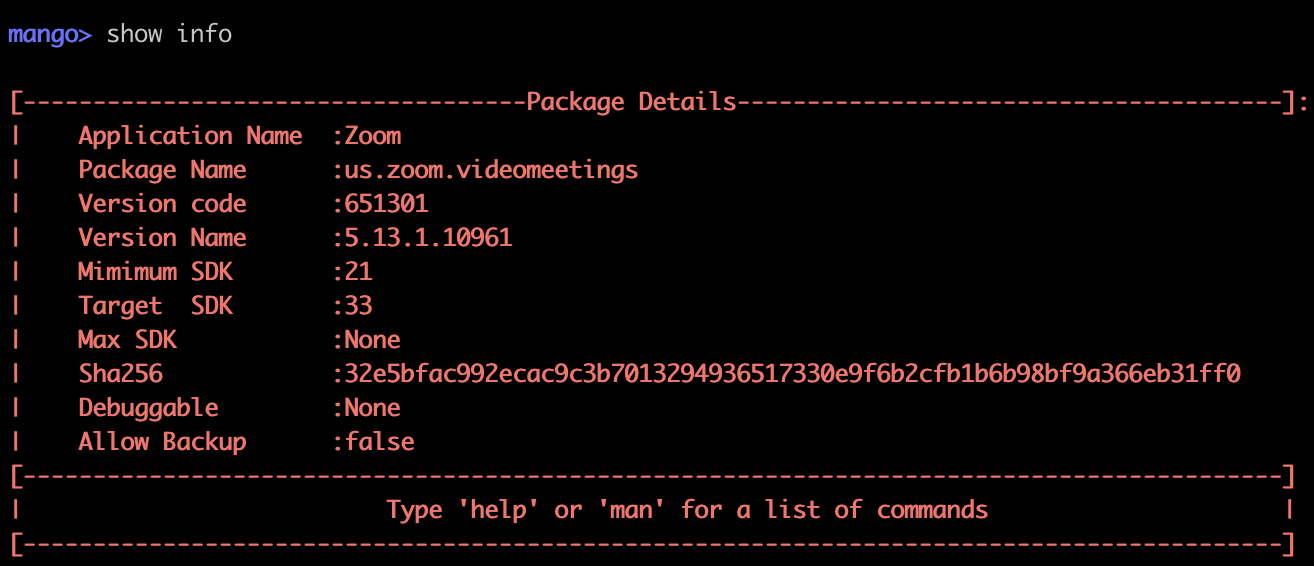
mango> show info
Prints handy information about the loaded application:
- manifest, e.g.
mango> show info
Prints the application's manifest
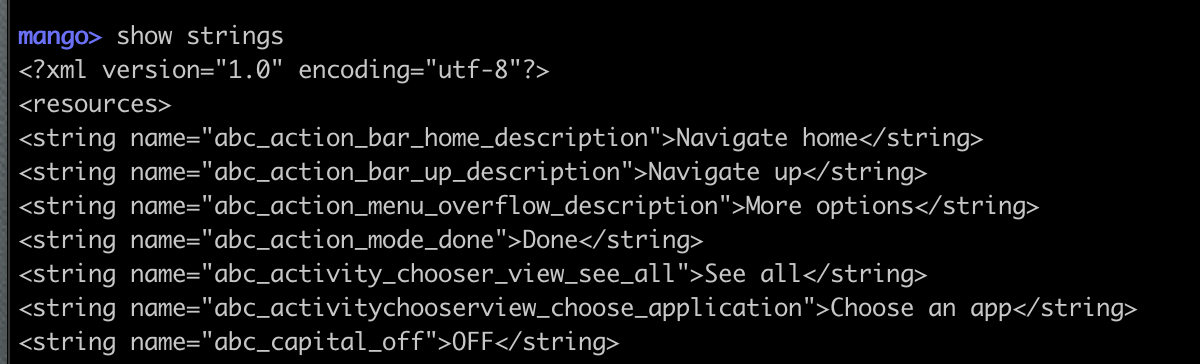
- strings, e.g.
mango> show strings
Prints the application's string resources
- database, e.g.
mango> show database
Prints the structure of the database file. The output can be used to construct raw sql queries (see query command).
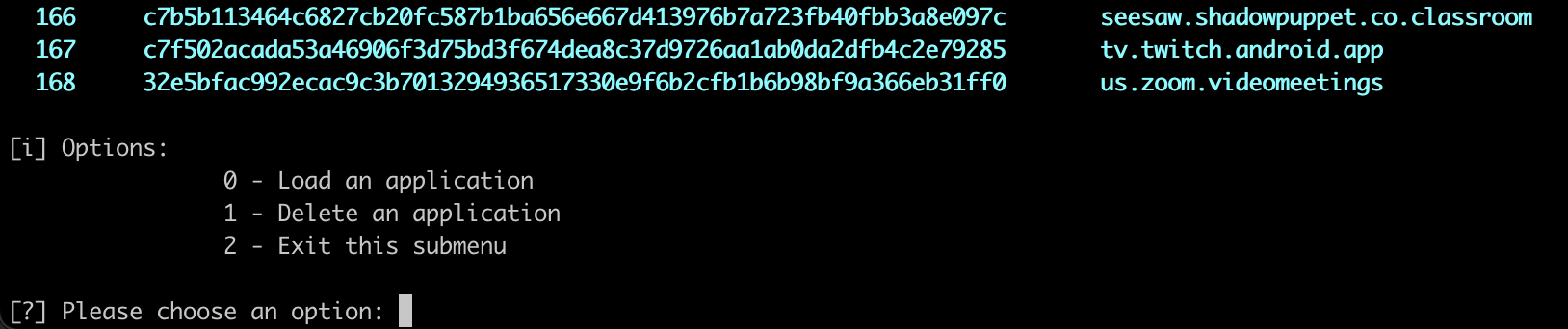
- applications, e.g.
mango> show applications
This option can be used to load a different application or manage the existing applications:
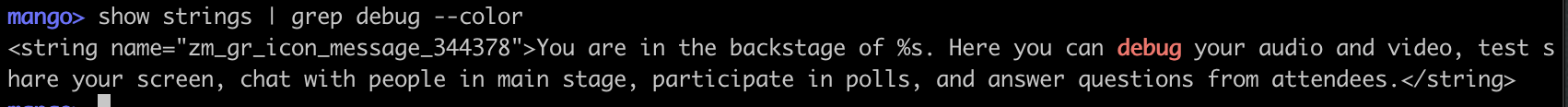
You can issue "raw" SQL queries to the db of your current session by typing query followed by the query body:

Important: mango as well as medusa supports the redirection of the output to another command using common pipes.
Example:
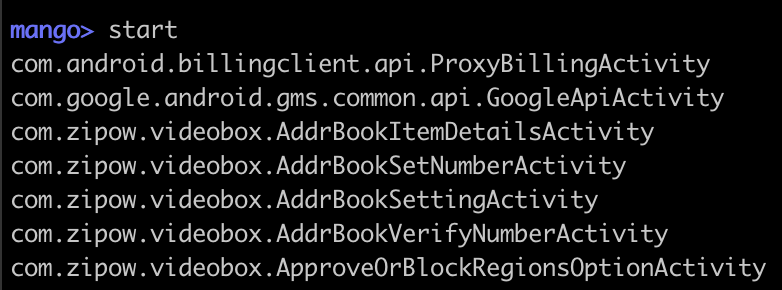
- You can force the currently loaded application to start an activity by typing
startfollowed by tab or the full name of an activity:
- Similarly you can force the application to start a service by typing
startsrvfollowed by tab or the full name of a service:
- To stop a service, type:
stopsrvfollowed by tab or the full name of the service.
Note: The components don't have to be exported
- To trigger a deeplink, type
deeplinkfollowed by tab or the full uri of the deeplink:
- Additionally, you can kill or start an application by typing
killorspawnrespectively followed by the application's name:
mango> kill com.example.package
Mango provides multiple commands that can help you to interact with a mobile device or emulator in multiple ways. What follows is a full list of the relative commands and their usage:
- You can install an application by using the
mango> install /full/path/to/foo.akor uninstall one by typingmango> uninstall [package name] - To install a burp certificate, type
installBurpCertand follow the steps indicated by mango - To modify the device's proxy settings, type
proxyfollowed by one of the following options:-
getto print the current proxy configuration -
set ip:portto set a proxy configuration. Adding -t (e.g.mango> proxy set -t 192.168.1.2:8080will set a transparent proxy -
resetwill clear the device's proxy
-
Examples:


- To start an interactive adb session, type
adb - To start an interactive shell with busybox support type
boxand follow the given instructions:

- To get a package specific logcat, type
logcat [package name]. You can also get the device's native logs by usingnlogor the Java crash logs by usingjlog:


-
To get a screenshot, type
screencap -o [filename.png] -
To run a shell command to the connected device, type:
cc [command]:

- You can send a notification to the device by typing
notify notification_title notification_body. The command requires the installation of the medusa agent which can be done by using theìnstallagentcommand.
-
You can set the debuggable flag to
trueof a given APK by typingpatch /full/path/to/foo.apk. This option requires the apksigner and zipalign to be installed in the device. If they aren't mango will download them locally and use them. -
Setting the debuggable flag can give you (among others) the option to dynamically debug an APK. You can do that by using the
jdwp [package name]command or (out of mango) you can use Android studio or the latest jadx version. -
Finally, you can use the
tracefollowed by one of the options below to start a frida-trace session: -
-jto trace all the functions of a java class. Example:trace -j com.myapp.name* // Trace all the functions of the com.myapp.name* class -
-nto trace a native function. Example:trace -n name* -
-ato trace the all the functions of a native library. Exampletrace -a libfoo.so
Medusa Wiki
Medusa Wiki
-
- Searching for the right module
- Getting info about a module
- Stashing / un-stashing
- Compiling
- Starting a session
- Hooking beyond the modules
- Importing Frida scripts
- Working with native libraries
- Working with the application's memory
- Getting Class and Object snapshots
- Useful utilities
- Saving a session (recipe)