-
Notifications
You must be signed in to change notification settings - Fork 254
Medusa
When running medusa, the first step is to select the device that you are going to use during your review. For this reason, medusa will display the currently detected devices and prompt you to choose one by entering the corresponding index number:

After this, medusa will display various info, regarding the device but also the currently active modules:

Make sure that a frida server is running on this device and you are good to go !
IMPORTANT: Medusa has an autocomplete functionality in order to indicate the available options. Simply said, you can always press the tab button to see your available options. For example, pressing the tab after the 'show' command, it yields

meaning that, after show you can either type: all, categories, mods or snippets
Medusa counts more than 90 modules, which are inactive until you add them to the stashed ones (we will see how). To navigate between these modules and find the right ones to stash, you can you the following commands:
The 'search' command can be used to search for the module that fit your needs based on a given keyword. For example, to search for HTTP communications related hooks, you can simply type:

The 'show' command, combined with an options can be used for the following tasks:
- Show all available modules:
show all
Modules are grouped according to their functionality, to see the available groups type:
- Display the available module categories:
show categories - Display the available modules for the selected category
show mods [category] - To list your stashed modules, type:
show mods
Let's say you found a super useful frida script and you want to save it, so you can use it later. You can add it under the /medusa/snippets directory and later import it using the import command:

While using medusa, to list those scripts, simply type: show snippets
Use the info [module-name] command to get details about a hook and its functionality:

To use the modules you first have to stash them, meaning that first you have to add them in a list of modules which later are going to be unified to a single script and run under a frida session.
To stash a module simply type: use followed by the module name. Here are some tips regarding this command:
- Pressing tab after the
usecommand will list all the available modules - Typing the initial letters of a module followed by a tab after the
usecommand will list all the modules starting with those letters:

- Typing
usefollowed by the initial letters of a module category will add all the modules of this category:

To un-stash a module, simply type rem followed by the module name. Furthermore, the same options with the use can be used (tab, initial letters etc.)
You can empty the stashed modules by typing reset. Keep in mind that this will also reset the unified script !
Some modules have to be stashed before others. For example the SSL unpinning modules have to be stashed always firsts. For this reason you can use swap to change the order of your stashed modules:

Finally, you can stash modules which have not been loaded from the standard modules directory using the following command:
add [full-path-to-module]
After stashing your modules, the next step is to compile them to a single script. This script is called agent.js and you can find it under the medusa/ directory, although most of the times you won't have to deal with it. That being said, in order to compile your script, simply type compile.
Sometimes you might need to add delay on loading your script (e.g. it may take time for libraries to be loaded so Frida won't be able to find them). To do so you can type: compile -t X where X is the delay time in milliseconds.
After you have selected, stashed and compiled your modules in to a unified script, the next step is to run the application. There are two main ways of doing that:
- Start or restart the app and attach to it, with:
run -f [package - name]orrun -n [package - number] - Attach to the application while it is running, with
run [package-name]
Regarding the first, you can simply type run -f followed by a tab, to get the installed packages. Alternatively, to start a session using a package number, type list and get the index number that corresponds to the app that you want to run from the output:



Regarding the second option, you can use the run followed by a tab in order to get the available packages and attach to the one you are interested about.
When a session starts Medusa prints various info regarding the Frida server (that runs in the device) and the running application:

While in session, you have the following set of commands available:

As it is depicted above, the in-session commands are pretty much self-explanatory. Regarding the (t)race and (r)e(s)et, they can be used to modify the scratchpad script on the fly (refer to the scratchpad section to get info about this module).
Each module intercepts a subset of Android APIs related to a specific functionality. For example the webviews/hook_webviews intercepts calls related to the Webview class, the intents/* to Intent and so on. To cover the gap of intercepting methods that belong to the app itself, Medusa provides a special module which is called scratchpad. That being said, it is possible to intercept Java or Native calls with a single command by using the hook command and its options.
The scratchpad can be stashed/un-stashed similarly to any module using the use scratchpad and rem scratchpad respectively. It is also added by default in case you issue a hook or pad command. The available options regarding this module are the following:
-
hook -a [class_name]Example:hook -a com.dropbox.android.activity.d. This option will add "hooks" to all the methods of the com.dropbox.android.activity.d and when a method will be invoked Medusa will log (if possible) its arguments and the value that it returns:
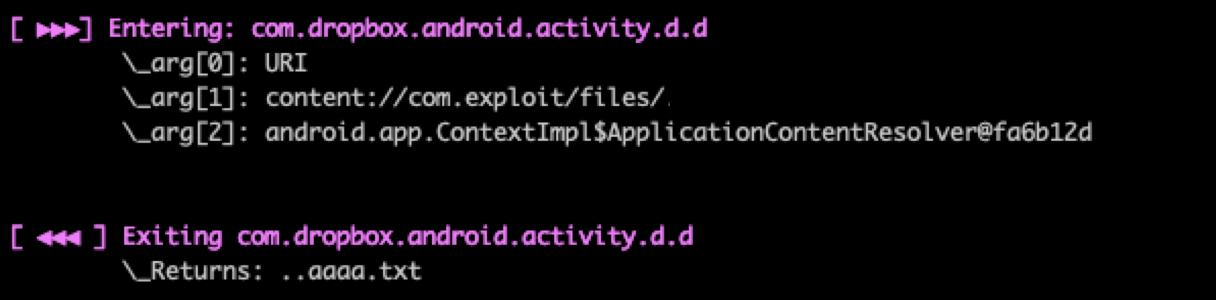
-
hook -fThis option can be used to intercept a single class method (including the constructor) and log its arguments, the returned value but also a stack trace of the methods that lead to this call. You can hook as many methods as you wish by entering a submenu and providing the requested information:

When one of the hooked methods gets called the output will be as follows:

You can also use the jtrace full_path_to_method to achieve the same result. Example: jtrace com.dropbox.android.activity.d.d
-
hook -nThis option can be used to intercept a single native method by giving its name or offset:

While most of the options are self-explanatory, the backtrace will print the call stack to the intercepted method, the 'memory read' will try to dump the method's arguments and returned values using a buffer size which is given in the subsequent input.
-
hook -rResets the current hooks and clears the scratchpad.
To further edit the scratchpad you can use the pad command which will open for edit it using vim:

The scratchpad can also be modified during a session, using the in-session menu's (t)race and (r)e(s)et options:


You can save your favourite Frida scripts under the medusa/snippets directory and import them to the scratchpad using the import command. For example, assuming that you want to import the example.js script, then:
- Remove the
Java.perform(function() { }keeping only the part highlighted below:
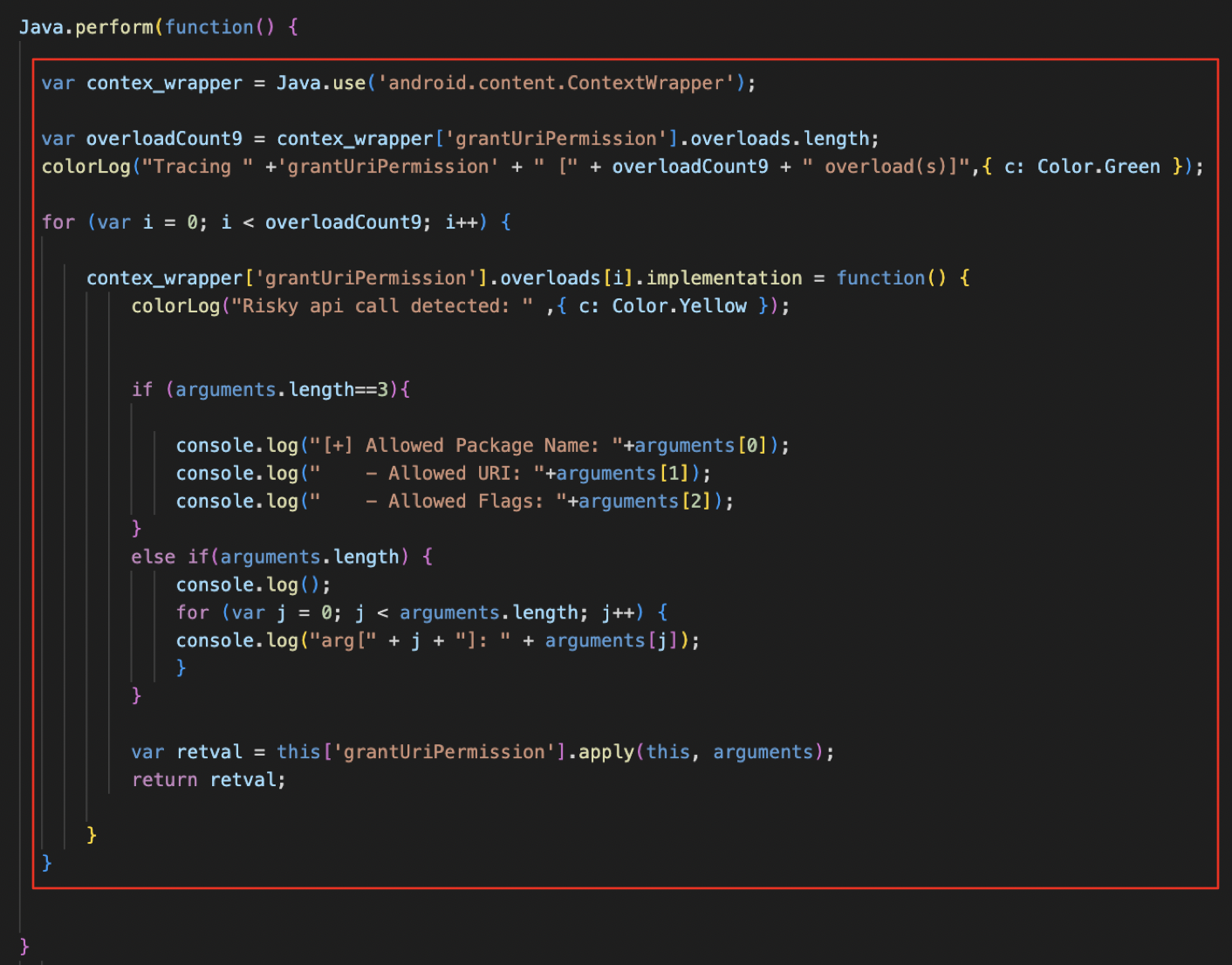
- Save it as /medusa/snippets/example.js
- Use the
import exampleto add it to the scratchpad
You can view the currently saved scripts by issuing the command snippet followed by a tab and then snippet [snippet_name] to view the script's code:

Medusa Wiki
Medusa Wiki
-
- Searching for the right module
- Getting info about a module
- Stashing / un-stashing
- Compiling
- Starting a session
- Hooking beyond the modules
- Importing Frida scripts
- Working with native libraries
- Working with the application's memory
- Getting Class and Object snapshots
- Useful utilities
- Saving a session (recipe)