-
Notifications
You must be signed in to change notification settings - Fork 233
Usage & FAQ
First of all, to perform the attacks you must have a network adapter that supports monitor mode, check airgeddon's Wiki for more info about this
Run as root (interface should be in managed mode)
wef -i wlan0Once you are inside the framework, you can use all the functions and attacks.
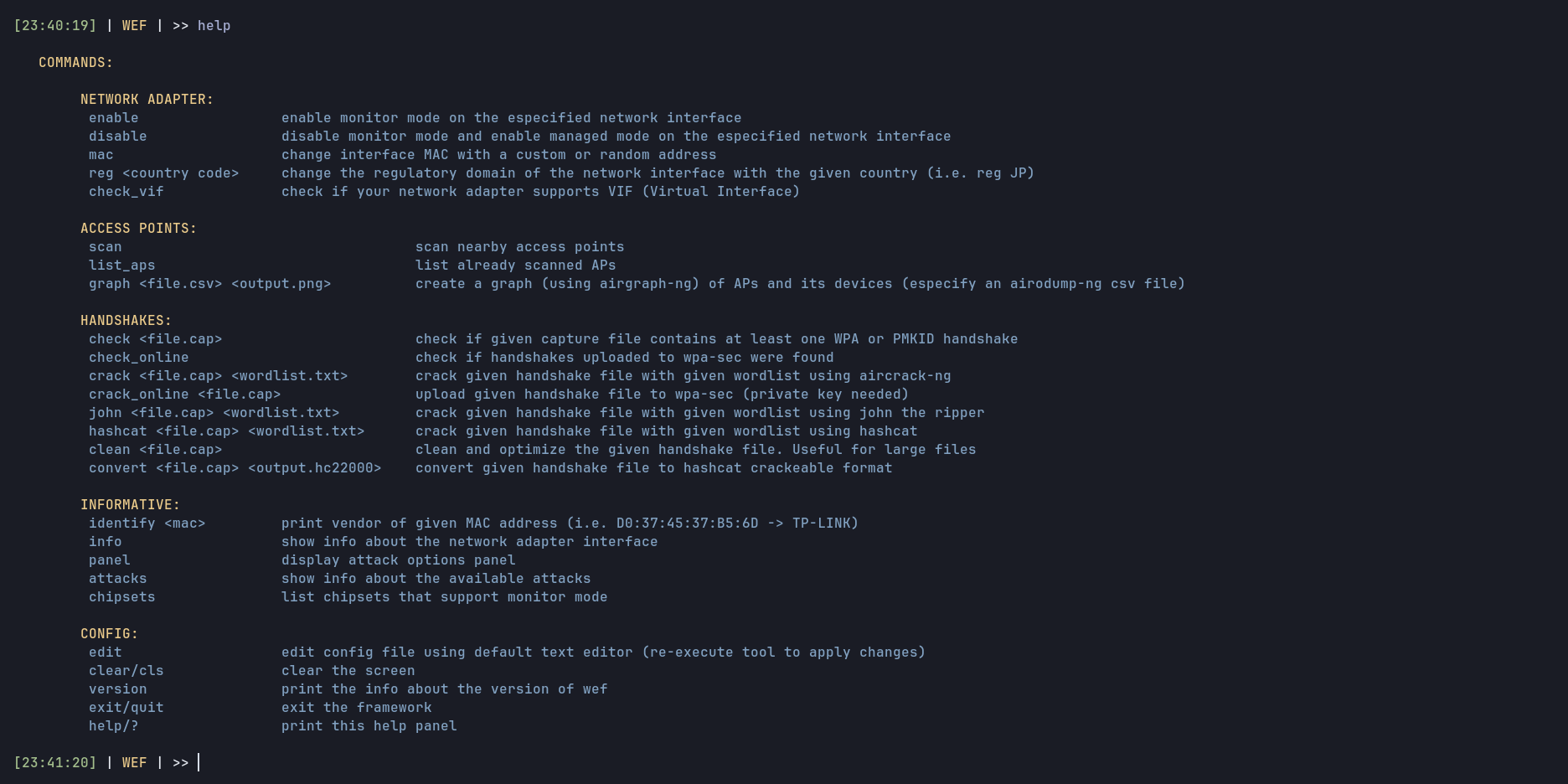
You can type "help" in order to display a panel with different commands and their descriptions.
The most common usage order of the tool would be:
- Enable monitor mode (enable command)
- Select attack (i.e. deauth)
- Select target and set attack parameters
- Launch attack and see results
At the start of the program, WEF does some checks and prints info (MAC address, interface name, current interface mode and frecuencies band). If it is the very first time you execute WEF, then it will ask you to create a configuration file you will be able to edit later. At the exit of the program it checks the monitor mode and other changes that has been made to revert it, so you don't have to worry about enabling or disabling the monitor mode, WEF does it for you.
You can select the different attacks by typing the number or typing the name of the attack. To perform the attacks, the interface should be in monitor mode, anyway the script detects the current mode so you will be notified.

WEF is fully compatible with 2 GHz and 5 GHz. Once you select an attack to perform, the tool will scan the nearby APs based on your configuration file (/usr/share/wef/wef.cnf), especifically based on the frequency_band value which accepts as value 2.4 for 2.4 GHz, 5 for 5 GHz and auto to detect the frequencies your network adapter supports (recommended)
If you enable the verbose (already enabled by default) you will see the output of the different tools like aireplay-ng or mdk4. It is better to have it enabled to know what is happening in each exact moment. You can configure it by editing config file and setting verbose to true or false
If you choose the wrong attack or you just want to go back to the main menu you can simply type "back" and press [Enter]. If the attack is running press Ctrl+C and it will ask to you to exit the tool, type "n" or "no" and the attack will stop and return you to the menu.
While doing attacks and scans, some files are created. However, they are removed when you exit the tool except files stored on /usr/share/wef/cache as they may be useful after using the tool (anyway they are deleted when the tools is executed again) so you don't have to worry about them. Only the files generated by airodump-ng (when capturing WPA handshakes) and hcxdumptool (when capturing PMKID handshakes) are saved under /usr/share/wef/main/captures/<target-AP-name>/ for later handshake cracking or using them on other tools like wireshark or kismet.
Also some logs are created with attack info like the AP channel, ESSID, BSSID, attack duration and date. Nevertheless, it is just done user side you don't have to worry about your attacks privacy. Its structure is the following:
[WEF] Wi-Fi Exploitation Framework
---------------------------------
Attack date: <day> <month> <year> <h:m:s>
Attack type: <attack type> (i.e. deauthentication)
Target access point: <ap-name>
BSSID: <bssid>
Attack duration: <duration>
AP channel: <channel>
---------------------------------
hcxtools output is a bit confusing if you aren't acquainted with it so you should know what everything means before launching the attack, this is the legend:
real time display:
R = + AP display: AP is in TX range or under attack
S = + AP display: AUTHENTICATION KEY MANAGEMENT PSK
P = + AP display: got PMKID
1 = + AP display: got EAPOL M1 (CHALLENGE)
3 = + AP display: got EAPOL M1M2M3 (AUTHORIZATION)
E = + CLIENT display: got EAP-START MESSAGE
2 = + CLIENT display: got EAPOL M1M2 (ROGUE CHALLENGE)
This attack may break and not work after some time as the project hcxtools is still in continuous development and the tools parameters may change leading to potential errors. If this happens, open an issue and I will try to re-implement it as soon as possible.
If you have experimented errors during the EvilTwin attack, and deauthentication is not working that could be due to a VIF problem. During the EvilTwin, the physical card is divided into 2 logical cards so if your adapter does not support this, it will cause errors. If you want to read more about that, read this from airgeddon's Wiki. Anyway if you want to manually check if your network adapter supports it, execute sudo iw list | grep "Supported interface modes" -A 8 and if you see "AP/VLAN" in output it means your network adapter allows VIF.
The main purpose of this attack is obtaining the password of the target AP by using a rogue AP.
[1] Rogue AP + Captive Portal
[2] Rogue AP + Captive Portal + DoS
[3] Rogue AP + Captive Portal + Wi-Fi Enterprise
[4] Rogue AP + Captive Portal + Wi-Fi Enterprise + DoS
The second one is the most recommended to deploy as it is faster, but also noiser since it deauthenticates connected devices. The tool asks the user some info and then it proceeds to set up all the things using hostapd, dnsmasq, lighttpd and aireplay-ng. As the legit network is being attacked and users cannot connect to it, they will see the fake AP with the same name (even same BSSID if you configure that option) and they will connect to it and provide its password on a simple but effective fake router login. Captive portal templates taken from airgeddon so all credits to v1s1t0r1sh3r3 and his awesome project.
If you want to set up an Evil Twin attack with a custom site template (i.e. google login), you can. WEF allows custom templates, you only have to select it when it asks to use pre-built or custom templates. Then you type the path to the template where it is stored and it should work. Just make sure the template works by its own before doing anything.