chore(deps): update module github.com/crossplane/crossplane to v1.17.2 [security] #84
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
This PR contains the following updates:
v1.17.1->v1.17.2GitHub Vulnerability Alerts
GHSA-7h65-4p22-39j6
A critical vulnerability was reported in the versions of golang that Crossplane depends on. Details of the golang vulnerability are included below. Crossplane does not directly use the vulnerable functions from the
net/netippackage, but the version of golang libraries, runtime, and build tools have still been updated as part of this security advisory nonetheless.Critical Vulnerabilities
Vulnerability: CVE-2024-24790,
golang: net/netip: Unexpected behavior from Is methods for IPv4-mapped IPv6 addressesDescription: The various Is methods (IsPrivate, IsLoopback, etc) did not work as expected for IPv4-mapped IPv6 addresses, returning false for addresses which would return true in their traditional IPv4 forms.
Affected versions: 1.17.1,1.16.2,1.15.5
See screenshot for more details
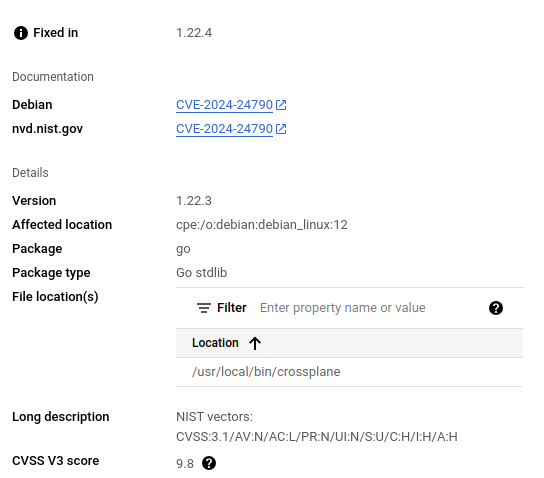
Fixed versions: 1.17.2,1.16.3,1.15.6
Release notes:
github.com/crossplane/crossplane: Unexpected behavior from Is methods for IPv4-mapped IPv6 addresses
GHSA-7h65-4p22-39j6 / GO-2024-3219
More information
Details
github.com/crossplane/crossplane: Unexpected behavior from Is methods for IPv4-mapped IPv6 addresses
Severity
Unknown
References
This data is provided by OSV and the Go Vulnerability Database (CC-BY 4.0).
github.com/crossplane/crossplane: Unexpected behavior from Is methods for IPv4-mapped IPv6 addresses
GHSA-7h65-4p22-39j6 / GO-2024-3219
More information
Details
A critical vulnerability was reported in the versions of golang that Crossplane depends on. Details of the golang vulnerability are included below. Crossplane does not directly use the vulnerable functions from the
net/netippackage, but the version of golang libraries, runtime, and build tools have still been updated as part of this security advisory nonetheless.Critical Vulnerabilities
Vulnerability: CVE-2024-24790,
golang: net/netip: Unexpected behavior from Is methods for IPv4-mapped IPv6 addressesDescription: The various Is methods (IsPrivate, IsLoopback, etc) did not work as expected for IPv4-mapped IPv6 addresses, returning false for addresses which would return true in their traditional IPv4 forms.
Affected versions: 1.17.1,1.16.2,1.15.5
See screenshot for more details

Fixed versions: 1.17.2,1.16.3,1.15.6
Release notes:
Severity
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:HReferences
This data is provided by OSV and the GitHub Advisory Database (CC-BY 4.0).
Release Notes
crossplane/crossplane (github.com/crossplane/crossplane)
v1.17.2Compare Source
This is a patch release scoped to fixing issues reported by users of Crossplane v1.17. First, this patch release addresses the below published security advisory that affects the versions of golang that Crossplane depends on.
Thank you @aditya-mayo for reporting this vulnerability! 🙇♂️
This release also addresses an issue (https://github.com/crossplane/crossplane/issues/5971) where users of v1.17 were not able to build or install Functions using v1 package metadata. Now that Functions have matured to v1, this will become much more pervasive throughout the Crossplane Functions ecosystem.
What's Changed
Full Changelog: crossplane/crossplane@v1.17.1...v1.17.2
Configuration
📅 Schedule: Branch creation - "" (UTC), Automerge - At any time (no schedule defined).
🚦 Automerge: Enabled.
♻ Rebasing: Whenever PR is behind base branch, or you tick the rebase/retry checkbox.
🔕 Ignore: Close this PR and you won't be reminded about this update again.
This PR was generated by Mend Renovate. View the repository job log.