-
Notifications
You must be signed in to change notification settings - Fork 2
QueryBooster Deployment
This guide will walk you through deploying QueryBooster on your server. Follow the steps below to set up and run QueryBooster.
Enter server and clone the project
ssh username@hostname
git clone https://github.com/ISG-ICS/QueryBooster.gitNavigate to the QueryBooster directory and set up a Python virtual environment, activate it, and install the required packages.
cd QueryBooster
python3 -m venv venv
source venv/bin/activate
pip install -r requirements.txtTo compile and deploy the QueryBooster client, go to the client directory and run the following commands:
cd client/
npm i
npm run buildNow, navigate to the server directory and start the QueryBooster server using Gunicorn:
cd ../server
gunicorn -w 4 -b 0.0.0.0:8000 'wsgi:app'You can access QueryBooster locally at http://ip:8000.
To enable HTTP and HTTPS traffic, make sure ports 80 and 443 are accessible by modifying your firewall rules. For CentOS, use the following commands:
sudo firewall-cmd --zone=public --add-port=80/tcp --permanent
sudo firewall-cmd --zone=public --add-port=443/tcp --permanent
sudo firewall-cmd --reload
sudo firewall-cmd --zone=public --list-allTo ensure that QueryBooster starts automatically after server reboots or crashes, create a systemd service unit file.
sudo vi /etc/systemd/system/querybooster.serviceAdd the following content to the querybooster.service file:
[Unit]
Description=Gunicorn instance to serve Flask app
After=network.target
[Service]
User=waans11
Group=waans11
WorkingDirectory=/home/waans11/QueryBooster/server
Environment="PATH=/home/waans11/QueryBooster/venv/bin"
ExecStart=/bin/bash -c 'source /home/waans11/QueryBooster/venv/bin/activate; gunicorn -w 4 --bind 127.0.0.1:8000 wsgi:app'
[Install]
WantedBy=multi-user.targetReload the systemd manager configuration and start the QueryBooster service:
systemctl daemon-reload
sudo systemctl start querybooster
sudo systemctl enable querybooster
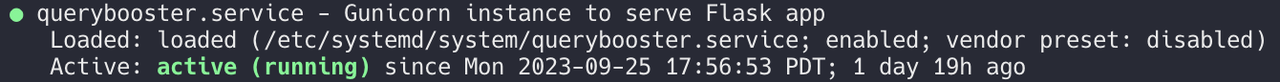
sudo systemctl status queryboosterThe sudo systemctl enable querybooster command ensures that QueryBooster starts automatically on system boot.
The command sudo systemctl status querybooster will show if querybooster is active:
Generate a key file (server.key) and a Certificate Signing Request (CSR) file (server.csr). Make sure to set a password for the key file.
*** Note: we will be needing the password when we set up Nginx so do NOT forget the password***
- Generate key file:
openssl genrsa -des3 -out server.key 2048- Generate CSR file:
openssl req -new -key server.key -out server.csrHere's the information that you'll need to create the CSR.
- Country Name (2 letter code) [XX]:US
- State or Province Name (full name) []:California
- Locality Name (eg, city) [Default City]:Irvine
- Organization Name (eg, company) [Default Company Ltd]:University of California, Irvine
- Organizational Unit Name (eg, section) []:Donald Bren School of Information and Computer Sciences
- Common Name (eg, your name or your server's hostname) []: <=== ENTER THE DOMAIN NAME OF THE SERVER (e.g., cloudberry.ics.uci.edu)
- Email Address []:helpdesk@ics.uci.edu
Please enter the following 'extra' attributes to be sent with your certificate request
- A challenge password []: <=== LEAVE BLANK
- An optional company name []: <=== LEAVE BLANK
Send server.csr to UCI HelpDesk(helpdesk@ics.uci.edu), server.key is not needed to be sent. They will generate a signed certificate file. There are multiple formats for that certificate file, please use PEM format (if multiple files are available, use the first link in the download email for the following example), and here we name it server.crt.
Note 1: So far there are three files: server.key, server.csr, server.crt. Please note for the difference. You only need server.csr to obtain server.crt, and no longer needed it for following steps. For all following steps, you should be using server.crt
Note 2: if the files are located under /etc/nginx/ssl/ there might be problems with File access: permission denied due to system security policy.
Install Nginx based on your OS. For CentOS, use the following commands:
sudo yum install epel-release
sudo yum update
sudo yum install nginxfor more information: https://docs.nginx.com/nginx/admin-guide/installing-nginx/installing-nginx-open-source/
If you have created a password for server.key. You need to create a file named querybooster.pass inside /etc/ssl/certs/ so that nginx can access the server.py file.
Use the command below and write down the password:
sudo vi /etc/ssl/certs/querybooster.passThe files we modify inside nginx are /etc/nginx/nginx.conf and /etc/nginx/conf.d/query_booster.conf
Modify nginx.conf to the following:
user nginx;
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /run/nginx.pid;
# Load dynamic modules. See /usr/share/doc/nginx/README.dynamic.
include /usr/share/nginx/modules/*.conf;
events {
worker_connections 1024;
}
http {
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 4096;
include /etc/nginx/mime.types;
default_type application/octet-stream;
# Load modular configuration files from the /etc/nginx/conf.d directory.
# See http://nginx.org/en/docs/ngx_core_module.html#include
# for more information.
include /etc/nginx/conf.d/*;
}Create file query_booster.conf:
sudo vi /etc/nginx/conf.d/query_booster.confAdd the following content to the query_booster.conf file:
server {
listen 80;
listen 443 ssl;
server_name querybooster.ics.uci.edu;
ssl_certificate /etc/ssl/certs/querybooster_ics_uci_edu.pem;
ssl_certificate_key /etc/ssl/certs/server.key;
ssl_password_file /etc/ssl/certs/querybooster.pass;
location / {
proxy_pass http://127.0.0.1:8000/;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-Prefix /;
}
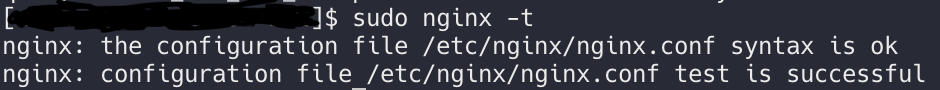
}Test the Nginx configuration file for syntax errors:
sudo nginx -tThe output should look similar to this:
Otherwise, check nginx.conf and query_booster.conf for syntax errors.
sudo nginx -s reload
sudo systemctl start nginx # or sudo systemctl restart nginxNow, you can access QueryBooster through the domain querybooster.ics.uci.edu from the web server.