Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
fix: update verifier interface and address gen (#13124)
## Description this PR contains mainly 3 changes: 1. update to use the new entrypoint in fastcrypto: verify_zklogin 2. update JWK updater to use fetch_jwks in fastcrypto and store the (kid, iss) -> jwk mapping, instead of kid -> jwk. so we can support multiple iss (providers). this also lets fastcrypto manage "supported providers". few renaming from OAuthProviderContent to JWK. 3. protocol config change: zklogin_supported_providers, use_secure_vk. zklogin_auth flag still in place this is only enabled for devnet. (4 for testing) keytool command for e2e testing based on MystenLabs/fastcrypto#615 ## Test Plan ``` # start a localnet cargo run --bin sui-test-validator # in another tab cargo build --bin sui && target/debug/sui keytool zk-login-sign-and-execute-tx --max-epoch 10 --fixed true # use prompt to test 3 providers' url, use fixed if you want the default key and randomness Ephemeral key identifier: 0xcc2196ee1fa156836daf9bb021d88d648a0023fa387e695d3701667a634a331f Ephemeral pubkey (BigInt): 84029355920633174015103288781128426107680789454168570548782290541079926444544 Jwt randomness: 100681567828351849884072155819400689117 Visit URL (Google): https://accounts.google.com/o/oauth2/v2/auth?client_id=575519204237-msop9ep45u2uo98hapqmngv8d84qdc8k.apps.googleusercontent.com&response_type=id_token&redirect_uri=https://sui.io/&scope=openid&nonce=hTPpgF7XAKbW37rEUS6pEVZqmoI Visit URL (Twitch): https://id.twitch.tv/oauth2/authorize?client_id=rs1bh065i9ya4ydvifixl4kss0uhpt&force_verify=true&lang=en&login_type=login&redirect_uri=https://sui.io/&response_type=id_token&scope=openid&nonce=hTPpgF7XAKbW37rEUS6pEVZqmoI Visit URL (Facebook): https://www.facebook.com/v17.0/dialog/oauth?client_id=233307156352917&redirect_uri=https://sui.io/&scope=openid&nonce=hTPpgF7XAKbW37rEUS6pEVZqmoI&response_type=id_token Finish login and paste the entire URL here (e.g. https://sui.io/#id_token=...): https://sui.io/#id_token=$YOUR_TOKEN_HERE&authuser=1&prompt=none User salt: 37603297217831327253368351620768767386 ZkLogin inputs: "{\"proof_points\":{\"pi_a\":[\"11919750190958936097341971645310122361427237718339506968604484178434524183763\",\"4066396655503961643966719205021673883457905225199432791695293704762383515464\",\"1\"],\"pi_b\":[[\"4944611897670024879056817717532675736403113855465546218202719469807483285716\",\"16588919619512150925750036824511259013041883375734888504590662076356111031305\"],[\"21216051686412759119183634053470555744351991062479561416927343692238334485548\",\"7497144533451348825947902642248234141372654747858237668577407146943851844730\"],[\"1\",\"0\"]],\"pi_c\":[\"14631487662109801464392056573524864320058039577512853397500854951219322772917\",\"17171172537255313036364669593310031389402112944054741144631323570508702243961\",\"1\"]},\"address_seed\":\"6766845480040838487230155646516397460223616307094485793506729789519059777352\",\"claims\":[{\"name\":\"iss\",\"value_base64\":\"yJpc3MiOiJodHRwczovL2FjY291bnRzLmdvb2dsZS5jb20iLC\",\"index_mod_4\":1},{\"name\":\"aud\",\"value_base64\":\"CJhdWQiOiI1NzU1MTkyMDQyMzctbXNvcDllcDQ1dTJ1bzk4aGFwcW1uZ3Y4ZDg0cWRjOGsuYXBwcy5nb29nbGV1c2VyY29udGVudC5jb20iLC\",\"index_mod_4\":1}],\"header_base64\":\"eyJhbGciOiJSUzI1NiIsImtpZCI6IjdjOWM3OGUzYjAwZTFiYjA5MmQyNDZjODg3YjExMjIwYzg3YjdkMjAiLCJ0eXAiOiJKV1QifQ\"}" ZkLogin Address: 0x504aade5d02308b1b7e58775adde9e1316f71898e2996c94ddd668fd559cdf32 Faucet requested and created test transaction: V1(TransactionDataV1 { kind: ProgrammableTransaction(ProgrammableTransaction { inputs: [Pure([190, 243, 14, 103, 26, 137, 73, 150, 28, 21, 83, 14, 186, 35, 123, 183, 214, 96, 104, 37, 174, 31, 244, 109, 131, 136, 4, 129, 106, 24, 197, 127]), Object(ImmOrOwnedObject((0xd93388f0bcdd1730ee4d5ff3b73a2f5301a2f6e13df3b84d23155698a9b450c6, SequenceNumber(2), o#FFJqkV96f6VtsyGKEn2BqJokAy6oGuW3SUsYtthgrvCk)))], commands: [TransferObjects([Input(1)], Input(0))] }), sender: 0x504aade5d02308b1b7e58775adde9e1316f71898e2996c94ddd668fd559cdf32, gas_data: GasData { payment: [(0x3f34a90f021abdc7928c335da354553255b96af4f8237a7d896a98febb58ab9e, SequenceNumber(2), o#3q1NmyLmHyskTwSMG7r7rSBDUd1kkiZQULoXmDGYDH8S)], owner: 0x504aade5d02308b1b7e58775adde9e1316f71898e2996c94ddd668fd559cdf32, price: 1000, budget: 5000000 }, expiration: None }) ZkLogin Authenticator Signature Serialized: "BQNNMTE5MTk3NTAxOTA5NTg5MzYwOTczNDE5NzE2NDUzMTAxMjIzNjE0MjcyMzc3MTgzMzk1MDY5Njg2MDQ0ODQxNzg0MzQ1MjQxODM3NjNMNDA2NjM5NjY1NTUwMzk2MTY0Mzk2NjcxOTIwNTAyMTY3Mzg4MzQ1NzkwNTIyNTE5OTQzMjc5MTY5NTI5MzcwNDc2MjM4MzUxNTQ2NAExAwJMNDk0NDYxMTg5NzY3MDAyNDg3OTA1NjgxNzcxNzUzMjY3NTczNjQwMzExMzg1NTQ2NTU0NjIxODIwMjcxOTQ2OTgwNzQ4MzI4NTcxNk0xNjU4ODkxOTYxOTUxMjE1MDkyNTc1MDAzNjgyNDUxMTI1OTAxMzA0MTg4MzM3NTczNDg4ODUwNDU5MDY2MjA3NjM1NjExMTAzMTMwNQJNMjEyMTYwNTE2ODY0MTI3NTkxMTkxODM2MzQwNTM0NzA1NTU3NDQzNTE5OTEwNjI0Nzk1NjE0MTY5MjczNDM2OTIyMzgzMzQ0ODU1NDhMNzQ5NzE0NDUzMzQ1MTM0ODgyNTk0NzkwMjY0MjI0ODIzNDE0MTM3MjY1NDc0Nzg1ODIzNzY2ODU3NzQwNzE0Njk0Mzg1MTg0NDczMAIBMQEwA00xNDYzMTQ4NzY2MjEwOTgwMTQ2NDM5MjA1NjU3MzUyNDg2NDMyMDA1ODAzOTU3NzUxMjg1MzM5NzUwMDg1NDk1MTIxOTMyMjc3MjkxN00xNzE3MTE3MjUzNzI1NTMxMzAzNjM2NDY2OTU5MzMxMDAzMTM4OTQwMjExMjk0NDA1NDc0MTE0NDYzMTMyMzU3MDUwODcwMjI0Mzk2MQExTDY3NjY4NDU0ODAwNDA4Mzg0ODcyMzAxNTU2NDY1MTYzOTc0NjAyMjM2MTYzMDcwOTQ0ODU3OTM1MDY3Mjk3ODk1MTkwNTk3NzczNTICA2lzczF5SnBjM01pT2lKb2RIUndjem92TDJGalkyOTFiblJ6TG1kdmIyZHNaUzVqYjIwaUxDAQNhdWRtQ0poZFdRaU9pSTFOelUxTVRreU1EUXlNemN0YlhOdmNEbGxjRFExZFRKMWJ6azRhR0Z3Y1cxdVozWTRaRGcwY1dSak9Hc3VZWEJ3Y3k1bmIyOW5iR1YxYzJWeVkyOXVkR1Z1ZEM1amIyMGlMQwFmZXlKaGJHY2lPaUpTVXpJMU5pSXNJbXRwWkNJNklqZGpPV00zT0dVellqQXdaVEZpWWpBNU1tUXlORFpqT0RnM1lqRXhNakl3WXpnM1lqZGtNakFpTENKMGVYQWlPaUpLVjFRaWZRCgAAAAAAAABhADkEuv1BTfolleAyzVWVZC/TpCtO0wljxjTRZKfGddxxNhfZ4hRlq438Mo6e/8HnlOZ040OFN4uAzvgrfv4G4gW5xu4WMO8+cRFEpkjbBruyKE9ydM++5T/87lA8waSSAA==" ╭──────────┬────────────────────────────────────────────────╮ │ txDigest │ 9V1ie4CkQ3afLtgAGKEmGQApjahkBUu7SAUFw6jRMRjJ │ ╰──────────┴────────────────────────────────────────────────╯ 2023-08-15T20:42:27.650449Z INFO sui::keytool: ╭──────────┬────────────────────────────────────────────────╮ 2023-08-15T20:42:27.650509Z INFO sui::keytool: │ txDigest │ 9V1ie4CkQ3afLtgAGKEmGQApjahkBUu7SAUFw6jRMRjJ │ 2023-08-15T20:42:27.650515Z INFO sui::keytool: ╰──────────┴────────────────────────────────────────────────╯ # the above command should work fine for google and twitch, if the above command does not work for facebook due to pasting issue, use this command instead. all the inputs should be printed from the above command. target/debug/sui keytool zk-login-enter-token --ephemeral-key-identifier 0xcc2196ee1fa156836daf9bb021d88d648a0023fa387e695d3701667a634a331f --max-epoch 10 --jwt-randomness 100681567828351849884072155819400689117 --kp-bigint 84029355920633174015103288781128426107680789454168570548782290541079926444544 --parsed-token $JWT_TOKEN # use prompt to test 3 providers' url, use fixed if you want the default key and randomness Ephemeral key identifier: 0xcc2196ee1fa156836daf9bb021d88d648a0023fa387e695d3701667a634a331f Ephemeral pubkey (BigInt): 84029355920633174015103288781128426107680789454168570548782290541079926444544 Jwt randomness: 100681567828351849884072155819400689117 Visit URL (Google): https://accounts.google.com/o/oauth2/v2/auth?client_id=575519204237-msop9ep45u2uo98hapqmngv8d84qdc8k.apps.googleusercontent.com&response_type=id_token&redirect_uri=https://sui.io/&scope=openid&nonce=hTPpgF7XAKbW37rEUS6pEVZqmoI Visit URL (Twitch): https://id.twitch.tv/oauth2/authorize?client_id=rs1bh065i9ya4ydvifixl4kss0uhpt&force_verify=true&lang=en&login_type=login&redirect_uri=https://sui.io/&response_type=id_token&scope=openid&nonce=hTPpgF7XAKbW37rEUS6pEVZqmoI Visit URL (Facebook): https://www.facebook.com/v17.0/dialog/oauth?client_id=233307156352917&redirect_uri=https://sui.io/&scope=openid&nonce=hTPpgF7XAKbW37rEUS6pEVZqmoI&response_type=id_token Finish login and paste the entire URL here (e.g. https://sui.io/#id_token=...): https://sui.io/#id_token=$YOUR_TOKEN_HERE&authuser=1&prompt=none User salt: 37603297217831327253368351620768767386 ZkLogin inputs: "{\"proof_points\":{\"pi_a\":[\"11919750190958936097341971645310122361427237718339506968604484178434524183763\",\"4066396655503961643966719205021673883457905225199432791695293704762383515464\",\"1\"],\"pi_b\":[[\"4944611897670024879056817717532675736403113855465546218202719469807483285716\",\"16588919619512150925750036824511259013041883375734888504590662076356111031305\"],[\"21216051686412759119183634053470555744351991062479561416927343692238334485548\",\"7497144533451348825947902642248234141372654747858237668577407146943851844730\"],[\"1\",\"0\"]],\"pi_c\":[\"14631487662109801464392056573524864320058039577512853397500854951219322772917\",\"17171172537255313036364669593310031389402112944054741144631323570508702243961\",\"1\"]},\"address_seed\":\"6766845480040838487230155646516397460223616307094485793506729789519059777352\",\"claims\":[{\"name\":\"iss\",\"value_base64\":\"yJpc3MiOiJodHRwczovL2FjY291bnRzLmdvb2dsZS5jb20iLC\",\"index_mod_4\":1},{\"name\":\"aud\",\"value_base64\":\"CJhdWQiOiI1NzU1MTkyMDQyMzctbXNvcDllcDQ1dTJ1bzk4aGFwcW1uZ3Y4ZDg0cWRjOGsuYXBwcy5nb29nbGV1c2VyY29udGVudC5jb20iLC\",\"index_mod_4\":1}],\"header_base64\":\"eyJhbGciOiJSUzI1NiIsImtpZCI6IjdjOWM3OGUzYjAwZTFiYjA5MmQyNDZjODg3YjExMjIwYzg3YjdkMjAiLCJ0eXAiOiJKV1QifQ\"}" ZkLogin Address: 0x504aade5d02308b1b7e58775adde9e1316f71898e2996c94ddd668fd559cdf32 Faucet requested and created test transaction: V1(TransactionDataV1 { kind: ProgrammableTransaction(ProgrammableTransaction { inputs: [Pure([190, 243, 14, 103, 26, 137, 73, 150, 28, 21, 83, 14, 186, 35, 123, 183, 214, 96, 104, 37, 174, 31, 244, 109, 131, 136, 4, 129, 106, 24, 197, 127]), Object(ImmOrOwnedObject((0xd93388f0bcdd1730ee4d5ff3b73a2f5301a2f6e13df3b84d23155698a9b450c6, SequenceNumber(2), o#FFJqkV96f6VtsyGKEn2BqJokAy6oGuW3SUsYtthgrvCk)))], commands: [TransferObjects([Input(1)], Input(0))] }), sender: 0x504aade5d02308b1b7e58775adde9e1316f71898e2996c94ddd668fd559cdf32, gas_data: GasData { payment: [(0x3f34a90f021abdc7928c335da354553255b96af4f8237a7d896a98febb58ab9e, SequenceNumber(2), o#3q1NmyLmHyskTwSMG7r7rSBDUd1kkiZQULoXmDGYDH8S)], owner: 0x504aade5d02308b1b7e58775adde9e1316f71898e2996c94ddd668fd559cdf32, price: 1000, budget: 5000000 }, expiration: None }) ZkLogin Authenticator Signature Serialized: "BQNNMTE5MTk3NTAxOTA5NTg5MzYwOTczNDE5NzE2NDUzMTAxMjIzNjE0MjcyMzc3MTgzMzk1MDY5Njg2MDQ0ODQxNzg0MzQ1MjQxODM3NjNMNDA2NjM5NjY1NTUwMzk2MTY0Mzk2NjcxOTIwNTAyMTY3Mzg4MzQ1NzkwNTIyNTE5OTQzMjc5MTY5NTI5MzcwNDc2MjM4MzUxNTQ2NAExAwJMNDk0NDYxMTg5NzY3MDAyNDg3OTA1NjgxNzcxNzUzMjY3NTczNjQwMzExMzg1NTQ2NTU0NjIxODIwMjcxOTQ2OTgwNzQ4MzI4NTcxNk0xNjU4ODkxOTYxOTUxMjE1MDkyNTc1MDAzNjgyNDUxMTI1OTAxMzA0MTg4MzM3NTczNDg4ODUwNDU5MDY2MjA3NjM1NjExMTAzMTMwNQJNMjEyMTYwNTE2ODY0MTI3NTkxMTkxODM2MzQwNTM0NzA1NTU3NDQzNTE5OTEwNjI0Nzk1NjE0MTY5MjczNDM2OTIyMzgzMzQ0ODU1NDhMNzQ5NzE0NDUzMzQ1MTM0ODgyNTk0NzkwMjY0MjI0ODIzNDE0MTM3MjY1NDc0Nzg1ODIzNzY2ODU3NzQwNzE0Njk0Mzg1MTg0NDczMAIBMQEwA00xNDYzMTQ4NzY2MjEwOTgwMTQ2NDM5MjA1NjU3MzUyNDg2NDMyMDA1ODAzOTU3NzUxMjg1MzM5NzUwMDg1NDk1MTIxOTMyMjc3MjkxN00xNzE3MTE3MjUzNzI1NTMxMzAzNjM2NDY2OTU5MzMxMDAzMTM4OTQwMjExMjk0NDA1NDc0MTE0NDYzMTMyMzU3MDUwODcwMjI0Mzk2MQExTDY3NjY4NDU0ODAwNDA4Mzg0ODcyMzAxNTU2NDY1MTYzOTc0NjAyMjM2MTYzMDcwOTQ0ODU3OTM1MDY3Mjk3ODk1MTkwNTk3NzczNTICA2lzczF5SnBjM01pT2lKb2RIUndjem92TDJGalkyOTFiblJ6TG1kdmIyZHNaUzVqYjIwaUxDAQNhdWRtQ0poZFdRaU9pSTFOelUxTVRreU1EUXlNemN0YlhOdmNEbGxjRFExZFRKMWJ6azRhR0Z3Y1cxdVozWTRaRGcwY1dSak9Hc3VZWEJ3Y3k1bmIyOW5iR1YxYzJWeVkyOXVkR1Z1ZEM1amIyMGlMQwFmZXlKaGJHY2lPaUpTVXpJMU5pSXNJbXRwWkNJNklqZGpPV00zT0dVellqQXdaVEZpWWpBNU1tUXlORFpqT0RnM1lqRXhNakl3WXpnM1lqZGtNakFpTENKMGVYQWlPaUpLVjFRaWZRCgAAAAAAAABhADkEuv1BTfolleAyzVWVZC/TpCtO0wljxjTRZKfGddxxNhfZ4hRlq438Mo6e/8HnlOZ040OFN4uAzvgrfv4G4gW5xu4WMO8+cRFEpkjbBruyKE9ydM++5T/87lA8waSSAA==" ╭──────────┬────────────────────────────────────────────────╮ │ txDigest │ 9V1ie4CkQ3afLtgAGKEmGQApjahkBUu7SAUFw6jRMRjJ │ ╰──────────┴────────────────────────────────────────────────╯ 2023-08-15T20:42:27.650449Z INFO sui::keytool: ╭──────────┬────────────────────────────────────────────────╮ 2023-08-15T20:42:27.650509Z INFO sui::keytool: │ txDigest │ 9V1ie4CkQ3afLtgAGKEmGQApjahkBUu7SAUFw6jRMRjJ │ 2023-08-15T20:42:27.650515Z INFO sui::keytool: ╰──────────┴────────────────────────────────────────────────╯ # the above command should work fine for google and twitch, if the above command does not work for facebook due to pasting issue, use this command instead. all the inputs should be printed from the above command. target/debug/sui keytool zk-login-enter-token --ephemeral-key-identifier 0xcc2196ee1fa156836daf9bb021d88d648a0023fa387e695d3701667a634a331f --max-epoch 10 --jwt-randomness 100681567828351849884072155819400689117 --kp-bigint 84029355920633174015103288781128426107680789454168570548782290541079926444544 --parsed-token $JWT_TOKEN ``` https://suiexplorer.com/txblock/9V1ie4CkQ3afLtgAGKEmGQApjahkBUu7SAUFw6jRMRjJ?network=local 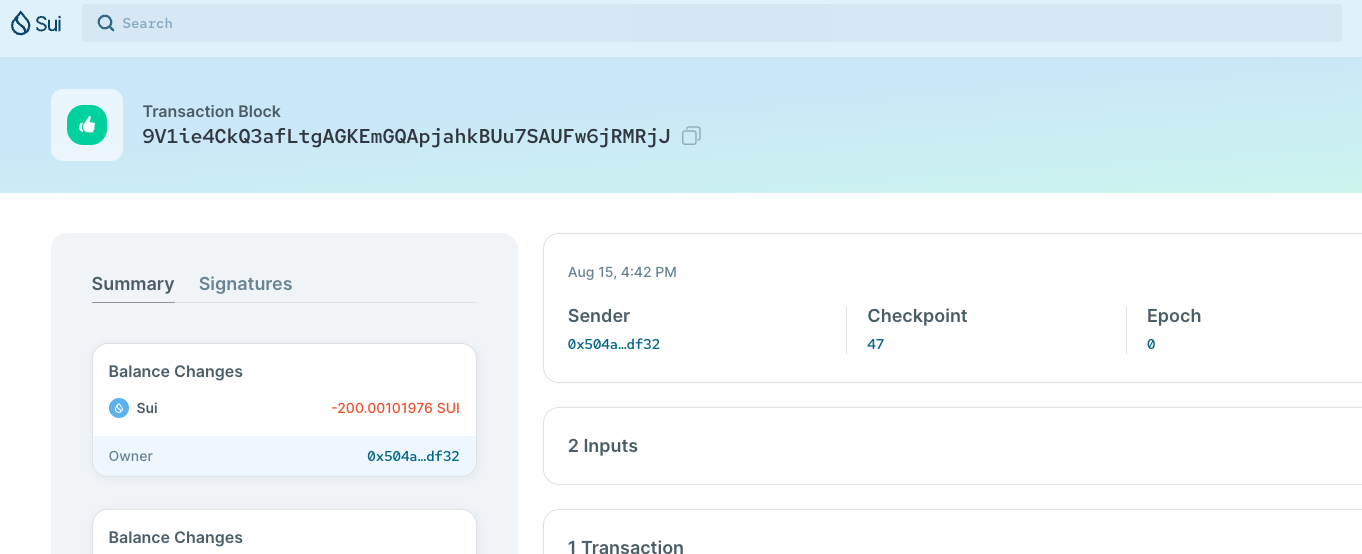 --- If your changes are not user-facing and not a breaking change, you can skip the following section. Otherwise, please indicate what changed, and then add to the Release Notes section as highlighted during the release process. ### Type of Change (Check all that apply) - [x] protocol change - [ ] user-visible impact - [ ] breaking change for a client SDKs - [ ] breaking change for FNs (FN binary must upgrade) - [x] breaking change for validators or node operators (must upgrade binaries) - [ ] breaking change for on-chain data layout - [ ] necessitate either a data wipe or data migration ### Release notes
- Loading branch information