📕 Glossary
Defines all the specific terms and vocabulary used throughout
Participants should use this glossary to ensure consistency and avoid the following happenstances.
- referring to the same thing using different names
- referring to different things using the same name (even worse)
Host-specific System Configuration
Purpose
The
/etc/hierarchy contains configuration files. A "configuration file" is a local file used to control the operation of a program; it must be static and cannot be an executable binary.1
To be clear,
/etc/may contain executable scripts, such as the command scripts commonly called byinitto start and shut down the system and start daemon processes. "Executable binary" in this context refers to direct machine code or pseudocode not in a human-readable format, such as native ELF executables.
Requirements
No binaries may be located under
/etc/.1The following directories, or symbolic links to directories are required in
/etc/:
Directory Description optConfiguration for /opt/
Specific Options
The following directories, or symbolic links to directories must be in
/etc/, if the corresponding subsystem is installed:
Directory Description X11Configuration for the X Window system (optional) sgmlConfiguration for SGML (optional) xmlConfiguration for XML (optional)
Systems that use the shadow password suite will have additional configuration files in
/etc/(/etc/shadow/and others) and programs in/usr/sbin/(useradd,usermod, and others).
The following files, or symbolic links to files, must be in
/etc/if the corresponding subsystem is installed:File Description csh.loginSystemwide initialization file for C shell logins (optional) exportsNFS filesystem access control list (optional) fstabStatic information about filesystems (optional) ftpusersFTP daemon user access control list (optional) gatewaysFile which lists gateways for routed (optional) gettydefsSpeed and terminal settings used by getty (optional) groupUser group file (optional) host.confResolver configuration file (optional) hostsStatic information about host names (optional) hosts.allowHost access file for TCP wrappers (optional) hosts.denyHost access file for TCP wrappers (optional) hosts.equivList of trusted hosts for rlogin, rsh, rcp (optional) hosts.lpdList of trusted hosts for lpd (optional) inetd.confConfiguration file for inetd (optional) inittabConfiguration file for init (optional) issuePre-login message and identification file (optional) ld.so.confList of extra directories to search for shared libraries (optional) motdPost-login message of the day file (optional) mtabDynamic information about filesystems (optional) mtools.confConfiguration file for mtools (optional) networksStatic information about network names (optional) passwdThe password file (optional) printcapThe lpd printer capability database (optional) profileSystemwide initialization file for sh shell logins (optional) protocolsIP protocol listing (optional) resolv.confResolver configuration file (optional) rpcRPC protocol listing (optional) securettyTTY access control for root login (optional) servicesPort names for network services (optional) shellsPathnames of valid login shells (optional) syslog.confConfiguration file for syslogd (optional)
mtabdoes not fit the static nature of/etc/: it is excepted for historical reasons.1
On some Linux systems,
/etc/mtabmay be a symbolic link to/proc/mounts, in which case this exception is not required.-
/etc/fstab⚓ -
A configuration file that contains entries identifying the storage device partitions Linux should mount at boot time.
👁️🗨️ Learn more…
-
A dynamic file that identifies the currently mounted partitions on the Linux system.
-
The main configuration file for
rsyslog, you can specify the rules according to whichrsyslogdhandles the messages. Generally, you can classify messages by their source and topic (facility) and urgency (priority), and then assign an action that should be performed when a message fits these criteria.2In
/etc/rsyslog.conf, you can also see a list of log files maintained byrsyslogd. Most log files are located in the/var/log/directory. Some applications, such ashttpdandsamba, store their log files in a subdirectory within/var/log/.2Additional resources
- The
rsyslogd(8)andrsyslog.conf(5)man pages. - Documentation installed with the
rsyslog-docpackage in the/usr/share/doc/rsyslog/html/index.htmlfile.2
- The
-
A detailed method of assigning granular user and group permissions to files and directories in a Linux system distinct from and more advanced than that which is governed by the
chmodcommand; involves setting an access control list (ACL) for each file and directory.ACLs allow system administrators to define not just read, write, and execute permissions for multiple users or groups but also more advanced rules like set user ID on execution, set group ID on execution, and inherited permissions.
On the flip side, ACLs allow file owners to specify extended access information about a file, granting additional rights to users/groups other than those owning the file. This form of discretionary access control allows users to manage their own collaborative projects without intervention of system administrators to maintain groups, but also without granting rights to all users on the system via use of the "other" permission bits.3
The
setfaclcommand allows one to set these permissions, and thegetfaclcommand allows one to view these permissions as they exist in real-time.For example, an ACL could allow user Bob read/write access to
file1.txtwhile denying access tofile2.txt, allow thesysadmingroup full access to a set of configuration files, and set thesetuidbit on a program while removing access for other users.ACLs are implemented as extended attributes in the [Linux ext file systems][] and store the security rules in the metadata of the file or directory being protected rather than altering the standard Unix permission bits. This allows them to augment and extend the standard Unix file permissions model and are critical for implementing least privilege and defense in depth when securing sensitive Linux resources.
The next level of security involves setting context-based permissions à la SELinux (for Red Hat–based Linux distributions) and AppArmor (for Debian-based Linux distributions).
-
An application used by Debian-based distributions to implement context-based permissions for applications.
-
A command-line command that allows the owner or system administrator to change the group assigned to a file or directory.
-
A command-line command that allows the system administrator to change the permissions assigned to a file or directory.
-
A command-line command that allows the system administrator to change the owner of a file or directory.
-
A Linux distribution derived from the sources of Red Hat Enterprise Linux (RHEL).4
-
A command-line command that allows a way to perform commands as another user. It aims to be a a simplified and lightweight replacement for
sudo.doasis easy to configure and use and suits most use cases.5 Thedoastool was originally developed for OpenBSD as a simpler and safersudoreplacement and was released with OpenBSD 5.8 in October 2015 replacingsudo.67For a smooth transition from
sudotodoasand to stay downward compatible, one may add the following to one's own shell environment.8alias sudo='doas' alias sudoedit='doas rnano'
-
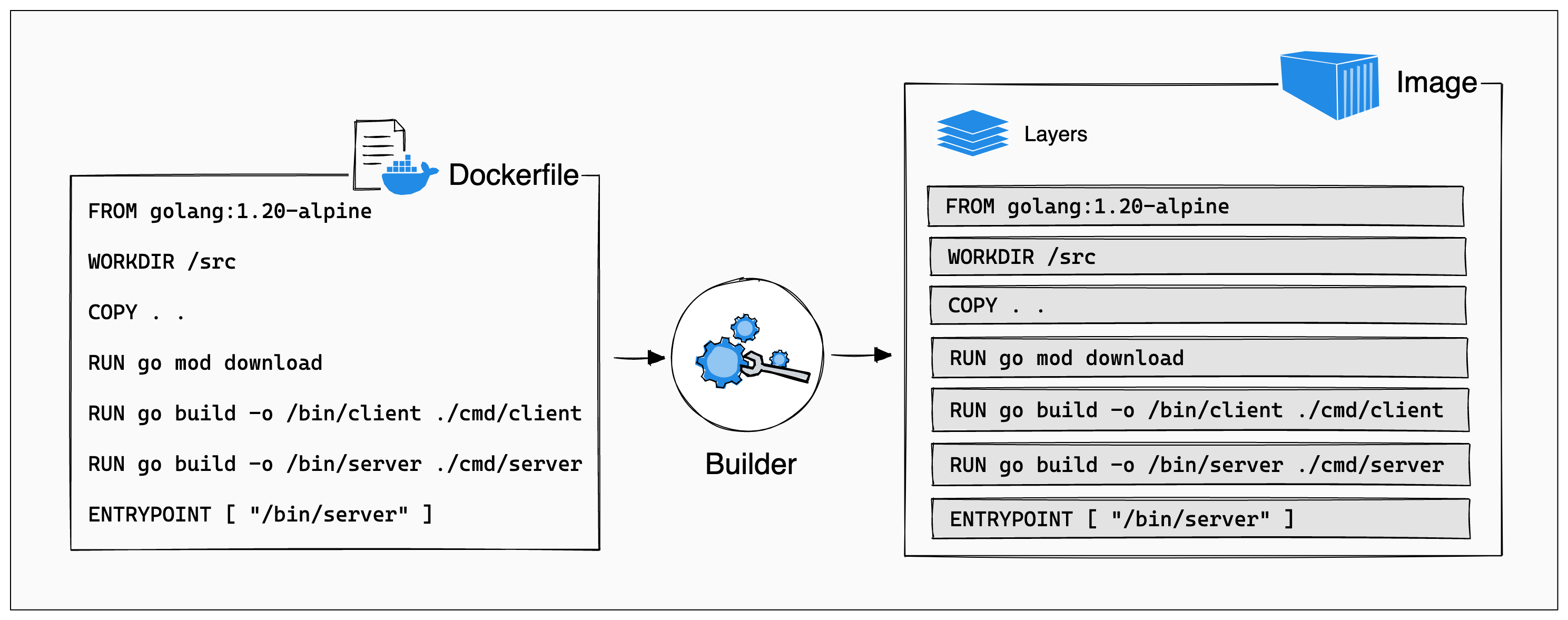
An image is a read-only template with instructions for creating a Docker container. Often, an image is based on another image, with some additional customization. For example, you may build an image which is based on the
ubuntuimage, but installs the Apache web server and your application, as well as the configuration details needed to make your application run.9 -
The order of Dockerfile instructions matter. A Docker build consists of a series of ordered build instructions. Each instruction in a Dockerfile roughly translates to an image layer. The following diagram illustrates how a Dockerfile translates into a stack of layers in a container image.10
Docker images have intermediate layers that increase reusability, decrease disk usage, and speed up docker build by allowing each step to be cached. These intermediate layers are not shown by default.11
Each
RUNinstruction will create a new layer in the resulting image. Therefore squashing consecutiveRUNinstructions will reduce the layer count (see https://docs.docker.com/develop/dev-best-practices/). In addition to that, eachRUNinstruction runs in its own shell, which can be the source of confusion when part of aRUNinstruction changes something about the environment, because these changes may vanish in the nextRUNinstruction.12
-
The type of event logged by syslog.
-
The upstream source of the commercial Red Hat Enterprise Linux distribution.13
-
A command-line command that displays the advanced access control list (ACL) permission entries for a file or directory.
-
A number that is used by Linux to identify groups.
-
Also known as a virtual machine monitor or VMM, is software that creates and runs virtual machines (VMs). A hypervisor allows one host computer to support multiple guest VMs by virtually sharing its resources, such as memory and processing.14
- Type 1 Hypervisor
- Also known as bare-metal or native hypervisor. It runs directly on the host's hardware and controls the hardware; manages and monitors guest operating systems, which run on a separate level above the hypervisor.
- Type 2 Hypervisor
- Also known as hosted hypervisor. It runs as a software layer on an operating system (the host OS), like other computer programs. Guest operating systems run on a third level above the hardware (within host OS).
-
The Linux system assigns the access control list (ACL) permissions assigned to a directory to all files contained within the directory.
-
mount⚓ -
The
mountcommand allows users to mount, i.e., attach additional child filesystems to a particular mount point on the currently accessible filesystem.Learn more…
To temporarily mount a filesystem to the Linux virtual directory, use the
mountcommand; the basic format for themountcommand is:$ mount -t fstype device mountpointUse the
-tcommand-line option to specify the filesystem type of the device:$ sudo mount -t ext4 /dev/sdb1 /media/usb1If one specifies the
mountcommand with no parameters, it displays all devices currently mounted on the Linux system. Be prepared for a long output though, as most Linux distributions mount many virtual devices in the virtual directory to provide information about system resources. Listing 11.1 shows a partial output from amountcommand.
$ mount ... /dev/sda2 on / type ext4 (rw,relatime,errors=remount-ro,data=ordered) /dev/sda1 on /boot/efi type vfat (rw,relatime,fmask=0077,dmask=0077,codepage=437,iocharset=iso8859 -1,shortname=mixed,errors=remount-ro) ... /dev/sdb1 on /media/usb1 type ext4 (rw,relatime,data=ordered) /dev/sdb2 on /media/usb2 type ext4 (rw,relatime,data=ordered) rich@rich-TestBox2:~$
Listing 11.1 | Output from the
mountcommand.
To save space, the output from the
mountcommand was trimmed down to only show the physical devices on the system. The main hard drive device (/dev/sda) contains two partitions, and the USB memory stick device (/dev/sdb) also contains two partitions.
The
mountcommand uses the-ooption to specify additional features of the filesystem, such as mounting it in read-only mode, user permissions assigned to the mount point, and how data is stored on the device. These options are shown in the output of themountcommand. Usually, one may omit the-ooption to use the system defaults for the new mountpoint.The downside to the
mountcommand is that it only temporarily mounts the device in the virtual directory. On rebooting the system, one must still manually mount the devices again. This is usually fine for removable devices, such as USB memory sticks, but for more permanent devices, it would be nice if Linux automatically mounted them for us — fortunately for us — Linux can do just that.To remove a mounted drive from the virtual directory, use the
umountcommand (note the missing “n”). One may remove the mounted drive by specifying either i) the device filename or ii) the mountpoint directory.
-
The method of defining standard Unix file permissions of owner, group, and other using three octal numbers.
-
Runs multiple Linux distributions at the same time, assuming that hardware has enough resources.
-
RSyslog ⚓
-
Learn more…
The project claims the r stands for rocket fast. Speed is the focus of the rsyslog project and the rsyslog application had quickly become the standard logging package for many Linux distributions.
It offers high performance, great security features, and a modular design. While it started as a regular syslogd, rsyslog has evolved into a kind of Swiss army knife of logging, being able to:
- accept inputs from a wide variety of sources
- transform them
- output the results to diverse destinations
Rsyslog has a strong enterprise focus but also scales down to small systems. It supports, among others, MySQL, PostgreSQL, failover log destinations, ElasticSearch, syslog/tcp transport, fine grain output format control, high precision timestamps, queued operations, and the ability to filter on any message part.15
History of Rsyslog in Debian
Deprecation in Bookworm
“In Bookworm, since the persistent journal from Systemd's journald has been activated and most log messages would end up being written twice on disk, the rsyslog package has been demoted from the Important to the Optional priority, which means it is no longer installed by default in a base Debian system”
-
rsyslogd ⚓
-
The SysVinit method of logging events on a server and accepting log events from remote servers.
Learn more…
The
rsyslogddaemon also provides extended filtering, encryption-protected relaying of messages, input and output modules, and support for transportation using the TCP and UDP protocols.2See entry for
/etc/rsyslog.conf, which is the main configuration file forrsyslog.
-
Used in context-based permissions applications such as SELinux to define a user, role, and type assigned to a file or directory.
-
An application commonly used on Red Hat-based Linux distributions to implement context-based permissions.
-
A bit set on a directory that forces all files created in the directory to have the same group assigned as the directory and not that of the user who creates the file.
-
A bit set on a file that allows standard users the ability to run the file as the file owner.
-
A command-line command to set the access control list (ACL) permissions for a file or directory.
-
The importance of event logged by syslog.
-
A bit set on a file that prevents users from deleting the file unless they are the file owner, even if the user is a member of the group that has write permissions to the file.
-
A command-line command that allows users to run applications as another user account on the system.
-
A command-line command that allows users to run commands with root privileges.
-
A command-line command that opens the specified file in an editor using the root account privileges.
-
A de facto Unix and Linux protocol for storing event messages.
The syslog protocol has become the de facto standard for most Linux logging applications. It identifies events using a facility code, which defines the event type, and a severity, which defines how important the event message is. The
sysklogd,syslogd-ng, andrsyslogdapplications all use the syslog protocol for managing system and application events in Linux. -
The original Syslog application; includes two programs:
-
An application that is used to manage log messages and implement centralized logging where the aim is to collect log messages of several devices on a single and central log server. This program added advanced features, such as message filtering and the ability to send messages to remote hosts.
syslog-ngis available on a number of different Linux and Unix distributions. Some install it as the system default, or provide it as a package that replaces the previous standard syslogd. Several Linux distributions that usedsyslog-nghave replaced it withrsyslog.16 -
A system and session manager for Linux, compatible with System V and LSB init scripts.17 The main features are:
- provides aggressive parallelization capabilities
- uses socket and D-Bus activation for starting services
- offers on-demand starting of daemons
- keeps track of processes using Linux cgroups
- supports snapshotting and restoring of the system state
- maintains mount and automount points
- implements an elaborate transactional dependency-based service control logic
-
This is part of the Systemd application for system startup and initialization. Many Linux distributions are now using this for logging. It does not follow the syslog protocol, but uses a completely different way of reporting and storing system and application events.
-
-
An open-source operating system based on the Debian Linux distribution.
-
A particular form of access permitted to a file.18
-
The base standard POSIX file access control mechanism that uses file permission bits for the file permission model and is found on almost all Linux and Unix-like systems nowadays.
-
An operating system setup and configuration tool unique to openSUSE. It can be thought of as a command-center utility; allows the control of many system services from one interface.
Footnotes
-
https://refspecs.linuxfoundation.org/FHS_3.0/fhs/ch03s07.html ↩ ↩2 ↩3
-
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/8/html/configuring_basic_system_settings/assembly_configuring-a-remote-logging-solution_configuring-basic-system-settings#the-rsyslog-logging-service_assembly_configuring-a-remote-logging-solution ↩ ↩2 ↩3 ↩4
-
https://docs.docker.com/engine/reference/commandline/images/#description ↩
-
https://app.deepsource.com/directory/analyzers/docker/issues/DOK-W1001 ↩
-
https://docs.fedoraproject.org/en-US/quick-docs/fedora-and-red-hat-enterprise-linux/#relationship-between-fedora-and-red-hat-enterprise-linux ↩
-
https://www.vmware.com/topics/glossary/content/hypervisor.html ↩
-
https://documentation.suse.com/sles/12-SP5/html/SLES-all/cha-systemd.html#sec-boot-systemd-whatissystemd ↩
-
https://pubs.opengroup.org/onlinepubs/9699919799/basedefs/V1_chap03.html#tag_03_03 ↩