-
Notifications
You must be signed in to change notification settings - Fork 168
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Readme file - Update file verification section (to use keybase.io), clarify the download section, and other minor edits #285
Conversation
Clarifed shasum result about ignoring the warning about 4 improperly formatted lines
After a long hiatus, I have finally completed my proposed changes to the software verification section of our readme. The verification focuses on keybase.io now storing and verifying the 3 online properties (seedsigner.com, twitter.com/seedsigner and github.com/seedsigner) This makes the key more secure, easier to import and generally less hassle. its also revokable. There is more detail about how/why in the expand blocks, but It was suggested to me to keep the instructions straightforward (ie do this and now do that) , so I have reduced focus much on the why. However, some basic "why & how" has also been placed in new collapsible sections, at the end of each step. Later on, I want to add color to the collapse sections so that they show a natural boundary, but so far that markdown code is elusive to me. ;) Done is better than perfect.... The same for getting my external links to open in a new tab/window. sigh. Markdown is ... well....tricky. I can make the screenshots smaller. please comment on their size. The Verification is done in 3 steps: 1. import the public key 2. Verify its the correct key by verying it and then comparing the Key ID to Keybase.io/seedsigner. If it matches, then its the real seedsigner project person that signed. this is arguablly the most critical step of verifying and hence we ask the user to check for themselves that the key ID from verify is the same as on keybase.io. Hence the Key ID's are blurred in the screenshots. We dont want the user to compare the screenshots to each other. we want them to compare their result to their browser. 3. Verify that the other files (at this stage just the .zip file) are also not altered. This does a comparision of the various files actual and expected hashes. If all is well here, then tell the user about their success :). Explain the warnings, which ones are benign, and what to do if verification fails. Lastly, "Write the software to the MicroSD' section - I have got draft text for this, but havent published it yet. The verify PR is big enough !! Please review for my PR flow and clarity, I do still want to improve the formatting, but wanted to get everyone's thoughts before messing with the detailed formatting and line breaks, which are especially painful! FYI - I have done my screenshots using layers, so it easy to edit in the future. I think they
Readme file updates- Changes to the verification section (to use keybase.io), clarify the steps thereof, and various other minor edits.
|
Good stuff, this content should be covered in primary school. |
|
I've gone through the steps and its all working fine, and the level of detail exhaustively explains the process and reasoning to users, which is all good. The challenge I think now is that from a volume perspective these verification steps have come to dominate the readme to the point that I think this verification process might be better placed within a secondary markdown document within the repo. Curious to hear what @newtonick thinks. The amount of work that has gone into this is apparent and I really appreciate it. |
|
Seed, thanks so much for your kind words! Yes, it certainly was a deep dive that I found fascinating, and it results in a large section, so I share that concern. When I showed it to Keith in LA recently , he also wanted to keep it shortened to "do this, see this result". However, iirc, we both noted that there are some users that are more interested in the why, or wanted more documentation to help them. So we discussed a supporting doc published elsewhere. I will probably try my hand at a full length article in BTC magazine etc, and then we could link to that. But that's a few months out still. Shortening it: Although the collapsible sections do work kind of ok, having color will help , but the formatting in markdown is limited. I can try see if I can get color to work in the collapsible sections. I hadn't thought of putting a large part of it into a separate (linked) repo document until you mentioned it. Comparing to sparrow: they put the verify instructions on their website html, and control the apparent length using its better formatting. Html helps! One other option that comes to mind now is: (to corrupt keybases own verification, a hacker would have to hack all 3 properties (github, Twitter (extremely visible to us)/) and website). So a shorter verify section in the readme itself if that can still be followable, link to the full length on the SS website, and confirm the keybase address on the readme also. Some middle ground is somewhere... Is the website vision for it to move to the front more maybe, instead of always sending users to GitHub? Git is familiar if you know it, but otherwise pretty scary. Idk. Thanks for going through such a lengthy PR! It became a fascinating subject to me, in an act of madness 😉 M. |
|
I think it would be best to keep the verification steps within the repo. What makes the most sense I think is having the abbreviated version in the main readme, and then link to the more exhaustive explanation also within the repo. |
README.md
Outdated
| ``` | ||
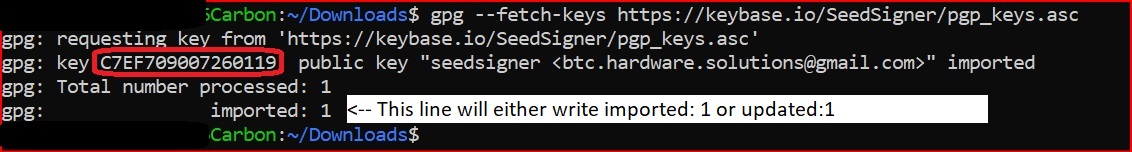
| When the command completes successfully, it will show that this key was either imported or updated from Keybase.io. A numeric ID, as circled in red in the example below is known as the keys fingerprint. Please ignore the email address shown, because it is not part of any verification. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
"...is known as the key's fingerprint..." (possessive "s")
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Fixed. thx.
README.md
Outdated
|  | ||
|
|
||
| <details><summary>Learn more about how keybase.io helps you check that someone is who they say they are</summary> | ||
| <p> |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
If color coding fails, you could italicize the collapsed text. Not ideal, but at least visually sets it off from the main body.
README.md
Outdated
| <p> | ||
| The Keybase.io website allows you to independently verify that the public key provided is authentic and that it belongs to the organization it claims to represent. | ||
| Keybase has checked the pubkey cryptographically when it was saved in the 3 separate online locations. These are: on www.twitter.com/seedsigner, on the website www.seedsigner.com , and in the software repository at Github www.github.com/seedsigner. | ||
| You can verify those 3 separate Key locations yourself, by clicking the 3 blue badges on www.keybase.io/seedsigner. (The Twittter blue badge one is the most human-readble.) |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
"...by clicking on the links provided here or by clicking the three blue badges on..."?
My only minor concern is that Keybase potentially becomes a single point of failure; if we're absurdly paranoid, we should emphasize where we can cut Keybase out of the loop entirely.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
<>
Good point. I have revised it into 2 separate methods. via keybase verification, or directly to the files.
Line 121 is also changed to describe how to be independent of Keybase.
Reliance on Keybase: Yes, we can always remove keybase.io , and replace it with an ventual successor. (keyoxide.org is one such project being built out now, but is not yet live.)
So Keybase's purpose now, is mostly to host the pubkey, allow users to verify that this published pubkey matches the 3 other PubKey locations, and that they are still genuine, also not revoked.
(To a lesser extent, to verify that the signing keys on Seedsigners (2) devices are still the same.).
Yes, I will add language that Keybase can be removed/substituted, if it is compromised or creases to function.
README.md
Outdated
| <details><summary>Learn more about how keybase.io helps you check that someone is who they say they are</summary> | ||
| <p> | ||
| The Keybase.io website allows you to independently verify that the public key provided is authentic and that it belongs to the organization it claims to represent. | ||
| Keybase has checked the pubkey cryptographically when it was saved in the 3 separate online locations. These are: on www.twitter.com/seedsigner, on the website www.seedsigner.com , and in the software repository at Github www.github.com/seedsigner. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
(see comment below)
Again, I'd reframe this as: You can independently verify the public key at these three links.
No need to trust Keybase's verification/aggregation. We can verify ourselves straight from each source.
Keybase is a convenience, but we could write a version of these docs that make no mention whatsoever of Keybase, right?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This section has now been re-stated to describe both options: verifying via Keybase, and also verifying out-of-band without keybase at all. Mention is made to use the out-of-band method if keybase is not available or it no longer exists.
Update to incorporate Keiths suggestions about not relying on keybase and also offering an option to link directly to the published pubkey files. Fix apostrophes'
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@Marc-Gee, I'd started to review this back in December then never clicked "Finish your review". I see that you've made some corrections since then. Are you considering to break some of the key-base details into their own readme while leaving only brief summary in this one, as SeedSigner suggested?
If you'd benefit from a tight feedback loop and fresh eyes, I'd be happy to proof read any changes you have and get back to you quickly (and verify that you've got my feedback this time) to get these into 0.5.2.
README.md
Outdated
|
|
||
| After downloading the .zip file, extract the seedsigner .img file, and write it to a MicroSD card (at least 4GB in size or larger). Then install the MicroSD in the assembled hardware and off you go. | ||
| Once the files have all finished downloading, follow the steps below to verify, and to write the software onto a MicroSD card. Then insert the MicroSD into your assembled hardware and turn on the USB power. Allow about 45 seconds for our logo to appear, and then you can begin using your Seedsigner! |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
"to verify, and to write" becomes "to verify the download before continuing on to write" (or "install", or "burn", or "flash", I like "write")
" Then insert the MicroSD" becomes " Next, insert the MicroSD card"
"turn on" becomes "connect"
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Fixed in [a136a86]
README.md
Outdated
| > gpg: WARNING: This key is not certified with a trusted signature! | ||
| > gpg: There is no indication that the signature belongs to the owner. | ||
|
|
||
| **If** you received the phase **"good Signature"**, then the last output line will display a 16 character fingerprint ID. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
"phase" becomes "phrase"
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Fixed in [a136a86]
| @@ -77,60 +77,139 @@ Notes: | |||
|
|
|||
| # Software Installation | |||
|
|
|||
| ## Special Note on Minimizing Trust | |||
| ## A Special Note On Minimizing Trust | |||
| As is the nature of pre-packaged software downloads, downloading and using the prepared SeedSigner release images means implicitly placing trust in the individual preparing those images; in our project the release images are prepared and signed by the eponymous creator of the project, SeedSigner "the person". That individual is additionally the only person in possession of the PGP keys that are used to sign the release images. | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
"eponymous" becomes "anonymous"
" That individual is additionally" becomes " That individual is also" or " Additionally, that individual is"
Is it 'SeedSigner "the person"', or is it 'SeedSigner "the man"' ???
(nicer masking in the image)
|
Appreciate these tweaks. We will also likely have to revisit this with the next release as with SeedSigner OS there will be several different binaries for some of the different Raspberry Pi hardware profiles. |
README.md
Outdated
|
|
||
| <br> | ||
|
|
||
| ### 2. Verifying that the *software images/binaries* are genuine |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
The last level3 header was "Step 1.", so here maybe "Step 2." instead of "2."
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Fixed in [a136a86]
Spelling, grammar edits were made, - as suggested by the reviewers comments. Additionally: 1) the Windows certutil (aka shasum) command for windows was clarified. 2) the shasum command on osX and Linux now includes the ignore-missing flag for compatibility with the expected new 0.5.2 shasum file format. The 0.5.2 shasum file will include hashes for multiple binaries now , but the user will likely only be checking one single binary. hence we tell shasum command to skip any missing files and to not report "missing files" error.
|
Thanks all, for your review comments thus far. (I didnt realise yesterday that my own commits get sync'd upstream automatically (somehow...um, thx Git!) A Summary of Sunday and Mondays changes: @SeedSigner - regarding the multiple binaries in 0.5..2, i have added the ignore-missing flag in shasum command to deal with that , but we will need to update the download files section. (Let me know what you expect the file list to be and i can work on new wording for that section. That should then be all thats required for extra download files. (I did always anticipate more binaries than just the one.) 👍 |
|
I walked through the updated "Software Installation" section of the README. LGTM on the PGP/Keybase changes. The "Writing the software to your MicroSD card" section remains incomplete with a comment to insert more instructions. |
README.md
Outdated
| ``` | ||
| Good signature from "seedsigner <btc.hardware.solutions@gmail.com>" [unknown] | ||
| shasum -a 256 --ignore-missing -check seedsigner_0_*_*.img.zip.sha256 |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I missed this on my first pass, -check needs to be be --check
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thx Nick, great catch! The "--check" is fixed now. I will work on the Writing to MicroSD section today.
I will keep it short, and just emphasize doing the "verify image" step to avoid those occasional errors users pick up when the device wont boot/nothing displays onscreen.
1st draft of MicroSD. Thus far I am holding back on elaborating on the DD usage, until the commands are tested some more. I have/can insert screenshots of the Pi Imager/Etcher basic actions, but I am concerned its getting too long.
|
Instructions for writing the MicroSD card are now included for review. |
Cleaned up some MicroSd verify wording since the Pi Etcher and Balena software now do a write-verify by default. 👍 Fixed spelling mistakes. Moved the advanced user suggestion of using DD, further up, away from the Windows specific instructions.
Included a table of the various now-platform specific binaries available. This table includes direct links (for the first time ) to the actual download files Prior version downloads are available via a link to the github repo releases page
|
Table format and direct links to binaries was included for consideration. please let me know if you prefer not to have direct links. If the table layout for the various binaries is liked and accepted, I could make the total table height shorter, by putting the (larger Pi's 3 and 4) in a columnon the right. |
README.md
Outdated
| | Pi Zero v1.3 or Pi Zero (W or WH) | [SeedSigner for R-Pi Zero V1.3](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/SeedSigner_OS.0.6.0.pi0.img) | | ||
| | Pi Zero **2** W | [SeedSigner for R-Pi Zero 2 W](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/SeedSigner_OS.0.6.0.pi02w.img) | | ||
| | Pi 2 (not a Pi *Zero* 2) | [SeedSigner for R-Pi 2](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/SeedSigner_OS.0.6.0.pi2.img) | | ||
| | Pi 3 | [SeedSigner for R-Pi 3](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/SeedSigner_OS.0.6.0.pi02w.img) | |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Im not sure that a binary for pi3 is planned. I've since learned via DT that pi02 and pi3 are same architecture.
README.md
Outdated
| | Pi Zero **2** W | [SeedSigner for R-Pi Zero 2 W](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/SeedSigner_OS.0.6.0.pi02w.img) | | ||
| | Pi 2 (not a Pi *Zero* 2) | [SeedSigner for R-Pi 2](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/SeedSigner_OS.0.6.0.pi2.img) | | ||
| | Pi 3 | [SeedSigner for R-Pi 3](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/SeedSigner_OS.0.6.0.pi02w.img) | | ||
| | Pi 4 | [SeedSigner for R-Pi 4](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/SeedSigner_OS.0.6.0.pi04.img) | |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I believe this file will end in ".pi4.img", and I'm not at all certain about caps at all in the file's basename.
Changed the table format to 2 columns. linked were verified as working and to the correct/specific binaries. Added language to notify [existing] users that their downloads will be much faster than expected. (100x small file size!) Small edits to the language and links which point to our prior software versions.
changes resulting from testing the scripts with the new 0.6.0 filename (new naming format and also now hardware specific): the binary file is no longer (inside) a zip file The base image filename format is now different. it was seedsigner_x_x_x but is now seedsigner_os.x.x.x , 2 Screenshots were updated for filename convention changes. and less blurred. Fixed 0.6.0 references versus 0.6.x references for maximum forward compatibility. Included references to the older versions zip file where appropriate. (As this same readme file will be visible for 0.5.0 and also 0.6.x versions) Removed reference to shasum warnings in the signature file as it is now correctly formatted. "shasum: WARNING: 4 Lines are improperly formatted"
README.md
Outdated
|
|
||
| **also download** these 2 signature verification files to the same folder | ||
| [The Plaintext Manifest File](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/seedsigner.0.6.0.sha256) | ||
| [The Signed Manifest File](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/seedsigner.0.6.0.sha256.sig) |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
"The Signed Manifest File" becomes "The Signature of the manifest file"
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Done.
README.md
Outdated
| [The Plaintext Manifest File](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/seedsigner.0.6.0.sha256) | ||
| [The Signed Manifest File](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/seedsigner.0.6.0.sha256.sig) | ||
|
|
||
| Users of our software prior to version 0.6.0 might be surprised how fast their downloads are, but since the our migration to SeedSignerOS the software files are in fact, 100x smaller and hence your downloads and verifications will be very quick now! (approx 40 Megabyte images) |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
"..., but since the our migration..." becomes "..., but since our migration..."
README.md
Outdated
| |--- |--- |--- | | ||
| | [SeedSigner software for the Pi Zero **2** W (The "Pi Zero **TWO** W")](https://github.com/seedsigner/seedsigner/releases/download/0.6.0/seedsigner_os.0.6.0.pi02w.img) | | [SeedSigner software for the Raspberry Pi 4 Model B](https://github.com/seedsigner/seedsigner/releases/download/0.6.0/seedsigner_os.0.6.0.pi4.img) | | ||
| | [SeedSigner software for the Pi Zero W or Pi Zero WH](https://github.com/seedsigner/seedsigner/releases/download/0.6.0/seedsigner_os.0.6.0.pi0.img) | | [SeedSigner software for the Raspberry Pi 3 Model B](https://github.com/seedsigner/seedsigner/releases/download/0.6.0/seedsigner_os.0.6.0.pi02w.img) | | ||
| | [SeedSigner software for the Pi Zero **V1.3**](https://github.com/seedsigner/seedsigner/releases/download/0.6.0/seedsigner_os.0.6.0.pi0.img) | | [SeedSigner software for the Raspberry Pi 2 Model B ](https://github.com/SeedSigner/seedsigner/releases/download/0.6.0/SeedSigner_OS.0.6.0.pi2.img) <br> This is not the file for a Pi **ZERO** 2. <br>That hardware is a different chipset and motherboard. | |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
In the basename of the url for RPi2 download...
"SeedSigner_OS.0.6.0.pi2.img" works but might be more case-specifically-correct as "seedsigner_os.0.6.0.pi2.img"
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
thx. corrected to lowercase. I also made a few other case corrections via a search and replace, so now:
all URL's are lowercase.
link descriptions are TitleCase: "SeedSinger".
The project name is TitleCase: SeedSinger (but not in any urls).
YouTube URL's do use capitalization (reasons vary but for link shortening afaik) so those have been left as-is.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Suggested changes are now made.
all URL's are lowercase. link descriptions are TitleCase: "SeedSinger". The project name is TitleCase: SeedSinger (but not in any urls). YouTube URL's do use capitalization (reasons vary but for link shortening afaik) so those have been left as-is.
Clarification for wifi chip removal: to still use the image file of the original(un-modified) hardware.
|
For the case of the first folder of a github url, I preferred "https://github.com/SeedSigner/..." even if there is some url-rewrite magic happening that makes it case-insensitive -- we land on the more correct url which uses "SeedSigner". In the case of files, there is more rewrite magic happening but still, we end up downloading files just as SeedSigner-the-man put them there... all in lowercase. |
Revert and correct some changes made in yesterday's commit of the url case. These now match the lowercase/titlecase of the various sites more accurately to what they use. The display URL's are/were not affected, hence users will still see the Title Case of SeedSigner.
Position-swap of pi0.img (Pi zero 1.3) and pi02w.img (Pi Zero TWO) in "Downloading the software" table. The Pi zero V1.3 hardware is the most prevalent Zero hardware currently, so it is now moved into the Top Left position. Added tooltips to all 6 image file download links, to display the hardware/filename its linked to. ie "Download the ...pi02w.img file"
|
LGTM |
This is a new PR, continuing on from a prior PR [209 ] #209 opened by @mauricio.
That prior PR (209) was sub-forked by me, but it eventually became too difficult to co-ordinate for the 2 fork maintainers, so today Mauricio and I agreed that its now best to have me (MarcG) make a new PR and submit directly into SS.
I would like to thank and acknowledge @mauricio for his work in getting the prior PR started, and helping me through my proposed changes!
So continuing from PR 209:
After a long hiatus, I have finally completed my proposed changes to the software verification section of our readme!
The new verification section focuses on using the project's Pubkey stored at keybase.io , and thus uses keybase's own methods verifying that Pubkey, and that it matches in 3 separate project properties (seedsigner.com, twitter.com/seedsigner and github.com/seedsigner). Ie the publisher was able to upload to 3 separate online properties, and those are were not rejected.
Using Keybase:
and most importantly, improves how users will verify that the software they have downloaded is both authentic (signed by the correct people) and also unchanged.
Its also revokable in case its compromised.
This PR:
Clarifies the software download steps from github, and then changes how the current readme instructs users to check for authentic signatures. ie the email address is meaningless.
There is more detail about how/why in the new expand blocks, as It was suggested to me to keep the instructions straightforward (ie do this and now do that) , so I now have reduced the focus about why, and rather put that into the new expand blocks.
("why & how's" have been placed into the new collapsible sections, and moved to the end of each step.)
Note: I also adjusted the download section to align with the new verification steps.
Subsequently, I want to add color to the collapse sections so that they show a natural boundary, but so far that markdown code is elusive to me. ;)
Done is better than perfect....
The same for getting my external links to open in a new tab/window. sigh. Markdown is ... well....tricky.
I can make the screenshots smaller. please comment on their size.
How verification of software should be done:
(Note: Sparrow wallets explanation is more accurate then what we have in the current readme, but its also not perfect. Coldcard's firmware verification section doesn't actually verify it. They do the steps, but dont actually verify it)
Having studied this over many hours, this is how (and why) it is supposed to be done, in 3 steps:
Import the public key directly from the url https://keybase.io/seedsigner
Run the GPG verify command on the downloaded signature (.sig) file to see who made the signature.
This produces the 16 char pubkey of the signature file when "crossed" with your imported key from step 1.
Compare the outputted Key ID to Keybase.io/seedsigner.
If the 2 fingerprints match, then its the real seedsigner project/person that made the signature file!
This visual comparison is arguably the most critical step of verifying and hence we ask the user to check for themselves
that the key ID from their output matches exactly to keybase.io/seedsigner. The Key ID's are thus deliberately blurred in our
example screenshots, because we don't want the user to accidently compare 2 screenshots to each other. Rather, we want
them to compare their result to their browser. If this succeeds, then you have a untampered .sha256 text file, that was also signed by the correct person!
Shasum: Verify that the other files (at this stage just the .zip file) have not been not altered/appended from when they were signed (by that correct person). This does a comparison of the various files actual hashes and expected hashes, using the signature file (.sha256). This .sha256 file was confirmed as genuine, and also unaltered, in the prior step.
If the shasum succeeds, then tell the user about their verification success :).
Explain the warnings, which ones are benign, and what to do if verification fails.
Lastly, "Write the software to the MicroSD' section -
I have got draft text for this, but havent published it yet, i think this verify PR is big enough !!
Please review for my PR flow and clarity, I do still want to improve the formatting, but wanted to get everyone's thoughts before messing with the detailed formatting and line breaks, which are especially painful!
FYI - I have done my screenshots using layers, so it easy to edit in the future. Can make them smaller too.
Please note, the readme is an almost-final draft now, but it needs formatting fixes still before any decision to make it live.
Thanks all !
Marc.