-
Notifications
You must be signed in to change notification settings - Fork 77
Security Taint Vulnerabilities Investigation
The content on this page has moved: https://docs.sonarsource.com/sonarlint/visual-studio/using-sonarlint/taint-vulnerabilities/
The SonarLint documentation has moved! Please visit https://docs.sonarsource.com/sonarlint/visual-studio/ to have a look at the new documentation website. We’ve improved the documentation as a whole, integrated the four SonarLint IDE extension docs together, and moved everything under the sonarsource.com domain to share a home with the SonarQube docs (SonarCloud to come in Q3 of 2023).
These GitHub wikis will no longer be updated after October 1st, 2023 but no worries, we’ll keep them around a while for those running previous versions of SonarLint for Visual Studio.
SonarLint now provides a way to investigate Taint Vulnerabilities found on SonarCloud or your SonarQube server.
- SonarLint version 4.31 or higher.
- The correct solution must be open in Visual Studio and it must be in Connected Mode to SonarCloud or SonarQube version 8.6 or higher.
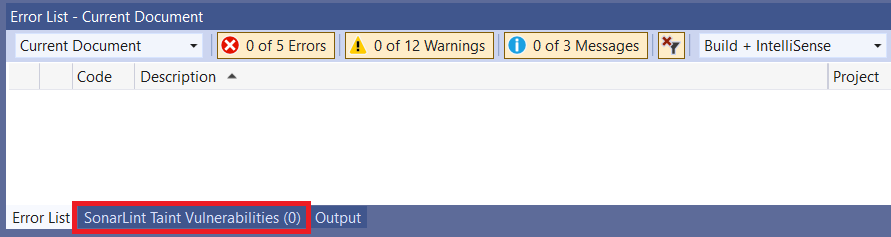
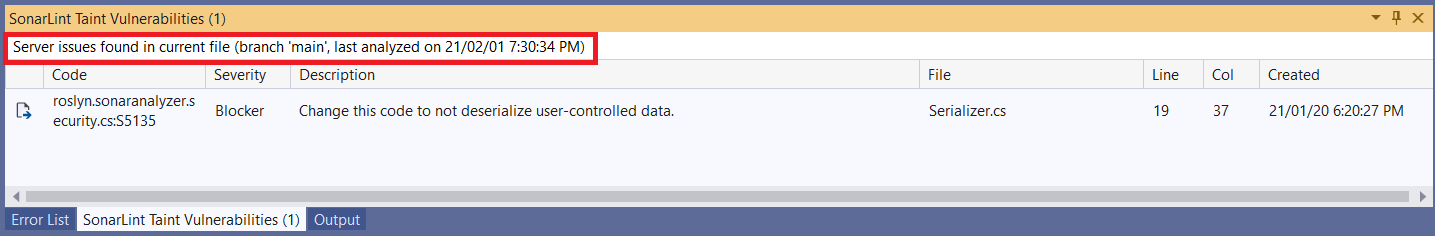
When a solution connected to SonarCloud or SonarQube is open in Visual Studio, SonarLint will fetch the vulnerabilities from the configured server. If any vulnerabilities exist, a new tool window will be displayed in a new tab next to the Error List:
The tool window will appear automatically if your server has any taint vulnerabilities in your project. If you are not in Connected Mode, or if your server has no taint vulnerabilities, the window will not appear.
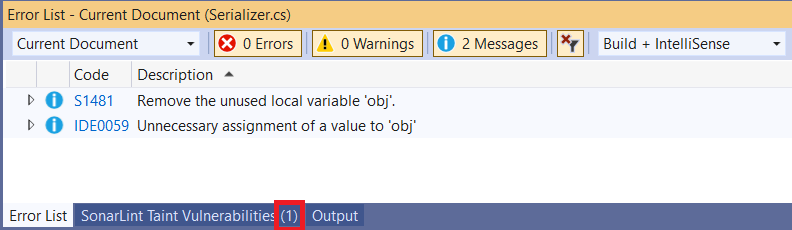
The taint list is filtered to display remote vulnerabilities found in the currently open code file. When a file containing issues is opened, the caption of the tool window will update to reflect the number of remote vulnerabilities found in the file:
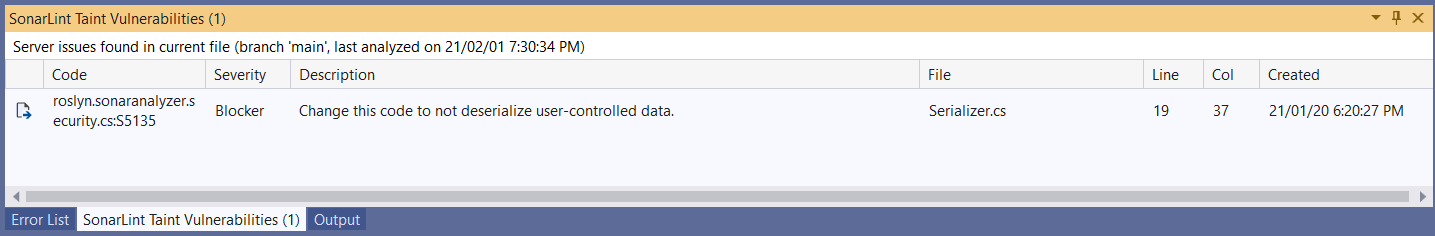
The header of the list will display information about the analysis in which these issues were found:
Note: Currently SonarLint does not detect Taint Vulnerabilities during live analysis in the IDE. The issues appearing in the Taint Vulnerabilities list are the issues reported on your SonarQube or SonarCloud server.
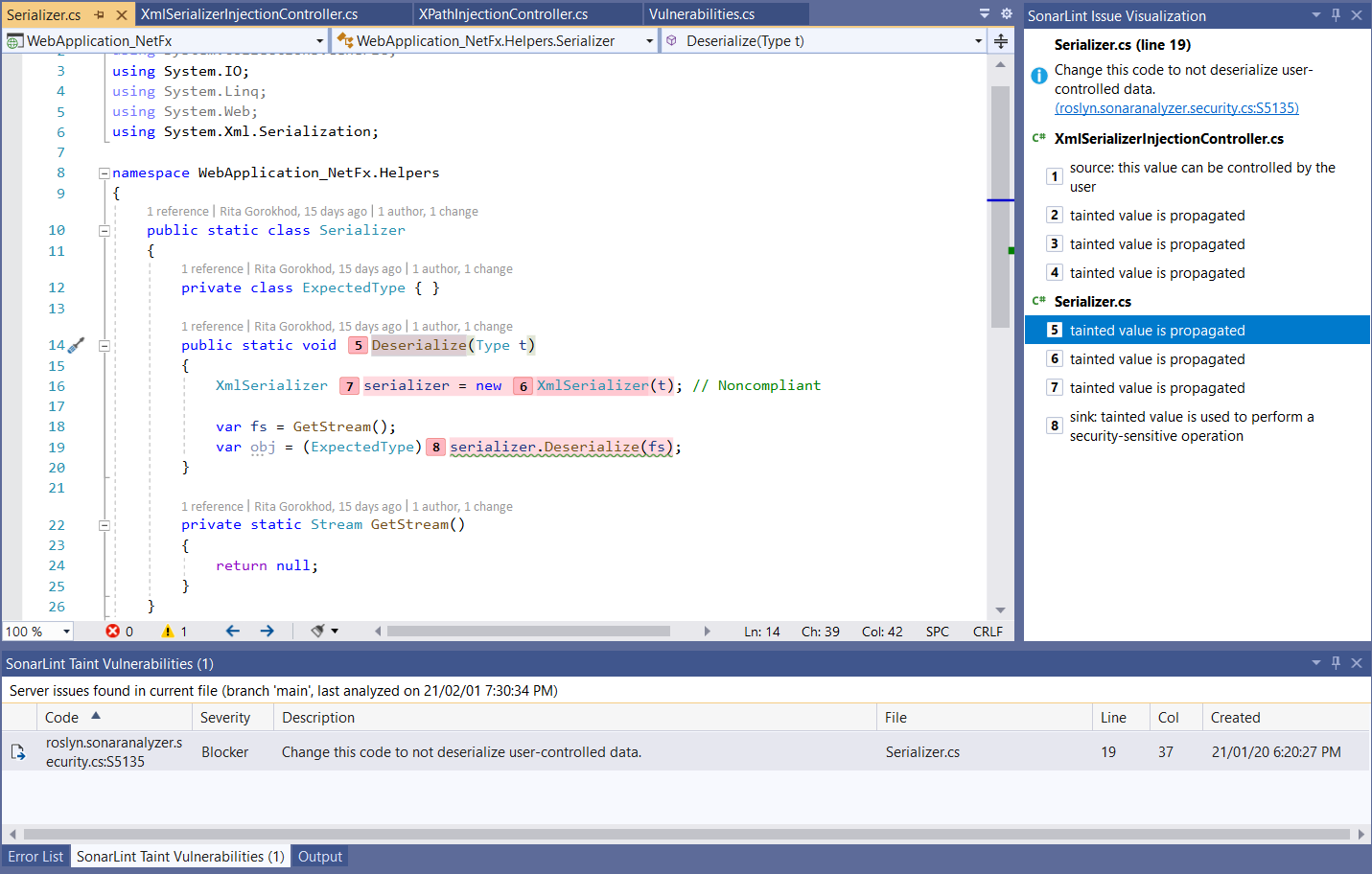
You can investigate a vulnerability by using a double-click or the Enter key. This will take you to the relevant code location and open the SonarLint Issue Visualization panel with visualization of your code flow.
Note: if you do not see the Issue Visualization panel, click on Extensions → SonarLint → Show Issue Visualization. See SonarLint Issue Visualization for more information.
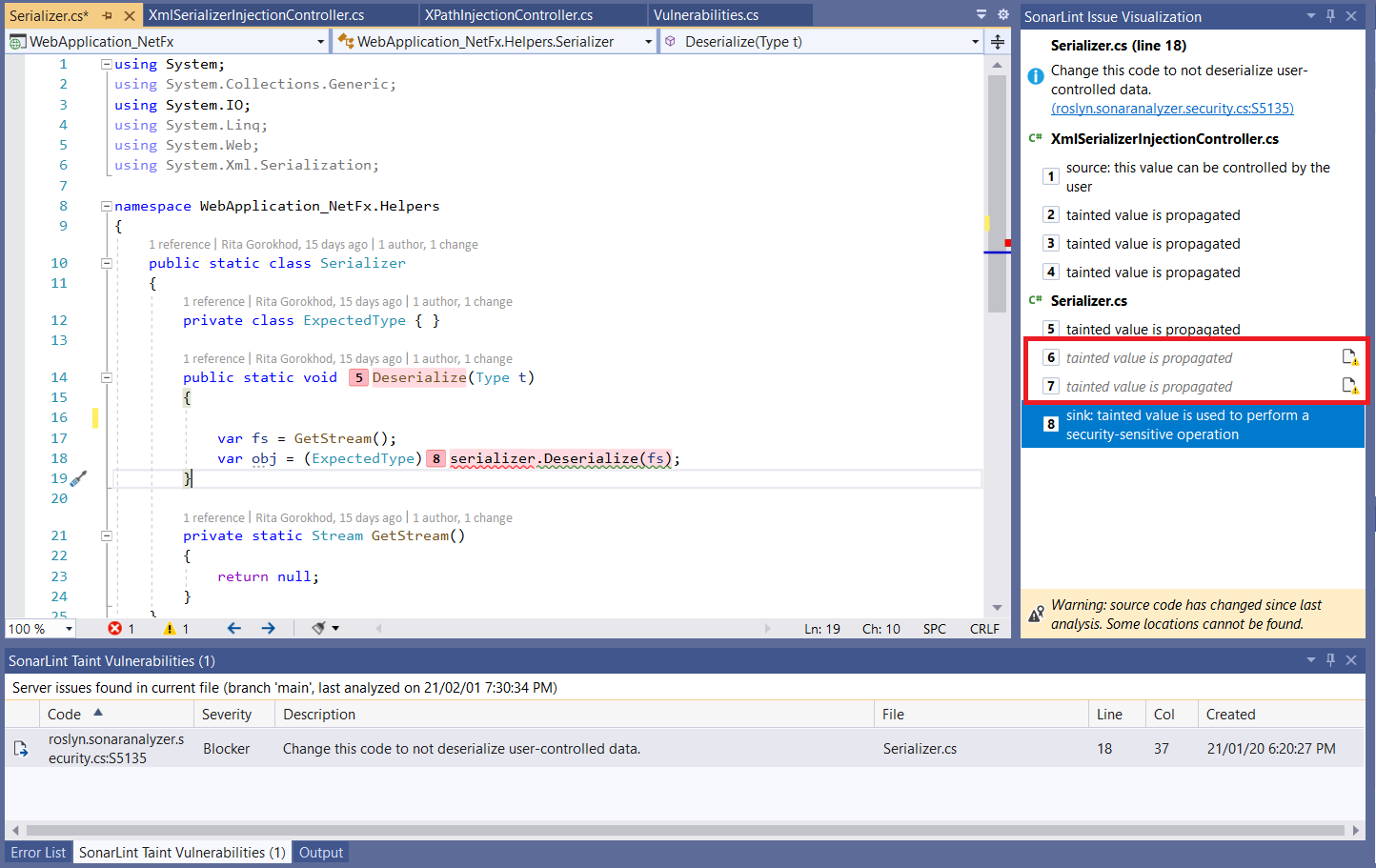
Since taint vulnerabilities are fetched from your configured server, it is possible that the code on your server does not match your local code version, e.g. if code changes have been made since the last analysis. In this case, non-navigable locations will be displayed with an indication that they are not navigable:
If you manually close the tool window, it will no longer appear and disappear automatically when a solution is opened. You can show the window again by clicking on Extensions → SonarLint → Connected Mode → View Taint Vulnerabilities: