-
Notifications
You must be signed in to change notification settings - Fork 851
Optimize: rewrite getbyname_imm and getSRVbyname_imm as wrappers for getby #4961
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
8e9cc11 to
bb23a5d
Compare
 scw00
left a comment
scw00
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM ..
iocore/hostdb/HostDB.cc
Outdated
| if (opt.flags & HOSTDB_FORCE_DNS_ALWAYS) { | ||
| force_dns = true; | ||
| } else if (opt.flags & HOSTDB_FORCE_DNS_RELOAD) { | ||
| force_dns = (hostdb_re_dns_on_reload ? true : false); |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
A couple of alternatives.
force_dns = host_db_re_dns_on_reload;
or
if (hostdb_re_dns_on_reload) {
force_dns = true;
HOST_DB_INCREMENT_DYN_STAT(..);
}
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
updated
|
|
||
| if (!lock2.is_locked() && !trylock) { | ||
| // Refer to: [TS-374](http://issues.apache.org/jira/browse/TS-374) | ||
| lock2.acquire(thread); |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This could be a deadlock concern, if the thread blocks on acquiring a lock.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I just rewrote SCOPED_MUTEX_LOCK(lock, bucket_mutex, thread);.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Please check the TS-374 commit via ba3b7d0.
It solves a performance issue of reverse proxy.
|
Overall I like the cleanup, but I'm quite concerned about the blocking lock. I don't see why cannot be bound in to the |
|
IMO, the |
|
Clearly, which is the reason to do a try lock. But if that fails, hard locking and creating blockage from lock contention is the slow path. |
|
@SolidWallOfCode The |
|
[approve ci autest] |
|
@SolidWallOfCode @vmamidi |
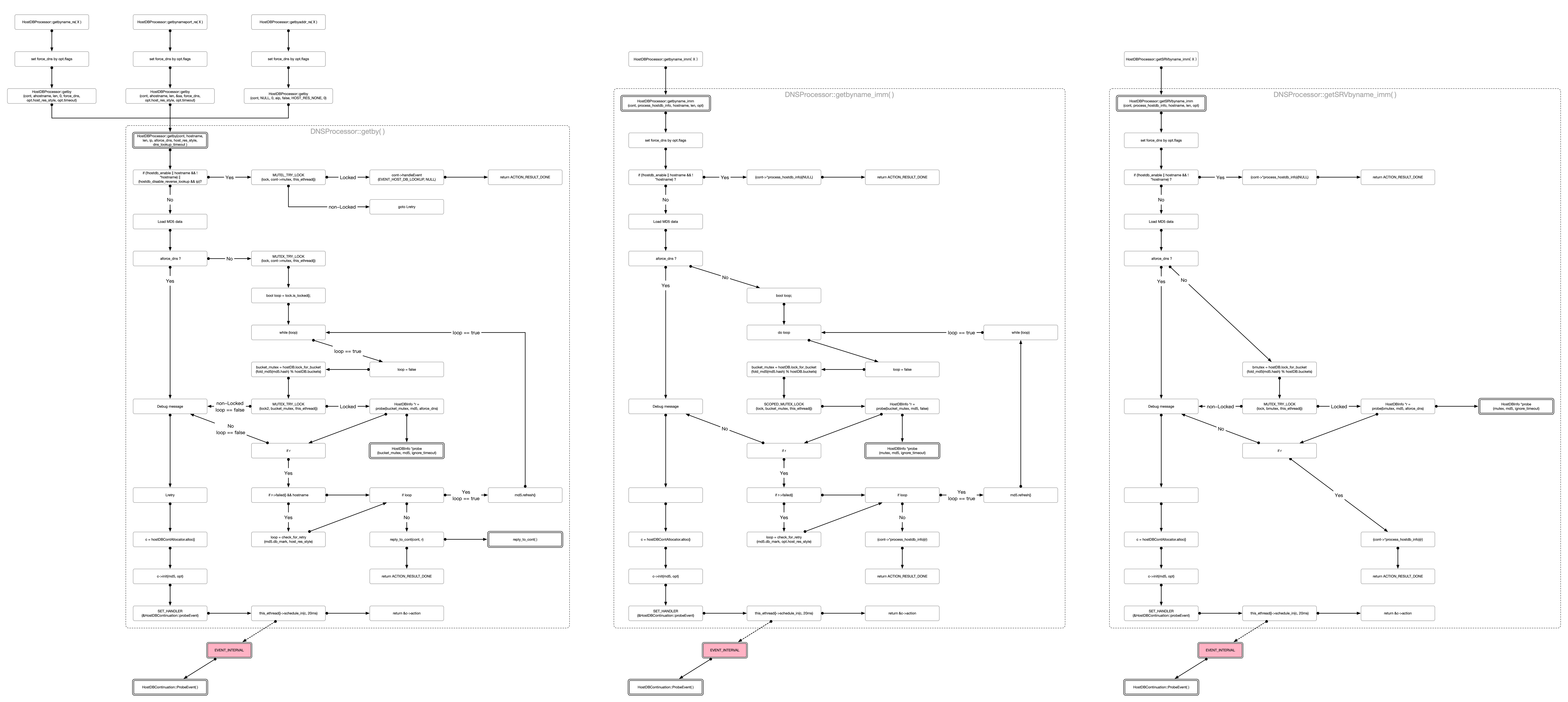
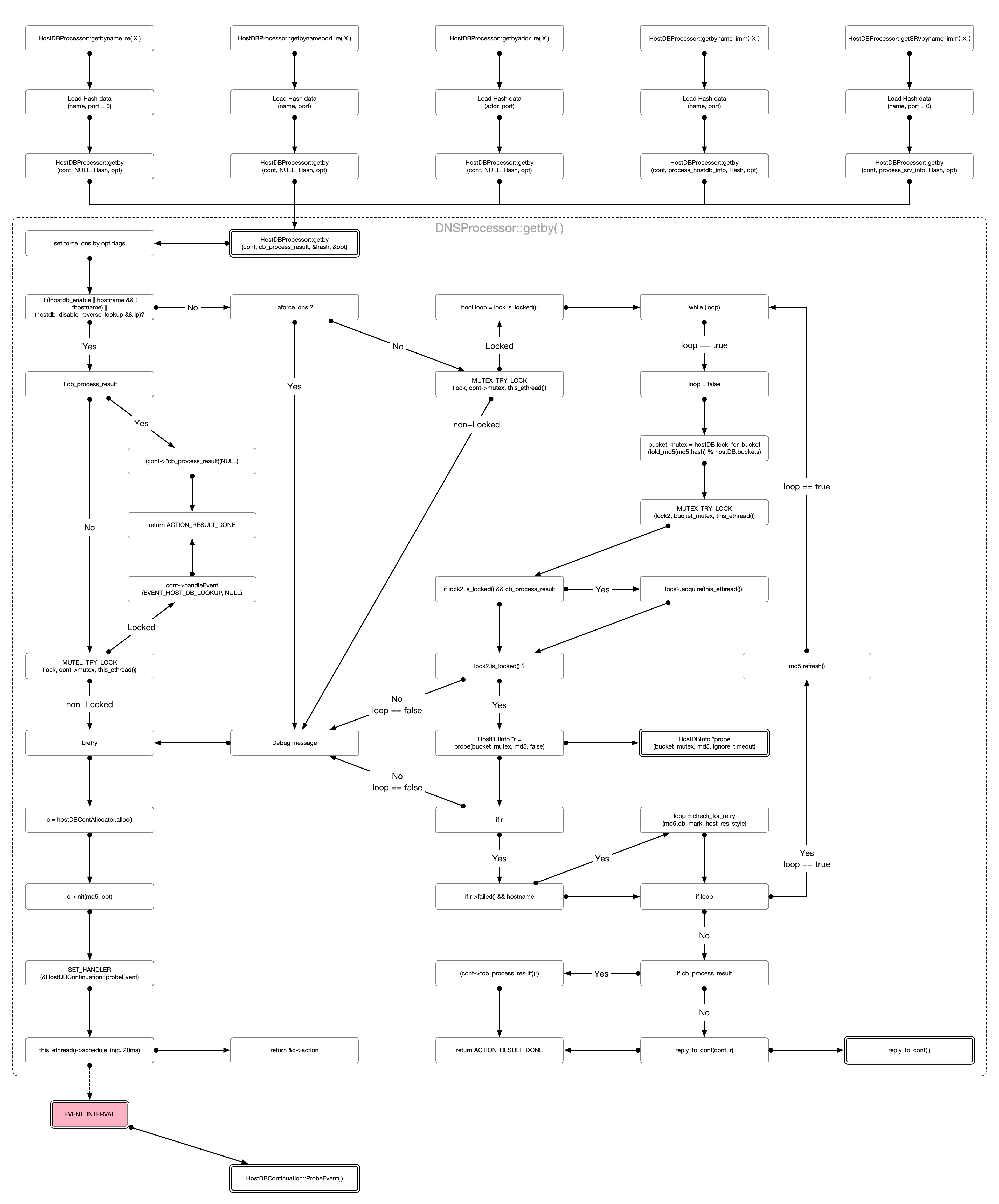
No description provided.