-
Notifications
You must be signed in to change notification settings - Fork 4k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
chore(release): 2.10.0 #18733
Merged
Merged
chore(release): 2.10.0 #18733
Conversation
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
I’m trying to use the new format=esm bundling with NodejsFunction I noticed that it bundles the “CJS” version of dependencies not the ESM version (if available). esbuild has some wack defaults - https://esbuild.github.io/api/#main-fields This causes problems because the CJS versions usually have stuff like require() and they don’t work for tree-shaking. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
Fixes: #18443 *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
Depends on #18577 ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
…mplete (#18536) There are [upcoming changes](https://aws.amazon.com/blogs/compute/coming-soon-expansion-of-aws-lambda-states-to-all-functions/) that will rollout Lambda states to all Lambda Functions. Prior to this update (current functionality) when you made an `updateFunctionCode` request the function was immediately available for both invocation and future updates. Once this change is rolled out this will no longer be the case. With Lambda states, when you make an update to a Lambda Function, it will not be available for future updates until the `LastUpdateStatus` returns `Successful`. This PR introduces a custom waiter that will wait for the update to complete before proceeding. The waiter will wait until the `State=Active` and the `LastUpdateStatus=Successful`. The `State` controls whether or not the function can be invoked, and the `LastUpdateStatus` controls whether the function can be updated. Based on this, I am not considering a deployment complete until both are successful. To see a more in depth analysis of the different values see #18386. In my testing I found that the time it took for a function to go from `LastUpdateStatus=InProgress` to `LastUpdateStatus=Successful` was: - ~1 second for a zip Function not in a VPC - ~25 seconds for a container Function or a Function in a VPC - ~2 minutes to deploy a VPC function (best proxy for StateReasonCode=Restoring) There are a couple of built in waiters that could have been used for this, namely [functionUpdated](https://docs.aws.amazon.com/AWSJavaScriptSDK/latest/AWS/Lambda.html#functionUpdated-waiter). This waiter uses `getFunctionConfiguration` which has a quota of 15 requests/second. In addition the waiter polls every 5 seconds and this cannot be configured. Because hotswapping is sensitive to any latency that is introduced, I created a custom waiter that uses `getFunction`. `getFunction` has a quota of 100 requests/second and the custom waiter can be configured to poll every 1 second or every 5 seconds depending on what type of function is being updated. fixes #18386 ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
Closes #18508. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
The logs monitor test was using `Date.now()` which sometimes caused the actual result to differ from the expected result. Turns out the reason I needed the dynamic date is because I was generating the timestamp incorrectly. Fixed that which allowed me to use a hardcoded timestamp. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
fixes #18575 Models documentation for [similar](https://docs.aws.amazon.com/cdk/api/v1/docs/@aws-cdk_aws-ec2.VpcAttributes.html) [structs](https://docs.aws.amazon.com/cdk/api/v1/docs/@aws-cdk_aws-lambda.FunctionAttributes.html) ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
…odePipeline (#18530) This adds support for importing a ECS Cluster via the Arn, and not requiring the VPC or Security Groups. This will generate an ICluster which can be used in `Ec2Service.fromEc2ServiceAttributes()` and `FargateService.fromFargateServiceAttributes()` to get an `IBaseService` which can be used in the `EcsDeployAction` to allow for cross account/region deployments in CodePipelines. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
This PR is proposed by #17711. The first step of the roadmap in #17711 is implemented in this PR. > 1. implement DetectorModel and State with only required properties > - It will not be able to have multiple states yet. If this PR is merged, the simplest detector model can be created as following: 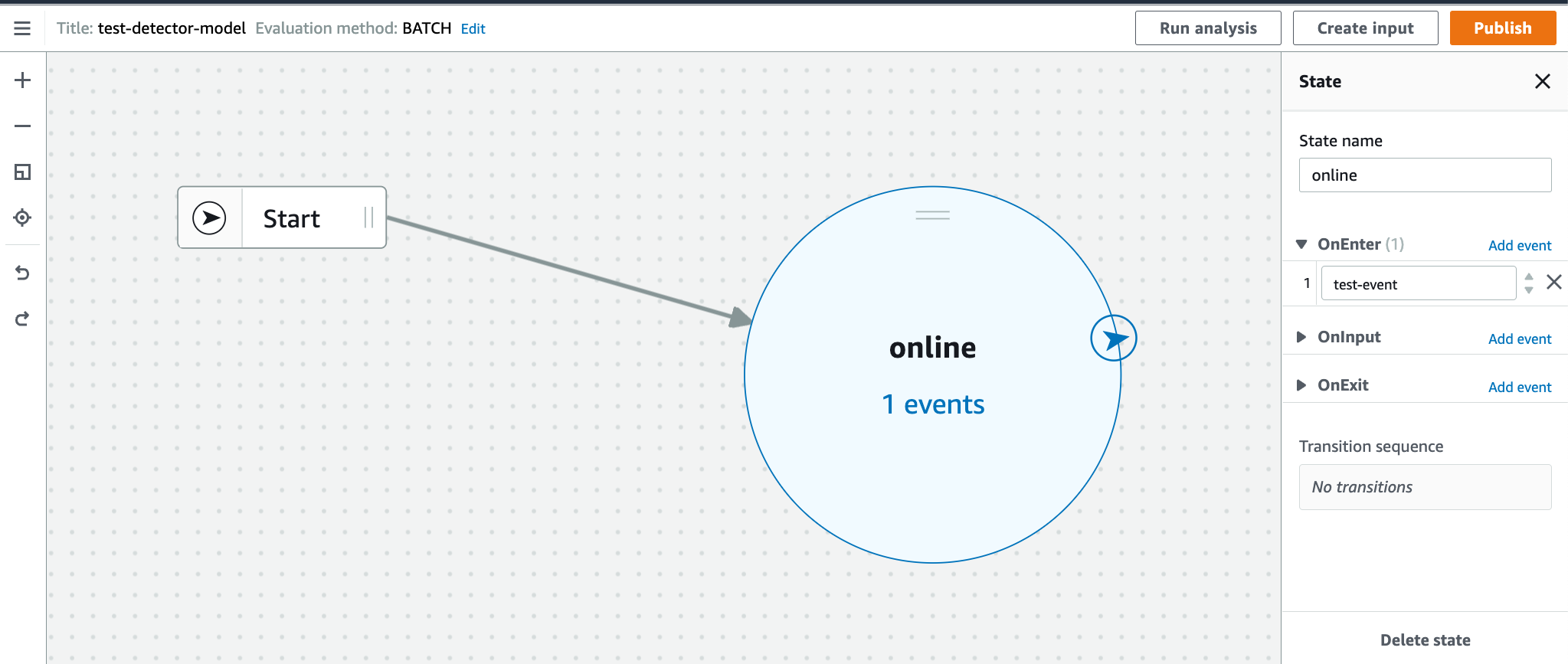 ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
Co-authored-by: AWS CDK Team <aws-cdk@amazon.com>
---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
- cognito - acmpca - codeguruprofiler - cloud9 - signer ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
…ore customization (#18561) ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
When using synthetics runtime "syn-nodejs-puppeteer-3.1" the default role tries to call s3:getBucketLocation on the artifacts bucket, but the policy is incorrect to allow that action. The policy should allow for that call directly on the bucket arn. fixes #13572 ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
Looking to unblock users who want to use assertions with annotations added on a stack. Fixes #18347 Example: ```ts class MyAspect implements IAspect { public visit(node: IConstruct): void { if (node instanceof CfnResource) { this.warn(node, 'insert message here', } } protected warn(node: IConstruct, message: string): void { Annotations.of(node).addWarning(message); } } const app = new App(); const stack = new Stack(app); new CfnResource(stack, 'Foo', { type: 'Foo::Bar', properties: { Baz: 'Qux', }, }); Aspects.of(stack).add(new MyAspect()); AssertAnnotations.fromStack(stack).hasMessage({ level: 'warning', entry: { data: 'insert message here', }, }); ``` ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
Migrates all of comcalvi's modules to assertions. PR is complete when these modules are migrated: - [x] autoscaling - [x] application autoscaling - [x] autoscaling common - [x] autoscaling hooktargets - [x] cloudtrail - [x] cloudformation-include - [x] logs ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
…18590) Add support for session timeout and client login banner for Client VPN endpoints. Modeled the session timeout as an `enum` and not a `Duration` because it only accepts a sets of values (comparable to `RetentionDays` in `aws-logs`). ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
could pass another bucket, but automatically created buckets are convenient/popular, so worth improving defaults https://docs.aws.amazon.com/cdk/api/latest/docs/@aws-cdk_aws-cloudtrail.Trail.html https://docs.aws.amazon.com/cdk/api/latest/docs/@aws-cdk_aws-s3.Bucket.html --- ```sh # updated integ snapshots packages/@aws-cdk/aws-cloudtrail $ /workspace/aws-cdk/tools/\@aws-cdk/cdk-integ-tools/bin/cdk-integ --dry-run packages/@aws-cdk/aws-codepipeline-actions $ /workspace/aws-cdk/tools/\@aws-cdk/cdk-integ-tools/bin/cdk-integ --dry-run ``` --- ```sh # eslint fix /workspace/aws-cdk/node_modules/eslint/bin/eslint.js packages/@aws-cdk/aws-cloudtrail/test/ --ext=.ts --fix ``` ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
…es not grant all necessary permissions (#18558) `ALB.logAccessLogs` today grants the ELB account Put/Abort on the bucket. The NLB code extends this to also grant permissions to the `delivery.logs.amazonaws.com` service principal. The ALB documentation now states that the permissions required for ALB are the same as NLB, so consolidating the code back into the base. fixes #18367 ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
…reating QueueProcessingFargateService (#18219) The `QueueProcessingFargateService` construct internally creates a service Container with the default healthcheck that cannot currently be overriden by the user. This change allows users to optionally provide a custom healthcheck that can be passed on to the internal ECS container definition. fixes #15636 ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
We forgot to remove this dependency when we migrated over to assertions. The assertions dependency is already added, so just removing this one. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
We implemented TagOptions as a full construct, and created its own unit test suite. We are moving some of the basic validation tests out of the other resources unit tests, and then the cross resource association tests as well. The only TagOption tests that remain in portfolio/product are for testing the association and adding as a prop, validation and multi resource tests will be in the `tag-option` test suite. The removed validation tests are already in the `tag-option` test suite. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
The autolabeler will now do different things depending on how the issue comes in. If it's guidance, it's automatically assigned to OSDS. If it's a PR, the autolabeler will not continue to work if the PR has `contribution/core`. For issues, the autolabeler will not continue to work on the issue if `needs-triage` is removed. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
Co-authored-by: AWS CDK Team <aws-cdk@amazon.com>
…pOriginProps` (#18697) This pull request extends the maximum value of the `readTimeout` property for `HttpOriginProps` up to 180 seconds. This allows the use of the construct also in the case that a limit increase has been approved for CloudFront [origin request timeout quota](https://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/cloudfront-limits.html#limits-web-distributions). The 180 seconds cap should be AWS hard limit for that quota. Closes #18628 ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
…18635) While using the Python Lambda with Code Artifact, discovered that Code Artifact was still inaccessible because bundling occurs at _run_ time, which can only access env vars, not build args. This is not a security issue because bundled output doesn't contain any of the secret values. **Note:** Without this, using Code Artifact (or any other private packaging for Python Lambdas) is currently broken. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
…8062) Revamped the logic of running `tsc`, previously we were running `tsc` once for the whole project and due to this logic, `tsc` was not running as on the first run as `createBundlingCommand` first prepare command to execute on Docker and then for local bundling and on the first run we already updated the flag to not run `tsc` now. Closes [#18002](#18002) ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
A dependency cycle was inadvertently introduced to CDK Pipelines in #18492. Fix that dependency cycle, and also one in Cognito IdentityPools. Add facilities to the `assertions` library to automatically detect this in the future, to stop errors like this from slipping in. We could make it a separate assertion method (`Template.fromStack().assertNoCycles()`), but the only thing that will do is give you an opportunity to forget to put the test in. Instead, we just check it by default for every generated template. Fixes #18673. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
Publishing our internal migration script written by @rix0rrr for others to benefit. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
Fixes #4159 ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
`Pillow` is an image processing library that we don't need at all, but our tests use. It has a high priority CVE reported against it. Since we don't actually need it, away it goes. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
The version of PyYAML that comes wit the AWS CLI we use has a CVE reported against it: CVE-2020-14343 Upgrade to a version of AWS CLI that has PyYAML >= 5.4. ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
Automated action from aws/cdk-ops
AWS CodeBuild CI Report
Powered by github-codebuild-logs, available on the AWS Serverless Application Repository |
|
Thank you for contributing! Your pull request will be automatically updated and merged without squashing (do not update manually, and be sure to allow changes to be pushed to your fork). |
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Labels
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
See CHANGELOG