This repo is forked from: https://github.com/hashicorp/terraform-azurerm-vault
https://github.com/hashicorp/terraform-azurerm-consul
Originally made by Gruntwork.
I have merged the two projects, and updated the code. Since the two repo's has not been updated or maintained for over a year.
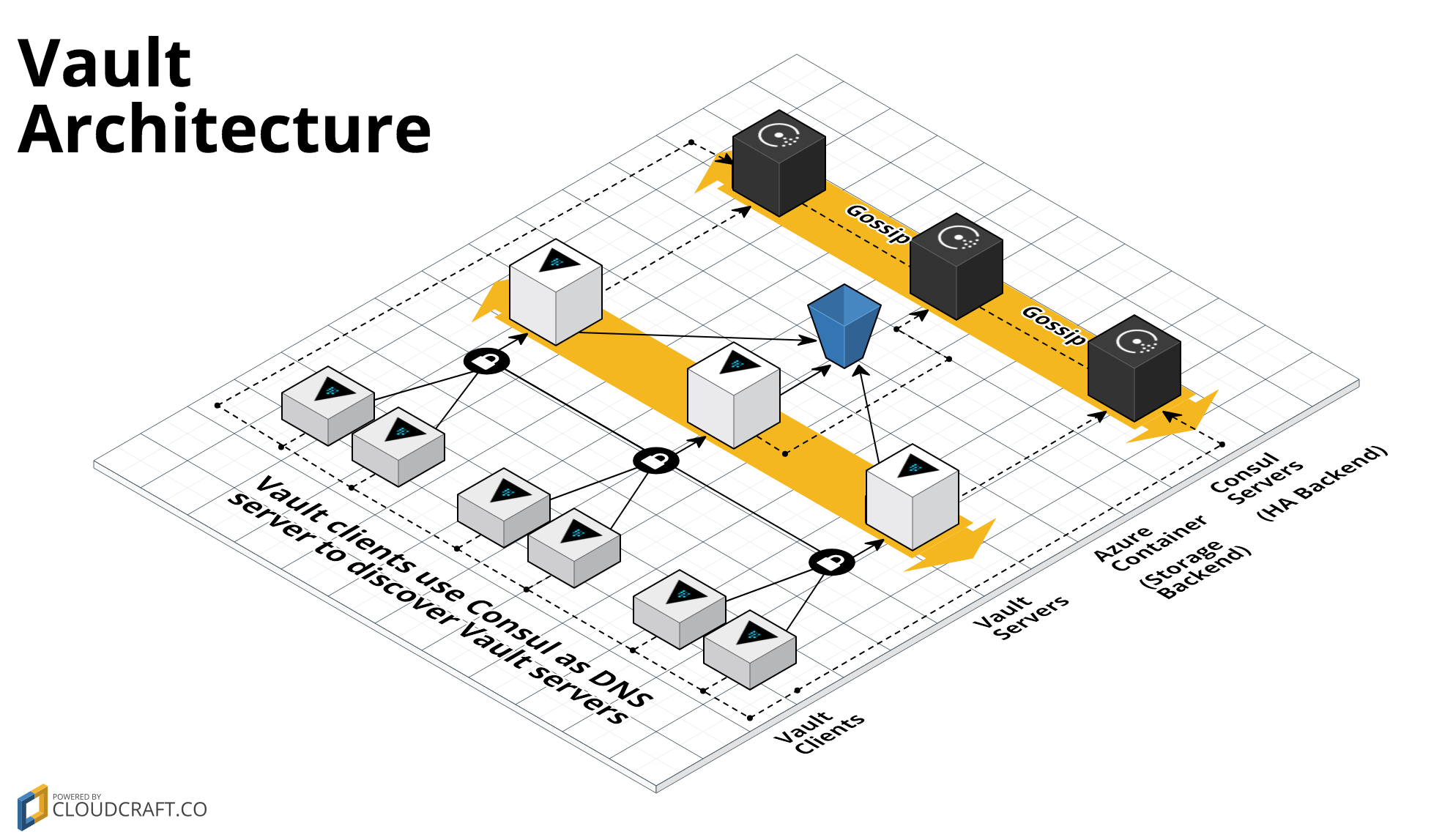
This repo contains a Module to deploy a Vault cluster on Azure using Terraform. Vault is an open source tool for managing secrets. This Module uses Azure Storage as a storage backend and a Consul server cluster as a high availability backend
Consul is a distributed, highly-available tool that you can use for service discovery and key/value storage. A Consul cluster typically includes a small number of server nodes, which are responsible for being part of the consensus quorum, and a larger number of client nodes, which you typically run alongside your apps::
This Module includes: ##Vault Cluster
-
install-vault: This module can be used to install Vault. It can be used in a Packer template to create a Vault Azure Manager Image.
-
run-vault: This module can be used to configure and run Vault. It can be used in a Custom Data script to fire up Vault while the server is booting.
-
vault-cluster: Terraform code to deploy a cluster of Vault servers using an [Scale Set] (https://docs.microsoft.com/en-us/azure/virtual-machine-scale-sets/virtual-machine-scale-sets-create).
-
private-tls-cert: Generate a private TLS certificate for use with a private Vault cluster.
-
update-certificate-store: Add a trusted, CA public key to an OS's certificate store. This allows you to establish TLS connections to services that use this TLS certs signed by this CA without getting x509 certificate errors.
##Consul Cluster
-
install-consul: This module can be used to install Vault. It can be used in a Packer template to create a Vault Azure Manager Image.
-
run-consul: This module can be used to configure and run Consul. It can be used in a Custom Data script to fire up Vault while the server is booting.
-
consul-cluster: Terraform code to deploy a cluster of Vault servers using an Scale Set.
-
consul-security-group-rules: Defines the security group rules used by a Consul cluster to control the traffic that is allowed to go in and out of the cluster.
-
install-dnsmasq: This folder contains a script for installing Dnsmasq and configuring it to forward requests for a specific domain to Consul.
A Module is a canonical, reusable, best-practices definition for how to run a single piece of infrastructure, such as a database or server cluster. Each Module is created primarily using Terraform, includes automated tests, examples, and documentation, and is maintained both by the open source community and companies that provide commercial support.
Instead of having to figure out the details of how to run a piece of infrastructure from scratch, you can reuse existing code that has been proven in production. And instead of maintaining all that infrastructure code yourself, you can leverage the work of the Module community and maintainers, and pick up infrastructure improvements through a version number bump.
Each Module has the following folder structure:
- root: The root folder contains the main terraform project and variables that other modules will use.
- modules: This folder contains the reusable code for this Module, broken down into one or more modules.
- examples: This folder contains the packer image example. Plus initial azure setup (Resource Group, Storage Account, and Secret key)
To remove Public IP loadbalancer go into module/vault-cluster and module/consul-cluster and comment out LoadBalancing Section and uncomment Non-Loadbalancing section. You will need to use a bastion host/Jump Box to access Vault and Consul. Recommended for Production environments.
- Create Azure Resource Group and Storage account - This is created separatly since the Packer Image needs to be created and uploaded before running the main terraform.
- Go to examples/azure-project-setup
- In vars.tf enter your Azure subscription_id, tenant_id, client_id, secret_access_key - Save the file
- Now run terraform plan, terraform apply
- Copy the output and enter it into the main vars.tf file under root. Also enter Azure subscription_id, tenant_id, client_id, secret_access_key, plus your ssh-rsa.
- To find your ssh-rsa, in your terminal "cat ~/.ssh/id_rsa.pub" - Copy the whole output, create a new public rsa key if you like.
- Create your SSL Certs
- Go to /modules/private-tls-cert
- Run terraform plan, terrform apply.
- Copy certificates - ca.crt.pem, vault.crt.pem, vault.key.pem to examples/vault-consul-image/tls
- Create Packer Image
- Go to examples/vault-consul-image/vault-consul.json
- Add Azure subscription_id, tenant_id, client_id, secret_access_key(client_secret) also add your github oath token.
- If you want to use your own forked or cloned repo. Go to line 64 and edit the repo.
- Save file.
- Run "packer build vault-consul.json"
- This will take some time to create your images and push to Azure.
- Once it has completed copy the image_uri
- Paste into main vars.tf in root, under image_uri ex. "/subscriptions/xxxxxxxx/resourceGroups/vault-consul-cluster/providers/Microsoft.Compute/images/vault-consul-ubuntu-2019-02-12-185900"
- Deploy Vault and Consul Cluster
-
Go to the root directory
-
Run - terraform plan, terrform apply
-
This will take some time to complete.
-
Once successfully deploy it should output your external IP addresses. Ex "Apply complete! Resources: 23 added, 0 changed, 0 destroyed.
Outputs:
consul_admin_user_name = consuladmin
consul_cluster_size = 3 consul_load_balancer_ip_address = [ 104.22.245.235 ] vault_admin_user_name = vaultadmin vault_cluster_size = 3 vault_load_balancer_ip_address = [ 104.22.222.210 ]"
- Test to see if Consul is running.
- Consul external IP Address with port 8500 ex. http://104.22.245.235:8500
- You will see errors since you need to initialize and unseal vault.
- Vault init and unseal.
- Find the ssh port for vault. Go to Azure Console or use azure CLI.
- Azure Console - resourceGroups/vault-consul-cluster/providers/Microsoft.Network/loadBalancers/vault-cluster_access/overview
- You need to SSH into all three, but only 'vault init' on the first one.
- ssh vaultadmin@104.22.222.210 -p 2200
- Once logged in - Run 'vault operator init'
- Vault will display your Unseal keys and Initial Root Token. ###Copy these to a safe place
- To unseal your vault server - Run - 'vault unseal'
- Copy one of your unseal keys. You will need to run this command another two times with the different keys. To unseal vault.
- Login to the other two vault servers. No need to run 'vault operator init' since it is alrady intialized. Only Run - 'vault unseal'. You will need to do this 3 times as well, on each server.
- Complete
- If you go back to your Consul API, you will see everything is healthy.
- Destroy
- In the root directory - Run 'terraform destroy'
- You might need to run this twice since sometimes Azure is slow.
- Go to examples/azure-resource-project - Run 'terraform destroy' - or just run this to destroy everything.
This code is released under the Apache 2.0 License. Please see LICENSE and NOTICE for more details.