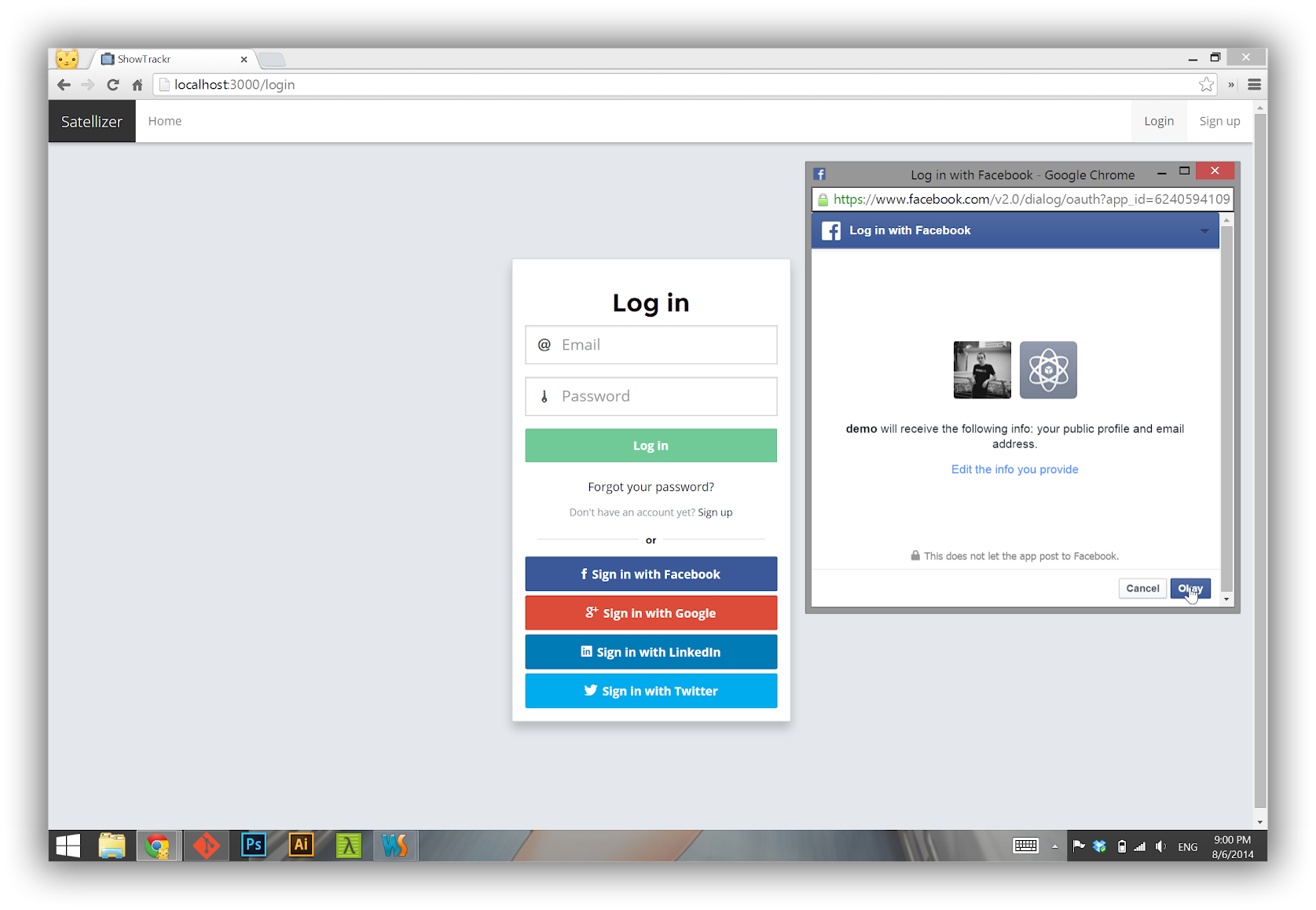
Live Demo: https://satellizer.herokuapp.com
Satellizer is a simple to use, end-to-end, token-based authentication module for AngularJS with built-in support for Google, Facebook, LinkedIn, Twitter, GitHub, Yahoo, Twitch, Microsoft OAuth providers, as well as Email and Password sign-in. However, you are not limited to the sign-in options above, in fact you can add any OAuth 1.0 or OAuth 2.0 provider by passing provider-specific information in the app config block.
- Installation
- Usage
- Configuration
- Browser Support
- Authentication Flow
- Login with Email and Password
- Login with OAuth 1.0
- Login with OAuth 2.0
- Logout
- Obtaining OAuth Keys
- API Reference
- FAQ
- Credits
- License
The easiest way to get Satellizer is by running one of the following commands:
# Bower
bower install satellizer
# NPM
npm install satellizerAlternatively, you may download the latest release or use the CDN:
<!--[if lte IE 9]>
<script src="//cdnjs.cloudflare.com/ajax/libs/Base64/0.3.0/base64.min.js"></script>
<![endif]-->
<script src="//cdn.jsdelivr.net/satellizer/0.13.0/satellizer.min.js"></script>Note: Sattelizer depends on window.atob() for decoding JSON Web Tokens. If you need to support IE9 then use Base64 polyfill above.
Step 1. App Module
angular.module('MyApp', ['satellizer'])
.config(function($authProvider) {
$authProvider.facebook({
clientId: 'Facebook App ID'
});
$authProvider.google({
clientId: 'Google Client ID'
});
$authProvider.github({
clientId: 'GitHub Client ID'
});
$authProvider.linkedin({
clientId: 'LinkedIn Client ID'
});
$authProvider.instagram({
clientId: 'Instagram Client ID'
});
$authProvider.yahoo({
clientId: 'Yahoo Client ID / Consumer Key'
});
$authProvider.live({
clientId: 'Microsoft Client ID'
});
$authProvider.twitch({
clientId: 'Twitch Client ID'
});
// No additional setup required for Twitter
$authProvider.oauth2({
name: 'foursquare',
url: '/auth/foursquare',
clientId: 'Foursquare Client ID',
redirectUri: window.location.origin,
authorizationEndpoint: 'https://foursquare.com/oauth2/authenticate',
});
});Step 2. Controller
angular.module('MyApp')
.controller('LoginCtrl', function($scope, $auth) {
$scope.authenticate = function(provider) {
$auth.authenticate(provider);
};
});Step 3. Template
<button ng-click="authenticate('facebook')">Sign in with Facebook</button>
<button ng-click="authenticate('google')">Sign in with Google</button>
<button ng-click="authenticate('github')">Sign in with GitHub</button>
<button ng-click="authenticate('linkedin')">Sign in with LinkedIn</button>
<button ng-click="authenticate('instagram')">Sign in with Instagram</button>
<button ng-click="authenticate('twitter')">Sign in with Twitter</button>
<button ng-click="authenticate('foursquare')">Sign in with Foursquare</button>
<button ng-click="authenticate('yahoo')">Sign in with Yahoo</button>
<button ng-click="authenticate('live')">Sign in with Windows Live</button>
<button ng-click="authenticate('twitch')">Sign in with Twitch</button>Note: For server-side usage please refer to the examples directory.
Below is a complete listing of all default configuration options.
httpInterceptor: function() { return true; },
$authProvider.withCredentials = true;
$authProvider.tokenRoot = null;
$authProvider.cordova = false;
$authProvider.baseUrl = '/';
$authProvider.loginUrl = '/auth/login';
$authProvider.signupUrl = '/auth/signup';
$authProvider.unlinkUrl = '/auth/unlink/';
$authProvider.tokenName = 'token';
$authProvider.tokenPrefix = 'satellizer';
$authProvider.authHeader = 'Authorization';
$authProvider.authToken = 'Bearer';
$authProvider.storageType = 'localStorage';
// Facebook
$authProvider.facebook({
name: 'facebook',
url: '/auth/facebook',
authorizationEndpoint: 'https://www.facebook.com/v2.5/dialog/oauth',
redirectUri: window.location.origin + '/',
requiredUrlParams: ['display', 'scope'],
scope: ['email'],
scopeDelimiter: ',',
display: 'popup',
type: '2.0',
popupOptions: { width: 580, height: 400 }
});
// Google
$authProvider.google({
url: '/auth/google',
authorizationEndpoint: 'https://accounts.google.com/o/oauth2/auth',
redirectUri: window.location.origin || window.location.protocol + '//' + window.location.host,
requiredUrlParams: ['scope'],
optionalUrlParams: ['display'],
scope: ['profile', 'email'],
scopePrefix: 'openid',
scopeDelimiter: ' ',
display: 'popup',
type: '2.0',
popupOptions: { width: 452, height: 633 }
});
// GitHub
$authProvider.github({
url: '/auth/github',
authorizationEndpoint: 'https://github.com/login/oauth/authorize',
redirectUri: window.location.origin || window.location.protocol + '//' + window.location.host,
optionalUrlParams: ['scope'],
scope: ['user:email'],
scopeDelimiter: ' ',
type: '2.0',
popupOptions: { width: 1020, height: 618 }
});
// LinkedIn
$authProvider.linkedin({
url: '/auth/linkedin',
authorizationEndpoint: 'https://www.linkedin.com/uas/oauth2/authorization',
redirectUri: window.location.origin || window.location.protocol + '//' + window.location.host,
requiredUrlParams: ['state'],
scope: ['r_emailaddress'],
scopeDelimiter: ' ',
state: 'STATE',
type: '2.0',
popupOptions: { width: 527, height: 582 }
});
// Twitter
$authProvider.twitter({
url: '/auth/twitter',
authorizationEndpoint: 'https://api.twitter.com/oauth/authenticate',
redirectUri: window.location.origin || window.location.protocol + '//' + window.location.host,
type: '1.0',
popupOptions: { width: 495, height: 645 }
});
// Twitch
$authProvider.twitch({
url: '/auth/twitch',
authorizationEndpoint: 'https://api.twitch.tv/kraken/oauth2/authorize',
redirectUri: window.location.origin || window.location.protocol + '//' + window.location.host,
requiredUrlParams: ['scope'],
scope: ['user_read'],
scopeDelimiter: ' ',
display: 'popup',
type: '2.0',
popupOptions: { width: 500, height: 560 }
});
// Windows Live
$authProvider.live({
url: '/auth/live',
authorizationEndpoint: 'https://login.live.com/oauth20_authorize.srf',
redirectUri: window.location.origin || window.location.protocol + '//' + window.location.host,
requiredUrlParams: ['display', 'scope'],
scope: ['wl.emails'],
scopeDelimiter: ' ',
display: 'popup',
type: '2.0',
popupOptions: { width: 500, height: 560 }
});
// Yahoo
$authProvider.yahoo({
url: '/auth/yahoo',
authorizationEndpoint: 'https://api.login.yahoo.com/oauth2/request_auth',
redirectUri: window.location.origin || window.location.protocol + '//' + window.location.host,
scope: [],
scopeDelimiter: ',',
type: '2.0',
popupOptions: { width: 559, height: 519 }
});
// Generic OAuth 2.0
$authProvider.oauth2({
name: null,
url: null,
clientId: null,
redirectUri: null,
authorizationEndpoint: null,
defaultUrlParams: ['response_type', 'client_id', 'redirect_uri'],
requiredUrlParams: null,
optionalUrlParams: null,
scope: null,
scopePrefix: null,
scopeDelimiter: null,
state: null,
type: null,
popupOptions: null,
responseType: 'code',
responseParams: {
code: 'code',
clientId: 'clientId',
redirectUri: 'redirectUri'
}
});
// Generic OAuth 1.0
$authProvider.oauth1({
name: null,
url: null,
authorizationEndpoint: null
redirectUri: null,
type: null,
popupOptions: null
});| 9* | ✓ | ✓ | ✓ | ✓ | ✓ |
* Requires Base64 polyfill.
Satellizer relies on token-based authentication using JSON Web Tokens instead of cookies.
Client: Enter your email and password into the login form.
Client: On form submit call
$auth.login()with email and password.Client: Send a
POSTrequest to/auth/login.Server: Check if email exists, if not - return
401.Server: Check if password is correct, if not - return
401.Server: Create a JSON Web Token and send it back to the client.
Client: Parse the token and save it to Local Storage for subsequent use after page reload.
Client: Open an empty popup window via
$auth.authenticate('provider name').Client: Unlike OAuth 2.0, with OAuth 1.0 you cannot go directly to the authorization screen without a valid
request_token.Client: The OAuth 1.0 flow starts with an empty POST request to /auth/provider.
Server: Obtain and return
request_tokenfor the authorization popup.Client: Set the URL location of a popup to the
authorizationEndpointwith a validrequest_tokenquery parameter, as well as popup options for height and width. This will redirect a user to the authorization screen. After this point, the flow is very similar to OAuth 2.0.Client: Sign in with your username and password if necessary, then authorize the application.
Client: Send a POST request back to the /auth/provider with
oauth_tokenandoauth_verifierquery parameters.Server: Do an OAuth-signed
POSTrequest to the /access_token URL since we now haveoauth_tokenandoauth_verifierparameters.Server: Look up the user by their unique Provider ID. If user already exists, grab the existing user, otherwise create a new user account.
Server: Create a JSON Web Token and send it back to the client.
Client: Parse the token and save it to Local Storage for subsequent use after page reload.
Client: Open a popup window via
$auth.authenticate('provider name').Client: Sign in with that provider, if necessary, then authorize the application.
Client: After successful authorization, the popup is redirected back to your app, e.g. http://localhost:3000, with the
code(authorization code) query string parameter.Client: The
codeparameter is sent back to the parent window that opened the popup.Client: Parent window closes the popup and sends a POST request to /auth/provider with
codeparameter.Server: Authorization code is exchanged for access token.
Server: User information is retrived using the access token from Step 6.
Server: Look up the user by their unique Provider ID. If user already exists, grab the existing user, otherwise create a new user account.
Server: In both cases of Step 8, create a JSON Web Token and send it back to the client.
Client: Parse the token and save it to Local Storage for subsequent use after page reload.
Note: To learn more about JSON Web Tokens visit JWT.io.
Note: Make sure you have turned on Contacts API and Google+ API in the APIs tab.
- Visit [Facebook Developers](https://developers.facebook.com/) - Click **Apps > Create a New App** in the navigation bar - Enter *Display Name*, then choose a category, then click **Create app** - Click on *Settings* on the sidebar, then click **+ Add Platform** - Select **Website** - Enter *http://localhost:3000* for *Site URL*
- Sign in at [https://apps.twitter.com](https://apps.twitter.com/) - Click on **Create New App** - Enter your *Application Name*, *Description* and *Website* - For **Callback URL**: *http://127.0.0.1:3000* - Go to **Settings** tab - Under *Application Type* select **Read and Write** access - Check the box **Allow this application to be used to Sign in with Twitter** - Click **Update this Twitter's applications settings**
- Visit [Live Connect App Management](http://go.microsoft.com/fwlink/p/?LinkId=193157). - Click on **Create application** - Enter an *Application name*, then click on **I accept** button - Go to **API Settings** tab - Enter a *Redirect URL* - Click **Save** - Go to **App Settings** tab to get *Client ID* and *Client Secret*
Note: Microsoft does not consider
localhostor127.0.0.1to be a valid URL. As a workaround for local development add127.0.0.1 mylocalwebsite.netto /etc/hosts file and specifymylocalwebsite.netas your Redirect URL in the API Settings tab.
$auth.login(user, [options])$auth.signup(user, [options])$auth.authenticate(name, [userData])$auth.logout()$auth.isAuthenticated()$auth.link(name, [userData])$auth.unlink(name, [options])$auth.getToken()$auth.getPayload()$auth.setToken(token)$auth.removeToken()$auth.setStorageType(type)
Sign in using Email and Password.
| Param | Type | Details |
|---|---|---|
| user | Object |
JavaScript object containing user information. |
| options (optional) | Object |
HTTP config object. See $http(config) docs. |
- response - The HTTP response object from the server.
var user = {
email: $scope.email,
password: $scope.password
};
$auth.login(user)
.then(function(response) {
// Redirect user here after a successful log in.
})
.catch(function(response) {
// Handle errors here, such as displaying a notification
// for invalid email and/or password.
});Create a new account with Email and Password.
| Param | Type | Details |
|---|---|---|
| user | Object |
JavaScript object containing user information. |
| options (optional) | Object |
HTTP config object. See $http(config) docs. |
- response - The HTTP response object from the server.
var user = {
firstName: $scope.firstName,
lastName: $scope.lastName,
email: $scope.email,
password: $scope.password
};
$auth.signup(user)
.then(function(response) {
// Redirect user here to login page or perhaps some other intermediate page
// that requires email address verification before any other part of the site
// can be accessed.
})
.catch(function(response) {
// Handle errors here.
});Starts the OAuth 1.0 or the OAuth 2.0 authorization flow by opening a popup window.
| Param | Type | Details |
|---|---|---|
| name | String |
One of the built-in or custom OAuth provider names created via $authProvider.oauth1() or $authProvider.oauth2(). |
| userData (optional) | Object |
If you need to send additional data to the server along with code, clientId and redirectUri (OAuth 2.0) or oauth_token and oauth_verifier (OAuth 1.0). |
- response - The HTTP response object from the server.
$auth.authenticate('google')
.then(function(response) {
// Signed in with Google.
})
.catch(function(response) {
// Something went wrong.
});Deletes a token from Local Storage (or Session Storage).
$auth.logout();Checks authentication status of a user.
| State | True | False |
|---|---|---|
| No token in Local Storage | ✓ | |
| Token present, but not a valid JWT | ✓ | |
JWT present without exp |
✓ | |
JWT present with exp and not expired |
✓ | |
JWT present with exp and expired |
✓ |
// Controller
$scope.isAuthenticated = function() {
return $auth.isAuthenticated();
};<!-- Template -->
<ul ng-if="!isAuthenticated()">
<li><a href="/login">Login</a></li>
<li><a href="/signup">Sign up</a></li>
</ul>
<ul ng-if="isAuthenticated()">
<li><a href="/logout">Logout</a></li>
</ul>Alias for $auth.authenticate(name, [userData]).
💡 Note: Account linking (and merging) business logic is handled entirely on the server.
// Controller
$scope.link = function(provider) {
$auth.link(provider)
.then(function(response) {
// You have successfully linked an account.
})
.catch(function(response) {
// Handle errors here.
});
};<!-- Template -->
<button ng-click="link('facebook')">
Connect Facebook Account
</button>Unlinks an OAuth provider.
By default, sends a POST request to /auth/unlink with the { provider: name } data object.
| Param | Type | Details |
|---|---|---|
| name | String |
One of the built-in or custom OAuth provider names created via $authProvider.oauth1() or $authProvider.oauth2(). |
| options (optional) | Object |
HTTP config object. See $http(config) docs. |
- response - The HTTP response object from the server.
$auth.unlink('github')
.then(function(response) {
// You have unlinked a GitHub account.
})
.catch(function(response) {
// Handle errors here.
});Returns a token from Local Storage (or Session Storage).
$auth.getToken();
// eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOjEyMzQ1Njc4OTAsIm5hbWUiOiJKb2huIERvZSJ9.kRkUHzvZMWXjgB4zkO3d6P1imkdp0ogebLuxnTCiYUUReturns a JWT Claims Set, i.e. the middle part of a JSON Web Token.
$auth.getPayload();
// { exp: 1414978281, iat: 1413765081, userId: "544457a3eb129ee822a38fdd" }Saves a JWT or an access token to Local Storage / Session Storage.
| Param | Type | Details |
|---|---|---|
| token | Object |
An object that takes a JWT (response.data[config.tokenName]) or an access token (response.access_token). |
Removes a token from Local Storage / Session Storage. Used internally by $auth.logout().
$auth.removeToken();Sets storage type to Local Storage or Session Storage.
| Param | Type | Details |
|---|---|---|
| type | String |
Accepts 'localStorage' and 'sessionStorage' values. |
$auth.setStorageType('sessionStorage');Coming Soon
| Contribution | User |
|---|---|
| Dropwizard (Java) Example | Alice Chen |
| Go Example | Salim Alami |
| Ruby on Rails Example | Simonas Gildutis |
| Ionic Framework Example | Dimitris Bozelos |
Additionally, I would like to thank all other contributors who have reported bugs, submitted pull requests and suggested new features!
The MIT License (MIT)
Copyright (c) 2014-2015 Sahat Yalkabov
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.