DERO News Forum Wiki Explorer Source Twitter Discord Github Stats WebWallet Medium
DERO has migrated from Atlantis(CryptoNote) to it's own DERO Homomorphic Encrytion Blockchain Protocol on 26 Feb 2022 with code name Stargate.
Homomorphic Encryption offers offers very high level of privacy.
Please visit new repo of DERO-HE.
For migration of your DERO from DERO-Atlantis to new DERO-Stargate check DERO swap-HowTO.
This repo is now outdated and will be archived.
- ABOUT DERO PROJECT
- DERO Crypto
- DERO PORTS
- Technical
- DERO blockchain salient features
- DERO Innovations
- DERO Mining
- DERO Installation
- Next Step After DERO Installation
- DERO Explorer
- Proving DERO Transactions
DERO is decentralized DAG(Directed Acyclic Graph) based blockchain with enhanced reliability, privacy, security, and usability. Consensus algorithm is PoW based on DERO AstroBWT: ASIC/FPGA/GPU resistant CPU mining algorithm . DERO is industry leading and the first blockchain to have bulletproofs, TLS encrypted Network.
DERO is the first crypto project to combine a Proof of Work blockchain with a DAG block structure and wholly anonymous transactions based on CryptoNote Protocol. The fully distributed ledger processes transactions with a twelve-second average block time and is secure against majority hashrate attacks. DERO will be the first CryptoNote blockchain to have smart contracts on its native chain without any extra layers or secondary blockchains. At present DERO have Smart Contracts on testnet.
Secure and fast crypto is the basic necessity of this project and adequate amount of time has been devoted to develop/study/implement/audit it. Most of the crypto such as ring signatures have been studied by various researchers and are in production by number of projects. As far as the Bulletproofs are considered, since DERO is the first one to implement/deploy, they have been given a more detailed look. First, a bare bones bulletproofs was implemented, then implementations in development were studied (Benedict Bunz,XMR, Dalek Bulletproofs) and thus improving our own implementation.
Some new improvements were discovered and implemented (There are number of other improvements which are not explained here). Major improvements are in the Double-Base Double-Scalar Multiplication while validating bulletproofs. A typical bulletproof takes ~15-17 ms to verify. Optimised bulletproofs takes ~1 to ~2 ms(simple bulletproof, no aggregate/batching). Since, in the case of bulletproofs the bases are fixed, we can use precompute table to convert 64*2 Base Scalar multiplication into doublings and additions (NOTE: We do not use Bos-Coster/Pippienger methods). This time can be again easily decreased to .5 ms with some more optimizations. With batching and aggregation, 5000 range-proofs (~2500 TX) can be easily verified on even a laptop. The implementation for bulletproofs is in github.com/deroproject/derosuite/crypto/ringct/bulletproof.go , optimized version is in github.com/deroproject/derosuite/crypto/ringct/bulletproof_ultrafast.go
There are other optimizations such as base-scalar multiplication could be done in less than a microsecond. Some of these optimizations are not yet deployed and may be deployed at a later stage.
Mainnet:
P2P Default Port: 20202
RPC Default Port: 20206
Wallet RPC Default Port: 20209
Testnet:
P2P Default Port: 30303
RPC Default Port: 30306
Wallet RPC Default Port: 30309
For specific details of current DERO core (daemon) implementation and capabilities, see below:
- DAG: No orphan blocks, No soft-forks.
- BulletProofs: Zero Knowledge range-proofs(NIZK)
- Cryptonight Hash: This is memory-bound algorithm. This provides assurance that all miners are equal. ( No miner has any advantage over common miners).
- P2P Protocol: This layers controls exchange of blocks, transactions and blockchain itself.
- Pederson Commitment: (Part of ring confidential transactions): Pederson commitment algorithm is a cryptographic primitive that allows user to commit to a chosen value while keeping it hidden to others. Pederson commitment is used to hide all amounts without revealing the actual amount. It is a homomorphic commitment scheme.
- Borromean Signature: (Part of ring confidential transactions): Borromean Signatures are used to prove that the commitment has a specific value, without revealing the value itself.
- Additive Homomorphic Encryption: Additive Homomorphic Encryption is used to prove that sum of encrypted Input transaction amounts is EQUAL to sum of encrypted output amounts. This is based on Homomorphic Pederson commitment scheme.
- Multilayered Linkable Spontaneous Anonymous Group (MLSAG) : (Part of ring confidential transactions): MLSAG gives DERO untraceability and increases privacy and fungibility. MLSAG is a user controlled parameter ( Mixin) which the user can change to improve his privacy. Mixin of minimal amount is enforced and user cannot disable it.
- Ring Confidential Transactions: Gives untraceability , privacy and fungibility while making sure that the system is stable and secure.
- Core-Consensus Protocol implemented: Consensus protocol serves 2 major purpose
- Protects the system from adversaries and protects it from forking and tampering.
- Next block in the chain is the one and only correct version of truth ( balances).
- Proof-of-Work(PoW) algorithm: PoW part of core consensus protocol which is used to cryptographically prove that X amount of work has been done to successfully find a block.
- Difficulty algorithm: Difficulty algorithm controls the system so as blocks are found roughly at the same speed, irrespective of the number and amount of mining power deployed.
- Serialization/De-serialization of blocks: Capability to encode/decode/process blocks .
- Serialization/De-serialization of transactions: Capability to encode/decode/process transactions.
- Transaction validity and verification: Any transactions flowing within the DERO network are validated,verified.
- Socks proxy: Socks proxy has been implemented and integrated within the daemon to decrease user identifiability and improve user anonymity.
- Interactive daemon can print blocks, txs, even entire blockchain from within the daemon
- status, diff, print_bc, print_block, print_tx and several other commands implemented
- GO DERO Daemon has both mainnet, testnet support.
- Enhanced Reliability, Privacy, Security, Useability, Portabilty assured.
- DAG Based: No orphan blocks, No soft-forks.
- 51% Attack resistant.
- 12 Second Block time.
- Extremely fast transactions with 2 minutes confirmation time.
- SSL/TLS P2P Network.
- CryptoNote: Fully Encrypted Blockchain
- Dero Fastest Rocket BulletProofs: Zero Knowledge range-proofs(NIZK).
- Ring signatures.
- Fully Auditable Supply.
- DERO blockchain is written from scratch in Golang. See all unique blockchains from scratch.
- Developed and maintained by original developers.
Following are DERO first and leading innovations.
DERO DAG implementation builds outs a main chain from the DAG network of blocks which refers to main blocks (100% reward) and side blocks (8% rewards).
DERO DAG Screenshot Live
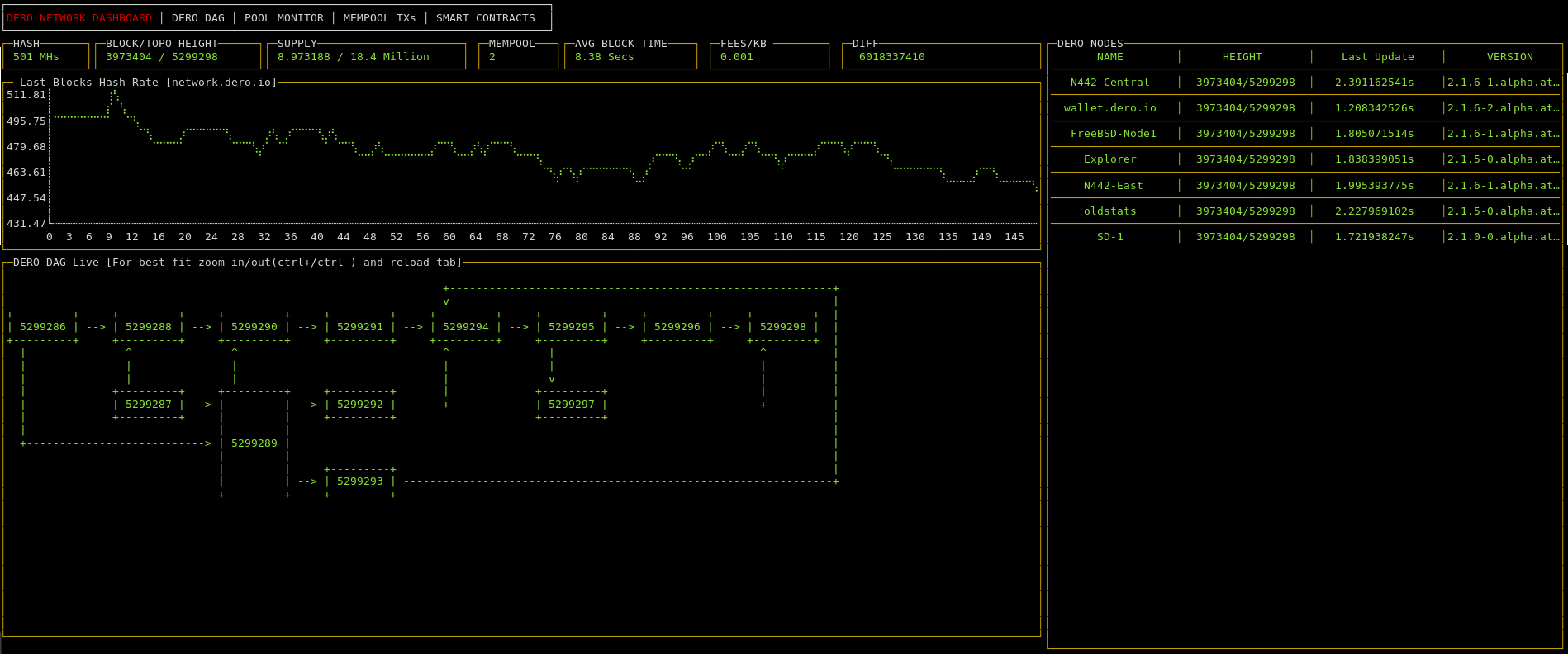
DERO DAG Screenshot Live
Traditional Blockchains process blocks as single unit of computation(if a double-spend tx occurs within the block, entire block is rejected). However DERO network accepts such blocks since DERO blockchain considers transaction as a single unit of computation.DERO blocks may contain duplicate or double-spend transactions which are filtered by client protocol and ignored by the network. DERO DAG processes transactions atomically one transaction at a time.
-
Dero ultrafast bulletproofs optimization techniques in the form used did not exist anywhere in publicly available cryptography literature at the time of implementation. Please contact for any source/reference to include here if it exists. Ultrafast optimizations verifies Dero bulletproofs 10 times faster than other/original bulletproof implementations. See: https://github.com/deroproject/derosuite/blob/master/crypto/ringct/bulletproof_ultrafast.go
-
DERO rocket bulletproof implementations are hardened, which protects DERO from certain class of attacks.
-
DERO rocket bulletproof transactions structures are not compatible with other implementations.
Also there are several optimizations planned in near future in Dero rocket bulletproofs which will lead to several times performance boost. Presently they are under study for bugs, verifications, compatibilty etc.
DERO DAG implementation builds outs a main chain from the DAG network of blocks which refers to main blocks (100% reward) and side blocks (8% rewards). Side blocks contribute to chain PoW security and thus traditional 51% attacks are not possible on DERO network. If DERO network finds another block at the same height, instead of choosing one, DERO include both blocks. Thus, rendering the 51% attack futile.
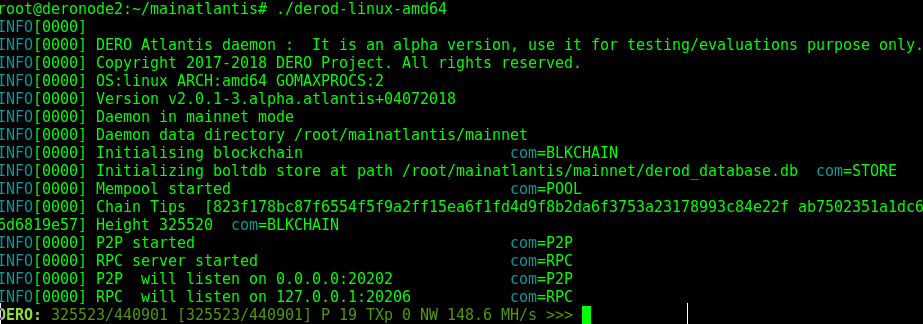
DERO is written in golang and very easy to install both from source and binary.
- Install Golang, Golang version 1.12.12 required.
- In go workspace:
go get -u github.com/deroproject/derosuite/... - Check go workspace bin folder for binaries.
- For example on Linux machine following binaries will be created:
- derod-linux-amd64 -> DERO daemon.
- dero-wallet-cli-linux-amd64 -> DERO cmdline wallet.
- explorer-linux-amd64 -> DERO Explorer. Yes, DERO has prebuilt personal explorer also for advance privacy users.
Download DERO binaries for ARM, INTEL, MAC platform and Windows, Mac, FreeBSD, OpenBSD, Linux etc. operating systems.
Most users required following binaries:
Windows 7-10, Server 64bit/amd64
Windows 32bit/x86/386
Linux 64bit/amd64
Linux 32bit/x86
FreeBSD 64bit/amd64
OpenBSD 64bit/amd64
Mac OS
Contact for support of other hardware and OS.
Running DERO daemon supports DERO network and shows your support to privacy.
Run derod.exe or derod-linux-amd64 depending on your operating system. It will start syncing.
- DERO daemon core cryptography is highly optimized and fast.
- Use dedicated machine and SSD for best results.
- VPS with 2-4 Cores, 4GB RAM, 60GB disk is recommended.
Dero cmdline wallet is most reliable and has support of all functions. Cmdline wallet is most secure and reliable.
DERO cmdline wallet is menu based and very easy to operate.
Use various options to create, recover, transfer balance etc.
NOTE: DERO cmdline wallet by default connects DERO daemon running on local machine on port 20206.
If DERO daemon is not running start DERO wallet with --remote option like following:
./dero-wallet-cli-linux-amd64 --remote
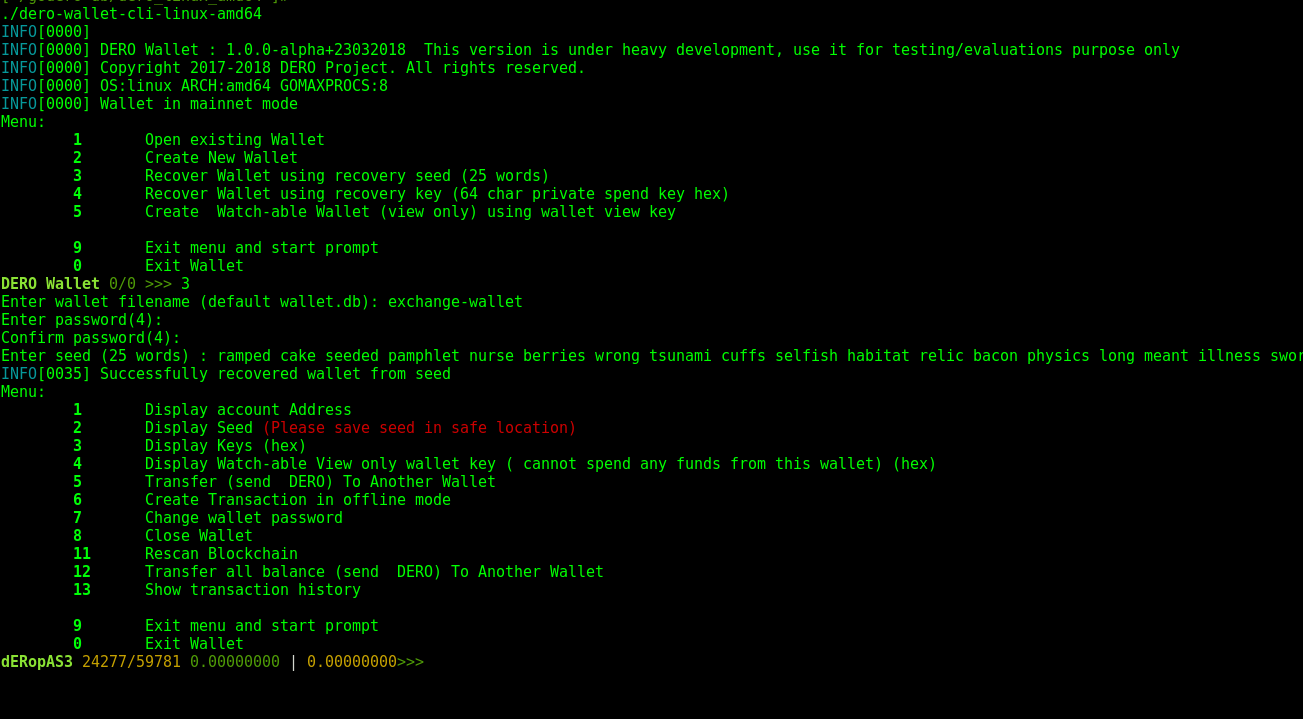
DERO Cmdline Wallet Screenshot
Web Wallet runs in your browser, your seeds, keys etc. never leave your browser.
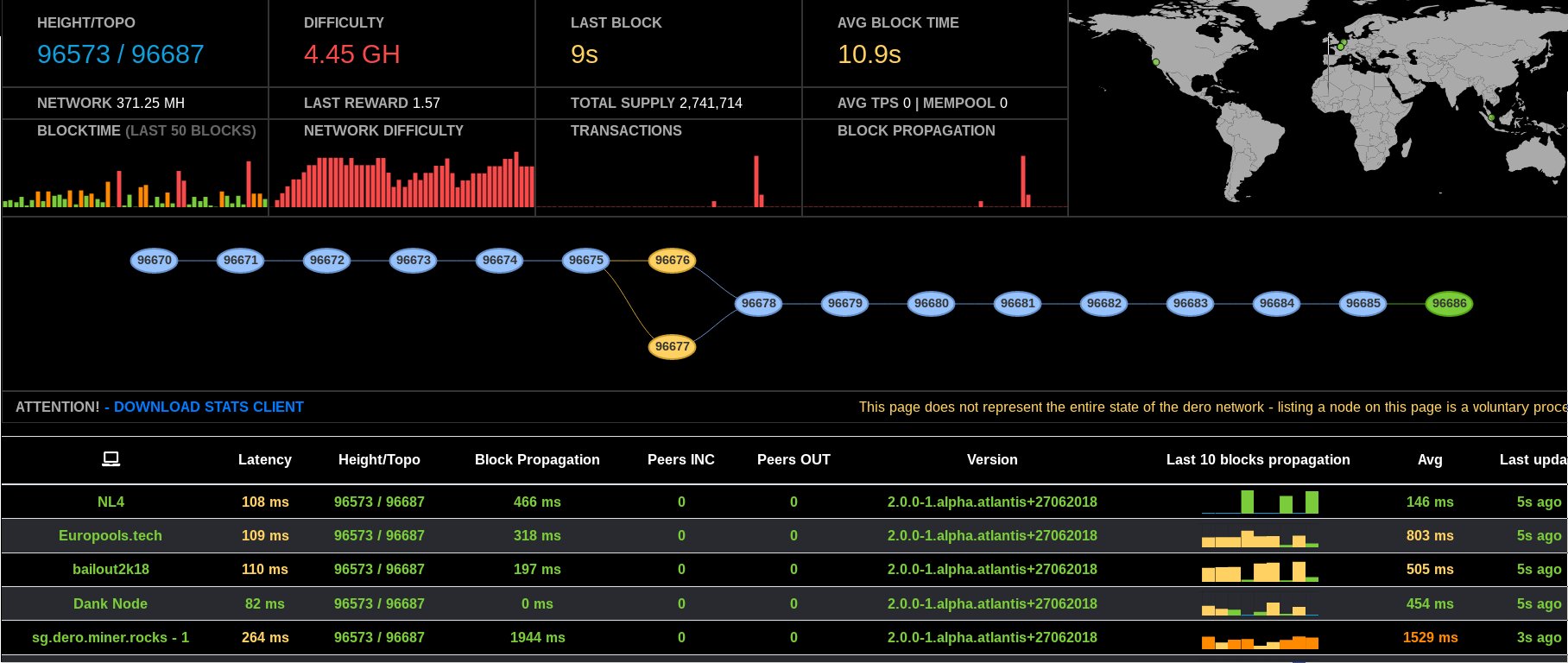
DERO Explorer is used to check and confirm transaction on DERO Network.
DERO users can run their own explorer on local machine and can browse on local machine port 8080.
 DERO EXPLORER Screenshot
DERO EXPLORER Screenshot
DERO blockchain is completely private, so anyone cannot view, confirm, verify any other's wallet balance or any transactions.
So to prove any transaction you require Tx private key and receiver address.
Tx private key can be obtained using get_tx_key command in dero-wallet-cli.
Enter the Tx private key and receiver address in DERO EXPLORER
 DERO Explorer Proving Transaction
DERO Explorer Proving Transaction