This project implements a text encryption and decryption system using a matrix-based encryption technique. This project serves as an educational and practical exploration of matrix-based encryption techniques, demonstrating the fundamental concepts of encryption and decryption in a user-friendly manner.
Clone the repository and copy the library your local project folder then include MatrixEncryptor.h. After that you need to implement Eigen to your project. From the given link, only the folder Eigen is required. After putting it to your project folder, from your Project's Property Pages, C/C++ -> General -> Additional Include Directories add Eigen folder's path.
Before getting started with Text Encryption With Linear Algebra, ensure that you have the following dependencies installed on your Linux system:
- g++ compiler
- Eigen library
To use the Text Encryption With Linear Algebra, follow these steps:
- Clone this repository
git clone git@github.com:farukalpay/TextEncryptionWithLinearAlgebra.git- Clone the repository of Eigen Library:
git clone https://gitlab.com/libeigen/eigen- Go inside the directory of Eigen Library and copy the directory Eigen into this repository
cp -r <path-to-Eigen-directory> <path-to-this-repo>- Use the Makefile to compile with make
make- Now you should see the executable in the directory of Text Encryption With Linear Algebra
-
Initialization:
-
Given an input string
$S$ of length$n$ , where$S = s_1 s_2 s_3 \ldots s_n$ , and each$s_i$ represents a character in the string.
Initialize an empty vector$\text{parsed}$ to store the ASCII integer representations of characters extracted from the input string$S$ . -
Consider the input string
$S = \text{"Hello World"}$ .
Initialize$\text{parsed} = []$ .
-
-
Token Extraction:
-
Extract tokens (words) from the input string
$S$ . Let$T_1, T_2, \ldots, T_m$ be the tokens extracted from$S$ , where$m$ is the number of tokens. -
Extract tokens:
$T_1 = \text{"Hello"}$ and$T_2 = \text{"World"}$ .
-
-
Character Processing for Token
$T_i$ :-
For each token
$T_i$ , consisting of characters$t_{i1}, t_{i2}, \ldots, t_{ik}$ , where$k$ is the length of the token:- Convert each character
$t_{ij}$ to its ASCII integer representation$a_{ij}$ . - Add each
$a_{ij}$ to end of the$parsed$ vector.
- Convert each character
-
Convert 'H' to ASCII integer
$72$ , 'e' to$101$ , 'l' to$108$ , 'l' to$108$ , 'o' to$111$ .
Add these integers to$\text{parsed}$ :$[72, 101, 108, 108, 111]$ .
-
-
Adding Space:
-
After processing each character in a token
$T_i$ , add a space character ' ' to the$parsed$ vector. -
Add a space ' ' to
$\text{parsed}$ .
-
-
End of Token:
-
Repeat steps 3-4 for all tokens
$T_1, T_2, \ldots, T_m$ . -
Process characters for
$T_2$ :- Convert 'W' to ASCII integer
$87$ , 'o' to$111$ , 'r' to$114$ , 'l' to$108$ , 'd' to$100$ . - Add these integers to
$\text{parsed}$ :$[87, 111, 114, 108, 100]$ . - Add a space ' ' to
$\text{parsed}$ .
- Convert 'W' to ASCII integer
-
-
Return Result:
-
The function returns the
$\text{parsed}$ vector containing ASCII integer representations of characters in$S$ , with spaces after each token. -
Return
$\text{parsed} = [72, 101, 108, 108, 111, 32, 87, 111, 114, 108, 100, 32]$ .
-
-
Initialization:
-
Let
$key$ be a square matrix of size$size \times size$ , represented as$key = [key_{ij}]$ where$i, j = 0, 1, \ldots, size - 1$ . -
Each element
$key_{ij}$ denotes a value in the key matrix. -
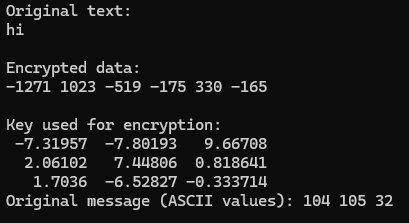
Consider the ASCII representation of the string
${\text{"hi"} + \text{Space (ASCII 32)}}$ , where the ASCII values are$[104, 105, 32]$ . Let$key$ be a square matrix of size$3 \times 3$
-
-
Random Number Generation Setup:
- Initialize a pseudo-random number generator with a random seed.
-
Uniform Distribution Setup:
- Define a uniform distribution to produce random numbers uniformly distributed between -10.0 and 10.0.
-
Random Key Generation:
- For each element
$key_{ij}$ of$key$ :- Sample a random value
$r_{ij}$ from the uniform distribution. - Assign
$r_{ij}$ as the value of$key_{ij}$ in the key matrix. - Mathematically,
$key_{ij} = r_{ij}$ for$i, j = 0, 1, \ldots, size - 1$ .
- Sample a random value
- For each element
-
Return the Key:
-
Once all elements of the matrix
$key$ have been assigned random values, return the resulting key matrix$key$ . -
Generated key matrix for
$[104, 105, 32]$ :
-
-
Message Padding:
-
Given a message
$M$ represented as a vector of integers$\text{message} = [m_1, m_2, \ldots, m_n]$ , where$n$ is the size of the message and$\text{size}$ is the size of the key matrix. -
Determine the remainder
$r$ when dividing the size of the message by the size of the key matrix:$r = \text{size} - (n \mod \text{size})$ . -
Pad the message with spaces to make its size a multiple of the size of the key matrix:
$M' = [m_1, m_2, \ldots, m_n, \underbrace{\text{space}, \text{space}, \ldots, \text{space}}_{r \text{ times}}]$ . -
The message
$\text{"hi"}$ corresponds to the vector$\text{message} = [104, 105, 32]$ . Since the size of the key matrix is 3, the message needs to be padded with spaces to make its size a multiple of$3$ . Thus, the padded message becomes$[104, 105, 32, 32, 32, 32]$ .
-
-
Message Vectorization:
-
Split the padded message
$M'$ into vectors of size$\text{size}$ :$\text{messageVector}_1, \text{messageVector}_2, \ldots, \text{messageVector}_k$ , where$k = \frac{n + r}{\text{size}}$ . -
Each
$\text{messageVector}_i$ is a column vector of size$\text{size}$ containing consecutive elements from$M'$ . -
Generated
$\text{messageVector}_i$ column matrices for$[104, 105, 32, 32, 32, 32]$ :
-
-
Encryption:
- For each message vector
$\text{messageVector}_i$ :- Perform matrix-vector multiplication with the key matrix
$K$ :$\text{encryptedVector}_i = K \cdot \text{messageVector}_i$ . - After performing the matrix-vector multiplication, the resulting elements in
$\text{encryptedVector}_i$ rounded to the nearest integer. - Each element of
$\text{encryptedVector}_i$ represents an encrypted value corresponding to the corresponding message vector element.
- Perform matrix-vector multiplication with the key matrix
- For each message vector
For
For
-
Result:
-
Concatenate all elements of the encrypted vectors to form the encrypted message
$E$ :$E = [\text{encryptedVector}_1[1], \text{encryptedVector}_1[2], \ldots, \text{encryptedVector}_k[\text{size}], \ldots]$ . -
The resulting encrypted message corresponding to the input
$\text{"hi"}$ encrypted using this key matrix is:
-
-
Initialization:
-
Let
$\text{EncryptedMessage} = [e_1, e_2, \ldots, e_n]$ be the encrypted message represented as a vector of integers, where$n$ is the size of the encrypted message. -
Consider the encrypted message
${E = [-241, 272, -740, -161, -30, -142]}$ -
Key matrix
$K$ used for encryption:
-
-
Segmentation:
-
Divide the encrypted message into segments, each consisting of
$\text{size}$ elements, where$\text{size}$ is the size of the key matrix$K$ . -
Segments of the encrypted message, denoted as
$\text{Segment}_i$ , are obtained by splitting$\text{EncryptedMessage}$ into$\frac{n}{\text{size}}$ segments, where$i$ ranges from$1$ to$\frac{n}{\text{size}}$ . -
Each segment
$\text{Segment}_i$ consists of$\text{size}$ consecutive elements starting from index$i \times \text{size}$ . -
Each segment
$\text{Segment}_i$ is represented as a column matrix of size$\text{size}$ :
-
- Segmented column matrices for
${E = [-241, 272, -740, -161, -30, -142]}$ :
-
Matrix Multiplication:
- For each segment
$\text{encryptedVector}_i$ :- Perform matrix-vector multiplication with the inverse key matrix
$K^{-1}$ :$\text{decryptedVector}_i = K^{-1} \cdot \text{encryptedVector}_i$ - After performing the matrix-vector multiplication, the resulting elements in
$\text{decryptedVector}_i$ rounded to the nearest integer. - Each element of
$\text{decryptedVector}_i$ represents an decrypted ASCII value corresponding to the corresponding message vector element.
- Perform matrix-vector multiplication with the inverse key matrix
- For each segment
For
For
-
Result:
-
Concatenate all elements of the decrypted message vectors to form the decrypted message
$D$ :$D = [\text{decryptedVector}_1[1], \text{decryptedVector}_1[2], \ldots, \text{decryptedVector}_k[\text{size}], \ldots]$ . The resulting decrypted message is a sequence of ASCII characters obtained by converting each integer in$D$ to its corresponding ASCII character. -
The resulting decrypted message corresponding to the encrypted message
${E = [-241, 272, -740, -161, -30, -142]}$ decrypted using the key matrix is:
-
The decrypted message