-
Notifications
You must be signed in to change notification settings - Fork 737
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
A/B testing support for Gloo Edge ingress controller #758
Closed
+842
−457
Closed
Changes from all commits
Commits
Show all changes
16 commits
Select commit
Hold shift + click to select a range
4cf057b
Small docs fixes
kdorosh ffc1442
Initial commit
kdorosh e94353c
Add route table codegen
kdorosh c6bc21b
Update gloo logic to use route tables, cleanup
kdorosh f187d86
Add permissions
kdorosh 87c57fe
Fix api mistakes
kdorosh a88f4ae
Fix compile error
kdorosh 107113f
Fix test
kdorosh 250df0e
Fix json naming
kdorosh d063db6
Update documented flow
kdorosh ea53160
First pass A/B testing
kdorosh 657e2ef
Update to use new Gloo Edge 1.6 API
kdorosh 0085ccf
Remove dated comment
kdorosh f3b0581
Fix rebase
kdorosh 130bd3a
Guide is working
kdorosh 3bc8a02
We are generating 404s not 400s
kdorosh File filter
Filter by extension
Conversations
Failed to load comments.
Loading
Jump to
Jump to file
Failed to load files.
Loading
Diff view
Diff view
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,12 +1,15 @@ | ||
| # Gloo Canary Deployments | ||
|
|
||
| This guide shows you how to use the [Gloo](https://gloo.solo.io/) ingress controller and Flagger to automate canary deployments. | ||
| This guide shows you how to use the [Gloo Edge](https://gloo.solo.io/) ingress controller and Flagger to automate canary deployments. | ||
|
|
||
| 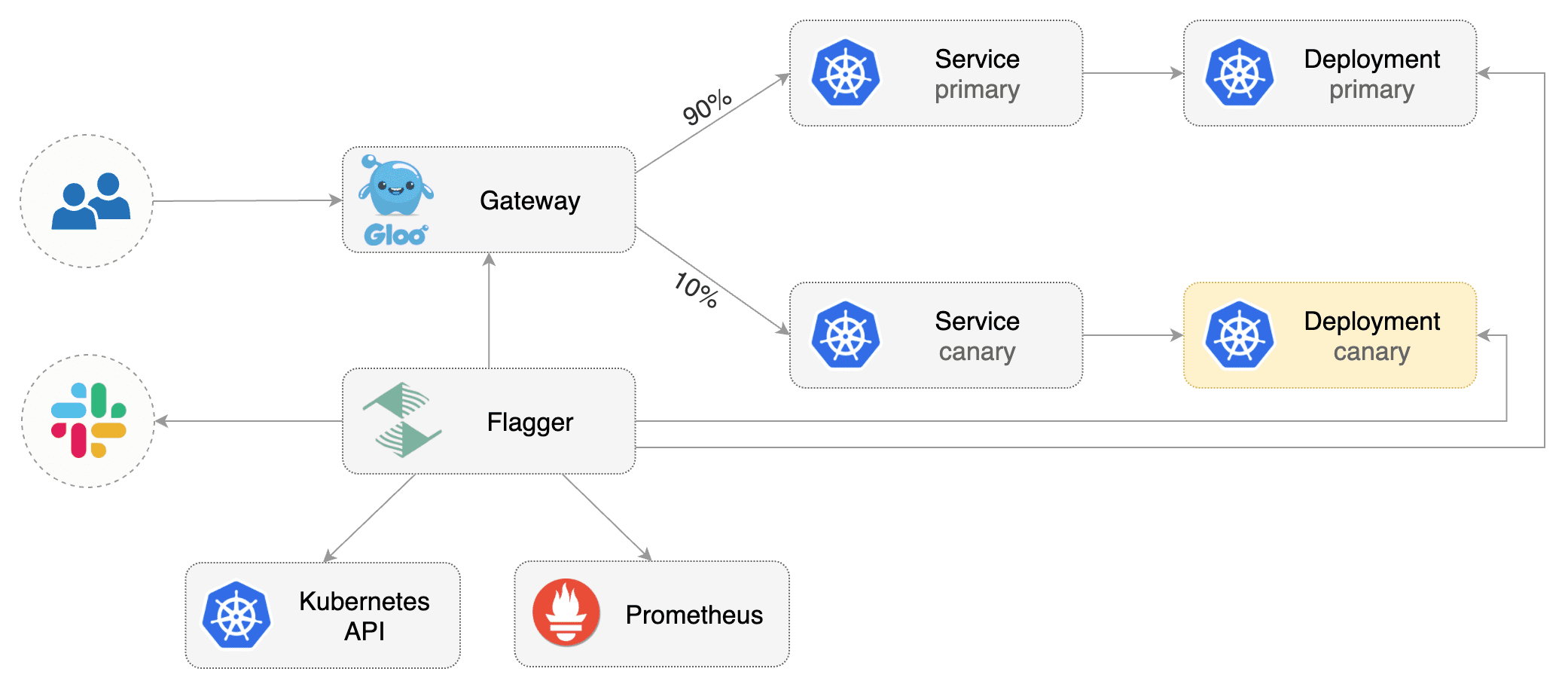 | ||
|
|
||
| ## Prerequisites | ||
|
|
||
| Flagger requires a Kubernetes cluster **v1.11** or newer and Gloo ingress **1.3.5** or newer. | ||
| This guide was written for Flagger version **1.5.0** or higher. Prior versions of Flagger used Gloo upstream groups to handle | ||
| canaries, but newer versions of Flagger use Gloo route tables to handle canaries as well as A/B testing. | ||
|
|
||
| Flagger requires a Kubernetes cluster **v1.11** or newer and Gloo Edge ingress **1.6.0** or newer. | ||
|
|
||
| Install Gloo with Helm v3: | ||
|
There was a problem hiding this comment. Choose a reason for hiding this commentThe reason will be displayed to describe this comment to others. Learn more. note, the guide will not work as written until 1.6.0 is released in two weeks, as I can provide the |
||
|
|
||
|
|
@@ -31,7 +34,7 @@ helm upgrade -i flagger flagger/flagger \ | |
| ## Bootstrap | ||
|
|
||
| Flagger takes a Kubernetes deployment and optionally a horizontal pod autoscaler (HPA), | ||
| then creates a series of objects (Kubernetes deployments, ClusterIP services and Gloo upstream groups). | ||
| then creates a series of objects (Kubernetes deployments, ClusterIP services and Gloo route tables). | ||
| These objects expose the application outside the cluster and drive the canary analysis and promotion. | ||
|
|
||
| Create a test namespace: | ||
|
|
@@ -52,7 +55,7 @@ Deploy the load testing service to generate traffic during the canary analysis: | |
| kubectl -n test apply -k github.com/weaveworks/flagger//kustomize/tester | ||
| ``` | ||
|
|
||
| Create an virtual service definition that references an upstream group that will be generated by Flagger | ||
| Create a virtual service definition that references a route table that will be generated by Flagger | ||
| (replace `app.example.com` with your own domain): | ||
|
|
||
| ```yaml | ||
|
|
@@ -68,8 +71,8 @@ spec: | |
| routes: | ||
| - matchers: | ||
| - prefix: / | ||
| routeAction: | ||
| upstreamGroup: | ||
| delegateAction: | ||
| ref: | ||
| name: podinfo | ||
| namespace: test | ||
| ``` | ||
|
|
@@ -168,7 +171,7 @@ horizontalpodautoscaler.autoscaling/podinfo-primary | |
| service/podinfo | ||
| service/podinfo-canary | ||
| service/podinfo-primary | ||
| upstreamgroups.gloo.solo.io/podinfo | ||
| routetables.gateway.solo.io/podinfo | ||
| ``` | ||
|
|
||
| When the bootstrap finishes Flagger will set the canary status to initialized: | ||
|
|
@@ -252,13 +255,13 @@ podinfod=stefanprodan/podinfo:3.1.2 | |
| Generate HTTP 500 errors: | ||
|
|
||
| ```bash | ||
| watch curl -H 'Host: app.example.com' http://gateway-proxy-v2.gloo-system/status/500 | ||
| watch curl -H 'Host: app.example.com' http://gateway-proxy.gloo-system/status/500 | ||
| ``` | ||
|
|
||
| Generate high latency: | ||
|
|
||
| ```bash | ||
| watch curl -H 'Host: app.example.com' http://gateway-proxy-v2.gloo-system/delay/2 | ||
| watch curl -H 'Host: app.example.com' http://gateway-proxy.gloo-system/delay/2 | ||
| ``` | ||
|
|
||
| When the number of failed checks reaches the canary analysis threshold, the traffic is routed back to the primary, | ||
|
|
@@ -353,7 +356,7 @@ podinfod=stefanprodan/podinfo:3.1.3 | |
| Generate 404s: | ||
|
|
||
| ```bash | ||
| watch curl -H 'Host: app.example.com' http://gateway-proxy.gloo-system/status/400 | ||
| watch curl -H 'Host: app.example.com' http://gateway-proxy.gloo-system/status/404 | ||
| ``` | ||
|
|
||
| Watch Flagger logs: | ||
|
|
||
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,5 +1,5 @@ | ||
| package gloo | ||
|
|
||
| const ( | ||
| GroupName = "gloo.solo.io" | ||
| GroupName = "gateway.solo.io" | ||
| ) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,5 +1,5 @@ | ||
| // +k8s:deepcopy-gen=package | ||
|
|
||
| // Package v1 is the v1 version of the API. | ||
| // +groupName=gloo.solo.io | ||
| // +groupName=gateway.solo.io | ||
| package v1 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
Oops, something went wrong.
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
How does flagger versioning work? According to semver this is a new feature, so I put 1.5.0 here; please let me know what to put if that's not accurate.