-
-
Notifications
You must be signed in to change notification settings - Fork 5.7k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Migrating: Auth token is not properly protected in frontend #22174
Labels
topic/security
Something leaks user information or is otherwise vulnerable. Should be fixed!
type/enhancement
An improvement of existing functionality
Comments
silverwind
added a commit
to silverwind/gitea
that referenced
this issue
Mar 17, 2023
|
Let's reduce to one issue and move this to #22175. |
|
Actually, sorry I see the other is acutally the PR. |
h3xx
added a commit
to h3xx/gitea
that referenced
this issue
Mar 18, 2023
Seen when migrating from other hosting platforms. 1. Prevents exposing the token to screen capture/cameras/eyeballs. 2. Prevents the browser from saving the value in its autocomplete dictionary, which often is not secure. Closes go-gitea#22174 Signed-off-by: Dan Church <amphetamachine@gmail.com>
techknowlogick
pushed a commit
that referenced
this issue
Apr 23, 2023
Set `type="password"` on all `auth_token` fields Seen when migrating from other hosting platforms. 1. Prevents exposing the token to screen capture/cameras/eyeballs. 2. Prevents the browser from saving the value in its autocomplete dictionary, which often is not secure. 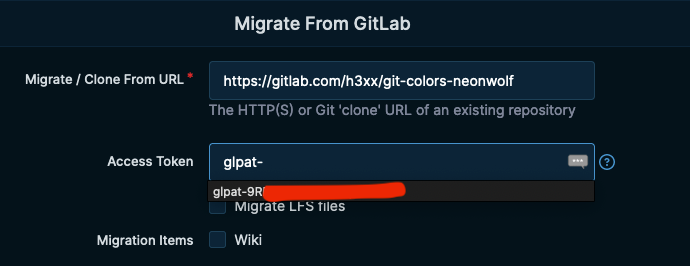 Closes #22174 --------- Signed-off-by: Dan Church <amphetamachine@gmail.com> Co-authored-by: silverwind <me@silverwind.io>
Sign up for free
to subscribe to this conversation on GitHub.
Already have an account?
Sign in.
Labels
topic/security
Something leaks user information or is otherwise vulnerable. Should be fixed!
type/enhancement
An improvement of existing functionality
Description
The migration form exposes the auth token to screen capture/cameras/eyeballs.
Browsers also pick this up, adding it to their auto complete dictionary.
Note: I already have a fix for this, I just wanted an issue to reference.
Gitea Version
2774671
Can you reproduce the bug on the Gitea demo site?
Yes
Log Gist
No response
Screenshots
Git Version
No response
Operating System
No response
How are you running Gitea?
Reproducible on try.gitea.io, so however that's running.
Database
None
Notes from other discussions:
I see this as needing replacement with a password input with an eyeball to hide/show the password. E.g.:
But I'm not sure what the best way to implement that in the current Gitea project is (or if the input type is already implemented elsewhere and I just need to pull it in). Anything I'd do, I'd want to make reusable.
The text was updated successfully, but these errors were encountered: