-
Notifications
You must be signed in to change notification settings - Fork 9.6k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
macOS Catalina error: “terraform” cannot be opened because the developer cannot be verified. #23033
Comments
|
Apparently, the workaround is quite painful:
The app is saved as an exception to your security settings, and you can open it in the future by double-clicking it or from cli, just as you can with any authorised app. |
|
Hi @roura356a! Thanks for reporting this. Indeed the new version of MacOS is stricter about running software you've downloaded that isn't signed with an Apple developer key. Terraform distributions are signed with a HashiCorp key with signatures distributed out of band on Thank you for sharing your workaround. We're looking into the best way to proceed here to see if we can make this work better. |
|
|
@EmpireJones Is there a way to do it for a specific app only? |
|
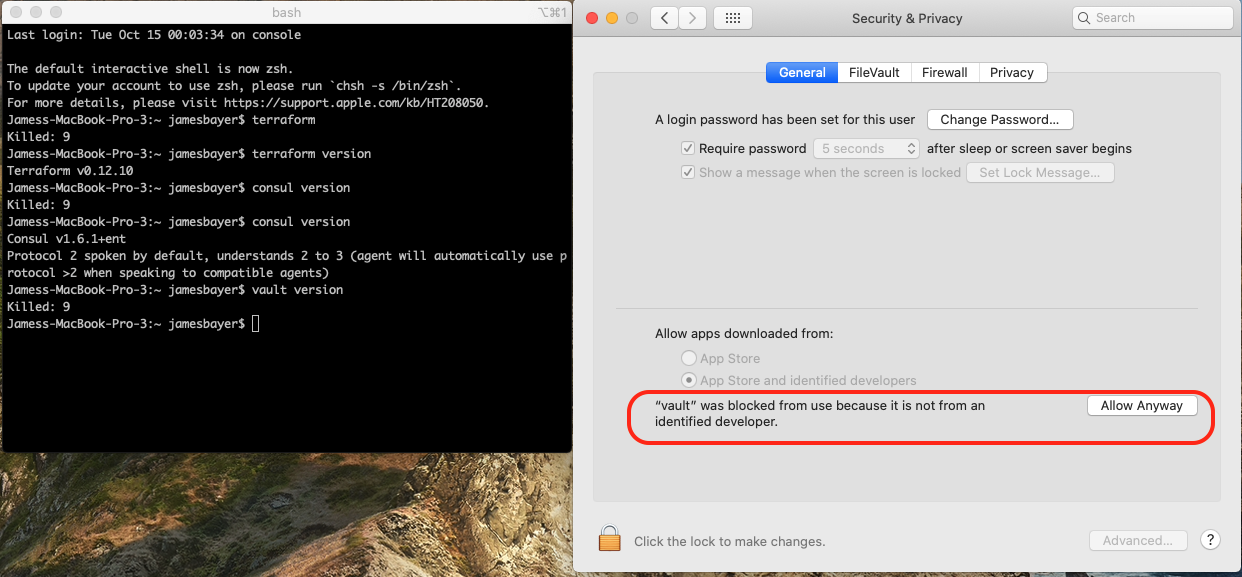
Another simpler way is to go to System Preferences -> Security & Privacy -> General and enable any blocked app from Allow apps downloaded from pane at the bottom of the window. |
|
@aprofromindia agreed, just like it always worked in Mac OS when you had security settings. Whenever an app is blocked. You just have to allow them there. |
|
Removing existing terraform executable and installing it with |
This does not appear to be available in Catalina.
This does work. |
|
This is affecting all HashiCorp binaries on Catalina. We are looking into the macOS notarizing process to no longer require these work-arounds on Catalina. We will provide an update when we learn more about this. Here is the process I used to run the existing binaries on Catalina that does not require control-click. First I open the "Security & Privacy" control panel from System Preferences.
|
|
Had a similar issue with The simple answer that @roura356a shared worked for me (just Good to know there are other workarounds too. Thanks for the wonderful and generally applicable workarounds! |
|
Same issue with 0.12.12 |
|
Argh! Same with latest Java (version 13.0.1) |
|
The only solution that worked for me is to delete the |
|
I've learned a bit more about this. The
|
This works, thanks a lot. |
|
@roura356a It is worked, pretty cool! thx. |
|
Hi all! Good news! HashiCorp release engineering has been working hard on getting a process build for OS X Catalina release notarization. We're planning on using this process for the upcoming Terraform 0.12.18 release, which is tentatively scheduled for Wednesday December 11th. Before then, we'd appreciate your help confirming that our signed binaries work in your environment. We've built an 0.12.18 pre-release solely for the sake of verifying that Catalina code notarization is working. I do not recommend using this build for production use - it's just for the sake of validating that we've added Apple notarization to the release process correctly. Here's the output of codesign on the terraform binary in that attached zip: If you care about this issue, please download that zip, run it on your Catalina OS X machine, and let us know here if you run into notarization issues. If we don't get any negative feedback here, we'll move forward and start notarizing future terraform releases starting on 0.12.18. And, again, when you're done please do not use this as 0.12.18 - throw it away when you're done and don't install it permanently. |
|
I downloaded 0.12.18 pre-release and tried getting it to run on my MacOS w/Catalina and I still get no response. I did update my XCode Tools before this so that I can get the Developer Tools icon to show up in the Security & Privacy dialog in the Privacy window based on the post above. I also clicked Agree to allow the terraform app to run even though it is an application purchased through the App Store. So after doing all the above, I open a new terminal window and navigate to the downloaded terraform app (already unzipped) and try to run it and it just hangs; no response. I voted down the post above indicating my issue with the terraform cli is not fixed with this release. I kinda need to get this working, I would have to have to roll back just to use terraform. |
Sorry you're still having issues with this. Do you have time for a screenshare so we can help sort this out? You can reach me at mdegges@hashicorp.com. Edit: Below are the steps you can use to test the 0.12.18 pre-release binary
|
|
Update: I uninstalled all the versions of terraform and reinstalled it using Brew and it installed this version: https://homebrew.bintray.com/bottles/terraform-0.12.17.catalina.bottle.tar.gz And it worked perfectly. |
Followed these steps and received no prompt. Everything worked as expected. |
|
@danieldreier When can we expect this pre-release to become an actual release? The notarization process seems to works fine. Is it possible to make a release with this ASAP? |
|
@sanspace We're planning a release this week! We know people are eager to have this 😄 |
|
|
|
Terraform 0.12.18 has been released with a notarized binary for OS X 10.15+: https://github.com/hashicorp/terraform/releases/tag/v0.12.18 A huge thanks to the community for your help and patience. From the changelog: NOTES:
|
|
This is really awesome. Sorry for commenting a closed issue, but @pkolyvas - does this apply to providers as well, or is only Terraform core signed...? The reason I'm asking is, the providers seem to be executing as different binaries. Some security software on Windows/Macs tend to block terraform - and not having signed binaries has been a painful issue also on those before, hence the question. |
Are you running into any errors trying to use the providers with the latest terraform core release? Testing with the AWS and GCP providers on my end doesn't reveal any errors, but we're happy to help troubleshoot if you can send over repro steps. |
I need to test this with our company's IT support to see how this works or not. Let's see... What I've understood is, it is the provider binary (AWS as an example) which would communicate with AWS APIs. hence I think the provider binary should also be signed so it could be whitelisted. |
|
@iiro my understanding of the way MacOS new protections work is that specified MacOS programs (such as web browsers like Chrome, Safari, Firefox) will add file system extended attributes like However, the typical terraform workflow the standard terraform binary that is signed will download the providers and does not add the file system extended attributes for the provider binaries that it downloads. That's why I think this worked in @mdeggies example. |
|
Friendly reminder that this is a closed issue and will be locked eventually -- any new issues should be reported as such (but it seems like what has followed has generally been discussion). Please open a new issue for any existing, or emergent, issues related to this, but the original issue is closed. |
Good one... |
|
I'm going to lock this issue because it has been closed for 30 days ⏳. This helps our maintainers find and focus on the active issues. If you have found a problem that seems similar to this, please open a new issue and complete the issue template so we can capture all the details necessary to investigate further. |

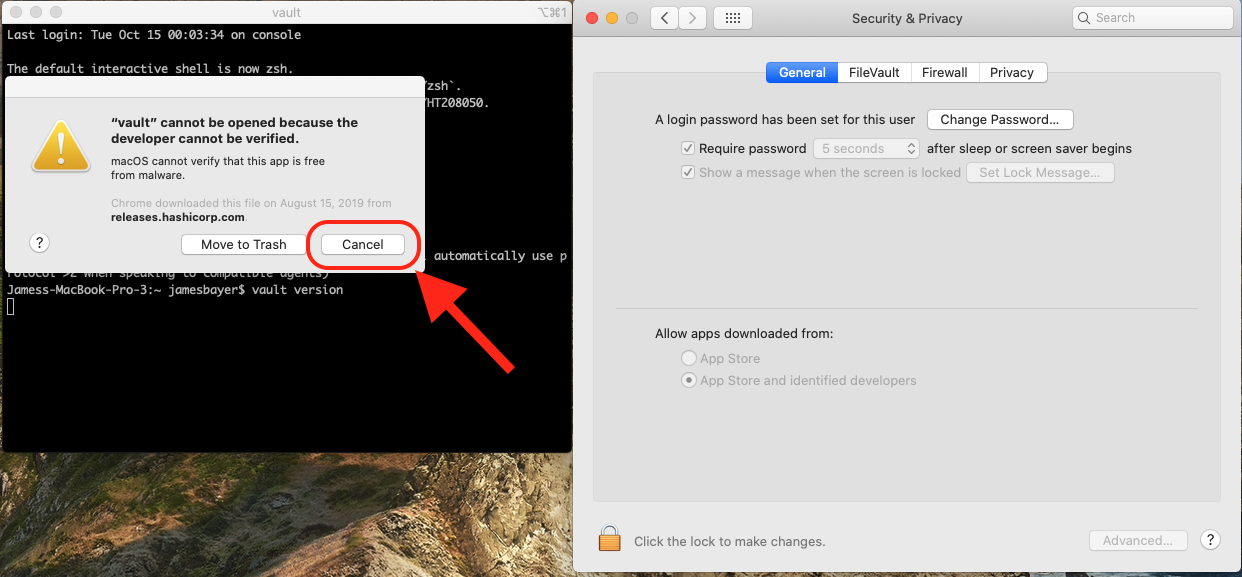




Terraform Version
Expected Behavior
It should run.
Actual Behavior
Steps to Reproduce
Run any terraform command.
The text was updated successfully, but these errors were encountered: