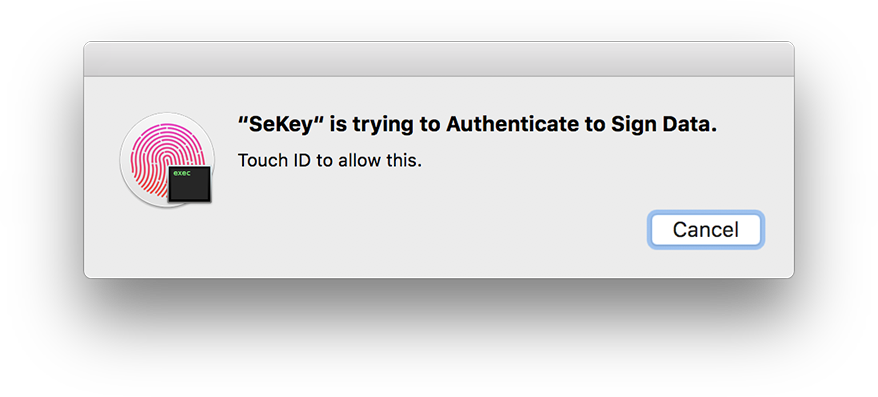
SeKey is a SSH Agent that allow users to authenticate to UNIX/Linux SSH servers using the Secure Enclave
The Secure Enclave is a hardware-based key manager that’s isolated from the main processor to provide an extra layer of security. When you store a private key in the Secure Enclave, you never actually handle the key, making it difficult for the key to become compromised. Instead, you instruct the Secure Enclave to create the key, securely store it, and perform operations with it. You receive only the output of these operations, such as encrypted data or a cryptographic signature verification outcome.
- Only support MacBook Pro with the Touch Bar and Touch ID
- Can’t import preexisting key
- Stores only 256-bit elliptic curve private key
Homebrew
Unfortunately, I can't make a Homebrew formula because KeyChain API requires entitlements, so the binary has to be signed to work, still you can use Homebrew Cask
Homebrew Cask
- Install Sekey
brew cask install sekey- Append the following line to your
~/.bash_profileor~/.zshrc
export SSH_AUTH_SOCK=$HOME/.sekey/ssh-agent.sshor
- Add the following line you your
~/.ssh/configor/etc/ssh/ssh_config
IdentityAgent ~/.sekey/ssh-agent.ssh
Pkg Installer
- Go to Releases and download the pkg release
- Install the application using the pkg.
- Set enviroment variables and fix the path of sekey folder.
export PATH=$PATH:/Applications/SeKey.app/Contents/MacOS
export SSH_AUTH_SOCK=$HOME/.sekey/ssh-agent.ssh
Manual Installation
- Go to Releases and download the zip release
- Place the App in the Applications folder.
- Go to ~/Library/LaunchAgents
- Create the file com.ntrippar.sekey.plist
- Paste the following into the file and fix the path of the sekey binary:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>com.ntrippar.sekey</string>
<key>ProgramArguments</key>
<array>
<string>/absolute/path/to/SeKey.app/Contents/MacOS/sekey</string>
<string>--daemon</string>
</array>
<key>StandardErrorPath</key>
<string>/dev/null</string>
<key>StandardOutPath</key>
<string>/dev/null</string>
<key>KeepAlive</key>
<true/>
</dict>
</plist>
- Fix permissions
chown youruser:staff /absolute/path/to/SeKey.app/Contents/MacOS/sekey- Load the agent to the user account:
launchctl load -F ~/Library/LaunchAgents/com.ntrippar.sekey.plist- Set enviroment variables and fix the path of sekey folder.
export PATH=$PATH:/path/to/SeKey.app/Contents/MacOS
export SSH_AUTH_SOCK=$HOME/.sekey/ssh-agent.ssh
For the help menu:
ntrippar@macbookpro:~% sekey -h
SeKey 1.0
Nicolas Trippar <ntrippar@gmail.com>
Use Secure Enclave for SSH Authentication
USAGE:
sekey [FLAGS] [OPTIONS]
FLAGS:
--daemon Run the daemon
-h, --help Prints help information
--list-keys List all keys
-V, --version Prints version information
OPTIONS:
--delete-keypair <ID> Deltes the keypair
--export-key <ID> export key to OpenSSH Format
--generate-keypair <LABEL> Generate a key inside the Secure EnclaveExamples
Create KeyPair inside the Secure Enclave:
ntrippar@macbookpro:~% sekey --generate-keypair "Github Key"
Keypair Github Key sucessfully generated
List keys in the secure enclave:
ntrippar@macbookpro:~% sekey --list-keys
┌────────────────────┬──────────────────────────────────────────────────┐
│ Label │ ID │
├────────────────────┼──────────────────────────────────────────────────┤
│ Github Key │ d179eb4c2d6a242de64e82240b8b6e611cf0d729 │
└────────────────────┴──────────────────────────────────────────────────┘Export public key to OpenSSH format:
ntrippar@macbookpro:~% sekey --export-key d179eb4c2d6a242de64e82240b8b6e611cf0d729
ecdsa-sha2-nistp25 AAAAEmVjZHNhLXNoYTItbmlzdHAyNQAAAAhuaXN0cDI1NgAAAEEE8HM7SBdu3yOYkmF0Wnj/q8t2NJC6JYJWZ4IyvkOVIeUs6mi4B424bAjhZ4Awgk5ax9r25RB3Q8tL2/7J/3xchQ==Delete Keypair:
ntrippar@macbookpro:~% sekey --delete-keypair d179eb4c2d6a242de64e82240b8b6e611cf0d729
Key d179eb4c2d6a242de64e82240b8b6e611cf0d729 sucessfully deletedUse key for a specific host:
- export the public key from sekey and save it to a file
ntrippar@macbookpro:~% sekey --export-key d179eb4c2d6a242de64e82240b8b6e611cf0d729 > ~/.ssh/example.com.pub- on the ssh config file located in
~/.ssh/configwe should add a entry so the ssh only query that key for the given host
Host example.com
IdentityFile ~/.ssh/example.com.pub
IdentitiesOnly yes
Build
Sekey is built with Cargo, the Rust package manager.
git clone https://github.com/ntrippar/sekey
cd sekey
cargo build --releaseSign
SeKey utilizes the KeyChain API on MacOS, for using it the app needs to be signed and have the correct entitlements.
You need to change the sign parameter to match your own signing key
Listing keys
security find-identity -v -p codesigningSign
codesign --force --identifier "com.ntrippar.sekey" --sign "Developer ID Application: Nicolas Trippar (5E8NNEEMLP)" --entitlements ./assets/sekey.entitlements --timestamp=none ./bundle/SeKey.appPackage
cp ./target/release/sekey ./bundle/Applications/SeKey.app/Contents/MacOS/sekeyif needed to create a pkg installer
pkgbuild --analyze --root ./bundle/ SeKey.plist
pkgbuild --sign "Developer ID Installer: Nicolas Trippar (5E8NNEEMLP)" --identifier com.ntrippar.sekey --root ./bundle/ --scripts ./install-scripts --component-plist ./Sekey.plist ./sekey.pkgMembers of the open-source community are encouraged to submit pull requests directly through GitHub.