-
Notifications
You must be signed in to change notification settings - Fork 36
New Accounts Approval
You want manager to approve every new account before it will be created in AD to save on licenses costs.
You want another approval from responsible person for every new mailbox after account is created to save on licenses costs.
When employees’ data is imported from HR then no AuthZ workflows are executed as all requests from FIM/MIM Sync submitted to FIM/MIM Service using FIM/MIM MA account bypass authorization stage, thus you can’t put approvals for any requests from FIM/MIM Sync to FIM/MIM Service.
In some cases you want to create AD accounts with manager approval (to save some licenses, for example, or when not every person needs an account).
Normally, you can set up authorization workflow and have such an approval for request submitted via FIM/MIM portal. However, when you have an external source for such a data like HR DB and requests are coming to FIM/MIM Service from FIM/MIM Sync, you cannot have such a policy being applied as all requests from FIM/MIM Sync will bypass authorization stage.
As a solution, you may want to add a boolean attribute ProvisionToAD to FIM/MIM Service Schema and change your synchronization rule to be applied only for users with this attribute set to true. Then add this attribute to Administrator filter permissions to enable filtering by this attribute.
Unfortunately, if you just try to modify this attribute using any workflow activity (except MIMWAL's update resource activity) then your request will not hit authorization stage and approval will not happen.
To solve this you may use Update Resource activity with apply auth policies flag set to true.
First, create a set !new users without AD accounts with criteria Provision to AD is not True (no users will be in this set until you or someone/something will set this attribute to false or unset/null/clear).

Second, create an action workflow AD: submit request to approve an account. Add Update Resources activity. Configure it as depicted below (mind Apply Authorization policy option checked):

The Actor Account Name contains a special service account you create in advance in FIM/MIM Service. MIMWAL will use this identity to submit requests to set ProvisionToAD attribute to true causing AuthZ policies to be applied. This in turn means that there must be another policy granting permissions to make such updates to this account.
So, you simply create a regular policy !AD: approve requests from FIM Agent - new accounts which grants permissions and asks a manager for approval.


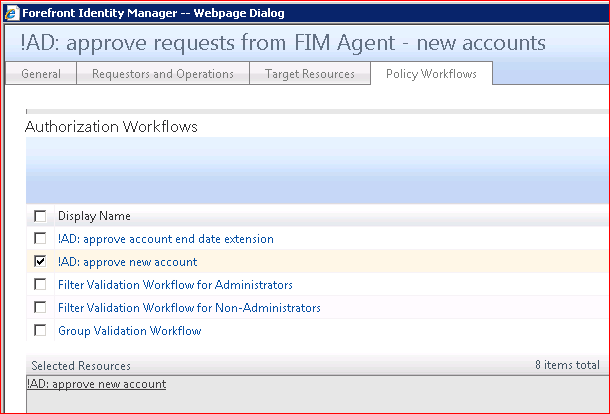

After that, create a transition IN policy !AD: make a request to approve an account to execute a workflow !AD: submit request to approve an account when any new user appears on a portal.


If a manager will not approve this request and an account will not be created in AD, you may use admin access to set this attribute to true manually.
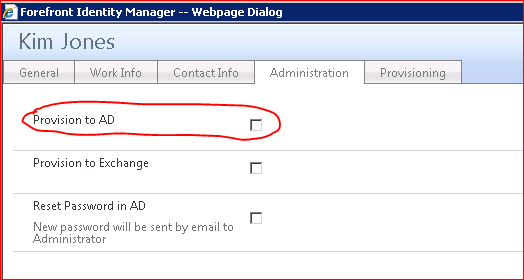
You may also extend criteria for !new users without AD accounts set and add other conditions to request account for specific users only while having everyone on a portal.
In some cases, you may need to provision AD accounts without mailboxes and request mailboxes for specific set of users with manager approval.
Extend the FIM/MIM Service schema and add ProvisionToExchange Boolean attribute.
Do not export mailnickName in default AD: OSR: provision new users sync rule, instead, create one more outbound sync rule AD: OSR: create a mailbox scoped to ProvisionToExchange equal true.

Your goal is to apply this sync rule to a user after manager approval.
Use the same technique as described above for AD accounts to create another workflow to submit requests to set ProvisionToExchange to true, have another transition IN policy to initiate such requests and have another policy to collect approvals.


- MIMWAL Site - http://aka.ms/MIMWAL
- MIMWAL Releases - http://aka.ms/MIMWAL/Releases
- MIMWAL Documentation Wiki - http://aka.ms/MIMWAL/Wiki
- MIMWAL FAQ - http://aka.ms/mimwal/faq
- MIMWAL GitHub Code Repo - http://aka.ms/MIMWAL/Repo
- MIMWAL TechNet Q&A Forum (now read-only) - http://aka.ms/MIMWAL/Forum