-
Notifications
You must be signed in to change notification settings - Fork 22
Use case 2 executable file embedded in RTF file
In this use case, a malicious RTF file with embedded executable file is analyzed. This RTF files exploits an old Microsoft Office vulnerability (CVE-2012-0158) and does not work on dynamic analysis with patched Microsoft Word. FileInsight-plugins can extract malware executable file from the RTF file to analyze it.
Open the RTF file with FileInsight.

While scrolling down, It is found that suspicious binary data is embedded from offset 0x2200.

There is sequence of bytes from 0x00 to 0xff at the end of the file. It is assumed that a malware executable file is embedded into the file and its content is XORed while incrementing XOR key (rolling XOR).

Use "Byte histgram" plugin to check byte frequency.
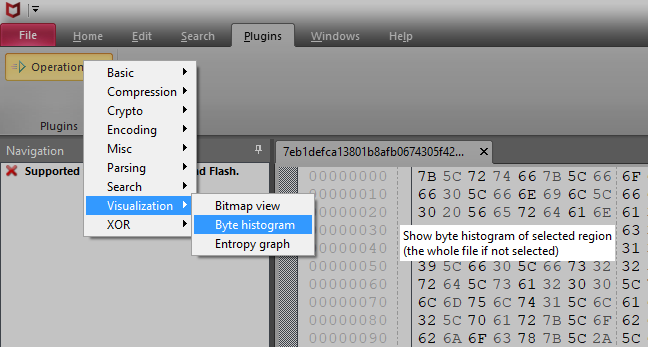
0x30 ("0") and 0x46 ("F") are frequently appeared in this file.
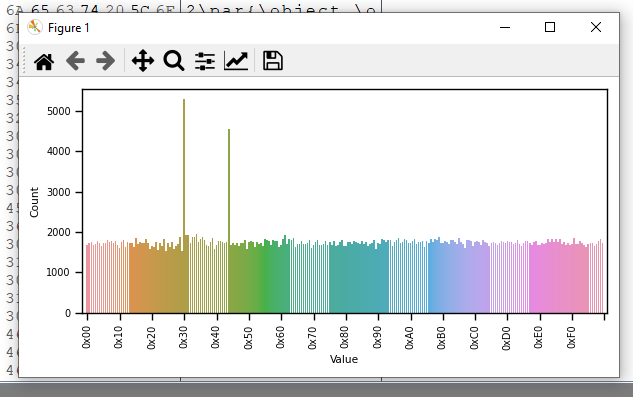

"Guess multibyte XOR keys" plugin can be used to defeat rolling XOR. This plugin guesses XOR keys based on revealed XOR keys (XORed with 0x00 of original file).

Guessed XOR key are shown as follows and the first XOR key can decode embedded 32 bit Windows DLL file and OLE2 Compound Document (old Microsoft Office document format).

And found files are bookmarked.

Hit Ctrl-A to select the whole file, copy the XOR key and paste it to the Decode tab in the left pane. Then click the Decode buttion.

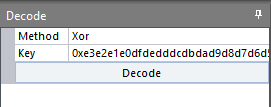
The whole file content is decoded. Jump to the first embedded file at offset 0x2233 by clicking a bookmark in the left pane. The embedded Windows DLL file is successfully decoded.

Click the bookmark of the DLL file to select its region, then use "Copy to new file" plugin to extract the region as new file.
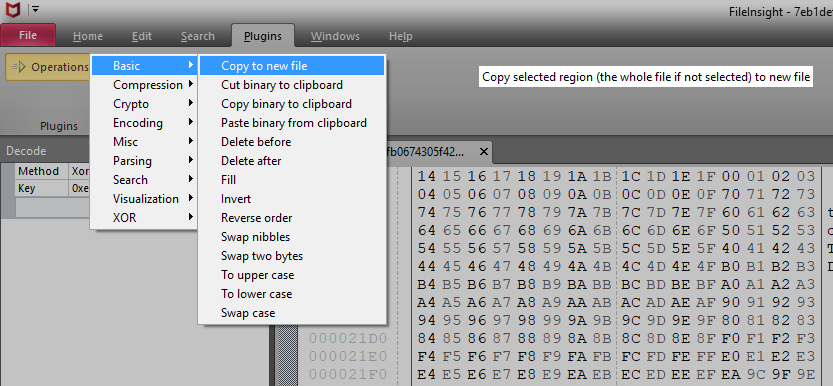

Use "File type" plugin to confirm its file type.
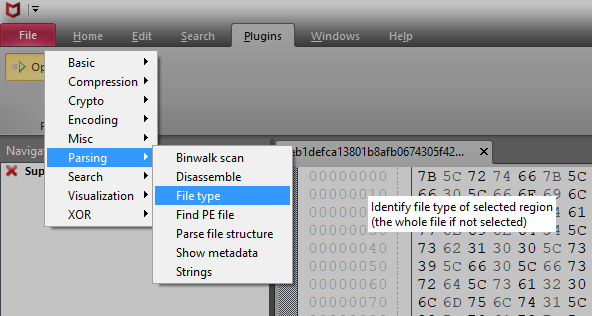
The plugin shows its file type as "PE32 executable (DLL) (GUI) Intel 80386, for MS Windows".

Use "Hash values" plugin to calculate hash values of the DLL file.

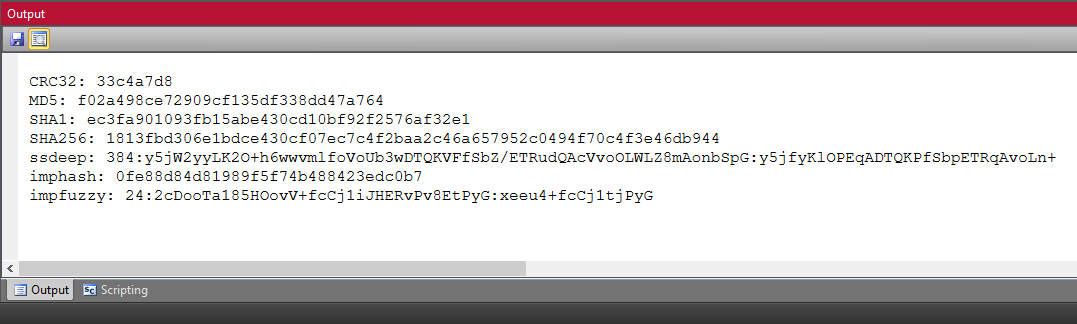
Save the DLL file and it is possible to proceed further analysis. You can defeat rolling XOR with FileInsight-plugins! 😁
MD5: 61be158fb2e20fbf5437e0deec6307aa
SHA1: bbb857110cc9dcf374be331bf4c2ff921e0c2469
SHA256: 7eb1defca13801b8afb0674305f4292aa9f2f80f295f8c7ff135d887ad477b64
ssdeep: 12288:+B5J48HGSbr00IENexEZzpJ9qTOuM5MNDoYnE:9kGr0IExzpJ9qO15MGYnE