-
Notifications
You must be signed in to change notification settings - Fork 30.5k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
process: upgrade process.binding to runtime deprecation #37485
Conversation
Signed-off-by: James M Snell <jasnell@gmail.com>
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
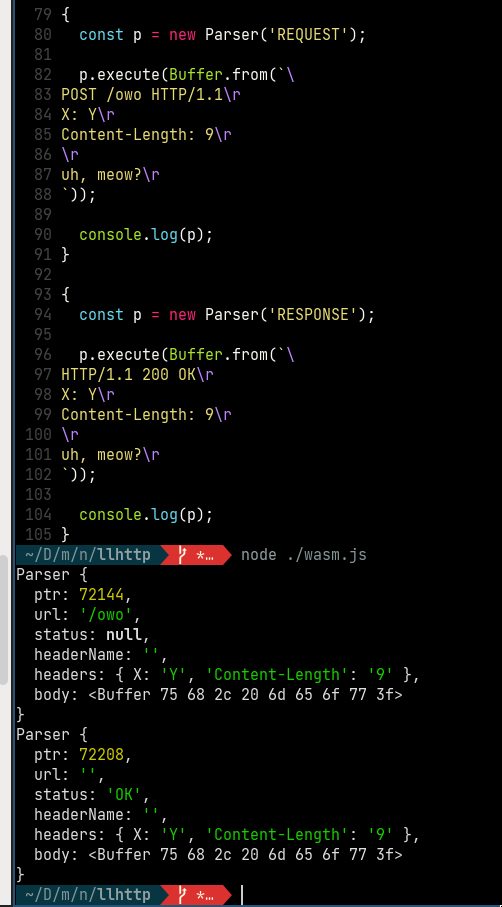
In undici we are using it to access the internal http parser. It would be good to get some way to retrieve it.
cc @ronag
|
Yep. Removing would break undici. |
|
can't you just depend on llhttp? it's kept in a separate repo and everything. |
|
The approach for undici then should be to open a PR that exposes a public API for interacting with the http parser. Using (or what @devsnek said) |
|
While +1 in general, Perhaps we could move forward by runtime-deprecating everything except a list of some exceptions (for That is, if we don't resolve those by the time of the next major release. Upd: will recheck |
We don’t want native deps. What we would like is to have a web assembly build of llhttp. But we need help for that... |
|
Also there is the consume/unconsume optimization which I’m not sure is possible without process.binding. In that case we would have to bring undici into core or somehow expose that functionality. |
This would be a reasonable move, IMO |
The biggest task with that is to port all the tests from tap. I’m actually sceptical to whether bringing undici into core give any value other than:
Doing it just for 1 seems a bit inefficient in terms of time and effort. |
|
I would add:
|
|
So could this be a way forward?
I'm happy with having undici both inside and outside of core. My main concern is the tests which I don't quite know what to do about. Would it be acceptable to have tap based tests in core? |
|
I would not be against adding tap in the repo for tests. Happy to look into it. We are talking about https://github.com/tapjs/node-tap, right? |
|
I'd rather not carve out any special cases as it just makes things more difficult. The viable alternatives that I can see are either: a) bring undici into core, b) expose the http parser as a supported core module, c) have undici depend on llhttp directly. Given that I believe there are several libraries that are getting to the http parser the same way, option (b) may actually be the better way to go. |
|
Oh, just remembered... it is also possible to get to the internal root@DESKTOP-5KK9VIR:~/node/node# ./node -pe "require('_http_common').HTTPParser"
[Function: HTTPParser] {
REQUEST: 1,
RESPONSE: 2,
kOnMessageBegin: 0,
kOnHeaders: 1,
kOnHeadersComplete: 2,
kOnBody: 3,
kOnMessageComplete: 4,
kOnExecute: 5,
kOnTimeout: 6
}That would likely be the most immediate way of avoiding the direct use of |
|
How do I do that? |
|
Could we get the wasm build on npm? |
|
I'm not planning to do so but I think as an org yes that is possible. We already publish readable-stream, for example. |
|
llhttp is already on npm. Though a bit outdated and lacking wasm. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
lgtm
I tested that we can use _http_common in Undici. Long term we will look into the wasm-based solution.
|
This is probably going to annoy many people but maybe that's necessary so the ecosystem migrates out of it. |
|
And yet |
This is a common theme, as you probably are aware. In the current download stats (screenshot below), you can see that the current |
|
Yep... thus the reason why I said "It's time to start nudging them harder out of the nest." in the original post ;-) |
|
@nodejs/tsc ... this needs additional review please. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I wish we could do this, but this isn't going to work without a plan for handling situations like the tmp one.
The only reasonable way forward here that I see, is:
- Do comprehensive research into what exact features ecosystem modules get through
process.binding()(this isn't actually going to be a huge API surface!) - Patch
process.binding()so that it returns objects that cover those use cases, implemented in terms of public APIs - Optionally, runtime-deprecate
process.binding()only for the cases that users aren't commonly encountering - Eventually, remove support for those cases specifically
- Leave it at that, don't runtime-deprecate
process.binding()as a whole and leave the shim in place forever
|
I found following uses in my code:
|
|
Closing this in favor of a more incremental approach |
Ref: #37485 (review) Ref: #37787 PR-URL: #37819 Refs: #37787 Reviewed-By: James M Snell <jasnell@gmail.com> Reviewed-By: Benjamin Gruenbaum <benjamingr@gmail.com> Reviewed-By: Colin Ihrig <cjihrig@gmail.com> Reviewed-By: Rich Trott <rtrott@gmail.com> Reviewed-By: Antoine du Hamel <duhamelantoine1995@gmail.com> Reviewed-By: Michaël Zasso <targos@protonmail.com> Reviewed-By: Anto Aravinth <anto.aravinth.cse@gmail.com>

@nodejs/tsc ... this one still may be controversial but I figured I'd give it a shot.
process.binding()has always been problematic and has been deprecated since the 11.x timeframe. We have fully migrated tointernalBinding()internally but there are still a few stragglers in the ecosystem that have not let go of their hold on our internal bindings. It's time to start nudging them harder out of the nest.Fixes: #30884