-
Notifications
You must be signed in to change notification settings - Fork 60
Detailed Features
Proving ground:https://github.com/outlaws-bai/GalaxyDemo
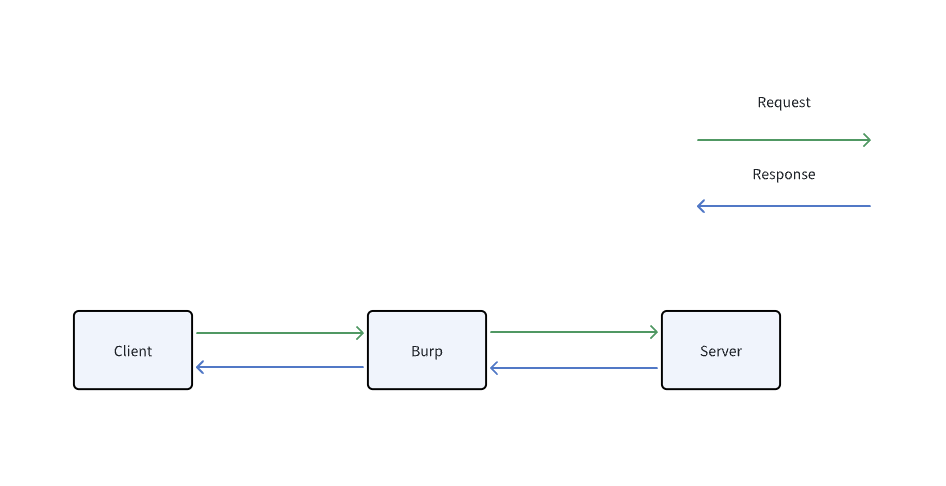
Under normal circumstances, when we conduct penetration testing through Burp proxy, the flow of traffic is shown in the figure.
And this plugin added 4 hooks to the process through Burp's' Montoya API ', making the traffic flow situation as shown in the following figure.
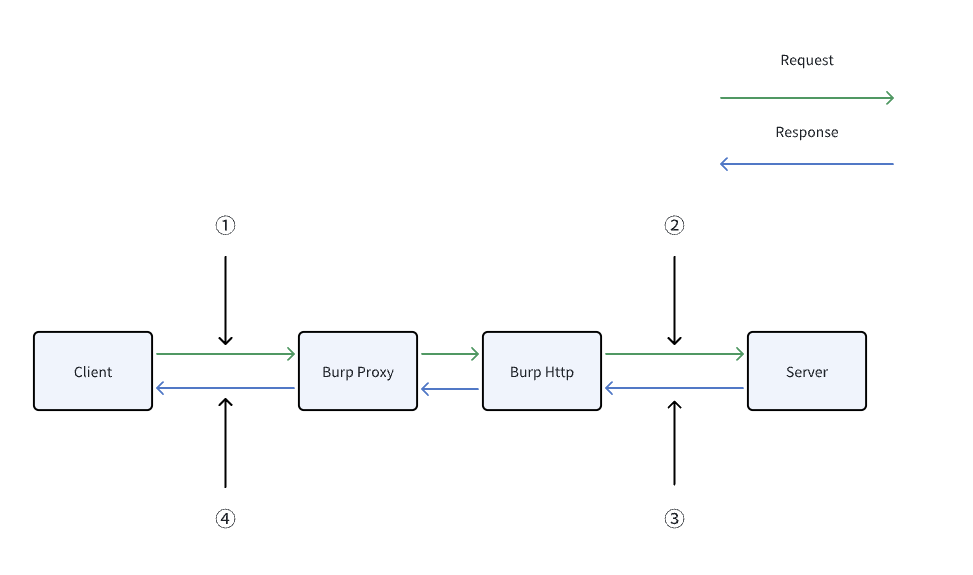
①:The HTTP request was triggered when it reached Burp from the client. You need to complete the code for decrypting the request here, so that you can see the plaintext request message in Burp.
②:The HTTP request was triggered when it was about to be sent from Burp to the server. You need to complete the request encryption code here so that the encrypted request message can be sent to the server.
③:The HTTP response was triggered when it reached Burp from the server. You need to complete the response decryption code here so that you can see the plaintext response message in Burp.
④:The HTTP response is triggered when it is about to be returned from Burp to the client. You need to complete the response encryption code here so that you can return the encrypted response message to the client.
In fact, by reading this, you will find that this tool can not only be used for automated encryption and decryption, but also has a good effect on preventing replay bypass and automatically recalculating signatures (complete the corresponding code logic in ②).
I will name these four hooks as hookRequestToBurp,hookRequestToServer, hookResponseToBurp, hookResponseToClient
These four hooks need to be implemented by you, and the project provides two ways for you to implement them:http(preference)、 jython
If you cannot see the jython hook, Please configure a folder in Burp's Java environment (Settings ->Extensions) and place jython-standalone-xxx.jar in that folder.
http: You can implement an HTTP server in any language and implement four 'Hook interfaces' within it. Below is a Python implementation
Obviously, you can use frida, jsRPC, cdp, or execute cp client code using node.
https://github.com/outlaws-bai/GalaxyHttpHooker
jython:You need to use jython to implement the hook script and implement four 'Hook functions' in it. Below are the hook scripts corresponding to all encryption schemes in the shooting range (already built into the plugin).
https://github.com/outlaws-bai/Galaxy/tree/main/src/main/resources/examples/jython
Hooker: hook ways
Auto Scan Decrypted Request: Switch, does it automatically forward decrypted requests from the Proxy module to the passive proxy scanner.
When linking passive agent scanners, the upstream agent of the passive scanner must be configured as Burp.
Expression: mvel bool expression,Use requests to determine whether traffic requires hooks.
default expression:!request.isStaticExtension() && request.host=='192.168.1.3' It means that the request cannot be a static suffix, and the host must be 192.168.1.3. Note that request.Host here does not have a port.
The first recommended hook method for the project is HTTP, which has lower requirements compared to Jython and is easier to understand. If you have some confidence in your coding ability, you can try Jython's method. It will definitely bring you unexpected surprises, but at the same time, you will also step into many pitfalls. Please choose carefully. I want use jython
After starting the HTTP Hook service, right-click in any HTTP request/response editor to find the corresponding button, and click to test it.
You need to check the logs (which can be debugged when using HTTP) to determine why the error occurred.
The running logs will be sent to two places:
- ${WorkDir} / run.log
-
Burp -> Extensions -> Galaxy -> Output/Errors(Only partial display, and occasional bugs in the burn are not displayed)
WorkDir:Linux/Mac in ~/.galaxy,Windows in %USERPROFILE%/.galaxy
- Linkage sqlmap:Right click on the decrypted request and find
Send Decrypted Request To Sqlmap, then click on it. - Linkage xray:Configure XRay's upstream proxy as Burp burp,Start
Auto Scan Decrypted RequestOr right-click on the decrypted request and findSend Decrypted Request To Scanner, then click on it
When linking sqlmap and xray, as the traffic will pass through Burp again, there will inevitably be more scanning traffic in Burp's proxy. You can add the following code snippet to Bambda to not display these traffic.
!requestResponse.annotations().notes().contains("HookedByGalaxy")