-
Notifications
You must be signed in to change notification settings - Fork 469
Zest and ZAP integration Introduction
dscarson edited this page Aug 16, 2014
·
1 revision
####What is Zest ?
Zest is an experimental specialized scripting language developed by the Mozilla security team and is intended to be used in web oriented security tools. https://developer.mozilla.org/en-US/docs/Zest
####What is ZAP ?
ZAP is an easy to use integrated penetration-testing tool for finding vulnerabilities in web applications, which has in-built functionality to run Zest Scripts. https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project
####Quick Guide
-Quick guide to get started -Video tutorial
####Installation
Installation guide
####How is this useful in OWTF ?
OWTF does a great job in finding vulnerabilities and building the report,
but unfortunately in many cases developers and system administrators may lack
the security knowledge to understand or reproduce the problem.
Zest integration will facilitate the understanding of security issues by
developers and system-administrators despite their potential lack of security knowledge
or lack of skill to run penetration testing tools.
While it is necessary to describe vulnerabilities (using Reports), this project
will allow security teams to create reproducible test scripts (Zest Scripts),
which they can then share with the developers.
These scripts can be used by the developers to:
-Reproduce the issues
-Create their fixes
-Test the created fixes
Additionally this will allow OWTF to send HTTP requests(implemented) and Zest scripts (not implemented yet)
to third party tools, such as ZAP.
ZAP will be able to run Zest scripts and send HTTP requests sent from OWTF.
OWTF will be able to run Zest scripts and send HTTP requests on its own.
Ultimately, information exchange via HTTP requests and Zest scripts from OWTF to
third-party tools will be feasible.
This will ensure that users can reproduce or verify vulnerabilities found by OWTF
from any third party tool able to replay HTTP requests or run Zest scripts,
such as ZAP.
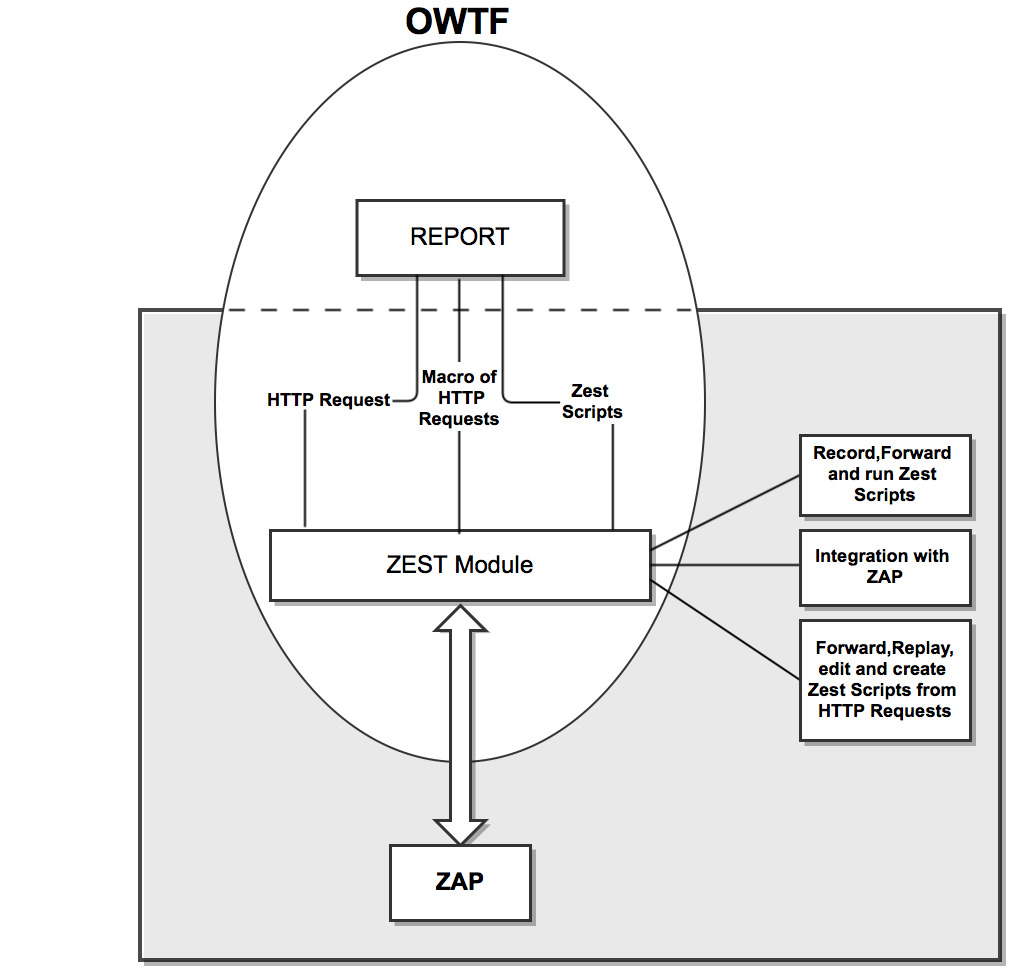
####What features of Zest and ZAP are implemented in OWTF ?
- Zest script creator module
- Zest script creation from single HTTP transaction
- Zest script creation from multiple HTTP transaction (macro of requests)
- HTTP request editing window (from which you can replay the request)
- Zest script Console
- Record a Zest script functionality
- Zest script Runner
- Forward HTTP request to ZAP
More resources on Zest : (will be updated soon)
This wiki and the OWTF README document contains a lot of information, please take your time and read these instructions carefully.
We provide a CHANGELOG that provides details about almost every OWTF release.
Be sure to read the CONTRIBUTING guidelines before reporting a new OWTF issue or opening a pull request.
If you have any questions about the OWTF usage or want to share some information with the community, please go to one of the following places:
- IRC channel
#owtf(irc.freenode.net)
Google Summer of Code 2018 Guide
Installation
Getting Started
- Define where your tools are
- Run OWASP OWTF
- HTTP Auth Configurations
- Simulation mode
- AUX plugins usage
- FAQ
SET usage
Cookbooks (GSoC 2014 Projects UPDATE)
-
Zest Integration:
- Quick Guide to get started with Zest,ZAP and Replay
- Zest and ZAP API Installation
- Zest and ZAP integration Introduction
- Zest Runner module
- Forward HTTP request to ZAP
- Zest script creation from single HTTP transaction
- Zest script creation from multiple HTTP transactions
- Zest Script Creator module
- HTTP Request Editing Window (Replay Function)
- Zest Script Recording Functionality
- Zest scripting console
Development
-
Plugins:
-
Tests:
Contact
