fix(deps): update dependency @strapi/plugin-users-permissions to v4.24.2 [security] #13
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
This PR contains the following updates:
4.5.2->4.24.2GitHub Vulnerability Alerts
GHSA-xv3q-jrmm-4fxv
Summary
Strapi through 4.5.6 does not verify the access or ID tokens issued during the OAuth flow when the AWS Cognito login provider is used for authentication.
Details
Strapi through 4.5.6 does not verify the access or ID tokens issued during the OAuth flow when the AWS Cognito login provider is used for authentication. A remote attacker could forge an ID token that is signed using the 'None' type algorithm to bypass authentication and impersonate any user that use AWS Cognito for authentication.
IoC
Reviewing of application logs is recommended to detect any suspicious activity. Running the following regex pattern will extract all ID tokens sent to
/api/auth/cognito/callback./\/api\/auth\/cognito\/callback\?[\s\S]*id_token=\s*([\S]*)/Once you have a list of the ID tokens, you will need to verify each token using the public key file for your AWS Cognito user pool that you can download from
https://cognito-idp.{region}.amazonaws.com/{userPoolId}/.well-known/jwks.json. If there are any JWT tokens that cannot be verified using the correct public key, then you need to inspect the JWT body and see if it contains theemailandcognito:usernameclaims (example below).{ "cognito:username": "auth-bypass-example", "email": "user@example.com" }If there are any JWTs that have this body, verify when the account with the email address was created. If the account was created earlier than the request to
/api/auth/cognito/callbackwith the invalid JWT token, then you need to contact the user to inform them their account has been breached!After upgrading to Strapi v4.6.0 or greater you will need to reconfigure your AWS Cognito provider to include the JWKS URL for it to work properly. If you do not reconfigure your provider you will receive an error message when attempting to login.
Impact
Any Strapi user using the users-permissions AWS Cognito provider before 4.6.0
CVE-2023-22621
Summary
Strapi through 4.5.5 allows authenticated Server-Side Template Injection (SSTI) that can be exploited to execute arbitrary code on the server.
Details
Strapi through 4.5.5 allows authenticated Server-Side Template Injection (SSTI) that can be exploited to execute arbitrary code on the server. A remote attacker with access to the Strapi admin panel can inject a crafted payload that executes code on the server into an email template that bypasses the validation checks that should prevent code execution.
IoC
Using just the request log files, the only IoC to search for is a
PUTrequest to URL path/users-permissions/email-templates. This IoC only indicates that a Strapi email template was modified on your server and by itself does not indicate if your Strapi server has been compromised. If this IoC is detected, you will need to manually review your email templates on your Strapi server and backups of your database to see if any of the templates contain alodashtemplate delimiter (eg.<%STUFF HERE%>) that contains suspicious JavaScript code. Generally speaking these templates should look like the following, you may have minor adjustments but any unrecognized code should be considered suspicious.Reset Password Template:
Email Confirmation Template:
Specifically you should look for odd code contained within the
<%STUFF HERE%>blocks as this is what is used to bypass the lodash templating system. If you find any code that is not a variable name, or a variable name that is not defined in the template you are most likely impacted and should take immediate steps to confirm there are no malicious applications running on your servers.Impact
All users on Strapi below 4.5.6 with access to the admin panel and the ability to modify the email templates
CVE-2023-22893
Strapi 3.2.1 until 4.6.0 does not verify the access or ID tokens issued during the OAuth flow when the AWS Cognito login provider is used for authentication. A remote attacker could forge an ID token that is signed using the 'None' type algorithm to bypass authentication and impersonate any user that use AWS Cognito for authentication.
CVE-2023-38507
1. Summary
There is a rate limit on the login function of Strapi's admin screen, but it is possible to circumvent it.
2. Details
It is possible to avoid this by modifying the rate-limited request path as follows.
3. PoC
Access the administrator's login screen (
/admin/auth/login) and execute the following PoC on the browser's console screen.Pattern 1 (uppercase and lowercase)
This PoC does the following:
429 Too Many Requests)/admin/Login) and make a request again to confirm that it is possible to bypass the rate limit and log in. (200 OK)Pattern 2 (trailing slash)
This PoC does the following:
429 Too Many Requests)/admin/login/) and make a request again to confirm that it is possible to bypass the rate limit and log in. (200 OK)PoC Video
4. Impact
It is possible to bypass the rate limit of the login function of the admin screen.
Therefore, the possibility of unauthorized login by login brute force attack increases.
5. Measures
Forcibly convert the request path used for rate limiting to upper case or lower case and judge it as the same path. (
ctx.request.path)Also, remove any extra slashes in the request path.
https://github.com/strapi/strapi/blob/32d68f1f5677ed9a9a505b718c182c0a3f885426/packages/core/admin/server/middlewares/rateLimit.js#L31
6. References
CVE-2023-39345
System Details
Description
I marked some fields as private fields in user content-type, and tried to register as a new user via api, at the same time I added content to fill the private fields and sent a post request, and as you can see from the images below, I can write to the private fields.
To prevent this, I went to the extension area and tried to extend the register method, for this I wanted to do it using the sanitizeInput function that I know in the source codes of the strap. But the sanitizeInput function did not filter out private fields.
here's the solution I've temporarily kept to myself, code snippet
CVE-2024-34065
Summary
By combining two vulnerabilities (an
Open Redirectandsession token sent as URL query parameter) in Strapi framework is its possible of an unauthenticated attacker to bypass authentication mechanisms and retrieve the 3rd party tokens. The attack requires user interaction (one click).Impact
Unauthenticated attackers can leverage two vulnerabilities to obtain an 3rd party token and the bypass authentication of Strapi apps.
Technical details
Vulnerability 1: Open Redirect
Description
Open redirection vulnerabilities arise when an application incorporates user-controllable data into the target of a redirection in an unsafe way. An attacker can construct a URL within the application that causes a redirection to an arbitrary external domain.
In the specific context of Strapi, this vulnerability allows the SSO token to be stolen, allowing an attacker to authenticate himself within the application.
Remediation
If possible, applications should avoid incorporating user-controllable data into redirection targets. In many cases, this behavior can be avoided in two ways:
If it is considered unavoidable for the redirection function to receive user-controllable input and incorporate this into the redirection target, one of the following measures should be used to minimize the risk of redirection attacks:
Example 1: Open Redirect in /api/connect/microsoft via
$_GET["callback"]$_GET["callback"]Payload:
Final payload:
User clicks on the link:
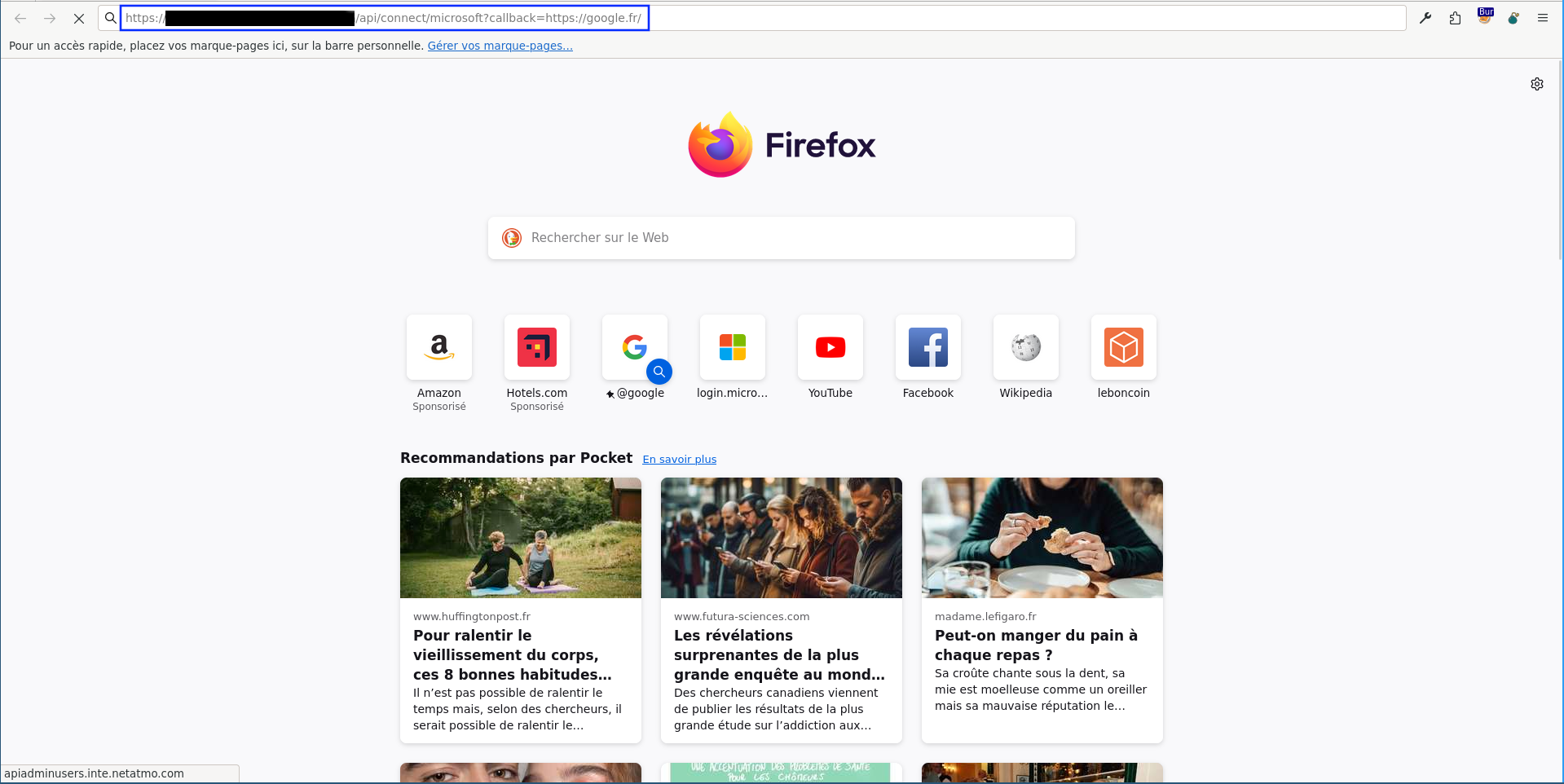
Look at the intercepted request in Burp and see the redirect to Microsoft:
Microsoft check the cookies and redirects to the original domain (and route) but with different GET parameters.
Then, the page redirects to the domain controlled by the attacker (and a token is added to controlled the URL):
The domain originally specified (https://google.fr) as
$_GET["callback"]parameter is present in the cookies. So <TARGET> is using the cookies (koa.sess) to redirect.koa.sesscookie:{"grant":{"provider":"microsoft","dynamic":{"callback":"https://google.fr/"}},"_expire":1700234244263,"_maxAge":86400000}The vulnerability seems to come from the application's core:
File: packages/plugins/users-permissions/server/controllers/auth.js
And more specifically:
... // Ability to pass OAuth callback dynamically grantConfig[provider].callback = _.get(ctx, 'query.callback') || _.get(ctx, 'session.grant.dynamic.callback') || grantConfig[provider].callback; grantConfig[provider].redirect_uri = getService('providers').buildRedirectUri(provider); return grant(grantConfig)(ctx, next); ...Possible patch:
_.get(ctx, 'query.callback')=$_GET["callback"]and_.get(ctx, 'session')=$_COOKIE["koa.sess"](which is{"grant":{"provider":"microsoft","dynamic":{"callback":"https://XXXXXXX/"}},"_expire":1701275652123,"_maxAge":86400000}) so_.get(ctx, 'session.grant.dynamic.callback')=https://XXXXXXX/.The route is clearly defined here:
File: packages/plugins/users-permissions/server/routes/content-api/auth.js
File: packages/plugins/users-permissions/server/services/providers-registry.js
If parameter
$_GET["callback"]is defined in the GET request, the assignment does not evaluate all conditions, but stops at the beginning. The value is then stored in the cookiekoa.sess:koa.sess=eyJncmFudCI6eyJwcm92aWRlciI6Im1pY3Jvc29mdCIsImR5bmFtaWMiOnsiY2FsbGJhY2siOiJodHRwczovL2FkbWluLmludGUubmV0YXRtby5jb20vdXNlcnMvYXV0aC9yZWRpcmVjdCJ9fSwiX2V4cGlyZSI6MTcwMTI3NTY1MjEyMywiX21heEFnZSI6ODY0MDAwMDB9Which once base64 decoded become
{"grant":{"provider":"microsoft","dynamic":{"callback":"https://<TARGET>/users/auth/redirect"}},"_expire":1701275652123,"_maxAge":86400000}.The signature of the cookie is stored in cookie
koa.sess.sig:koa.sess.sig=wTRmcVRrn88hWMdg84VvSD87-_0File: packages/plugins/users-permissions/server/bootstrap/grant-config.js
Vulnerability 2: Session token in URL
Description
Applications should not send session tokens as URL query parameters and use instead an alternative mechanism for transmitting session tokens, such as HTTP cookies or hidden fields in forms that are submitted using the POST method.
Example 1: SSO token transmitted within URL (
$_GET["access_token"])$_GET["callback"]When a callback was called, the 3rd party token was transmitted in an insecure way within the URL, which could be used to increase the impact of the Open Redirect vulnerability described previously by stealing the SSO token.
Weaponized payload:
With a web server specially developed to exploit the vulnerability listening on <C2>:8080, it is possible to retrieve a JWT token allowing authentication on Strapi.
A user is on his browser when he decides to click on a link sent to him by e-mail.
The server specially developed by the attacker to show that the vulnerability is exploitable, recovers the user's SSO token.
Because the victim didn't change to another Web page.
The attacker can use the SSO token to authenticate himself within the application and retrieve a valid JWT token enabling him to interact with it.
Details
Get the JWT token with the
access_tokenFirst of all, thanks to the SSO token, you authenticate yourself and get a JWT token to be able to interact with the various API routes.
Request (HTTP):
Response (HTTP):
Request API routes using the JWT token
Then reuse the JWT token to request the API.
Request (HTTP):
Response (HTTP):
POC (Web server stealing SSO token and retrieving JWT token then bypassing authentication)
Release Notes
strapi/strapi (@strapi/plugin-users-permissions)
v4.24.2Compare Source
Strapi was made aware of a vulnerably that were patched in this release, for now we are going to delay the detailed disclosure of the exact details on how to exploit it and how it was patched to give time for users to upgrade before we do public disclosure.
📚 Update and Migration Guides
Full Changelog: strapi/strapi@v4.24.2...v4.24.1
v4.24.1Compare Source
🔥 Bug fix
📚 Update and Migration Guides
v4.24.0Compare Source
🔥 Bug fix
⚙️ Chore
📚 Update and Migration Guides
v4.23.2Compare Source
What's Changed
Full Changelog: strapi/strapi@v4.23.1...v4.23.2
v4.23.1Compare Source
📖 Documentation
⚙️ Chore
🔥 Bug fix
📚 Update and Migration Guides
v4.23.0Compare Source
⚙️ Chore
🔥 Bug fix
🚀 New feature
💅 Enhancement
📚 Update and Migration Guides
v4.22.1Compare Source
What's Changed
Full Changelog: strapi/strapi@v4.22.0...v4.22.1
v4.22.0Compare Source
Strapi was made aware of a vulnerably that were patched in this release, for now we are going to delay the detailed disclosure of the exact details on how to exploit it and how it was patched to give time for users to upgrade before we do public disclosure.
🔥 Bug fix
🚀 New feature
⚙️ Chore
📚 Update and Migration Guides
v4.21.1Compare Source
💅 Enhancement
🔥 Bug fix
📚 Update and Migration Guides
v4.21.0Compare Source
💅 Enhancement
🚀 New feature
📚 Update and Migration Guides
v4.20.5Compare Source
🔥 Bug fix
⚙️ Chore
📚 Update and Migration Guides
v4.20.4Compare Source
💅 Enhancement
🔥 Bug fix
⚙️ Chore
📚 Update and Migration Guides
v4.20.3Compare Source
🔥 Bug fix
📚 Update and Migration Guides
v4.20.2Compare Source
🔥 Bug fix
📚 Update and Migration Guides
v4.20.1Compare Source
💅 Enhancement
🔥 Bug fix
⚙️ Chore
📖 Documentation
🚀 New feature
📚 Update and Migration Guides
v4.20.0Compare Source
🔥 Bug fix
💅 Enhancement
📚 Update and Migration Guides
v4.19.1[Compare Source](https://togithub.com/strapi/strapi/compare/v4.19.0.
Configuration
📅 Schedule: Branch creation - "" (UTC), Automerge - At any time (no schedule defined).
🚦 Automerge: Disabled by config. Please merge this manually once you are satisfied.
♻ Rebasing: Whenever PR becomes conflicted, or you tick the rebase/retry checkbox.
🔕 Ignore: Close this PR and you won't be reminded about this update again.
This PR has been generated by Renovate Bot.