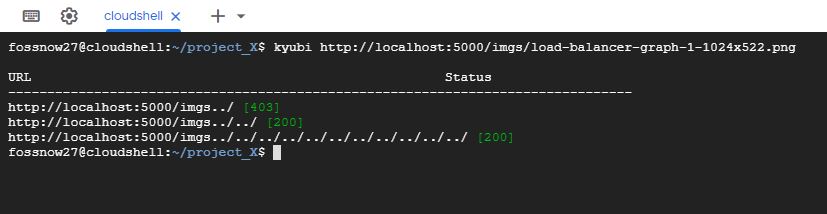
A tool to discover Nginx alias traversal misconfiguration, read more https://www.acunetix.com/vulnerabilities/web/path-traversal-via-misconfigured-nginx-alias/
git clone https://github.com/shibli2700/Kyubi.git
cd /Kyubi
sudo python3 setup.py install
pip install .
You can pull the Docker image from Docker Hub and running it locally using the following command:
docker pull saydocerr/kyubidocker run -it saydocerr/kyubiusage: kyubi [-h] [-v] [-a] url
This tool checks nginx alias traversal misconfiguration.
positional arguments:
url URL of the target
optional arguments:
-h, --help show this help message and exit
-v increase verbosity
-a append segment in the end
$ kyubi -v https://127.0.0.1/resources/images/users/profile/profile.png
- Brute forcing with filenames and directories.
- Web Interface.