-
-
Notifications
You must be signed in to change notification settings - Fork 410
FS_Process_Threads
The directory threads exists as a sub-directory in each process directory.
The threads directory contains one sub-directory for each thread named after its Thread ID (TID) and the threads.txt informational file.
Each thread sub-directory contains an info.txt file and files for the ETHREAD kernel struct, the kernel stack, the user mode stack and the thread environment block. Please note that not all files are guaranteed to exist - for kernel exclusive threads the user-mode kernel thread will be missing.
Each module directory contains a number of informational files and directories related to the loaded module. The files and directories and their contents are listed below:
| File | Description |
|---|---|
| callstack_enable.txt | Enable callstack parsing for the current process. *) |
| threads.txt | Summary of threads related to the current process. |
| [tid]/callstack.txt | The callstack if enabled and possible to parse. |
| [tid]/info.txt | Information about the current thread including its user and kernel mode stack, CPU instruction and stack pointers and additional information. |
| [tid]/ethread | The ETHREAD kernel structure. |
| [tid]/kstack | The kernel mode thread stack. |
| [tid]/stack | The user mode thread stack. |
| [tid]/teb | The thread environment block page. |
| [tid]/impersonation | Impersonation token (if existing). |
Files threads.txt and info.txt are read only. Other files in the individual thread sub-directories are writable if a write-capable memory acquisition device is used.
The file threads.txt contains information about threads related to the process. The meaning of the different columns are as follows:
# PID TID ETHREAD Status WaitReason Prio ExitSt StartAddress InstructionPtr TEB StackBase StackPtr StackLimit CreateTime ExitTime
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
0000 2788 404 ffffd00feda95080 5 Waiting 6 UserRequest 0 8 9 0 7ffeff16ce50 0 -- a18000 : 82e0000 > 0 > 82d2000 [2020-04-05 23:51:12 UTC :: ***]
0001 2788 1120 ffffd00fedca5080 5 Waiting 6 UserRequest 0 9 b 0 7ffeff16ce50 7ffefcec9a84 -- be6000 : 2f70000 > 2f6fc28 > 2f62000 [2020-04-05 23:51:10 UTC :: ***]
0002 2788 1176 ffffd00fee71d080 5 Waiting 15 WrQueue 0 8 8 0 ffffe0082ad6deb0 0 -- bea000 : 3070000 > 0 > 3062000 [2020-04-05 23:51:10 UTC :: ***]
0003 2788 1228 ffffd00fe999e080 5 Waiting 6 UserRequest 0 8 9 0 7ffeff16ce50 0 -- a44000 : b990000 > 0 > b982000 [2020-04-05 23:51:15 UTC :: ***]
0004 2788 2044 ffffd00fed45e080 5 Waiting 6 UserRequest 0 8 9 0 7ffeff16ce50 0 -- a9a000 : 6ed0000 > 0 > 6ec2000 [2020-04-05 23:53:36 UTC :: ***]
0005 2788 2332 ffffd00fed775080 5 Waiting 6 UserRequest 0 8 a 0 ffffe0082798b3a0 0 -- a06000 : 5de0000 > 0 > 5dd2000 [2020-04-05 23:51:11 UTC :: ***]
0006 2788 2504 ffffd00fed490040 4 Term 22 WrTerminated 0 8 9 0 7ffeff16ce50 0 -- 0 : 0 > 0 > 0 [2020-04-05 23:51:14 UTC :: 2020-04-05 23:57:47 UTC]
The callstack.txt file is disabled by default. Callstack parsing must be enabled by writing 1 to the file callstack_enable.txt in the module root folder.
Callstack parsing is resource intense and may download a significant amount of symbol files to the local symbol cache. Callstack parsing is only available on 64-bit user-mode processes. 32-bit processes and kernel processes are not currently supported.
Callstack parsing is best-effort. It may fail completely or fail in the middle of the stack trace. Results are not guaranteed to always be correct due to heuristics. It may however provide useful insights into interesting/suspicious threads.
Below is an example of a callstack.txt file:
Index RSP RetAddr Module!Function+Displacement
==================================================================
00: 0000000000000000 00007ffd004f9904
01: 000000000bfcf948 00007ffd0380f5cd win32u!ZwUserMsgWaitForMultipleObjectsEx+14
02: 000000000bfcf950 00007ffce6031338 user32!RealMsgWaitForMultipleObjectsEx+1d
03: 000000000bfcf990 00007ffd03aac315 stobject!CSSOSharedThread::ThreadProc+c8
04: 000000000bfcfe30 00007ffd04347e94 shcore!_WrapperThreadProc+f5
05: 000000000bfcff10 00007ffd0448a251 kernel32!BaseThreadInitThunk+14
06: 000000000bfcff40 0000000000000000 ntdll!RtlUserThreadStart+21
The example below shows the files in the threads/5372 sub-directory of the mspaint.exe process where 5372 is a thread id (TID).
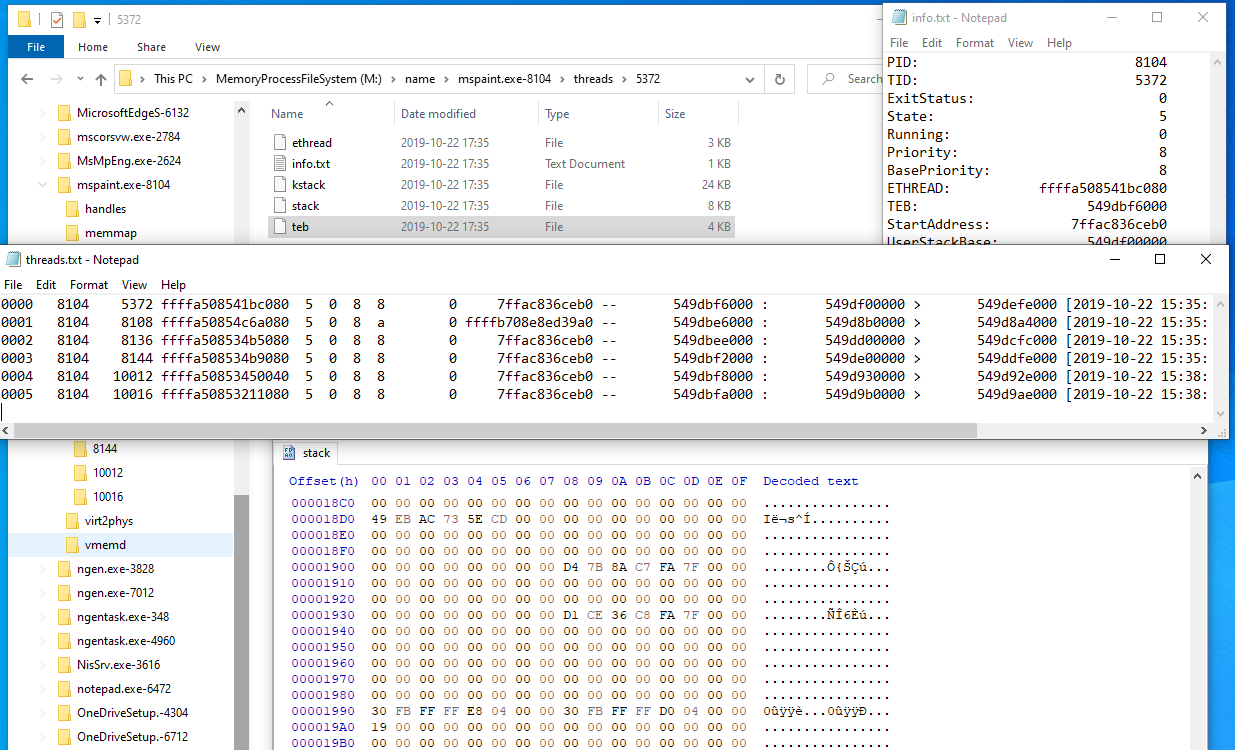
The threads sub-directory is implemented as a built-in native C-code plugin. The plugin source is located in the file modules/m_proc_thread.c in the vmm project.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖