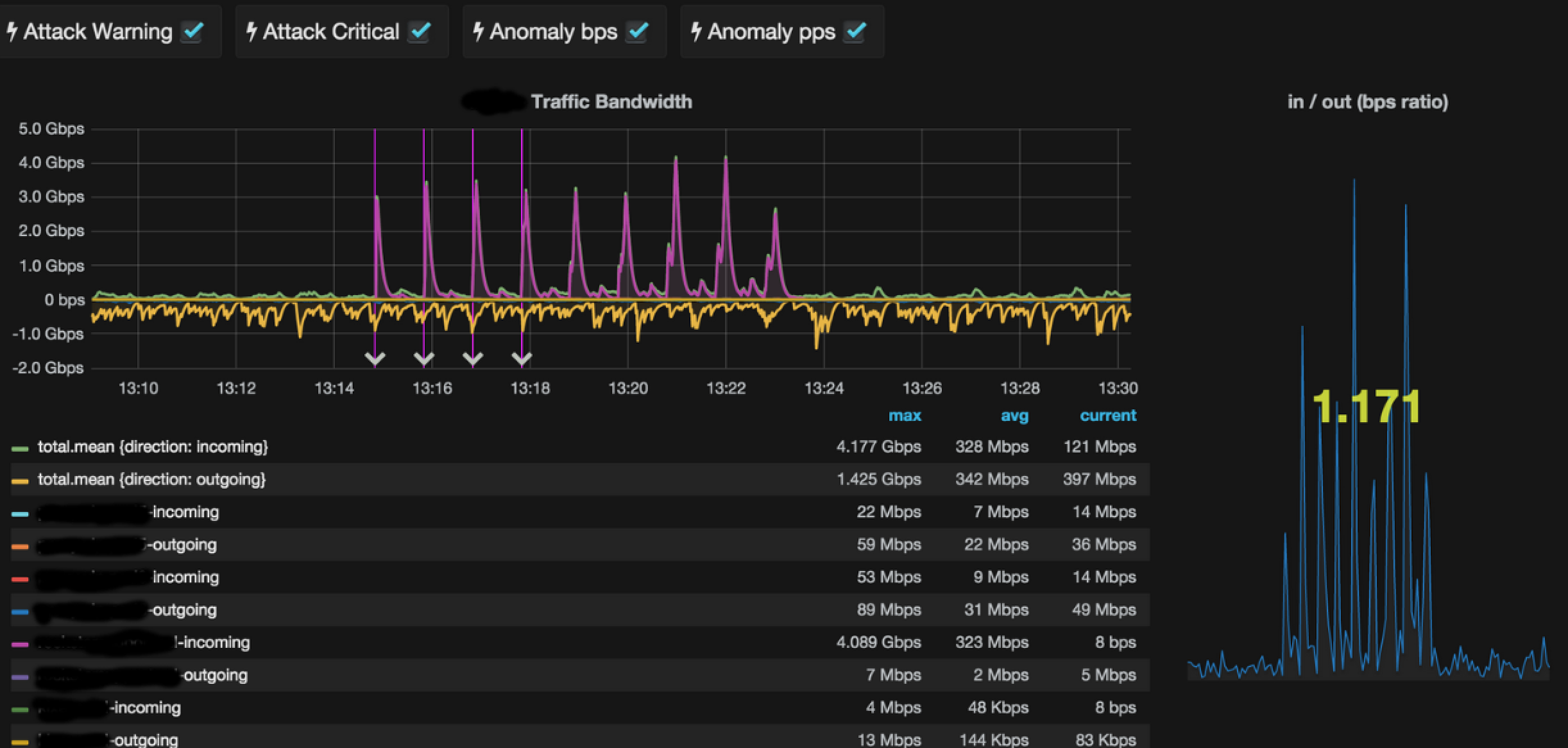
NET HEALER receive DDoS Attack reports from FastNetMon collectors allowing custom triggers on a per stage based actions.
Allows integration with non gaussian algorithms for anomaly detection.
Provides a RESTful like API
- clear - no Attack Reports received for any /32 target
- warning - less or equal to 2 Attack Reports received for /32 target(s)
- critical - more than 2 Attack Reports received for /32 target(s)
- under_attack - FastNetMon + anomaly detected
Each 1 FNM /32 ban = 1 NET HEALER Attack Report
Lower the FNM ban time, faster NET HEALER will advance in stages (thresholds can be customized)
Start with FNM ban time: 45 seconds (NET HEALER will converge from cleared to warning after 90 seconds)
- Grafana vertical bars markdown including stage/target(s)
- Pagerduty
- Flowdock chat messages
- BGP announces (BIRD + kernel blackhole tables)
- FastNetMon: a super cool tool written by Pavel Odintsov - https://github.com/pavel-odintsov/fastnetmon
- Redis (https://github.com/antirez/redis)
- InfluxDB (https://github.com/influxdb/influxdb)
- Grafana (https://github.com/grafana/grafana)
- Morgoth (https://github.com/nathanielc/morgoth)
##Installation 0. FastNetMon (FNM) should be configured to use:
- Redis (https://github.com/FastVPSEestiOu/fastnetmon/blob/master/docs/REDIS.md)
- InfluxDB (https://github.com/FastVPSEestiOu/fastnetmon/blob/master/docs/INFLUXDB_INTEGRATION.md)
- Add to /usr/local/bin/notify_about_attack.sh under if [ "$4" == "attack_details" ]; then
curl -sk https://{nethealer_ip:port}/healer/v1/ddos/pool
curl -sk https://{nethealer_ip:port}/healer/v1/ddos/actions
- install ruby (https://www.ruby-lang.org/en/documentation/installation/)
$ gem install bundler$ bundle install$ bundle exec script/bootstrap- Populate
.envwith a config $ bundle exec script/start
##How to query the API
{
"status": "clear",
"timestamp": "20150913-115403"
}
{
"reports": {
"200.200.200.10": {
"fqdn": "nethealer.hostingxpto.com",
"attack_type": "udp_flood",
"alerts": 2,
"protocol": [
"udp"
],
"incoming": {
"total": {
"mbps": 2894.96,
"pps": 781380,
"flows": 628
},
"tcp": {
"mbps": 1.71,
"pps": 2654,
"syn": {
"mbps": 0.08,
"pps": 109
}
},
"udp": {
"mbps": 2761,
"pps": 779884
},
"icmp": {
"mbps": 0,
"pps": 0
}
}
}
}
}
### GET /healer/v1/ddos/brief
=> query /32 targets + amount of current Attack Reports
```json
{
"reports": {
"200.200.200.10": 3,
},
"timestamp": "20150913-030255"
}=> PRs are more than welcome !
send me an email vdeluca@zendesk.com