-
Notifications
You must be signed in to change notification settings - Fork 61
Setting up Okta
We use Okta for identity management, both in production and lower test environments. We have a separate production instance, with real users, and a preview instance for lower environments.
To set up your Okta account for testing in a lower deployed environment, you will need to follow a few steps in Okta preview, where we manage Okta groups for deployed applications in lower environments.
First, ask a team member to invite you to the Okta Preview group (they can do so by inviting you to an organization through the SimpleReport UI.) Once you've received the welcome email and activated your account, ask someone to add you to the following Okta groups:
PRIME Team MembersSimpleReport EngineeringSR-{ENV}-ADMINS
Next, (once you've deployed to an environment) you'll want to set yourself up within the application:
- Go to
{env}.[simplereport.gov/app/sign-up, for instancetest.simplereport.gov/app/sign-up - Select “my org is new to SimpleReport”
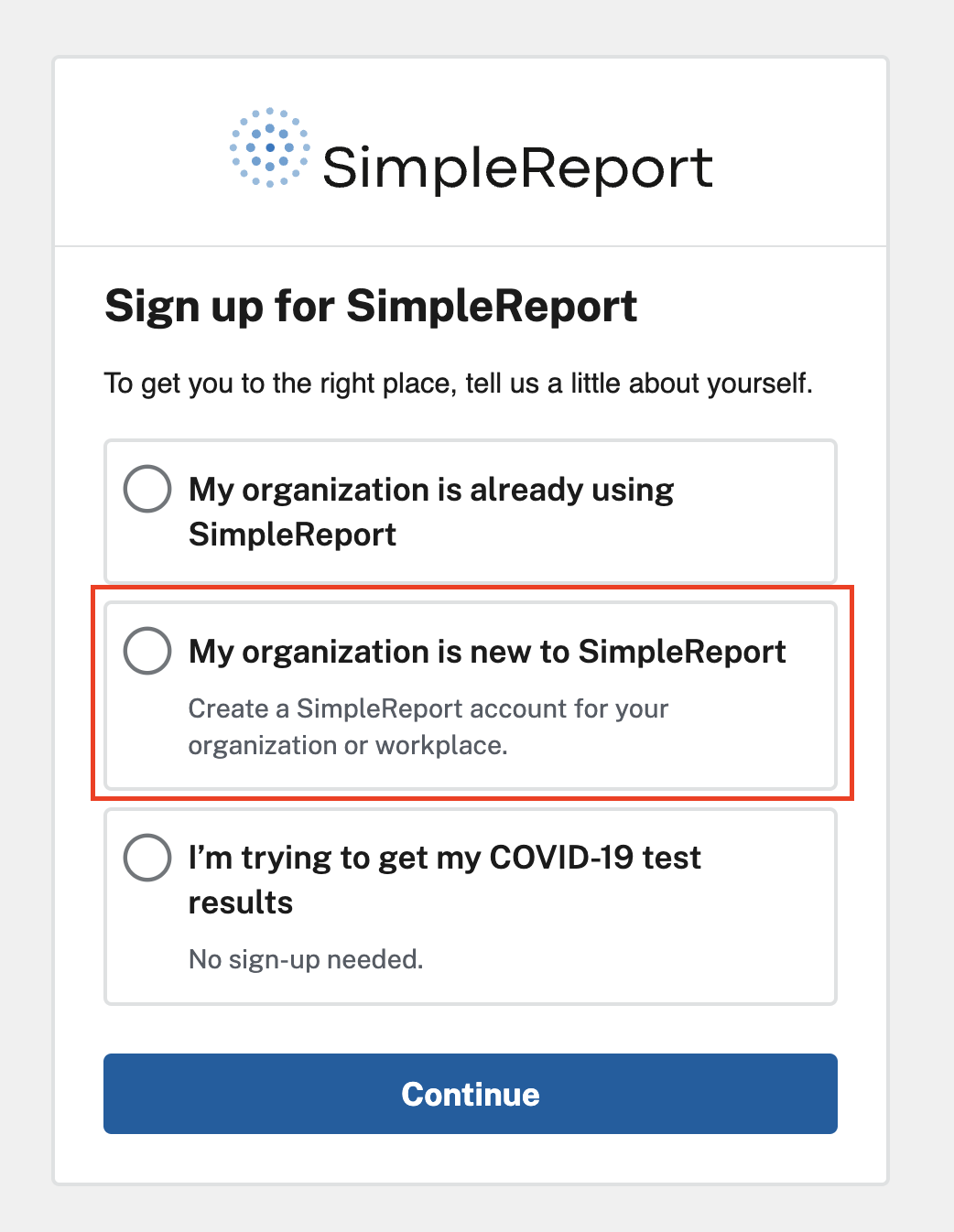
- Fill out the organization information (note that you will need to use a dummy email address, you’ll get an error if you try to register with an email already in the Okta system) and submit
- It’ll take you to a “personal details” form, which you don’t want to fill out - this is for the Experian automated ID verification flow, which is disabled and/or uses a dummy database for almost all lower environments.
- Go back to plain
{env}.simplereport.gov/app, and you should see the superadmin view if you’re part of the Okta groupSR-{ENV}-ADMINS(you may need to log out/in for the changes to take effect)
- If you don't see this view, ask a team member to add you to the Okta group
SR-{ENV}-ADMINS
- If you don't see this view, ask a team member to add you to the Okta group
- Go to “organizations pending identity verification” - it’s the first link
- Select and verify your organization.
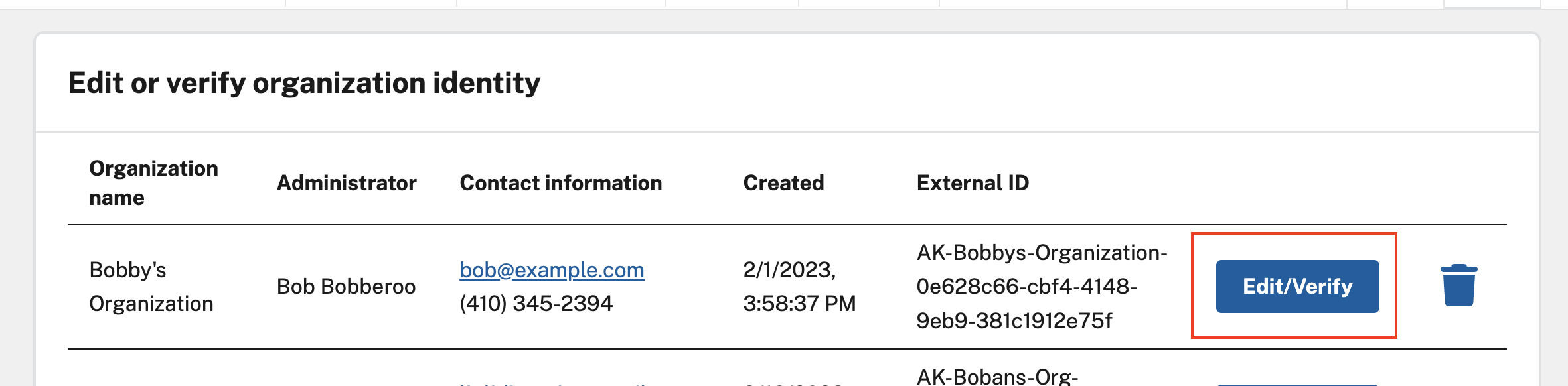
At this point, you have an organization that exists in both the database and as an Okta group! yay! However, you still can’t log into it...
8. Go back to the Okta preview admin view and find the Okta group for the org you just created. It’ll follow the pattern SR-{ENV}-TENANT:{State abbrv.}-{ORG-NAME}-{ORG EXTERNAL ID}

- Add yourself to the
ADMINandNO_ACCESSgroups for that organization - Go back to the environment and you should see the facility creation page this time! Which means you’ve successfully created the org, you’re in it, and now need to add a facility for it. (You may need to log in/out for the changes to take effect). Voila!
Note that it's advisable to do these separate tasks for your "real" and "dummy" user accounts in separate incognito browser windows.
You may wish to run the app locally with Okta enabled. To do so, be sure to follow setup instructions first to run the app.
Once you've completed setup, you can log in with your Okta credentials. At this point, you will need to follow the same steps for Setting up Okta for Testing in Lower Environments, see above.
- Make sure you have an account set up in Okta Preview
- Follow the steps outlined above to create a new organization, including creating an account with a dummy email address
- In Okta Preview, assign yourself to the appropriate groups
Ask a developer who already has production access to add you to "Real" Okta.
See Adding-a-Developer for instructions on the specific groups to add.
For more information about Okta and managing support requests through the Okta UI, see the docs repo wiki.
- Getting Started
- [Setup] Docker and docker compose development
- [Setup] IntelliJ run configurations
- [Setup] Running DB outside of Docker (optional)
- [Setup] Running nginx locally (optional)
- [Setup] Running outside of docker
- Accessing and testing weird parts of the app on local dev
- Accessing patient experience in local dev
- API Testing with Insomnia
- Cypress
- How to run e2e locally for development
- E2E tests
- Database maintenance
- MailHog
- Running tests
- SendGrid
- Setting up okta
- Sonar
- Storybook and Chromatic
- Twilio
- User roles
- Wiremock
- CSV Uploader
- Log local DB queries
- Code review and PR conventions
- SimpleReport Style Guide
- How to Review and Test Pull Requests for Dependabot
- How to Review and Test Pull Requests with Terraform Changes
- SimpleReport Deployment Process
- Adding a Developer
- Removing a developer
- Non-deterministic test tracker
- Alert Response - When You Know What is Wrong
- What to Do When You Have No Idea What is Wrong
- Main Branch Status
- Maintenance Mode
- Swapping Slots
- Monitoring
- Container Debugging
- Debugging the ReportStream Uploader
- Renew Azure Service Principal Credentials
- Releasing Changelog Locks
- Muting Alerts
- Architectural Decision Records
- Backend Stack Overview
- Frontend Overview
- Cloud Architecture
- Cloud Environments
- Database ERD
- External IDs
- GraphQL Flow
- Hibernate Lazy fetching and nested models
- Identity Verification (Experian)
- Spring Profile Management
- SR Result bulk uploader device validation logic
- Test Metadata and how we store it
- TestOrder vs TestEvent
- ReportStream Integration
- Feature Flag Setup
- FHIR Resources
- FHIR Conversions
- Okta E2E Integration
- Deploy Application Action
- Slack notifications for support escalations
- Creating a New Environment Within a Resource Group
- How to Add and Use Environment Variables in Azure
- Web Application Firewall (WAF) Troubleshooting and Maintenance
- How to Review and Test Pull Requests with Terraform Changes