-
Notifications
You must be signed in to change notification settings - Fork 39
Tutorial 7: ISP Security Demonstrator SDN 2016
The goal of this tutorial is to setup a small RINA-based service provider network which hides most of its DIFs from customers or peer providers. The tutorial illustrates the isolation that DIFs provide, showing that rogue customers / peers can only compromise e-mall DIFs and to do that they would need access to the key material providing authentication and SDU Protection policies are in place. This scenario, demonstrated at the SDN World Congress 2016, has been setup with the demonstrator, using an IRATI image with a pristine-1.5 branch snapshot.
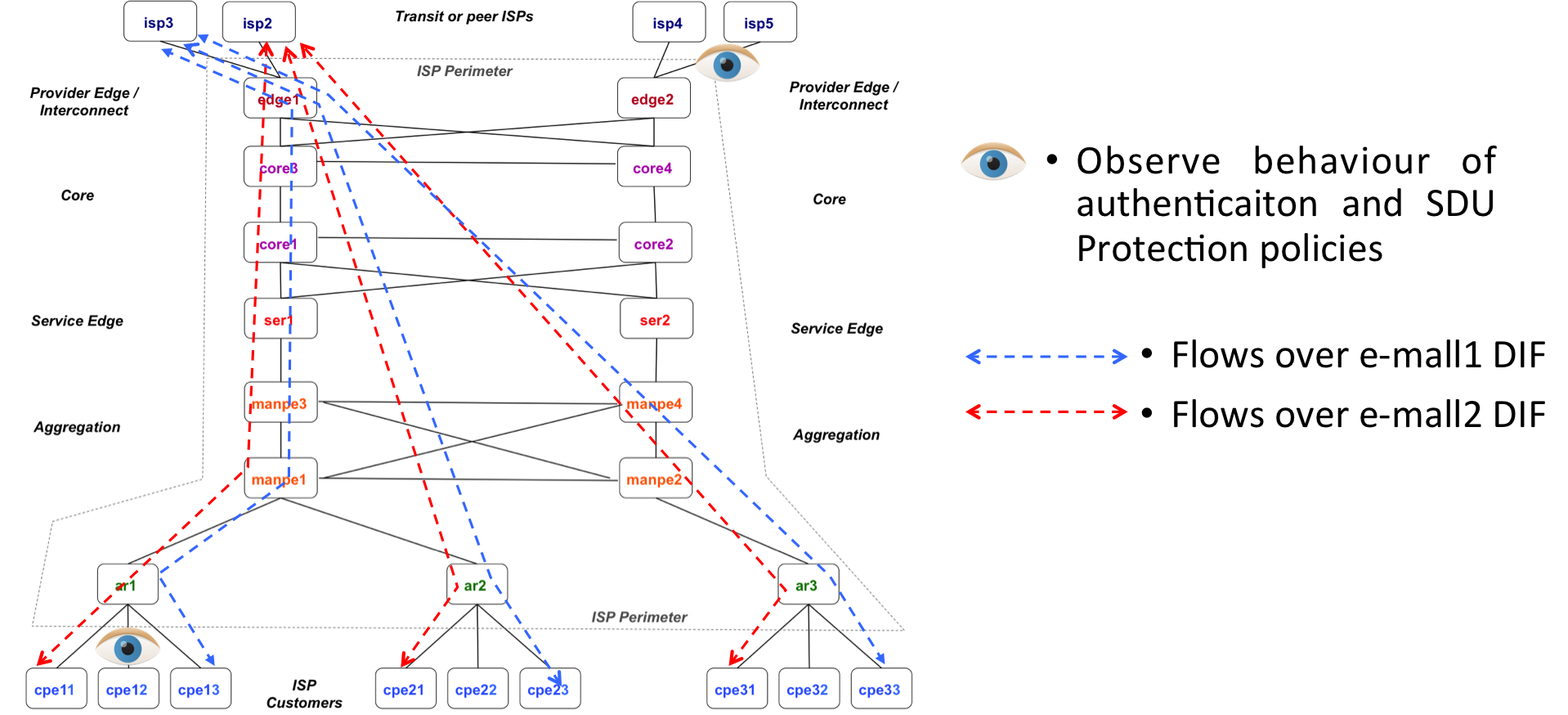
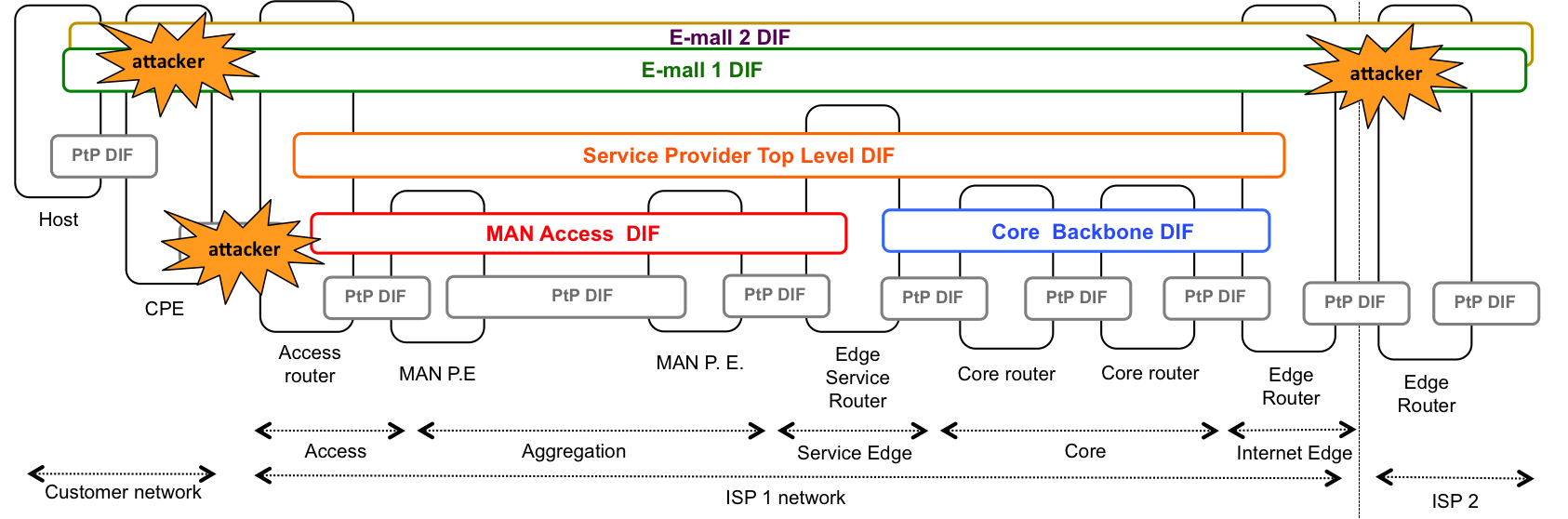
The service provider scenario is depicted in the two images above. The first one shows the 28 systems that are part of the demo: 9 CPE routers belonging to customers, 3 access routers, 4 Metropolitan area aggregation routers, 2 edge service routers, 4 core routers, 2 edge interconnection routers and 4 edge routers from different providers. The second one shows the DIF structure of the provider network, with different DIFs providing metro aggregation, core transport and service differentiation within the provider network. The only DIFs that are shared with customers and peers in this configuration are the "e-mall" DIFs (the DIFs that directly support applications).
The Demonstrator is command-line tool (gen.py) which allows the user to easily try and test the IRATI stack in a multi-node scenario. Each node is implemented using a light Virtual Machine (VM), run under the control of the QEMU hypervisor. All the VMs are run locally without any risk for your PC, so you don't need a dedicated machine or multiple physical machines.
To install the demonstrator you need a physical Linux machine with support for QEMU and KVM. To obtain the demonstrator, just clone its repository:
git clone https://github.com/IRATI/demonstrator.git
After that cd into the demonstrator directory.
Before running the scenario, we will take a look at the ISP security demo configuration file, located at examples/isp-sec.conf.
eth 110 0Mbps cpe11 ar1
eth 120 0Mbps cpe12 ar1
eth 130 0Mbps cpe13 ar1
eth 210 0Mbps cpe21 ar2
eth 220 0Mbps cpe22 ar2
eth 230 0Mbps cpe23 ar2
eth 310 0Mbps cpe31 ar3
eth 320 0Mbps cpe32 ar3
eth 330 0Mbps cpe33 ar3
eth 100 0Mbps ar1 manpe1
eth 200 0Mbps ar2 manpe1
eth 300 0Mbps ar3 manpe2
eth 410 0Mbps manpe1 manpe2
eth 411 0Mbps manpe1 manpe3
eth 412 0Mbps manpe1 manpe4
eth 420 0Mbps manpe2 manpe3
eth 421 0Mbps manpe2 manpe4
eth 430 0Mbps manpe3 manpe4
eth 510 0Mbps manpe3 ser1
eth 520 0Mbps manpe4 ser2
eth 600 0Mbps ser1 core1
eth 610 0Mbps ser1 core2
eth 620 0Mbps ser2 core1
eth 630 0Mbps ser2 core2
eth 700 0Mbps core1 core2
eth 710 0Mbps core1 core3
eth 720 0Mbps core2 core4
eth 730 0Mbps core3 core4
eth 640 0Mbps core3 edge1
eth 650 0Mbps core4 edge1
eth 660 0Mbps core3 edge2
eth 670 0Mbps core4 edge2
eth 800 0Mbps edge1 isp2
eth 810 0Mbps edge1 isp3
eth 820 0Mbps edge2 isp4
eth 830 0Mbps edge2 isp5
# DIF core
dif core ser1 600 610
dif core ser2 620 630
dif core core1 600 620 700 710
dif core core2 610 630 700 720
dif core core3 640 660 710 730
dif core core4 650 670 720 730
dif core edge1 640 650
dif core edge2 660 670
# DIF access
dif access ar1 100
dif access ar2 200
dif access ar3 300
dif access manpe1 100 200 410 411 412
dif access manpe2 300 410 420 421
dif access manpe3 411 420 430 510
dif access manpe4 412 421 430 520
dif access ser1 510
dif access ser2 520
# DIF service
dif service ar1 access
dif service ar2 access
dif service ar3 access
dif service ser1 access core
dif service ser2 access core
dif service edge1 core
dif service edge2 core
# DIF emall1
dif emall1 cpe11 110
dif emall1 cpe12 120
dif emall1 cpe21 210
dif emall1 cpe22 220
dif emall1 cpe31 310
dif emall1 ar1 110 120 service
dif emall1 ar2 210 220 service
dif emall1 ar3 310 service
dif emall1 edge1 service 800
dif emall1 edge2 service 820
dif emall1 isp2 800
dif emall1 isp4 820
# DIF emall2
dif emall2 cpe13 130
dif emall2 cpe23 230
dif emall2 cpe32 320
dif emall2 cpe33 330
dif emall2 ar1 130 service
dif emall2 ar2 230 service
dif emall2 ar3 320 330 service
dif emall2 edge1 service 810
dif emall2 edge2 service 830
dif emall2 isp3 810
dif emall2 isp5 830
#policies
policy emall1 * security-manager.auth.default PSOC_authentication-ssh2 keyExchangeAlg=EDH keystore=/creds/ssh2 keystorePass=test
policy emall1 * security-manager.encrypt.default default encryptAlg=AES128 macAlg=SHA256 compressAlg=deflate
policy emall1 ar1,ar2,ar3,edge1,edge2 security-manager.auth.service PSOC_authentication-none
policy emall2 * security-manager.auth.default PSOC_authentication-ssh2 keyExchangeAlg=EDH keystore=/creds/ssh2 keystorePass=test
policy emall2 * security-manager.encrypt.default default encryptAlg=AES128 macAlg=SHA256 compressAlg=deflate
policy emall2 ar1,ar2,ar3,edge1,edge2 security-manager.auth.service PSOC_authentication-none
#Enrollments
enroll access ar1 manpe1 100
enroll access ar2 manpe1 200
enroll access ar3 manpe2 300
enroll access ser1 manpe3 510
enroll access ser2 manpe4 520
enroll access manpe1 manpe2 410
enroll access manpe1 manpe3 411
enroll access manpe1 manpe4 412
enroll access manpe2 manpe3 420
enroll access manpe2 manpe4 421
enroll access manpe3 manpe4 430
enroll core core1 core2 700
enroll core core1 core3 710
enroll core core2 core4 720
enroll core core3 core4 730
enroll core ser1 core1 600
enroll core ser1 core2 610
enroll core ser2 core1 620
enroll core ser2 core2 630
enroll core edge1 core3 640
enroll core edge1 core4 650
enroll core edge2 core3 660
enroll core edge2 core4 670
enroll service edge1 edge2 core
enroll service edge1 ser1 core
enroll service edge1 ser2 core
enroll service edge2 ser1 core
enroll service edge2 ser2 core
enroll service ser1 ser2 core
enroll service ar1 ser1 access
enroll service ar1 ser2 access
enroll service ar2 ser1 access
enroll service ar2 ser2 access
enroll service ar3 ser1 access
enroll service ar3 ser2 access
enroll emall1 cpe11 ar1 110
enroll emall1 cpe12 ar1 120
enroll emall1 cpe21 ar2 210
enroll emall1 cpe22 ar2 220
enroll emall1 cpe31 ar3 310
enroll emall1 ar1 edge1 service
enroll emall1 ar1 edge2 service
enroll emall1 ar2 edge1 service
enroll emall1 ar2 edge2 service
enroll emall1 ar3 edge1 service
enroll emall1 ar3 edge2 service
enroll emall1 edge1 edge2 service
enroll emall1 isp2 edge1 800
enroll emall1 isp4 edge2 820
enroll emall2 cpe13 ar1 130
enroll emall2 cpe23 ar2 230
enroll emall2 cpe32 ar3 320
enroll emall2 cpe33 ar3 330
enroll emall2 ar1 edge1 service
enroll emall2 ar1 edge2 service
enroll emall2 ar2 edge1 service
enroll emall2 ar2 edge2 service
enroll emall2 ar3 edge1 service
enroll emall2 ar3 edge2 service
enroll emall2 edge1 edge2 service
enroll emall2 isp3 edge1 810
enroll emall2 isp5 edge2 830
#Overlays
overlay ar1 overlays/ispsec/ar1
overlay ar2 overlays/ispsec/ar2
overlay ar3 overlays/ispsec/ar3
overlay cpe11 overlays/ispsec/cpe11
overlay cpe12 overlays/ispsec/cpe12
overlay cpe13 overlays/ispsec/cpe13
overlay cpe21 overlays/ispsec/cpe21
overlay cpe22 overlays/ispsec/cpe22
overlay cpe23 overlays/ispsec/cpe23
overlay cpe31 overlays/ispsec/cpe31
overlay cpe32 overlays/ispsec/cpe32
overlay cpe33 overlays/ispsec/cpe33
overlay edge1 overlays/ispsec/edge1
overlay edge2 overlays/ispsec/edge2
overlay isp2 overlays/ispsec/isp2
overlay isp3 overlays/ispsec/isp3
overlay isp4 overlays/ispsec/isp4
overlay isp5 overlays/ispsec/isp5
In addition to creating the machines and the DIFs, we specify the security policies for the emall1 and emall2 DIFs (authentication and encryption between all the provider-customer and provider-other provider IPCPs) and also instruct the demonstrator to copy the files holding the credentials to the different VMs.
Go back to the main demonstrator folder, and type the following command:
./gen.py -m 1024 -e manual --vhost -f virtio-net-pci -c examples/isp-sec.conf
This will generate a number of configuration files and two scripts: up.sh and down.sh. In this case we are using VMs with 1024 MBs of RAM, you can run smaller machines (512 or even 256 if you don't plan to run rina-tgen should be ok). We are also telling the script to make the enrollments written down in the configuration file (manual option) as long as they have connectivity via an N-1 DIF. The text output after running this script should be the following one:
./gen.py --vhost -m 1024 -e manual -f virtio-net-pci -c examples/isp-sec.conf
You want to run a lot of nodes, so it's better if I give each node some time to boot (since the boot is CPU-intensive)
I am going to enroll ar1 to DIF access against neighbor manpe1, through lower DIF 100
I am going to enroll ar2 to DIF access against neighbor manpe1, through lower DIF 200
I am going to enroll ar3 to DIF access against neighbor manpe2, through lower DIF 300
I am going to enroll ser1 to DIF access against neighbor manpe3, through lower DIF 510
I am going to enroll ser2 to DIF access against neighbor manpe4, through lower DIF 520
I am going to enroll manpe1 to DIF access against neighbor manpe2, through lower DIF 410
I am going to enroll manpe1 to DIF access against neighbor manpe3, through lower DIF 411
I am going to enroll manpe1 to DIF access against neighbor manpe4, through lower DIF 412
I am going to enroll manpe2 to DIF access against neighbor manpe3, through lower DIF 420
I am going to enroll manpe2 to DIF access against neighbor manpe4, through lower DIF 421
I am going to enroll manpe3 to DIF access against neighbor manpe4, through lower DIF 430
I am going to enroll core1 to DIF core against neighbor core2, through lower DIF 700
I am going to enroll core1 to DIF core against neighbor core3, through lower DIF 710
I am going to enroll core2 to DIF core against neighbor core4, through lower DIF 720
I am going to enroll core3 to DIF core against neighbor core4, through lower DIF 730
I am going to enroll ser1 to DIF core against neighbor core1, through lower DIF 600
I am going to enroll ser1 to DIF core against neighbor core2, through lower DIF 610
I am going to enroll ser2 to DIF core against neighbor core1, through lower DIF 620
I am going to enroll ser2 to DIF core against neighbor core2, through lower DIF 630
I am going to enroll edge1 to DIF core against neighbor core3, through lower DIF 640
I am going to enroll edge1 to DIF core against neighbor core4, through lower DIF 650
I am going to enroll edge2 to DIF core against neighbor core3, through lower DIF 660
I am going to enroll edge2 to DIF core against neighbor core4, through lower DIF 670
I am going to enroll edge1 to DIF service against neighbor edge2, through lower DIF core
I am going to enroll edge1 to DIF service against neighbor ser1, through lower DIF core
I am going to enroll edge1 to DIF service against neighbor ser2, through lower DIF core
I am going to enroll edge2 to DIF service against neighbor ser1, through lower DIF core
I am going to enroll edge2 to DIF service against neighbor ser2, through lower DIF core
I am going to enroll ser1 to DIF service against neighbor ser2, through lower DIF core
I am going to enroll ar1 to DIF service against neighbor ser1, through lower DIF access
I am going to enroll ar1 to DIF service against neighbor ser2, through lower DIF access
I am going to enroll ar2 to DIF service against neighbor ser1, through lower DIF access
I am going to enroll ar2 to DIF service against neighbor ser2, through lower DIF access
I am going to enroll ar3 to DIF service against neighbor ser1, through lower DIF access
I am going to enroll ar3 to DIF service against neighbor ser2, through lower DIF access
I am going to enroll cpe13 to DIF emall2 against neighbor ar1, through lower DIF 130
I am going to enroll cpe23 to DIF emall2 against neighbor ar2, through lower DIF 230
I am going to enroll cpe32 to DIF emall2 against neighbor ar3, through lower DIF 320
I am going to enroll cpe33 to DIF emall2 against neighbor ar3, through lower DIF 330
I am going to enroll ar1 to DIF emall2 against neighbor edge1, through lower DIF service
I am going to enroll ar1 to DIF emall2 against neighbor edge2, through lower DIF service
I am going to enroll ar2 to DIF emall2 against neighbor edge1, through lower DIF service
I am going to enroll ar2 to DIF emall2 against neighbor edge2, through lower DIF service
I am going to enroll ar3 to DIF emall2 against neighbor edge1, through lower DIF service
I am going to enroll ar3 to DIF emall2 against neighbor edge2, through lower DIF service
I am going to enroll edge1 to DIF emall2 against neighbor edge2, through lower DIF service
I am going to enroll isp3 to DIF emall2 against neighbor edge1, through lower DIF 810
I am going to enroll isp5 to DIF emall2 against neighbor edge2, through lower DIF 830
I am going to enroll cpe11 to DIF emall1 against neighbor ar1, through lower DIF 110
I am going to enroll cpe12 to DIF emall1 against neighbor ar1, through lower DIF 120
I am going to enroll cpe21 to DIF emall1 against neighbor ar2, through lower DIF 210
I am going to enroll cpe22 to DIF emall1 against neighbor ar2, through lower DIF 220
I am going to enroll cpe31 to DIF emall1 against neighbor ar3, through lower DIF 310
I am going to enroll ar1 to DIF emall1 against neighbor edge1, through lower DIF service
I am going to enroll ar1 to DIF emall1 against neighbor edge2, through lower DIF service
I am going to enroll ar2 to DIF emall1 against neighbor edge1, through lower DIF service
I am going to enroll ar2 to DIF emall1 against neighbor edge2, through lower DIF service
I am going to enroll ar3 to DIF emall1 against neighbor edge1, through lower DIF service
I am going to enroll ar3 to DIF emall1 against neighbor edge2, through lower DIF service
I am going to enroll edge1 to DIF emall1 against neighbor edge2, through lower DIF service
I am going to enroll isp2 to DIF emall1 against neighbor edge1, through lower DIF 800
I am going to enroll isp4 to DIF emall1 against neighbor edge2, through lower DIF 820
Just execute the up.sh script. This will create all required software bridges and virtual Ethernet interfaces in the hosts, create the VMs, copy the configuration files to each machine, run RINA and trigger enrollments. Since this scenario is quite large it may take something in the 5-10 minutes region for the up.sh script to finalize.
The demonstrator has a convenient script for ssh'ing into each one of the machines, called access.sh and located at the main demonstrator folder. To access any given machine, you just need to call the script passing the name of the machine as argument (name of the machine as specified in the demonstrator configuration file). For example, let's access isp2 and start a rina-tgen server:
./access.sh isp2
./access.sh: 3: ./access.sh: source: not found
./access.sh: 6: [: tor1: unexpected operator
./access.sh: 12: [: 2257: unexpected operator
Accessing buildroot VM isp2
Warning: Permanently added '[localhost]:2257' (ECDSA) to the list of known hosts.
# rina-tgen -l
And now we will access cpe11 and allocate a flow
./access.sh cpe11
./access.sh: 3: ./access.sh: source: not found
./access.sh: 6: [: tor1: unexpected operator
./access.sh: 12: [: 2257: unexpected operator
Accessing buildroot VM cpe11
Warning: Permanently added '[localhost]:2257' (ECDSA) to the list of known hosts.
# rina-tgen --duration 20 -s 1450
4529(1482498219)#librina.logs (DBG): New log level: INFO
4529(1482498219)#librina.nl-manager (INFO): Netlink socket connected to local port 4529
4529(1482498219)#traffic-generator (INFO): starting test
4529(1482498239)#traffic-generator (INFO): sent statistics: 64946 SDUs, 90924400 bytes in 20006525 us, 36.3579 Mb/s
To quit the machine we just need to type the exit command from the machine's command prompt.
To stop the VMs and destroy any virtual interfaces and software bridges create by up.sh, we just need to execute the down.sh script from the main demonstrator folder. If we also want to clean up all the config files generated for the scenario (to be able to generate files for other ones, for example), we just need to call the clean.sh script.
- Home
- Software Architecture Overview
- IRATI in depth
-
Tutorials
- 1. DIF-over-a-VLAN-(point-to-point-DIF)
- 2. DIF over two VLANs
- 3. Security experiments on small provider net
- 4. Multi-tenant Data Centre Network configured via the NMS-DAF
- 5. Congestion control in multi-tenant DC
- 6. Multi-tenant Data Centre network with Demonstrator
- 7. ISP Security with Demonstrator
- 8. Renumbering in a single DIF
- 9. Application discovery and Distributed Mobility Management over WiFi
- 10. Distributed Mobility Management over multiple providers
- 11. Multi-access: multiple providers, multiple technologies