-
Notifications
You must be signed in to change notification settings - Fork 2.3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
On startup disable connections to google domains. #514
Comments
|
what are the full urls? These domains are used for different services |
|
for instance, clients2.google.com is used for extension updates so that might be widevine which I believe is expected - cc @bbondy |
|
switches::kDisableDomainReliability should be set to |
|
@bridiver I think widevine should only be called once widevine opt in is clicked at least once. So it's unexpected to me to be at startup. If it's from extensions though that code will be changing to always to go to a new server that redirects to the chrome server as needed. |
|
maybe add logging to the system network delegate @bridiver to see full URLs. |
|
On Windows it could be helpful to use procmon + filter on network events + brave pdb symbols + look on stack to see what is the point in code issues the request. This hadn't work, could see only kernel stack. |
|
I know at least some of these are domain reliability so I think we should go ahead and disable that before checking again |
|
although I think domain reliability reports shouldn't be sent if metrics reporting is disabled |
Partially addresses brave/brave-browser#514
This was true btw, so it's not on by default. But I added the switch anyway in case it is enabled. |
|
PR for disabling the domain reliability service is here: These are the only URLs coming up in the system context: I applied this patch to log it: Could you give extra steps for how to reproduce? Or am I possibly testing the wrong way? |
|
STR:
|
This disables connecting to client2.google.com, google.com and googleusercontent.com at startup. The service is meant to select which google services you need for your region. Addresses brave/brave-browser#514
|
Should be good to go now with disabling Google URL tracker and domain reliability service. |
|
Sounds good. Here is the backlog issue: #527 |
|
Verification passes since #512 is also verified and work continues in #527 (@kjozwiak is this acceptable for you?)
I have checked with Fiddler and these are the domains that Brave tries to connect to on startup: The work is still in progress: #527, but once it is done, we need to recheck this issue Verified passed with
Verification Passed on
|
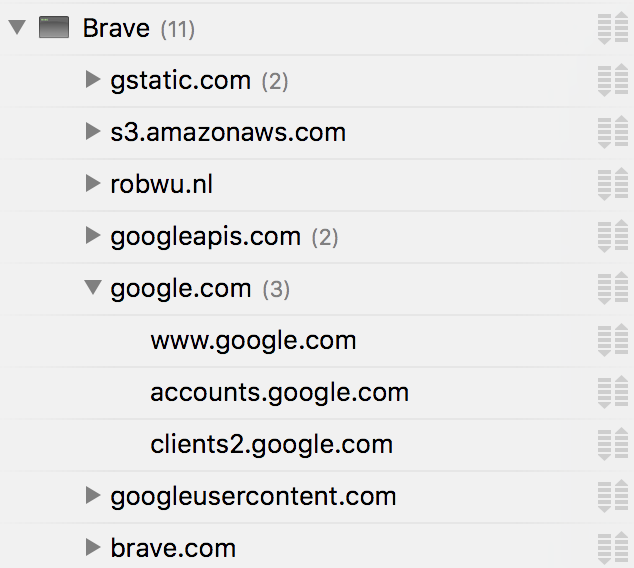
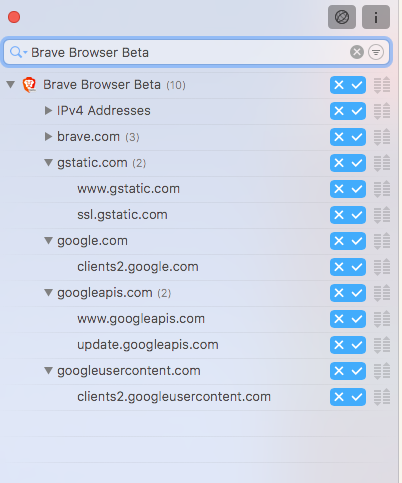
On startup brave connects to the following domains.
bc.googleusercontent.com
clients2.google.com
accounts.google.com
This might be a dupe of #512. Verify after the issue is addressed.
The text was updated successfully, but these errors were encountered: