-
Notifications
You must be signed in to change notification settings - Fork 37
Certificate setup
Philip Helger edited this page Feb 11, 2023
·
20 revisions
This page explains how to create a valid Java keystore (JKS) for usage with OpenPeppol SMP. This is surely not the only way, but one that worked for me.
The following prerequisites must be fulfilled to create the certificate:
- Install the necessary tool (see below)
- Install JDK 8 latest (for
keytool) - You received the Peppol certificates (pilot and or production, AP and/or SMP).
- Ensure Java 1.8 or later is installed
- Download KeyStore Explorer - see https://keystore-explorer.org/
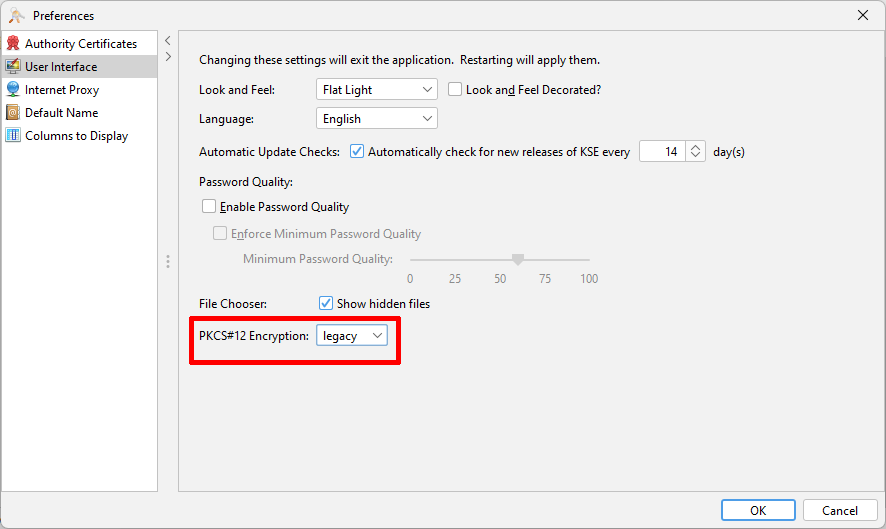
- Since KeyStore Explorer v5.5.2 there is a new setting "PKCS#12 Encryption". Ensure to set this to "legacy" if you are using PKCS#12.
- Open your existing Peppol SMP certificate in KeyStore Explorer
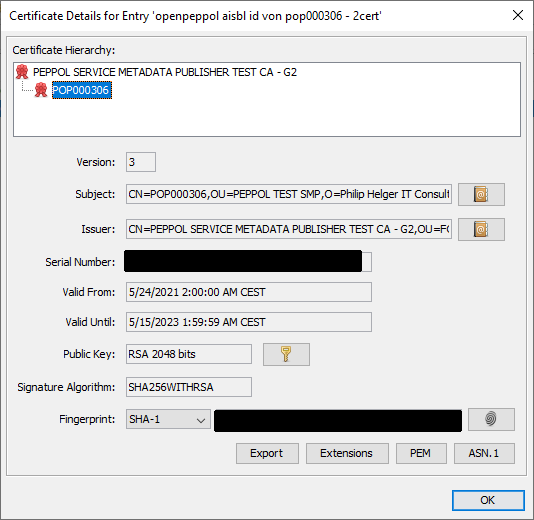
- Double click on the single entry (alias) and verify, that the "Certificate Hierarchy" contains a tree of 2 certificates. If your certificates does not contain a hierarchy of 2, don't follow this guide.
- What you now need is the matching OpenPeppol ROOT certificates. Go to https://openpeppol.atlassian.net/wiki/spaces/OPMA/pages/193069072/Introduction+to+the+revised+PKI+Certificate+infrastructure+and+issuing+process#IntroductiontotherevisedPKICertificateinfrastructureandissuingprocess-Requirements and download
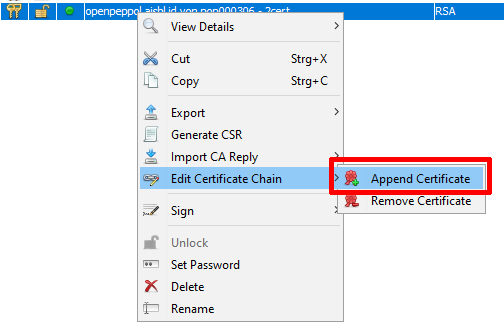
Peppol_Test_Root_CA.cer(for Test SMP) orPeppol_Root_CA.cer(for production SMP). - Now right click on the alias, and choose "Append certificate" (you should be asked for the password of the key):
- Now choose the matching OpenPeppol ROOT certificate downloaded in a previous step
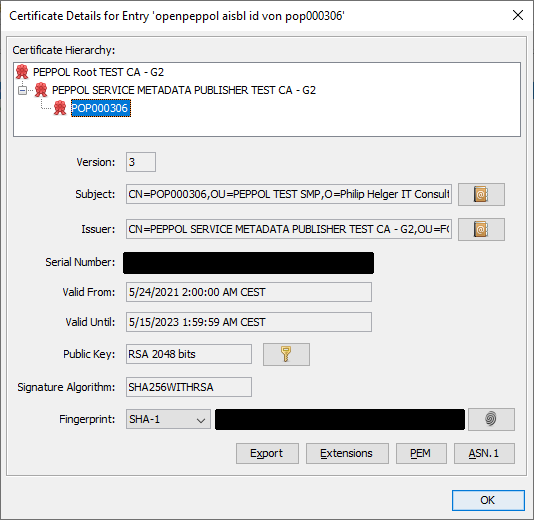
- Now verify, that you have a certificate hierarchy of 3:
- Ensure to save the keystore and you should be good to go
Steps to perform (tested on Windows 7 and Windows 10):
- Install OpenSSL latest - see e.g. https://wiki.openssl.org/index.php/Binaries
- Install JDK 1.8 or newer (for
keytool) - Copy all relevant OpenPeppol root certificates into a single file called "truststore_xxx.pem" (simply copy pasting in the text editor, one after the other). One for pilot, one for production. Order: ROOT certificate first, than SMP certificate. You may also download them from here: truststore_test_v3.pem or truststore_prod_v3.pem. Than copy the matching file into the directory where the certificate resides. Note: the term "pilot" in the old PKI was changed to "test" in the new PKI.
- Perform steps as described in the Enrollment mail. Don't forget the enrollment code you should have received via SMS.
- When exporting the certificates from your browser, the following text assumes you are using the password
passwd(it is used in the examples below). - Export the private key from the p12 file:
- SMP Test:
openssl pkcs12 -in smp-test.p12 -passin pass:passwd -nocerts -out smp-test.key -passout pass:passwd - SMP Production:
openssl pkcs12 -in smp-prod.p12 -passin pass:passwd -nocerts -out smp-prod.key -passout pass:passwd
- SMP Test:
- Export the public certificate from the p12 file:
- SMP Test:
openssl pkcs12 -in smp-test.p12 -passin pass:passwd -clcerts -nokeys -out smp-test.cer - SMP Production:
openssl pkcs12 -in smp-prod.p12 -passin pass:passwd -clcerts -nokeys -out smp-prod.cer
- SMP Test:
- Combine CER (public part) and KEY (private part) into a single PKCS12 keystore using the full chain. This steps requires the truststore files from step 1 (see above). When asked for the key password, use the one from step 4 (
passwdif you copy pasted the command).- SMP Test:
openssl pkcs12 -export -in smp-test.cer -inkey smp-test.key -out smp-test-complete.p12 -name smp-test -passout pass:passwd -certfile truststore_test_v3.pem - SMP Production:
openssl pkcs12 -export -in smp-prod.cer -inkey smp-prod.key -out smp-prod-complete.p12 -name smp-prod -passout pass:passwd -certfile truststore_prod_v3.pem - The outcome of this step are the files
smp-test-complete.p12with aliassmp-testandsmp-prod-complete.p12with aliassmp-prod.
- SMP Test:
- Convert the PKCS12 keystores to JKS keystores. I'm using the application
keytoolthat is part of the Java JDK (not in JRE!) - again with the passwordpasswd:- SMP Pilot:
"%java_home%\bin\keytool" -importkeystore -srckeystore smp-test-complete.p12 -srcstoretype PKCS12 -srcstorepass passwd -alias smp-test -destkeystore smp-test.jks -deststorepass passwd -destkeypass passwd - SMP Production:
"%java_home%\bin\keytool" -importkeystore -srckeystore smp-prod-complete.p12 -srcstoretype PKCS12 -srcstorepass passwd -alias smp-prod -destkeystore smp-prod.jks -deststorepass passwd -destkeypass passwd - The outcome of this step are the files
smp-test.jksandsmp-prod.jks. - Note: this step is optional. phoss SMP also supports PKCS12 based keystores and truststores. The respective
.typesetting must however bePKCS12compared toJKSfor JKS keystores.
- SMP Pilot:
- Done! Now place the keystore in correct place as outlined in Configuration
It is appreciated if you star the GitHub project if you like it.
Donation link: https://paypal.me/PhilipHelger

- Home
- News and noteworthy
- Migrations
- Download
- Features
- Configuration
- Running
- Source related
- Other information
- Future plans
- License
- Release Tasks