Ory Hydra, the OAuth2 and OpenID Connect server designed for web-scale deployments introduces over 6x higher OAuth2 throughput on a single PostgreSQL instance!
Want to check out Ory Hydra yourself? Try common OAuth2 flows in the Ory OAuth2 Get Started guide!
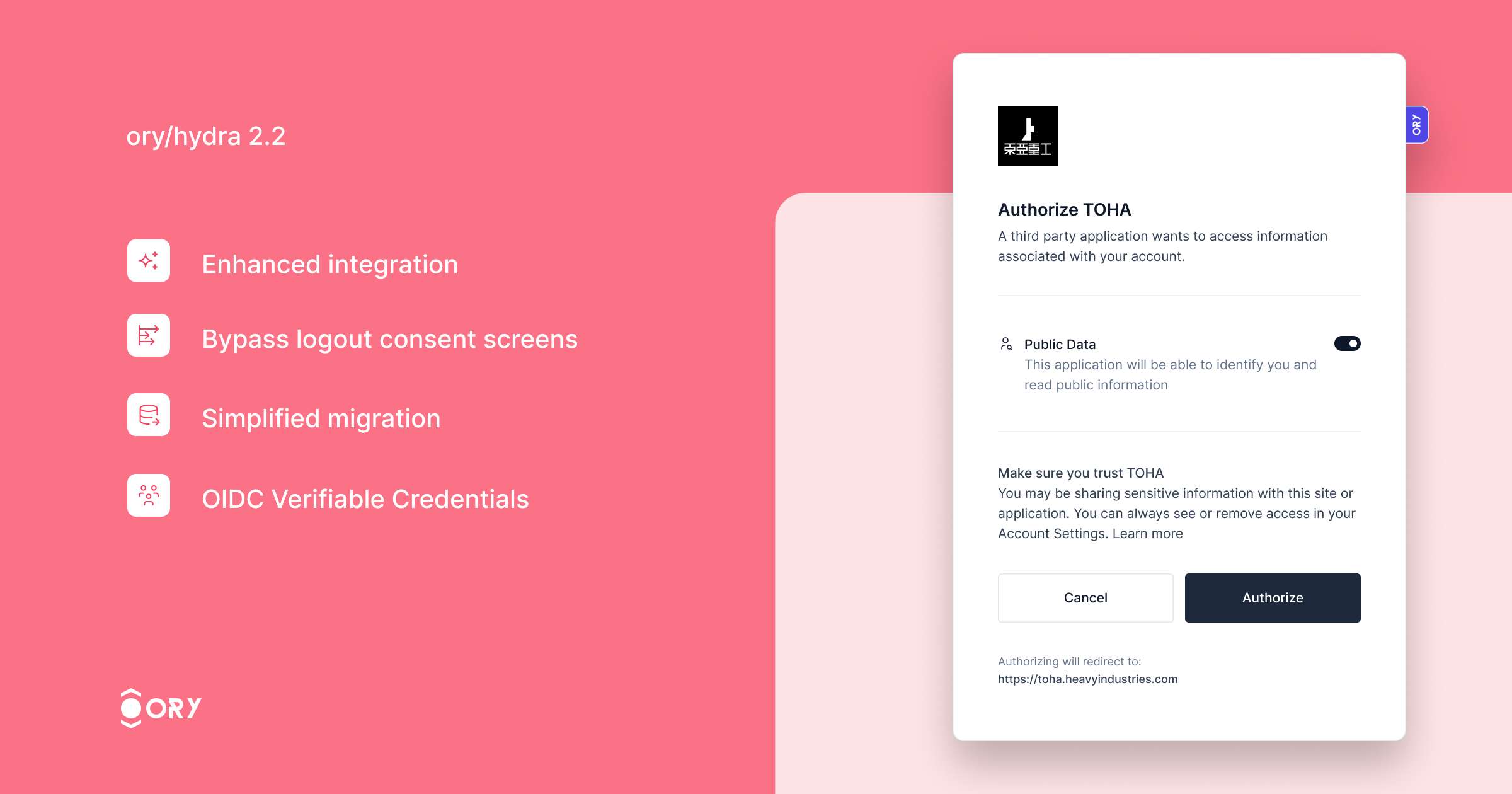
This version significantly enhances performance, processing over 6x more authorization flows than version 2.1, thanks to architectural improvements that minimize database interactions for login and consent processes.
Key improvements include:
- Enhanced integration with Ory Kratos, ensuring seamless synchronization of login and logout states across both services. Users logged out from Ory Hydra will automatically log out from Ory Kratos, enhancing security and user experience.
- The ability to bypass the logout consent screen for specific clients, streamlining the logout process.
- Simplified migration with the new feature to import OAuth2 Client IDs, making the transition to Ory Hydra smoother.
- Support for the OIDC Verifiable Credentials specification, expanding the server's capabilities in identity verification.
Thank all contributors who have made this release available!
Bug Fixes
-
Return empty slice if requested_scope or audience is null (#3711) (65165e7)
-
Correct id token type in token exchange response (#3625) (d1f9ba8):
Closes ory/client-go#2
-
Handle subject mismatch gracefully (#3619) (af0d477):
We now redirect to the original request URL if the subjects between
the remembered Hydra session and what was confirmed by the login
screen does not match. -
Handle token hook auth config (#3677) (1a40833):
- fix: handle token hook auth config
- fix: bump golangci-lint
-
Incorrect down migration (#3708) (8812e0e), closes /github.com/ory/hydra/pull/3705#discussion_r1471514014
-
Timeout in jwt-bearer grants when too many grants are available (#3692) (a748797)
-
Deflake ttl test (6741a49)
-
Only query access tokens by hashed signature (a21e945)
-
Reject invalid JWKS in client configuration / dependency cleanup and bump (#3603) (1d73d83)
-
Restore ability to override auth and token urls for exemplary app (#3590) (dfb129a)
-
Return proper error when the grant request cannot be parsed (#3558) (26f2d34)
Documentation
Features
-
Add prompt=registration (#3636) (19857d2):
Ory Hydra now supports a
registrationvalue for thepromptparameter of
the authorization request. When specifyingprompt=registration, Ory Hydra
will redirect the user to the URL found underurls.registration
(instead ofurls.login). -
Add skip_logout_consent option to clients (#3705) (2a653e6):
Adds a special field which disables the logout consent screen when performing OIDC logout.
-
Re-enable legacy client IDs (#3628) (5dd7d30):
This patch changes the primary key of the
hydra_clienttable. We do not expect issues, as that table is probably not overly huge in any deployment. We do however highly recommend to test the migration performance on a staging environment with a similar database setup. -
Remove flow cookie (#3639) (cde3a30):
This patch removes the flow cookie. All information is already tracked in the request query parameters as part of the {login|consent}_{challenge|verifier}.
-
Remove login session cookie during consent flow (#3667) (5f41949)
-
Add more resolution to events and collect client metrics (#3568) (466e66b)
-
Add state override (b8b9154)
-
Add support for OIDC VC (#3575) (219a7c0):
This adds initial support for issuing verifiable credentials
as specified in https://openid.net/specs/openid-connect-userinfo-vc-1_0.html.Because the spec is still in draft, public identifiers are
suffixed withdraft_00. -
Allow to disable claim mirroring (#3563) (c72a316):
This PR introduces another config option called
oauth2:mirror_top_level_claimswhich may be used to disable the mirroring of custom claims into theextclaim of the jwt.
This new config option is an opt-in. If unused the behavior remains as-is to ensure backwards compatibility.Example:
oauth2: allowed_top_level_claims: - test_claim mirror_top_level_claims: false # -> this will prevent test_claim to be mirrored within ext
Closes #3348
-
Bump fosite and add some more tracing (0b56f53)
-
cmd: Add route that redirects to the auth code url (4db6416)
-
Propagate logout to identity provider (#3596) (c004fee):
- feat: propagate logout to identity provider
This commit improves the integration between Hydra and Kratos when logging
out the user.This adds a new configuration key for configuring a Kratos admin URL.
Additionally, Kratos can send a session ID when accepting a login request.
If a session ID was specified and a Kratos admin URL was configured,
Hydra will disable the corresponding Kratos session through the admin API
if a frontchannel or backchannel logout was triggered.- fix: add special case for MySQL
- chore: update sdk
- chore: consistent naming
- fix: cleanup persister
-
Support different jwt scope claim strategies (#3531) (45da11e)
Changelog
- b346f90 autogen(docs): generate and bump docs
- 01aeffc autogen(docs): regenerate and update changelog
- 3a65840 autogen(docs): regenerate and update changelog
- 2dc52b4 autogen(docs): regenerate and update changelog
- 7473259 autogen(docs): regenerate and update changelog
- 4b8c971 autogen(docs): regenerate and update changelog
- d0dfc0f autogen(docs): regenerate and update changelog
- 9e9be2d autogen(docs): regenerate and update changelog
- ada59a5 autogen(docs): regenerate and update changelog
- cdd2647 autogen(docs): regenerate and update changelog
- e4c160f autogen(docs): regenerate and update changelog
- 5121dba autogen(docs): regenerate and update changelog
- 21e0a9b autogen(docs): regenerate and update changelog
- 89b1b1b autogen(docs): regenerate and update changelog
- 0a5e043 autogen(docs): regenerate and update changelog
- 6cbe089 autogen(docs): regenerate and update changelog
- 7861702 autogen(docs): regenerate and update changelog
- c9f4b5f autogen(docs): regenerate and update changelog
- fe260d1 autogen(docs): regenerate and update changelog
- fbf39dd autogen(docs): regenerate and update changelog
- 9b33fc5 autogen(docs): regenerate and update changelog
- f9cee32 autogen(docs): regenerate and update changelog
- 841d58b autogen(docs): regenerate and update changelog
- 4a8e9a4 autogen(docs): regenerate and update changelog
- cdc0bec autogen(openapi): regenerate swagger spec and internal client
- 4a00e3e autogen(openapi): regenerate swagger spec and internal client
- dedcf5b autogen(openapi): regenerate swagger spec and internal client
- 92eb03a autogen(openapi): regenerate swagger spec and internal client
- f9a87d3 autogen(openapi): regenerate swagger spec and internal client
- 1ff8f20 autogen(openapi): regenerate swagger spec and internal client
- 11bf9df autogen(openapi): regenerate swagger spec and internal client
- e796893 autogen(openapi): regenerate swagger spec and internal client
- 27f2ef5 autogen(openapi): regenerate swagger spec and internal client
- 35d6295 autogen(openapi): regenerate swagger spec and internal client
- ce00a42 autogen(openapi): regenerate swagger spec and internal client
- db4fd7d autogen(openapi): regenerate swagger spec and internal client
- 146b162 autogen(openapi): regenerate swagger spec and internal client
- e1636d1 autogen(openapi): regenerate swagger spec and internal client
- 9389773 autogen(openapi): regenerate swagger spec and internal client
- af859fe autogen(openapi): regenerate swagger spec and internal client
- f1708f2 autogen(openapi): regenerate swagger spec and internal client
- 3e8413e autogen(openapi): regenerate swagger spec and internal client
- 11c8c72 autogen(openapi): regenerate swagger spec and internal client
- 800ce0a autogen: add v2.2.0-rc.3 to version.schema.json
- 8168ee3 autogen: pin v2.2.0-pre.1 release commit
- 0487217 autogen: render config schema
- a0c06ec chore(deps): bump @cypress/request and cypress (#3641)
- b177f81 chore(deps): bump axios and @openapitools/openapi-generator-cli (#3701)
- 23c8194 chore(deps): bump debug from 3.2.6 to 3.2.7 (#3640)
- 18d9793 chore(deps): bump follow-redirects in /test/e2e/oauth2-client (#3697)
- 4fa2889 chore(deps): bump github.com/docker/docker (#3707)
- 2ba3547 chore(deps): bump golang.org/x/crypto from 0.15.0 to 0.17.0 (#3680)
- efc00a8 chore(deps): bump golang.org/x/net from 0.14.0 to 0.17.0 (#3645)
- 083c90d chore: build tag (#3613)
- 3615e3d chore: bump docker base images (#3632)
- aa8a364 chore: bump openapi-generator (#3696)
- 2dc6606 chore: improve context (#3656)
- 8e94929 chore: update otel (#3686)
- f0501d2 docs: fix typo (#3649)
- f502d6e feat: add --skip-logout-consent flag to CLI (#3709)
- 5c8e792 feat: add authentication options to hooks (#3633)
- 62c006b feat: add flag to export public keys (#3684)
- 39ee5e1 feat: add missing index for jwk table (#3691)
- 19857d2 feat: add prompt=registration (#3636)
- 2a653e6 feat: add skip_logout_consent option to clients (#3705)
- 88b0b7c feat: allow injecting extra fosite strategies (#3646)
- 5dd7d30 feat: re-enable legacy client IDs (#3628)
- cde3a30 feat: remove flow cookie (#3639)
- 5f41949 feat: remove login session cookie during consent flow (#3667)
- 95cc273 feat: support multiple token URLs (#3676)
- d1f9ba8 fix: correct id token type in token exchange response (#3625)
- 22f0119 fix: dropped persistence/sql test errors (#3670)
- 5133cf9 fix: handle logout double-submit gracefully (#3675)
- af0d477 fix: handle subject mismatch gracefully (#3619)
- 1a40833 fix: handle token hook auth config (#3677)
- 24c3be5 fix: improved SSRF protection (#3669)
- 8812e0e fix: incorrect down migration (#3708)
- 3a764a0 fix: remove required mark (#3693)
- a748797 fix: timeout in jwt-bearer grants when too many grants are available (#3692)
- 0176adc fix: verifiable credentials JWT format (#3614)
- 8e6c4bf autogen(docs): regenerate and update changelog
- 33950db autogen(docs): regenerate and update changelog
- 28e9e31 autogen(openapi): regenerate swagger spec and internal client
- 57096be autogen: pin v2.2.0 release commit
- bfc05d0 chore(deps): bump github.com/opencontainers/runc from 1.1.8 to 1.1.12 (#3710)
- 65165e7 fix: return empty slice if requested_scope or audience is null (#3711)
Artifacts can be verified with cosign using this public key.